
Kiteworks Report Benchmarks Privacy and Compliance Risks Related to Sensitive Content Communications
Protecting your data and demonstrating compliance with the regulations and standards that govern how it is shared and stored has never been more difficult. Foreign nation-states that sponsor cybercriminal activity, organized crime syndicates, and malicious lone actors understand the value of data, and therefore the volume and complexity of cyberattacks on data continues to grow. In the latest Verizon Data Breach Investigations Report, data breaches increased 33% year over year.
Certain types of cyberattacks experienced exponential spikes. For example, CrowdStrike’s 2022 Global Threat Report reveals ransomware-related data leaks jumped 82% last year. The average ransom amount demanded by bad actors also grew—up 36% from 2020. The multiplication of cyberattacks within the supply chain this past year was also jarring, serving as a wake-up call for many organizations.
While manufacturing and transportation sectors remain the primary targets for supply chain attacks, most sectors are susceptible to supply chain attacks. Indeed, supply chain attacks target more than just logistics. Rather, they encompass the different technologies an organization uses, the code—both open source and custom—used in applications, contractors and suppliers, partners, customers, and numerous third parties.
Surveying the Risks of Sensitive Content Communications
In Kiteworks’ newly published 2022 Sensitive Content Communications Privacy and Compliance Report, we found that nearly two-thirds of organizations admit that they regularly share sensitive content with over 1,000 external organizations—and one-third of respondents share sensitive content with over 2,500 third parties. Digital communications put confidential data at risk, both when it is shared (viz., data in motion) and when it stored (viz., data at rest).
Organizations leverage different digital communication channels when sending, sharing, and receiving sensitive content: email, file sharing, file transfer, managed file transfer, application programming interface (API) protocols, and web forms. Cybercriminals exploit these channels in different ways. Unencrypted email sends, file shares, and file transfers are easily intercepted and accessed. Additionally, inadequate encryption technology and policies can be exploited.
Bad actors also embed malware and viruses in messages and attachments that, when opened, enable access to systems that contain critical data. When those viruses facilitate account takeovers, emails, file shares, and file transfers can be intercepted and accessed. Finally, insider threats, whether unintentionally by a careless employee or intentionally by a malicious insider, also heighten risk of a sensitive data breach.
Achieving and Demonstrating Compliance in Governance and Security
Numerous government and industry regulations and standards exist to mitigate these risks. Some pertain to personally identifiable information (PII) and protected health information (PHI), such as the Health Insurance Portability and Accountability Act (HIPAA), General Data Protection Regulation (GDPR), California Consumer Privacy Act (CCPA), Personal Information Protection and Electronic Documents Act (PIPEDA), and Payment Card Industry Data Security Standard (PCI DSS). Some relate to protecting sensitive content communications with the government sector like Cybersecurity Maturity Model Certification (CMMC), Federal Risk and Authorization Management Program (FedRAMP), Federal Information Processing Standard (FIPS) 140-2, and Infosec Registered Assessors Program (IRAP). Others like the National Institute of Standards and Technology (NIST) 800-171 and SOC 2 provide private and public sector entities with rigorous standards to protect data privacy.
The types of sensitive content covered by the different regulations and standards vary. Nearly every organization sends, shares, receives, and stores PII related to their employees, contractors, partners, and customers. Financial firms—banks, investors, and insurers—provide trusted services to businesses and consumers and send, share, and transfer account statements, loan applications, insurance claims, and other sensitive financial documents. Product designs, customer lists, production schedules, and various intellectual property (IP)-related information fall into the sensitive content bucket for manufacturers. Healthcare organizations share protected health information (PHI) like patient records, X-rays, and prescriptions, not only related to HIPAA but to GDPR and PCI DSS, among other regulations. Other industry sectors like government, legal, and others have their own respective data types. Finally, our survey indicates finance, HR, and legal departments are typically the most active departments in sending, sharing, receiving, and storing sensitive content.
Four Sensitive Content Communication Insights in the Report
The Kiteworks 2022 Sensitive Content Communications Privacy and Compliance Report seeks to identify key trends and insights across industry sectors in the North American, Europe, and Asia Pacific regions. Surveying 400 IT, security, privacy, and compliance professionals in 15 different countries, the report provides organizations with a benchmark for evaluating the maturity of their sensitive content communications. The report breaks its insights into four categories.
Insight #1: Silos and Inefficiencies
Survey respondents indicated they employ different communication channels to send and receive sensitive content. Nine out of 10 respondents, for example, use email for one-quarter of their sensitive content communications, and slightly more than one-third use it for 35% or more (Figure 1). File sharing is ranked second with 45% of respondents using it for one-quarter or more of their communications. Other communication channels are used regularly, though in small numbers and frequency. Different systems are used for tracking, controlling, and securing sensitive content communications; four or more in two-thirds of instances. Needing to manage each of them and their separate consoles and data flows creates complexity and risk. This also makes it difficult to govern sensitive data and demonstrate compliance with regulators and auditors.
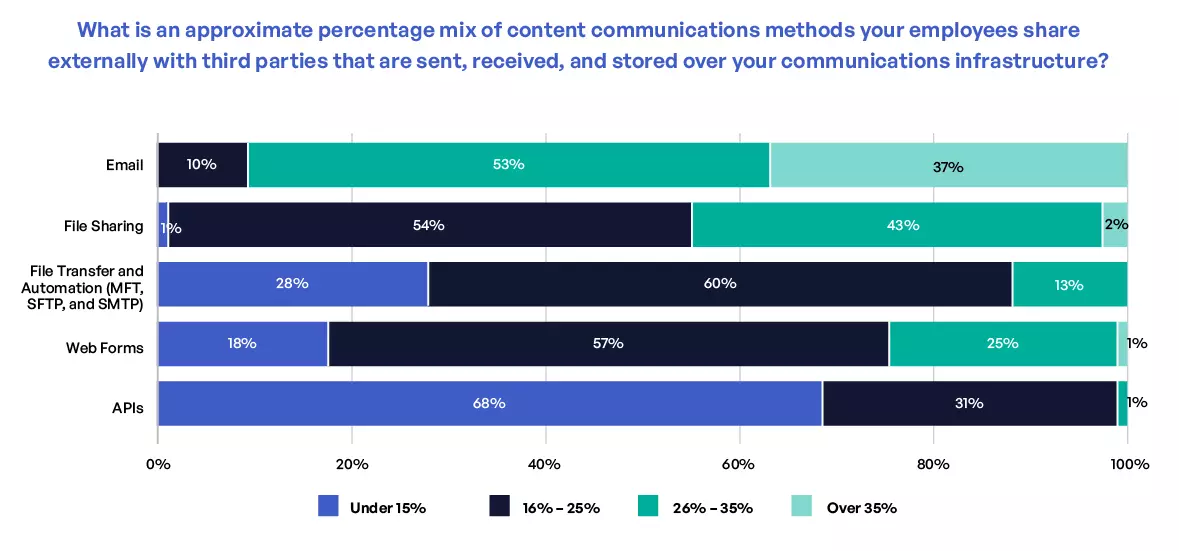
Figure 1. Communication channels used by employees to share and transfer sensitive content.
Email encryption protocols are incompatible with each other and complicate content communications with third parties that use another protocol internally. If an encrypted email cannot be decrypted onsite, 60% of respondents indicated they ask senders to resend unencrypted files through an unpublished shared drive link via Box, Dropbox, Google Drive, and other cloud-based content repositories; the remaining 40% ask senders to use a password-encrypted zip file. All this back and forth translates not only into inefficiencies but into risk as well (Figure 2).

Figure 2. How organizations deal with encrypted email that cannot be decrypted.
Insight #2: Security Gaps
Insider threats involve the sharing of sensitive content internally with third parties outside of an organization, where sensitive content is sent to or shared with the wrong person. This can be intentional (theft or sabotage) or unintentional (phishing, spear-phishing). More respondents listed insider threats as a top security concern than any other security area (26% ranked it #1). External threats also were top of mind for respondents, with nearly 6 out of 10 ranking it #1 or #2. Governance of sensitive content communications was also a security concern that was often listed by respondents, with 29% of respondents ranking it #1, #2, or #3 (Figure 3).
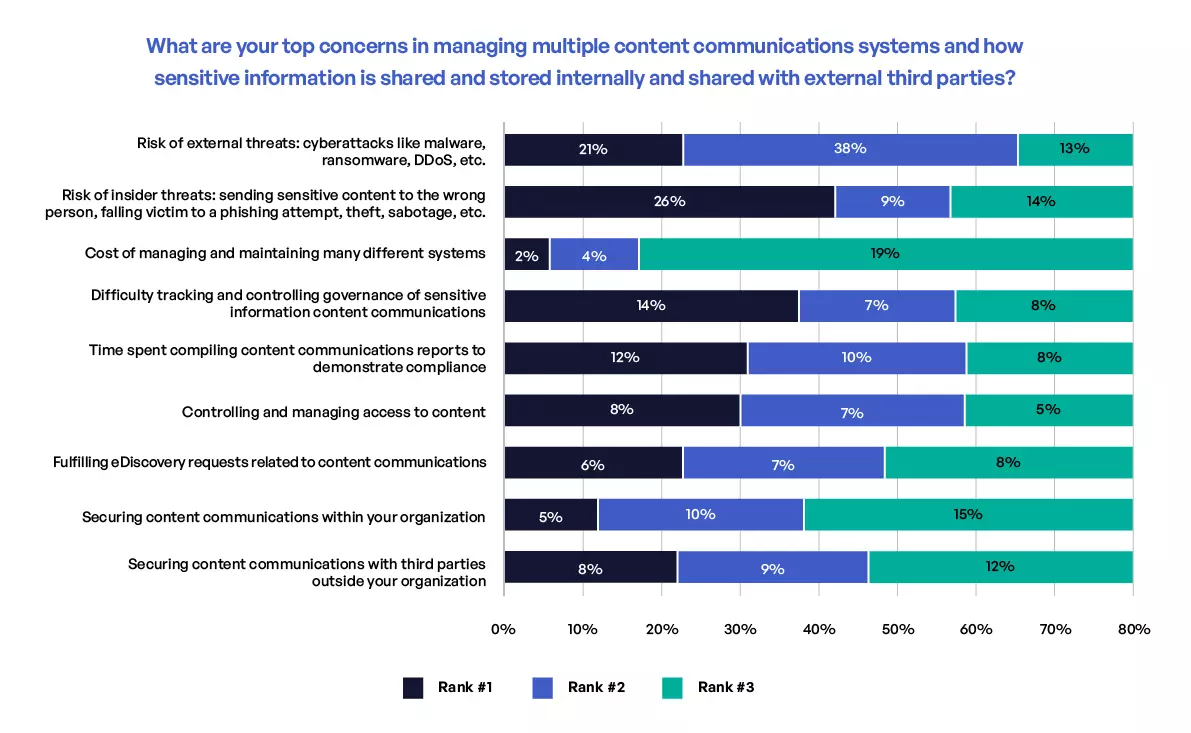
Figure 3. Top security concerns in managing sensitive content communications.
Surprisingly, the ratio of data loss prevention (DLP) for outbound sensitive content sharing was lower than one would expect. For example, 54% of respondents either do not use DLP or only use it for some emails sent to third parties. Almost 6 in 10 respondents either do not use DLP or only use it in some instances for file sharing and file transfer and automation. For inbound communications, 7% of respondents do not use antivirus or antispam technologies for all incoming content communications with third parties, and almost half only use them for some. And despite zero-trust security receiving significant attention including its pivotal importance in Executive Order 14028, zero trust is applied inconsistently across the different communication channels.
Insight #3: Risk Management
With a multitude of tools being used for sensitive content communications and a siloed infrastructure, risk management was cited by many respondents as a challenge. Over half indicated their organizations are inadequately protected against third-party sensitive content communication risks. Privacy and compliance professionals expressed the highest concern, with more than 7 in 10 indicating their organizations are not protected from third-party sensitive content risks.
Only 16% of respondents said their third-party risk management strategy is above reproach, whereas 41% want to see significant improvement or even a whole new approach. Respondents noted unifying, tracking, and controlling sensitive content communications is a top priority for executive leadership (Figure 4).
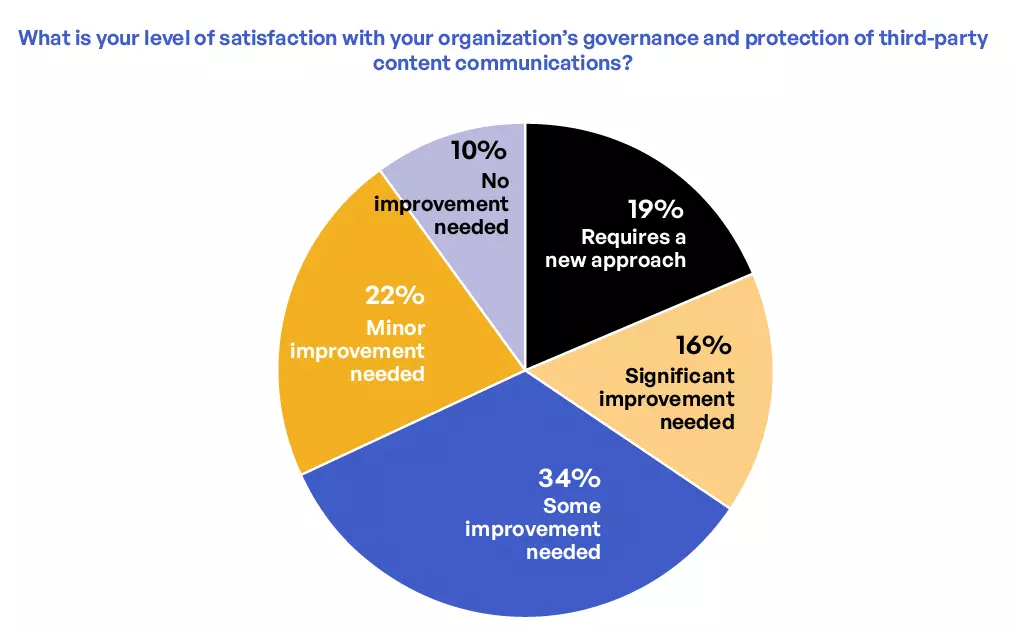
Figure 4. Level of confidence in risk management and protection of third-party sensitive content communications.
Insight #4: Compliance
Respondents cited numerous compliance regulations that impact their organizations. HIPAA, PCI DSS, CCPA, GDPR, and Data Protection Act (DPA) were listed by over 50% as standards with which they must comply annually. Over half of respondents (56%) produce seven-plus compliance reports annually. This adds up to a lot of hours, with 77% spending over 20 hours per report. And despite all of the time spent on compliance, a surprising 79% indicated their compliance reports are not fully accurate.
Why is this number so high? One reason is that 69% of respondents said improvement of their governance of sensitive content communications is needed. Of these, 35% believe significant improvement or an entirely new approach to governance is required.
Gleaning Key Sensitive Content Communication Takeaways
The threat of sensitive content being accessed by unauthorized users, whether intentionally or accidentally, while in transit or at rest, is real. As more PII, PHI, and IP comes online, cybercriminals find ways to steal it, sell it, or demand a ransom for it. Historically, organizations employed security mechanisms at the computing edge to secure sensitive, unstructured content. This report reveals a serious security and compliance gap, that when left unaddressed, can be costly; IBM and Ponemon Institute in their latest Cost of a Data Breach Report pinpoint the average cost of a data breach at $4.24 million.
As regulations and standards evolve and additional ones are introduced, compliance will continue to become increasingly important. But without the proper governance tracking and controls in place, organizations either will remain at risk of noncompliance or will struggle to demonstrate compliance due to a disaggregated, siloed set of tools. The stark reality is that current approaches to sensitive content communications simply cannot scale to meet the demands of modern businesses.
Visit our 2022 Sensitive Content Communications Privacy and Compliance Report webpage that consolidates all available resources ontoone page.
Additional Resources
- Blog PostData Sovereignty Compliance
- Blog PostHow Does Data Compliance Impact?
- Blog PostData Sovereignty And GDPR
- Blog PostHow to Be GDPR Compliant
- Blog PostProtecting Your Most Sensitive Content