
Efficiently Capture Support Files From Customers’ Products
Customer support teams often need to collect various types of files from customers’ products, such as logs, pictures, videos, screenshots, design files, databases, etc. These files can be large and diverse, making it challenging to capture and manage them efficiently. Additionally, these files may contain sensitive data, requiring secure handling to ensure data privacy and compliance with relevant regulations. Kiteworks provides a simple, secure, and efficient solution for capturing support files from customers’ products. Without leaving email or their Salesforce Cases and Accounts, customer support reps can effortlessly send, request, and store related documents, in any file type or size. Kiteworks also provides robust security and governance features, such as encryption, access controls, and audit logs, to protect the data and track all actions for compliance reporting.
Comply With Security Regulations Without Slowing Your Team
Customer support teams handle a lot of sensitive data from customers, including personally identifiable information (PII), intellectual property (IP), and protected health information (PHI). Complying with an ever-expanding list of compliance regulations and policies can slow down support responsiveness and reduce customer satisfaction. Ignoring these regulations, on the other hand, can lead to compliance fines, breaches, lawsuits, and lost business. Kiteworks provides a simple and transparent solution for enforcing and reporting on governance policies, without slowing down your team. With Kiteworks, you generate the reports you need to comply with GDPR, SOC 2, HIPAA, ISO 27001, 27017, and 27018, and other regulations.


Avoid High Cloud Storage Costs
While cloud-based customer support software offers power and convenience, the associated file storage costs can be prohibitive. Compliance requirements may necessitate keeping sensitive data on-premises. Kiteworks allows organizations to use the storage of their choice for customer support files, avoiding high cloud storage costs. It can be plugged directly into your support team’s Salesforce Service Cloud cases, enabling them to effortlessly send, receive, and store files securely.
Secure Customer Support Records
Customer support teams need to securely store customer support records, such as support tickets, case notes, and correspondence, to ensure data privacy and compliance with customer data regulations. Kiteworks provides a centralized platform for storing support records securely, with features like encryption, access controls, and audit logs to maintain data security and integrity.

Distribute Support Documentation
Distributing support documentation like user manuals, troubleshooting guides, or FAQs to customers or external partners requires a secure and efficient method to ensure data confidentiality and compliance with relevant regulations. Kiteworks provides a secure platform for sharing support documentation, with features like encryption, access controls, and audit logs to maintain data confidentiality and compliance.
Implement Notification and Record-keeping Requirements for Incidents
Organizations need to maintain detailed logs and records of data access, file transfers, and user activities, to comply with incident notification and record-keeping requirements. Kiteworks maintains detailed logs and records of data access, file transfers, and user activities, helping organizations comply with incident notification and record-keeping requirements.
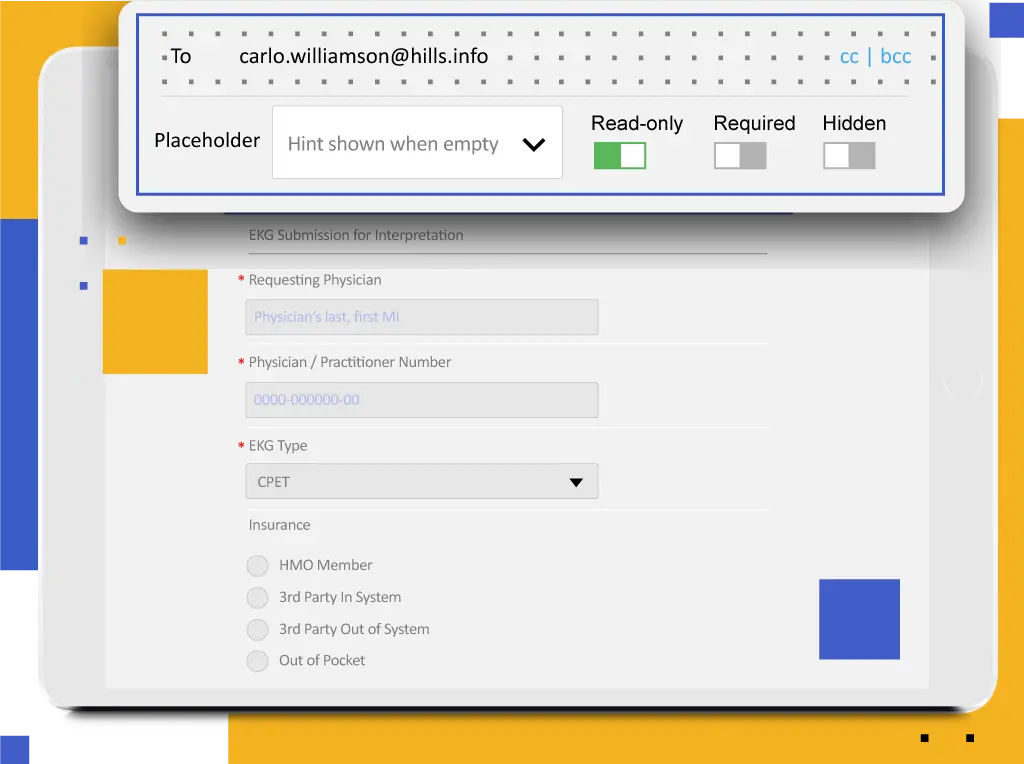
Establish Opt-in Mechanisms and Procedures for Data Collection
To comply with consent requirements, organizations need to provide secure web forms and data collection mechanisms that ensure personal information protection. Kiteworks provides secure web forms and data collection mechanisms that ensure personal information protection, helping organizations comply with consent requirements.
Roll Out to End-users
Customer support teams need to roll out new tools or updates to end-users in a secure and efficient manner, ensuring data confidentiality and compliance with relevant regulations. Kiteworks provides a secure platform for rolling out new tools or updates to end-users, with features like encryption, access controls, and audit logs to maintain data confidentiality and compliance.


Defend Your Intellectual Property From an External Threat
Organizations with a history of innovation are at risk of having their research stolen. Hackers, competitors, criminal organizations, and rogue nation-states pose grave risks to the intellectual property that researchers and developers have created. Kiteworks provides a secure platform for protecting sensitive content from cyberattacks. It creates a secure perimeter around the systems that receive, hold, and send sensitive content.
Securely Share Customer Data
Customer support teams often need to share sensitive customer data with other departments or external partners, requiring a secure and efficient method to ensure data confidentiality and compliance with relevant regulations. Kiteworks provides a secure platform for sharing customer data, with features like encryption, access controls, and audit logs to maintain data confidentiality and compliance.


Manage Data Retention Policies
Customer support teams need to manage data retention policies, ensuring that customer data is stored and deleted in accordance with legal requirements and company policies. Kiteworks provides features for managing data retention policies, such as automatic deletion of data after a specified period, to ensure compliance with legal requirements and company policies.
Respond to Data Subject Access Requests
Customer support teams need to quickly respond to data subject access requests or data breach notifications, requiring a secure and efficient method to access and share the requested data. Kiteworks provides a secure platform for accessing and sharing the requested data, with features like encryption, access controls, and audit logs to maintain data confidentiality and compliance.


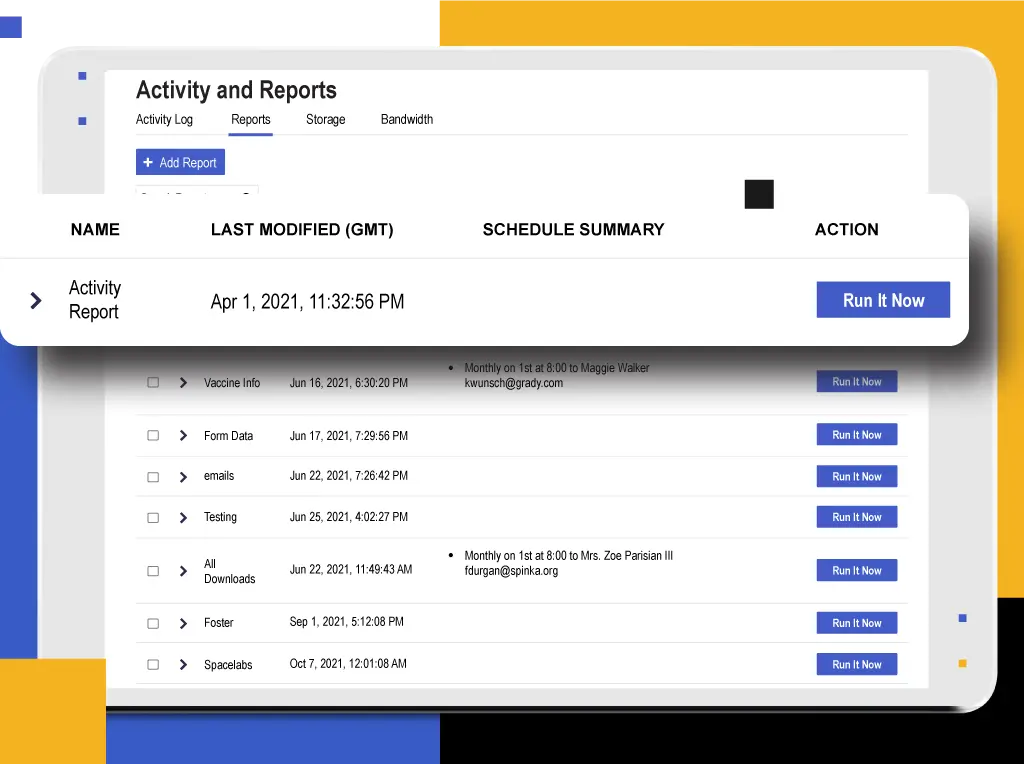
Streamline the Support Record Management Process
Customer support teams need to streamline the support record management process, ensuring that support records are easily accessible and manageable. Kiteworks integrates with other customer support tools, streamlining the support record management process and ensuring that support records are easily accessible and manageable.
Protect Customer Data During Transfers
Customer support teams often need to transfer customer data between different systems or locations, requiring a secure and efficient method to ensure data confidentiality and compliance with relevant regulations. Kiteworks provides a secure platform for transferring customer data, with features like encryption, access controls, and audit logs to maintain data confidentiality and compliance.

Frequently Asked Questions
Customer support organizations handle a variety of sensitive information types, including customer financial information (e.g., credit card numbers and bank account details), personally identifiable and protected health information (PII/PHI) (e.g., addresses, phone numbers, and email addresses, insurance information, etc.), passwords, and more. In addition, customer support organizations may also handle confidential product- or service-related information as well as information about customer preferences, behavior, and interests.
Customer support organizations can keep customer data secure by implementing best practices such as establishing strict access controls that only allows customer success organizations to access and prohibits access by employees in other departments like engineering, human resources, etc. To further protect customer data, it’s a good idea to apply encryption to this sensitive information both in transit and at rest, store it securely by ensuring it can only be accessed by authorized personnel, implement automated security tools such as intrusion detection systems (IDS), and even maintain tight control over the physical environment holding this information, such as secure buildings and locked data centers.
The best way for customer support organizations to securely send and receive customer logs, configuration settings, and other sensitive customer usage information is to use a secure file sharing platform that is designed with enterprise-grade security protocols. This type of platform should be capable of performing data encryption at rest and in motion, using strong authentication protocols, and allowing only authorized users to access files. Access controls policies can be set up to control who can view, download, or modify customer files.
Organizations should incorporate multi-factor authentication (MFA), identity access management (IAM), data encryption at rest and in motion, and access control policies to mitigate the risk of unauthorized access to customer logs and other customer data. Organizations should also regularly monitor and update their security protocols. It’s also a good idea to regularly back up customer data to ensure it is recoverable in the event of a ransomware attacks.
The risks associated with customer support processes include data breaches stemming from cyberattacks like ransomware attacks and phishing, and unauthorized access to customer files, leading to data leakage and a compliance violation. To avoid these and other risks, organizations should have a robust plan in place to protect customer data to ensure that only authorized customer support employees have access to customer content, and those staff members are properly trained in best-practice security protocols.
Compliance regulations for customer support organizations in the U.S. vary state to state but typically center around best practices for protecting customers’ personally identifiable and protected health information (PII/PHI). Organizations must ensure that their processes meet customer privacy and data collection standards, set by the state or federal government. The Gramm-Leach-Bliley Act (GLBA), the Payment Card Industry Data Security Standard (PCI DSS), the General Data Protection Regulation (GDPR), and the Health Insurance Portability and Accountability Act (HIPAA) are just a few examples of regulations that require customer support organizations and other employees to handle customer data in a manner that prioritizes data security and data privacy.
FEATURED RESOURCES

Achieving Zero Trust Security With Kiteworks: A Comprehensive Approach to Data Protection

Kiteworks Complies With ISO 27001, 27017, and 27018

Top 5 Ways Kiteworks Secures Microsoft 365 Third-party Communications


