
Secure Private Data Management Through FedRAMP Authorization
FedRAMP establishes uniform cloud security standards across federal agencies, requiring cloud service providers to meet strict security requirements. The Kiteworks Private Data Network, FedRAMP Authorized for Moderate Impact Level information, enables federal agencies and private organizations to securely handle sensitive CUI and FCI data. The platform offers robust security features including deployment on AWS virtual private cloud with dedicated servers, single-tenancy architecture ensuring sole encryption key ownership, and fully encrypted file storage and transfer that prevents access by third parties including Kiteworks, AWS, or law enforcement. Kiteworks undergoes annual rigorous audits of 400 controls and conducts continuous monitoring and vulnerability scanning between audits.
Streamline CMMC Certification to Win Contracts With the DoD
CMMC compliance affects all defense contractors in the U.S. Defense Industrial Base who handle CUI and FCI. The Kiteworks Private Data Network supports nearly 90% of CMMC 2.0 Level 2 requirements through its FedRAMP Moderate Authorization. The platform unifies secure email, file sharing, managed file transfer, web forms, and SFTP into one system with comprehensive protection features: end-to-end encryption, granular access controls, role-based permissions, and multi-factor authentication. Kiteworks enables defense contractors to maintain strict data custody with SafeEDIT DRM technology, which keeps sensitive documents within security perimeters while allowing collaboration. The consolidated audit log tracks all CUI and FCI movement, simplifying compliance verification during audits and reducing the time and cost of demonstrating adherence to CMMC requirements.


Comprehensive GDPR Compliance With a Secure and Visible Platform
GDPR affects all organizations handling EU citizens’ personal data across all industries operating in European markets. Kiteworks enables GDPR compliance through essential features: AES-256-bit encryption for data at rest, TLS 1.3 for transit, and sole encryption key ownership. The platform implements granular access controls with role-based permissions, supports multi-factor authentication, and provides comprehensive audit logs integrated with SIEM solutions. Organizations can efficiently manage consent, handle data subject requests, set retention policies, and execute Right to Be Forgotten requirements with a single click. The CISO Dashboard delivers unified visibility across all file activities containing PII.
Verified Data Protection Through SOC 2 Continuous Security Monitoring
SOC 2 compliance impacts organizations across all industries globally that handle sensitive customer data, requiring rigorous implementation of security controls based on the five trust service principles. The Kiteworks Private Data Network is SOC 2 Type II certified, ensuring customer data remains protected through comprehensive security measures. The platform implements continuous system monitoring to identify risks early and address security gaps proactively. Kiteworks maintains high system availability while ensuring data processing integrity through complete, accurate, and authorized procedures. Independent third-party audited security controls establish rigorous data privacy practices and formal protection policies.


ISO Certifications Ensuring Enterprise-grade Security Controls
ISO 27001, 27017, and 27018 certifications affect organizations across all industries worldwide handling sensitive information, particularly in regulated sectors like healthcare, finance, and government. These standards require implementing comprehensive information security management systems with documented controls and regular audits. Kiteworks’ validated 175 security controls and single-tenant architecture minimize external attack surfaces while the platform protects PII, PHI, and IP through defense-in-depth security featuring built-in hardening, end-to-end encryption (TLS 1.3 and AES-256), and zero-trust principles. Organizations maintain complete control over their sensitive data with exclusive encryption key ownership, while regular penetration testing, ongoing bounty programs, and assume-breach architecture provide robust security verification.
Australian Data Sovereignty Through IRAP-assessed Environment
IRAP compliance affects organizations across Australia that partner with federal and state government agencies, requiring strict protection of sensitive data from unauthorized access. The Kiteworks Private Data Network features an IRAP-assessed environment, assessed against PROTECTED level controls. The solution ensures complete data sovereignty with single-tenant hosting entirely within Australia on separate AWS virtual private clouds. Organizations maintain exclusive encryption key ownership while implementing defense-in-depth security through least-privilege defaults, role-based access controls, and multi-factor authentication. Kiteworks’ hardened virtual appliance incorporates WAF and network firewalls, intrusion detection, and unified logging for rapid event response.


Secure HIPAA PHI Exchange Through Zero-trust Architecture
HIPAA compliance affects healthcare providers, insurers, and their business associates across the United States who handle PHI such as lab results, prescriptions, and treatment plans. Organizations must implement robust safeguards to protect patient privacy and secure sensitive data. The platform enforces granular access controls with role-based permissions tied to specific job functions, while real-time alerts and comprehensive audit logs enable rapid incident detection and response. Healthcare organizations maintain secure collaboration with business associates through zero-trust data exchange policies and encryption of PHI in transit and at rest. Kiteworks provides secure mobile containers with remote wipe capabilities for lost devices, reliable data backup through geographically distributed centers, and customizable security policies.
FIPS 140-3 Validated Encryption for Regulatory Compliance
FIPS 140-3 compliance impacts U.S. government agencies, contractors, and regulated industries like healthcare and financial services that handle sensitive information including CUI, CDI, and FCI. Organizations must implement cryptographic modules tested and validated by NIST to protect confidential data. The Kiteworks Private Data Network offers FIPS 140-3 Level 1 validated encryption and customers maintain sole ownership of encryption keys with complete rotation control. Kiteworks enables organizations to set precise permissions, implement role-based access controls, and maintain comprehensive audit logs, demonstrating commitment to data security while building customer trust.


Militarized Data Protection Through ITAR Compliance Controls
ITAR compliance affects U.S. defense contractors and manufacturers worldwide handling items on the United States Munitions List, requiring strict protection of defense-related technical data against foreign access. The Kiteworks Private Data Network bridges NIST 800-171’s foundational cybersecurity controls and ITAR’s stringent export-control requirements through FedRAMP Moderate Authorized security with zero-trust access controls and granular permissions. The platform secures data through end-to-end encryption and maintains immutable audit logs across all communication channels. Anomaly detection identifies potential data breaches with immediate security alerts. Kiteworks’ point-and-click secure web forms with automatic policy enforcement enable organizations to maintain compliant operations while ensuring complete visibility for mandatory DDTC reporting and geographic restrictions that satisfy ITAR export controls.
Streamline Security Policy Management to Protect NIS 2 Data
The NIS 2 Directive affects critical and important entities throughout the European Union, requiring robust cybersecurity measures for network and information systems. The Kiteworks Private Data Network standardizes security policies across email, file sharing, MFT, SFTP, and mobile communications with AES-256/TLS encryption and role-based access controls. Anomaly detection immediately alerts teams to suspicious activities, while immutable audit logs support breach investigations and mandatory reporting. The platform’s ISO 27001/27017/27018 and SOC 2 certifications validate its cybersecurity effectiveness. Kiteworks maintains business continuity through built-in disaster recovery while simplifying vulnerability management with one-click updates and regular security testing.

PCI DSS Compliant Real-time Monitoring Through Immutable Audit Logs
PCI DSS compliance impacts merchants, payment processors, and service providers across retail, hospitality, e-commerce, financial, and healthcare industries who handle cardholder data. The Kiteworks Private Data Network supports compliance through its hardened virtual appliance on single-tenant AWS clouds with least-privilege defaults. The platform secures data using encryption at rest and in transit with customer-managed encryption keys. Granular access controls with unique user IDs restrict data to authorized personnel. Kiteworks creates immutable audit logs capturing all activities in real time with SIEM integration, while regular vulnerability scans and penetration tests ensure ongoing security.
DORA Support Through Third-party Communication Security
The Digital Operational Resilience Act (DORA) affects financial entities across the European Union, requiring robust ICT risk management, third-party oversight, incident reporting, and continuous testing. The Kiteworks Private Data Network enables compliance by securing sensitive financial information shared with clients and third parties. The platform implements end-to-end encryption and granular access controls while providing comprehensive visibility across all communication channels. Financial organizations gain real-time threat monitoring through the CISO Dashboard with detailed audit logs for swift incident detection and regulatory reporting. Kiteworks strengthens third-party risk management with continuous data monitoring and undergoes yearly audits and penetration testing to enhance digital resilience.


Data Sovereignty Enforcement Through Geofencing Controls
Data sovereignty affects multinational companies operating in regions with strict privacy regulations like the EU (GDPR), Australia (CDR), Canada (PIPEDA), and California (CCPA), requiring data storage within specific geographic boundaries. The Kiteworks Private Data Network enables compliance through configurable geofencing that restricts access via IP address block-lists and allow-lists. The platform supports multiple deployment models to ensure data remains in appropriate jurisdictions while maintaining exclusive encryption key ownership. Data is protected with TLS 1.3, AES-256, and FIPS 140-3 validated ciphers. The CISO Dashboard provides visibility into all file activities, enabling organizations to track data access, transfers, and portability requests across connected systems.
eDiscovery Compliance Through Centralized Communication Channels
eDiscovery requirements affect organizations worldwide facing litigation or regulatory investigations, demanding efficient electronic data identification and preservation. The Kiteworks Private Data Network streamlines eDiscovery by consolidating email, file sharing, and managed file transfer into a centrally controlled system. The platform maintains immutable audit logs of all file activities while preserving versions to establish chain of custody. Organizations gain comprehensive search across repositories including Salesforce, OneDrive, SharePoint, and Dropbox. Role-based access policies ensure only authorized personnel access sensitive information.


GxP Compliance Through Double-encrypted Data Protection
GxP regulations affect pharmaceutical, biotechnology, medical device, and food industries across the EU and U.S., requiring validated systems for electronic record integrity. Kiteworks supports EudraLex Annex 11 and CFR Title 21 Part 11 compliance through its hardened virtual appliance with zero-trust architecture and file/disk double encryption. The platform implements role-based access controls with least-privilege defaults and multi-factor authentication. Immutable, time-stamped audit logs capture all system activities without throttling while integrating with SIEM systems. Content-based risk policies enforce dynamic security controls, ensuring information flows maintain ALCOA+ principles throughout regulated processes.
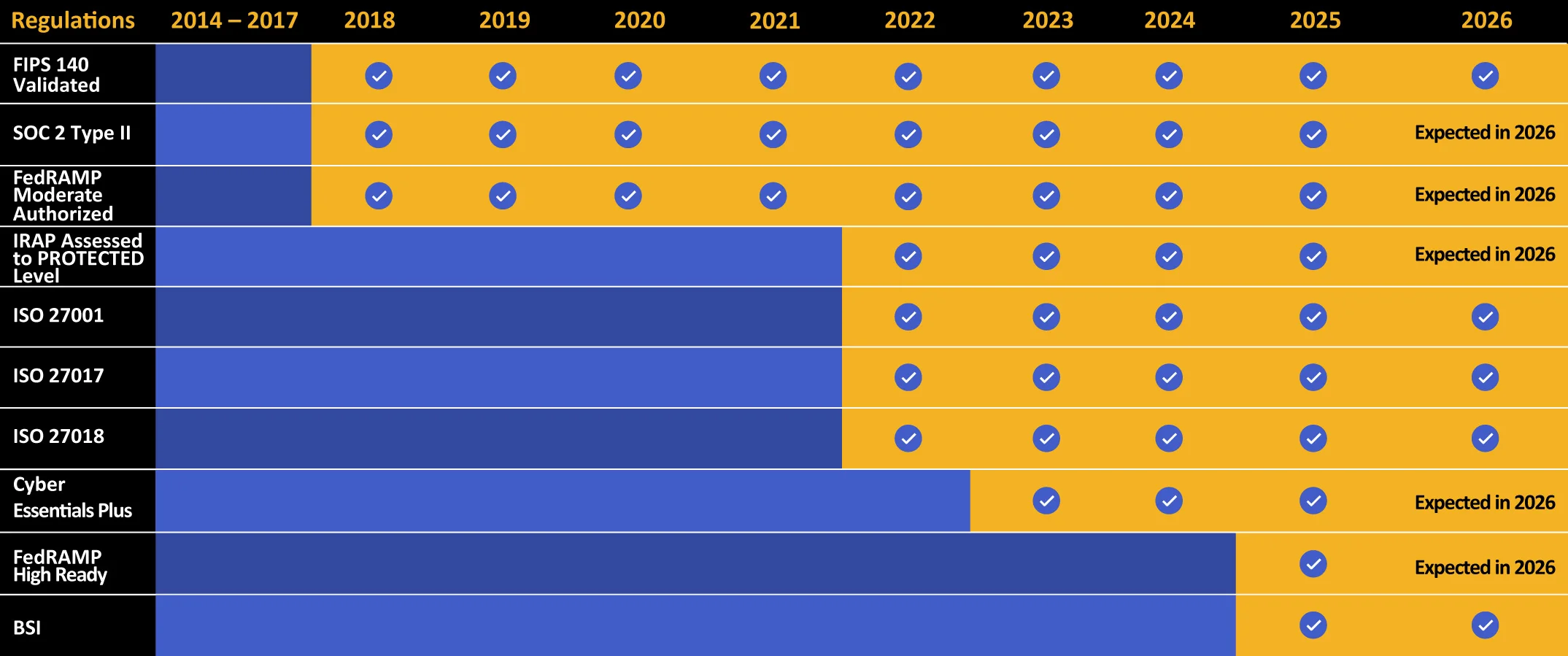
Kiteworks touts a long list of compliance and certification achievements.
Frequently Asked Questions
FEATURED RESOURCES

How To Protect PHI and Comply With HIPAA While Meeting Employee Vaccine Mandates

Federal Agency and Contractor Use Cases: Kiteworks Private Content Network Innovations

Create an IRAP-compliant Private Content Network With Kiteworks

Data Sovereignty and GDPR [Understanding Data Security]

