
NIS 2 Directive: What it Means for Your Business
The Network and Information Security Directive (NIS Directive) is a piece of legislation adopted by the European Union (EU) in 2016 to increase cybersecurity and protect essential services and infrastructure from cyber threats. The NIS Directive requires EU member states to establish a national framework for network and information security and designate certain operators of essential services (OES) and digital service providers (DSPs) as “critical infrastructure” that must meet cybersecurity standards. The directive also mandates incident reporting requirements and requires member states to cooperate on cybersecurity issues.
Evolution of the NIS Directive
The NIS Directive aimed to increase cooperation between member states, provide a culture of security across industries vital to the economy or society, and ensure that digital service providers and operators of essential services meet the necessary cybersecurity requirements.
With the rapid digital transformation and increasing cyber threats, however, more comprehensive legislation was needed. This led to the European Commission proposing the NIS 2 Directive in December 2020.
The NIS 2 Directive, an upgraded version of the NIS Directive, aims to address identified gaps and inconsistencies, such as those related to the security requirements and the oversight of key digital service providers. It also broadens the scope to cover more sectors like postal and courier services, waste water management, etc., and introduces stricter supervisory measures.
The NIS 2 Directive also aims to further harmonize the security obligations of companies, simplifying the regulatory environment and preventing forum shopping.
In November 2022, the European Union announced its intention to broaden the scope of the Network and Information Systems (NIS) Directive as a solution against cyber vulnerabilities and threats. These reforms, referred to now as NIS 2, aim to establish a stronger cyber resilience by adding outsourced IT providers and managed service providers (MSPs) to the current coverage of the directive. As expected, the new rules will affect essential service providers, such as energy, healthcare, transport, or water, which will force them to adhere to the regulations and risk facing fines of up to £17 million in the UK and €10 million or 2% of worldwide turnover in the EU for any noncompliance.
The formal approval of NIS 2 took place on November 10, 2022, with the formal publication coming into force on January 16, 2023. This means that EU member states must begin implementation within 21 months of the publication date. Thus, the implementation must be completed by October 17, 2024.
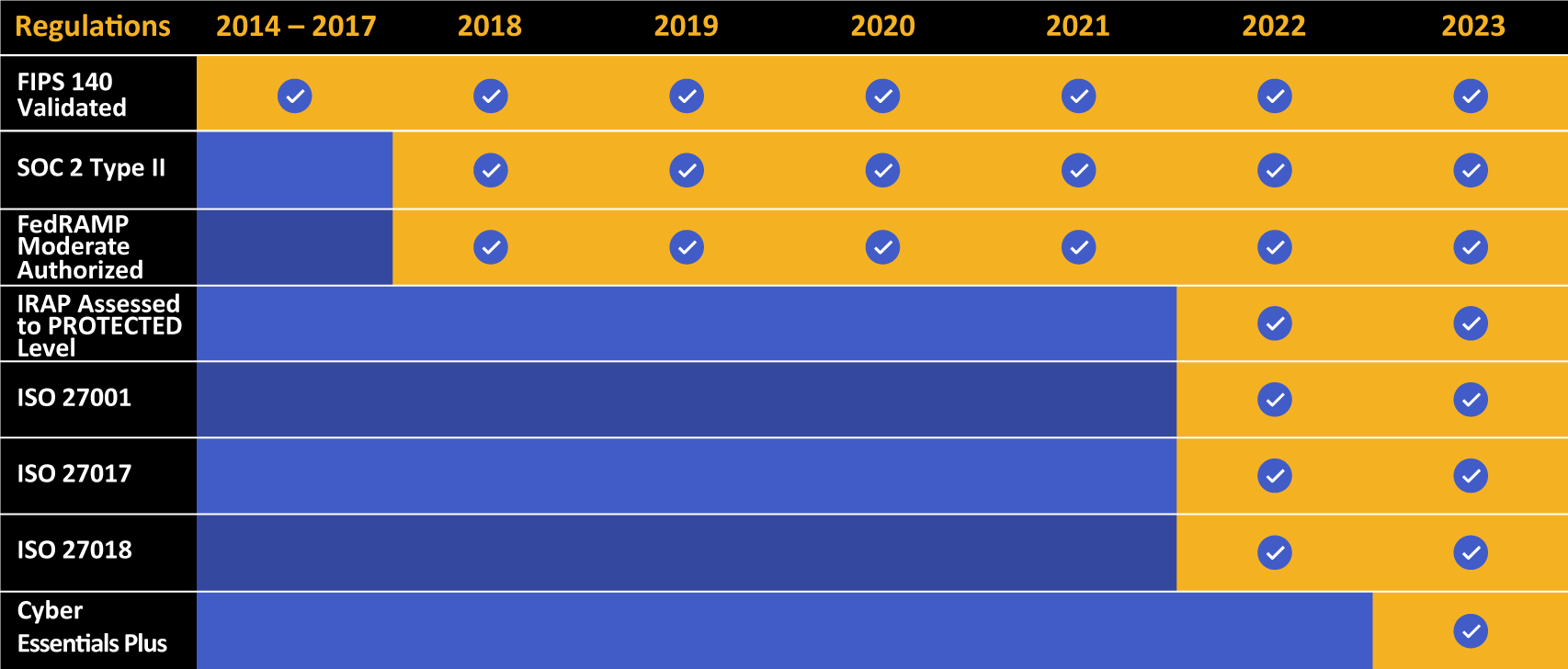
Kiteworks touts a long list of compliance and certification achievements.
NIS 2 Directive: Key Changes
The NIS 2 Directive rescinds the original NIS Directive and creates a more extensive and standardized set of rules on cybersecurity for organizations carrying out their activities within the EU. NIS 2 encompasses some major changes, including:
Wider Scope of Coverage for NIS 2 Directive
The number of organizations subject to the NIS 2 Directive has increased significantly over the original NIS Directive. The new NIS 2 Directive specifically defines the organizations to which the obligations apply. Inclusion of postal services, waste management, chemical production, and distribution and agricultural food sectors will see the number of sectors covered by the NIS 2 Directive increase from 19 to 35.
Additionally, NIS 2 provides greater detail on which entities within these sectors are subject to requirements. Any entity with more than 250 employees and an annual turnover of more than €50 million and/or an annual balance sheet above €43 million is covered. And in certain circumstances, entities must comply irrespective of company size, such as public electronic communications network providers.
Strengthened Security Requirements in NIS 2 Directive
The NIS 2 Directive strengthens security requirements for businesses by enforcing a risk management approach and providing a minimum list of basic security elements that must be applied. In addition, it introduces more specific provisions on the process of reporting incidents, the content of the reports, and the timing (i.e., within 24 hours of the discovery of the incident).
Increased Collaboration With NIS 2 Directive
NIS 2 aims to enhance collaboration by increasing trust and facilitating the sharing of information between EU member states and their coordinated management of large-scale cyber crises at the EU level. This led to the creation of the European Cyber Crisis Liaison Organization Network (EU CyCLONe), which is specifically dedicated to these initiatives at the EU level.
Faster Incident Reporting With NIS 2 Directive
NIS 2 mandates that key and critical entities must notify their respective national computer security incident response teams (CSIRTs) or, if applicable, the relevant competent authorities of any incident that has a major effect on their services. The steps to be taken include: sending an early warning within 24 hours of becoming aware of the incident, which must mention whether the incident could be the result of malicious acts or have a cross-border effect; sending an incident notification within 72 hours, providing an initial review of the incident and its magnitude and outcomes; sending an intermediate report if requested by the CSIRT, or competent authority; and sending a final report no later than one month from the notification of the incident, which must detail the likely cause of the incident, any mitigation measures employed, and any cross-border repercussions of the incident.
Enforcing NIS 2 Directive Compliance
EU member states will be able to use a stringent enforcement system, which includes the right to conduct inspections, safety evaluations, and demand data and documents. Breaches of the NIS 2 Directive could result in severe financial penalties:
- Up to €10 million or 2% of the total worldwide annual turnover for OES (Operator of Essential Services)
- Up to €10 million or 2% of the total worldwide annual turnover for DSPs (Digital Service Providers)
NIS 2 Directive Mitigates Third-party Risk in the Supply Chain
The supply chain is a focus of cyberattacks. Supply chain risk management (SCRM) seeks to understand and balance the differences between existing security controls, potential vulnerabilities, regulation requirements, and business goals. The NIS 2 Directive takes this cybersecurity risk into account by requiring stringent risk management of the supply chain.
NIS 2 Directive Brings Stricter, Risk-based Security Requirements
A risk-based approach to security underpins the new security obligations of the NIS 2 Directive. This approach is in line with other regulations such as the General Data Protection Regulation (GDPR). Incident response and crisis and risk management techniques play a key role in compliance with NIS 2 and should be a basis for implementing the security measures outlined in the directive. To maintain a high level of security within essential service providers, NIS 2 requires that relevant organizations must comply with strict requirements for:
- Completing a risk assessment and having sufficient information system security policies in place
- Preventing, detecting, and responding to incidents promptly
- Crisis management and operational continuity in the case of a major cyber incident
- Ensuring the security of their supply chain
- Ensuring the security of their network and information systems
- Having policies and procedures in place that assess the effectiveness of cybersecurity risk management practices
- Using strong encryption
How Businesses Can Improve Their NIS 2 Directive Compliance Readiness
Businesses can improve their NIS 2 compliance readiness by implementing the following measures, such as:
Content-defined Zero-trust Model
Zero-trust models are based on the principle of “never trust, always verify,” limiting access to a company’s network or system to only authorised users. Authentication policies must be implemented to ensure that access is not granted unless the user has been identified by the system via multi-factor authentication (MFA) or some other verification process. A content-defined zero-trust approach should include granular access control policies and logging to enable businesses to protect their sensitive content communications from cyber and compliance risks.
Cybersecurity Risk Management
Risk management must be a central component to any organisation’s security strategy. Risk assessments should be conducted on a regular basis to identify any potential threats or vulnerabilities. Policies and controls should also be put into place to counter any identified threats. This includes both technical solutions, such as firewalls, intrusion detection systems, and antivirus/anti-malware protection, as well as nontechnical solutions such as employee security training and procedures to manage and monitor potential risks.
Multi-factor Authentication
Multi-factor authentication can be used to add an additional layer of security to user authentication. This requires users to enter two or more authentication factors, such as a username and password, in order to gain access to a system or resource. This is especially important for remote access, where an additional verification process, such as a one-time code sent via SMS or email, adds an extra layer of security.
End-to-End Encryption
End-to-end encryption is critical for protecting sensitive data that is stored or transmitted over a network. This is a process of scrambling data, making it unreadable until it is unlocked using a proper key. There are several encryption algorithms that can be used, such as AES-256 encryption. Encryption can also be used to anonymize data or to ensure that only authorized users can access it, such as via an encryption key.
Secure File Sharing
This involves implementing a secure file sharing solution to protect confidential data from being shared with unauthorized individuals. This can include the use of access control policies to only allow authorized personnel to access the data and tools to monitor which staff members are sharing files. Additionally, digital rights management (DRM) can be used to control who can open, edit, and share files, and access can be restricted based on roles and user profiles.
Secure Email
Email is often the first target for social engineering or phishing scams, so it is important to ensure that emails are secure and that any sensitive information is encrypted. Secure email solutions can help protect against unauthorized access or interception of messages, and can include encryption, digital signatures, and other security measures.
Security Training and Awareness Program
It is essential that staff are aware of proper cybersecurity practices and can recognize and avoid potential threats. This can be accomplished through security awareness training programs, which can include topics such as phishing scams, social engineering tactics, and creating strong passwords. Additionally, it is important that employees remain up to date on new security measures, best practices, and the latest threats.
Network Security Solutions
Firewalls, intrusion prevention systems, and antivirus/anti-malware solutions are all essential elements of a comprehensive network security solution. Firewalls can be used to control the flow of traffic entering and leaving the system, preventing unauthorized access. Intrusion detection systems can detect any malicious activity, such as malware, data loss, and hacking attempts, and alert administrators. Antivirus/anti-malware solutions can protect against any malicious software that might be present on the system. Additionally, an effective security strategy should also include regular system and network scans, application patching, monitoring, and testing.
Kiteworks Supports Businesses With a NIS 2 Directive Compliant Private Content Network
Kiteworks helps organizations demonstrate NIS 2 Directive compliance. How? The Kiteworks Private Content Network provides the highest levels of visibility and control of their sensitive content, including where it’s stored, who has access to it and with whom they’re sharing it. Together, these capabilities helps comply with the NIS 2 Directive’s rigorous requirements. The Kiteworks platform does this through:
Enforcing Compliance With Information System Security Policies
Kiteworks allows customers to standardize security policies across email, file sharing, mobile, MFT, SFTP, and more with the ability to apply granular policy controls to protect data privacy. Administrators can define role-based permissions for external users, thereby enforcing NIS 2 compliance consistently across communication channels.
Supporting Business Continuity
Maintain accurate records of all activities and technical data with user-friendly tracking displays, allowing audit logs to serve the dual purpose of ensuring that an organization can investigate data breaches and provide evidence of compliance during audits. In the event of a breach, this grants an organization the ability to see exactly what was exfiltrated so they can get to work immediately on disaster recovery and continue their day-to-day business while maintaining compliance.
Defining and Enforcing Basic Cyber Hygiene Practices
ISO has validated Kiteworks to effectively protect your sensitive content from cyber risk (ISO 27001), including when deployed as a cloud service (ISO 27017), and to shield your organization from damaging leaks of personally identifiable information (PII) as validated by ISO 27018. In addition, Kiteworks has a library of compliance certifications, including being SOC 2 compliant and SOC 2 certified. These certifications, along with the single-tenant architecture and multilayered hardening, validate Kiteworks’ ability to mitigate content risk with the content management system and keep your basic cyber hygiene practices within NIS 2 compliance.
Protecting Content With Encryption
Ensure volume and file level encryption of all content at rest (with AES-256 encryption) and TLS encryption in transit to protect content from unauthorized access, data corruption, and malware. Flexible encryption allows customers to use Kiteworks’ end-to-end encryption and bridge to partners with different standards such as OpenPGP, S/MIME, and TLS. Kiteworks’ secure email provides encryption and uniform security controls with an Email Protection Gateway (EPG) that ensures only authenticated users can read messages.
Establishing Access Control Policies and Asset Management
Kiteworks administrators set up granular controls to protect sensitive content and enforce compliance policies, enabling business owners to easily manage content, folders, invitations, and access controls to ensure NIS 2 compliance of all content. Access control can be further managed within compliance with geofencing, app enablement, file type filtering, and email forwarding control.
Kiteworks provides a range of features to enforce compliance with information system security policies, handle incidents with efficiency, support business continuity, manage vulnerabilities in development and maintenance, define and enforce basic cyber hygiene practices, protect content with encryption, establish access control policies and asset management, and verify users with multi-factor authentication. These features enable organizations to detect and respond to security incidents, manage vulnerabilities, and maintain compliance with NIS 2 requirements.
Businesses across the EU looking to start their journey to NIS 2 Directive compliance can schedule a custom demo to learn more about the Kiteworks platform.
Additional Resources
- Video NIS 2 Directive: Requirements, Obligations, and How Kiteworks Can Help With Compliance
- Brief Optimize File Sharing Governance, Compliance, and Content Protection
- Webinar Unlock the Power of REAL Zero Trust Through Content-based Risk Policies
- Case Study Mitigating Risk With a Single, Secure File Sharing Platform
- Blog Post Zero Trust Architecture: Never Trust, Always Verify
