
Understanding Key Aspects of Data Compliance
Data compliance has become an integral part of business, regardless of an organization’s size, industry, or geographic location.
There are several factors behind the emergence of data compliance. Ultimately, a massive growth in data volume has precipitated an increase in cyber threats and cyber attacks, which in turn have necessitated a commitment to protect customer, constituent, and patient privacy. Data compliance requires organizations to pratice proper data management for efficiency, transparency, and privacy.
But how do organizations know which standards and regulations to follow and what data compliance processes to implement? This post takes a close look at data compliance and its role in modern business, in an effort to answer those questions.
Why Data Compliance Matters
Data compliance is the process of ensuring that organizations and their systems meet legal, regulatory, and operational data requirements. It involves establishing controls in order to protect data privacy, integrity, and availability and to prevent data misuse. It also includes the development of policies and procedures that govern how organizations and individuals handle data. Companies benefit from data compliance as it helps them create and maintain efficient systems for managing data.
Companies invest in data compliance in order to protect their customers’ data and to ensure they remain in compliance with industry regulations like GDPR, HIPAA, and many others. These regulations are necessary to protect customers’ right to privacy, security, and data accuracy. Regulatory compliance, and data compliance more broadly, helps businesses achieve and maintain a reputation for being good stewards of their customers’ personal data. Data compliance, if done successfully, enables businesses to build trust with their customers, protect the company from data breaches and compliance violations which include costly penalties, fines, and long-term repercussions on business reputation.
Data compliance has practical benefits, too. Investing in data compliance can help businesses increase their efficiency and profitability. Good data compliance practices help businesses ensure their data is not only safe and secure, but also up-to-date and accurate, which helps minimize costly errors. Additionally, effective data compliance can reduce the amount of time and money businesses spend finding, correcting, and replacing data.
Some examples of data compliance include:
- Implementing policies for data storage and maintenance
- Creating data access controls
- Training employees on data privacy and security
- Establishing procedures for data sharing and transfer
- Setting up systems for data archival and disposal
- Utilizing encryption to protect data
- Establishing security reviews and audits
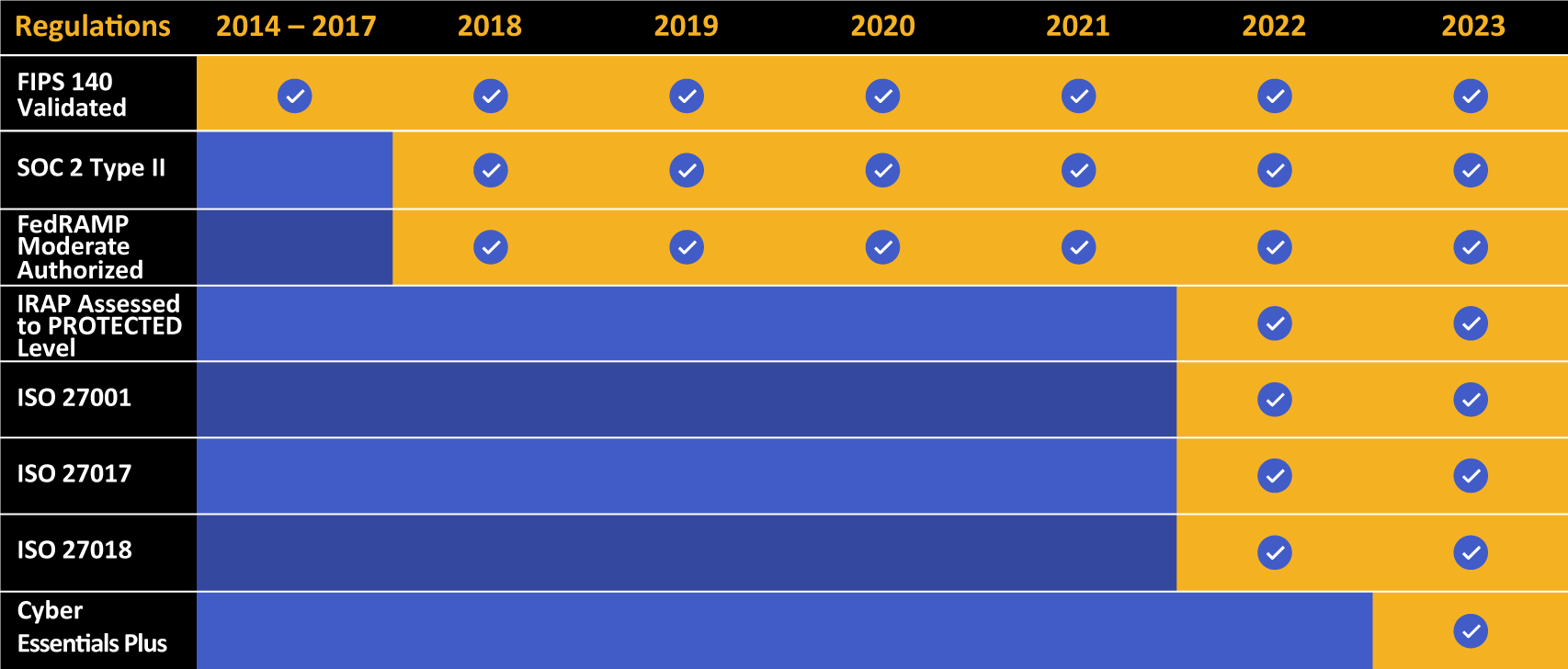
Kiteworks touts a long list of compliance and certification achievements.
Data Security Compliance: an Introduction
Data security compliance refers to a set of standards and laws that organizations must follow in order to secure their data and protect it from breaches, theft, or loss. This involves a wide array of practices and strategies, including encrypting sensitive data, providing user access controls, implementing reliable backup systems, and more. These standards and laws are often industry-specific. For example, healthcare organizations in the US must comply with the Health Insurance Portability and Accountability Act (HIPAA), which provides regulations for the use and disclosure of protected health information. Similarly, financial institutions may need to comply with the Sarbanes-Oxley Act (SOX), which includes rules for the reporting of electronic records. Compliance with data security laws is usually mandatory, and failure to comply can result in severe penalties, both financial and reputational. Therefore, organizations need to ensure that they understand the specific laws and regulations in their industry and that they have the necessary systems and processes in place to maintain compliance.
Data security compliance also involves ongoing monitoring and management. This means regularly auditing your systems and practices to ensure they’re still in line with the required standards, as well as updating your protocols as the regulations change. It’s worth noting that being compliant doesn’t necessarily mean that an organization’s data is completely secure. Compliance standards provide a minimum set of requirements, and many organizations choose to go beyond these to further enhance their data security.
Overall, data security compliance is about minimizing risk, protecting sensitive data, and meeting the regulatory standards set within your specific industry. It’s a critical aspect of managing information and can play a major role in an organization’s overall cybersecurity strategy.
How Data Security Compliance Differs From Data Compliance
While similar, data security compliance and data compliance have different focuses and objectives. Data security compliance, for example, primarily deals with how data is protected from breaches, loss, and unauthorized access. Data security compliance addresses the measures and standards that an organization implements to ensure that its data is safe and secure.
Data security compliance, once again, typically involves encrypting data, controlling user access, and establishing reliable backup systems. Data security compliance is critical for avoiding potential cyber threats and demonstrating compliance with data protection laws. Data compliance, by contrast, refers to the adherence to laws and regulations that govern the collection, storage, processing, and management of data. These rules not only cover data security but also data privacy, data sovereignty, data transparency, and more. For instance, the General Data Protection Regulation (GDPR) in the EU regulates how organizations must handle personal data of individuals, including provisions on obtaining explicit consent for data collection, providing clear information on how data is used, and giving individuals the right to access or delete their data.
So, while data security compliance focuses on the technical and operational aspects of protecting data from unauthorized access and breaches, data compliance has a broader scope and covers the all-encompassing legal, ethical, and regulatory aspects of managing and handling data. Essentially, data security compliance can be seen as part of the larger umbrella of data compliance. Both are equally important and interconnected in maintaining an organization’s overall data governance strategy.
Data Security Compliance: a Priority for Modern Businesses
Data security compliance touches every aspect of a business, from legal to reputational to operational. Hence, it is a mission-critical business obligation that can significantly impact a company’s success and longevity. Here are just a few examples of just how critical data security compliance is for organizations:
- Legal Compliance: The first and most apparent reason is legal compliance. Businesses need to adhere to various laws and regulations that mandate data protection. Non-compliance can result in heavy fines, lawsuits, and legal penalties.
- Protecting Reputation: Data breaches can cause irreparable damage to a company’s reputation. A single incident can erode customer trust, which might lead to loss of customers and revenue. In this age of information, news of data breaches spreads quickly, and rebuilding lost trust can be difficult and costly.
- Protection against Cyber Threats: With the rise in cybercrimes, ensuring data security has become a necessity. Through data security compliance, businesses can protect sensitive data from unauthorized access, theft, and breaches, thereby reducing the risk of cyber-attacks.
- Economic Considerations: Data breaches can be costly. Apart from potential fines, businesses might have to bear the costs of rectifying the breach, compensating affected customers, and even potential lawsuits. By adhering to data security compliance, businesses can avoid these hefty costs.
- Maintaining a Competitive Edge: Businesses that can demonstrate robust data security compliance tend to be more trusted by customers and partners alike, giving them a competitive edge in the market.
- Business Continuity: Data security breaches can interrupt business operations leading to business loss. Compliance with data security standards ensures smooth business operations.
- Regulatory Requirements: Depending on the industry, data security compliance might be a prerequisite for obtaining certain certifications, accreditations, or contracts, especially when dealing with government bodies or large corporations.
How Data Compliance Impacts Businesses
Once again, data compliance encompasses much more than data security compliance. Data compliance impacts how you store, transmit, and use information as part of your business operations. Think of data compliance as the intersection of consumer/patient/client data privacy and information rights against the proper business use of information that may fall under those data privacy rights.
To determine your organization’s obligations in regards to “data compliance,” you need to answer a few key questions:
- How are you protecting your data: unauthorized use or disclosure?
- How must that data be protected: through technical, administrative, or physical measures?
- How is the data used? for business or customer/client/patient services?
Security is an important component of a compliance regimen. Further, many governmental and industry standards and regulations have data privacy and protection as their focale point (e.g. GDPR, PCI DSS, etc.). Organizations must be able to demonstrate cyber risk management governance and compliance to auditors, boards of directors, executive staff, regulatory and compliance bodies, among others.
Data compliance is critical to businesses for various reasons:
- Data Compliance for Individual Rights: As covered later in the post, management of information for business purposes intersects with the rights of individuals to manage, control, and access their information. Different industries call for additional protection regulations based on other concepts of individual rights.
- Data Compliance for Ethics and Data Privacy: One of the essential facets of a data compliance framework is the ethics of maintaining user privacy. Healthcare, retail, finance, and other industries have regulations that define user privacy as sacred and foundational components of their operation.
- Data Compliance for Business Uses: Outside of data privacy from unauthorized disclosure, data compliance also intersects with proper business uses. While some data regulations are more rigorous than others, depending on where they have jurisdiction, many frameworks highlight how a business can use information and how it cannot. Some of these frameworks (like the General Data Protection Regulation [GDPR]) also specify stringent guidelines for how long information can be used and under what circumstances.
- Data Compliance for Consent: Following from the previous list item, consent is an integral part of compliance. Some frameworks require that you provide opt-out information for marketing or business use, while even more strict frameworks require that businesses get provable, documented consent.
How Different Regulations Impact Data Compliance
Not all data is created equal, and not all compliance frameworks and regulations call for the same level of data protection.
Some of the significant compliance standards and regulations impacting businesses include:
- HIPAA: Covering healthcare information for patients working with hospitals, insurance companies, or anyone related to providing healthcare, HIPAA compliance requirements strictly define compliance as pertaining to protected health information (PHI) or information related to a patient’s care or payment information related to care. Under HIPAA, businesses must never disclose PHI to third parties other than the patient without strict, documented consent. This requires well-documented third-party risk management (TPRM) policies and procedures. Likewise, that information must be protected against disclosure wherever it is—including databases, workstations/mobile devices, servers, and even during transmission between different parties. Most compliant technologies provide ways to secure information for use so that businesses don’t have to rely on encrypted email or other older technologies.
- Payment Card Industry Data Security Standard (PCI DSS): PCI compliance essentially covers credit card payments and the protection of payment information during purchases. Whereas HIPAA specifies compliance pertaining to PHI, PCI DSS focuses specifically on payment information at the point of sale, including credit card numbers, names, addresses, phone numbers, and so on. Unlike HIPAA, which the federal and state governments regulate, PCI is an invention of the major credit card networks (Visa, Mastercard, and American Express) and is enforced through penalties to noncompliant merchants or payment processors. Penalties, in this case, can call for compounding fines for each incident of noncompliance and a loss of a merchant account (which makes it difficult, if not impossible, to process credit card transactions).
- General Data Protection Regulation (GDPR): GDPR is generally considered one of the strictest information privacy laws in the world. With jurisdiction over the entirety of the European Union and several additional participating countries, GDPR calls for businesses to maintain strict controls over user data. This includes requirements for reporting on the proper use of that information (and only using consumer data based on rigorous business needs), providing easily accessible methods for consumers to gain access to their information and request its deletion, and documented consent at every point a consumer files a new consumer information request. This last requirement also calls for businesses to provide detailed reasoning to the customer for the data collection (whether for analytics, recurrent payments, email marketing, or dozens of other situations).
- California Consumer Privacy Act (CCPA): CCPA is modeled off of GDPR in many ways. Covering California residents and companies doing business in the state, CCPA defines personal information as everyday items like names, addresses, phone numbers, email addresses, and the like. CCPA defines requirements for businesses to provide opt-out measures so consumers can stop receiving or participating in business actions or stop your business from selling that information to third parties.
A critical difference between GDPR and CCPA (and many US regulations) is that GDPR is an “opt-in” law that requires companies to receive consent before doing anything with data. In contrast, CCPA and most other business regulations are “opt-out,” where your business can use consumer information until specifically told to stop.
- The Sarbanes-Oxley Act (SOX): SOX is a little different from consumer- or patient-facing regulations in that it requires companies to provide reporting and documentation about security, risk, and auditing that your company implements. In particular, SOX calls for companies to disclose their financial and safety information, specifically their security plans, policies, and implementation.
- FedRAMP: The Federal Risk and Authorization Management Program (FedRAMP) is a set of regulations that define how cloud providers protect information created or used in the service of federal agencies. Data protection for FedRAMP-compliant businesses depends on the sensitivity of that information. For example, even sensitive but publicly available information calls for specific protection measures during storage, sharing, or email. Additionally, protected information under other frameworks (PHI or payment information) increase FedRAMP requirements accordingly.
Other frameworks apply to specific companies or industries, usually developed by professional organizations or companies themselves. For example, the National Institute of Standards and Technology (NIST) developed several compliance documents for different areas of the federal government, and Adobe released the Common Control Framework (CCF) to support governance, risk, and compliance (GRC). Additionally, the International Organization for Standardization (ISO) offers hundreds of technical guidelines for security, operations, and interoperability that compliance frameworks will either borrow from or build from wholesale.
While there are specific requirements for every framework (listed above), most regulations include common security and privacy measures. These include the following:
- Encryption: All consumer, patient, or other protected data types must be encrypted with (usually) either AES-128 or AES-256 algorithms when stored in a server or with TLS 1.2+ when in transit during a file transfer.
- Email protection: Since information must be encrypted, emails are usually equally regulated. Since implementing email compliance through encryption is a challenge in user experience and business flexibility, many businesses use secure links back to internal, protected servers.
- Audit logging: Data protection almost always includes requirements for controlling how people access information and having records for system and file access events. Most compliance will consist of audit logs for how information is used, moved, and stored.
Nevertheless, you don’t have to start from scratch when preparing for compliance audits. Some preparatory steps include the following:
- Prepare in advance: If you know that you will undergo audits regularly, you should prepare ahead of time. This includes lining up documents, technical measures, and administrative reports. Even if you aren’t 100% compliant, preparing for the audit shows where you need to align your infrastructure.
- Prepare for data subject access requests: Under GDPR, consumers have the right to demand copies of all information stored and used by your company. Furthermore, you must provide this information within a reasonable period of time, usually between 30 and 45 days. Standardizing this process ahead of time can help you not only respond quickly but maintain compliance consistently.
- Use automation: In a modern world of digital collection and processing, businesses need to use automation to document, catalog, and streamline auditing and data request responses.
- Implement compliant technology: It is a basic fact at this point that businesses use cloud services to augment their operations. If you have compliance requirements, it follows that any service you implement must support those requirements.
- Training and continuing education: Your team should always have the right training to implement compliance controls within your specific infrastructure and perform audits as needed. Likewise, you must support continuing training to ensure that they are always up to speed on any compliance or technology changes. This includes a robust TPRM program.
Kiteworks Helps Organizations Achieve Data Compliance
The Kiteworks Private Content Network unifies, tracks, controls, and secures sensitive content communication. It provides comprehensive data compliance through compliance and security governance. Every confidential file sent, shared, or transferred into, within, and out of an organization is tracked and controlled.
Key capabilities in the Kiteworks platform include:
- Security and compliance: Kiteworks utilizes AES-256 encryption for data at rest and TLS 1.2+ for data in transit. Its hardened virtual appliance, granular controls, authentication and other security stack integrations, as well as comprehensive logging and audit reporting enable organizations to easily and quickly demonstrate compliance with security standards. Its out-of-the-box compliance reporting for industry and government regulations and standards, such as HIPAA, PCI DSS, SOC 2, and GDPR, are critically important. In addition, Kiteworks touts certification and compliance with various standards that include, but are not limited to, FedRAMP, FIPS (Federal Information Processing Standards), FISMA (Federal Information Security Management Act), CMMC (Cybersecurity Maturity Model Certification), and IRAP (Information Security Registered Assessors Program).
- Audit logging: With the Kiteworks platform’s immutable audit logs, organizations can trust that attacks are detected sooner and they are maintaining the correct chain of evidence to perform forensics. Since the system merges and standardizes entries from all the components, its unified syslog and alerts save security operations cetner (SOC) teams crucial time and help compliance teams to prepare for audits.
- Consent documentation: With many frameworks like GDPR calling for documented consent for collection and any data subject access request, organizations need a platform that automates that process. Kiteworks provides extensive reporting and logging of all consent forms and data requests so organizations can consistently demonstrate data compliance.
- Single-tenant cloud environment: File transfers, file storage, and user access occurs on a dedicated Kiteworks instance, deployed on premises, on an organization’s Infrastructure-as-a-Service (IaaS) resources, or hosted as a private, single-tenant instance by Kiteworks in the cloud by the Kiteworks Cloud server. This means no shared runtime, shared databases or repositories, shared resources, or potential for cross-cloud breaches or attacks.
- Seamless automation and MFT: The Kiteworks platform supports managed file transfer (MFT) automation to facilitate content transfer into and out of secure file transfer and other repositories like file shares and AWS S3.
- Visibility and management: The CISO Dashboard in Kiteworks gives organizations an overview of their information: where it is, who is accessing it, how it is being used, and if sends, shares, and transfers of data comply with regulations and standards. The CISO Dashboard enables business leaders to make informed decisions while providing a detailed view of compliance.
To learn more about the Kiteworks Private Content Network and how it delivers comprehensive data compliance capabilities, schedule a custom demo.
Additional Resources
