SOC 2 [Everything You Need To Know]
About to receive a SOC 2 audit or looking to prepare for one? We run through all the important points you need to consider before an audit.
What is SOC 2 compliance? SOC 2 is a compliance standard that checks your company’s security, availability, processing integrity, confidentiality, and privacy controls. These criteria were created by the American Institute of CPAs (AICPA) and are checked by an independent CPA or firm.
![SOC 2 [Everything You Need To Know] SOC 2 [Everything You Need To Know]](/wp-content/uploads/2022/01/SOC2-Glossary.webp)
What Is System Organization Control 2 Compliance?
The government does not mandate all security compliance frameworks. Different industries and organizations put forth specific frameworks that help address the challenges and risks that participating businesses and organizations might encounter. One of these frameworks, the SOC 2 framework, supports risk and security management for companies handling sensitive user information, primarily in the financial services industry.
While the AICPA created SOC compliance to address issues in the financial industry, there are several applications of the standard useful for many different businesses.
What Is a SOC 2 Audit?
Undergoing an audit is often called a “certification” or an “attestation,” and the report generated by an auditor attests to an organization’s compliance. If an organization chooses to undergo SOC 2 compliance audits, it must complete one of two reports:
- Type I reports describe an organization’s security and IT systems related to its suitability to meet compliance requirements.
- Type II reports detail the actual effectiveness of an organization’s systems under requirements.
The main difference is that Type I only reports the actual controls in place, while Type II attests to operational compliance within a specific period.
SOC 2 audits are based on the organization’s needs, as a general compliance achievement, as part of specific requirements under industry standards, or as a request for proposal (RFP). Audits are also divided into five “Trust Principles,” which cover specific security and privacy concerts.
Each audit includes at least one, if not more, examinations of controls and capabilities to discover if they meet the requirements of the Trust Principles.
The five Trust Principles are the following:
- Security: Security principles are all about cybersecurity, protection against breaches or unauthorized access, and maintaining system integrity. Controls expected under this principle often include encryption standards, email and file transfer requirements, software and hardware security, identity and access management, and perimeter security measures. Controls in this category include firewalls, antivirus software, and multi-factor authentication (MFA). Organizations must always undergo a security assessment no matter what else is included in an audit.
- Availability: Availability includes any and all technologies and practices that contribute to how users and employees can securely and effectively access information when needed. This includes availability to an organization’s clients—both from internal systems and as dictated by service level agreements (SLAs) with vendors.
- Integrity: It is important for digital systems to function properly and in line with the data contained therein. Systems should include controls and processing technologies that ensure that all data is complete, valid, accurate, timely, and authorized whenever it is used. System errors that can corrupt data, cause errors during collection or transmission, or create audit logs for that data do not meet integrity requirements.
- Confidentiality: Confidentiality ensures that information remains free of unauthorized disclosure at rest or during transmission. This can include transmission or other security measures related specifically to obfuscating information.
- Privacy: This principle specifically refers to the policies and procedures used to maintain users’ privacy and their personally identifiable information (PII).
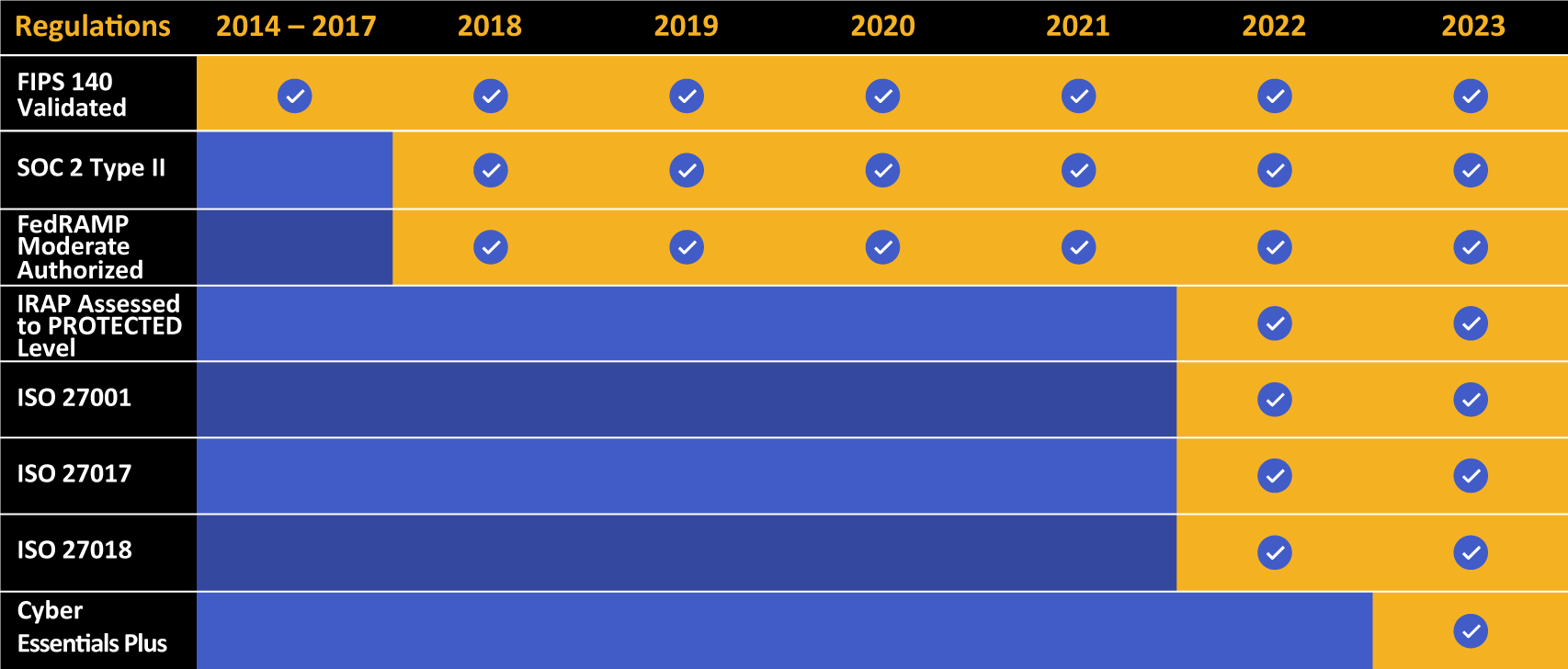
Kiteworks touts a long list of compliance and certification achievements.
What Is SOC 2 Trust Services Criteria? (TSC)
The SOC 2 Trust Services Criteria (TSC) is a framework for evaluating and reporting on the effectiveness of an organization’s controls related to security, availability, processing integrity, confidentiality, and privacy. It is a set of standards developed by the American Institute of Certified Public Accountants (AICPA) and is used by service providers to demonstrate their commitment to providing secure and reliable services to their clients. The TSC framework is organized into five categories, each of which contains a set of criteria that must be met to achieve compliance:
- Security: focuses on protecting information and systems from unauthorized access, both physical and logical
- Availability: ensures that the systems are accessible and available for use as needed
- Processing Integrity: ensures that data is processed accurately, completely, and timely
- Confidentiality: focuses on protecting confidential information
- Privacy: ensures that personal information is collected, used, retained, and disclosed in accordance with applicable laws and regulations
Understanding SOC 2 Requirements
SOC 2 is an auditing standard used to provide assurance about the security and controls of an organization or company’s information technology (IT) infrastructure, which is the internal system the company uses to store, process, and transmit its data. This standard is designed to provide assurance over certain elements of IT and security to users, customers, and shareholders of the company. It is important to note that SOC 2 is not a certification, and a company must obtain an independent audit of their system to obtain this assurance.
The five trust services principles (again: security, availability, processing integrity, confidentiality, and privacy) must be met in order to achieve SOC 2 compliance Each of these principles requires a company to have processes and controls in place to protect the data they handle. For example, the security principle requires companies to have a strong authentication process and prevent unauthorized access to their systems. The availability principle requires them to ensure their systems are always operational, and the processing integrity, confidentiality, and privacy principles require them to ensure the integrity, accuracy, and privacy of the data they store and transmit.
Overall, the SOC 2 audit is an important tool for companies to use in order to provide assurance to their users and customers that their IT system is secure and meets certain standards. It is also important for them to understand and meet the five trust services principles in order to achieve SOC 2 compliance.
Why Should I Pursue SOC 2 Compliance?
SOC 2 was developed primarily for organizations in financial services. However, many other businesses choose to pursue SOC 2 for a number of reasons.
Note that compliance is not a legal requirement for any business. For some financial businesses (like CPA firms), it serves as an industry requirement.
Some reasons for pursuing compliance include the following:
- Strong, Proven Security Posture: While many businesses comply with security regulations as part of legal or industry requirements, many also look to frameworks like SOC 2 to help them better position their infrastructure in the face of modern, evolving threats. Undergoing an audit adds an additional layer of attention and assessment to an organization’s security policies and procedures.
- Reputation and Trustworthiness: One of the major reasons businesses undergo audits is that the audit can attest to a business’s commitment to protecting data . A certification can demonstrate to customers, potential clients, and business partners that an organization values security and privacy.
- Implementing Risk Management: Since 2017, SOC 2 security requirements have included a risk assessment. This is not just a hoop to jump through—risk management is a critical part of modern security, and organizations that want to take proactive measures can use compliance as a guideline.
- Reduction of Costs: According to a report from IBM, an average data breach in the United States cost the victims $4.24 million. It goes without saying that the support and thoroughness of an audit will definitely save a company money in damages and remediation. Furthermore, there is no restoring a bad reputation, and compliance can prevent breaches that lose customers and clients.
- Complimentary Compliance: If an organization is preparing to meet compliance standards in another industry (like HIPAA or ISO 27001), then certification can provide a good starting point.
What Is a SOC 2 Report?
When an assessor completes an audit, they will compile a report that attests to the appropriateness of an organization’s technical and organizational controls. Only registered CPAs with security backgrounds can conduct audits and provide reports.
A SOC 2 report will typically contain the following sections:
- An Assertion of Management: This section, completed by each organization, attests to the controls, processes, products, and services that fall under and meet compliance regulations.
- Independent Service Auditor’s Report: Contains the scope, audit assessment, rating of systems and controls, and the auditor’s opinion overall. The auditor will assign certain ratings to an organization based on a passed, failed, or incomplete assessment.
- System Descriptions: The comprehensive section where the auditor details their assessments and descriptions of the organization’s systems based on the types of audits they deployed.
- Related Trust Service Criteria and Controls: This lengthy section includes the development of assessments related to the other Trust Service categories.
- Information Not Covered by Report: Future plans, noteworthy information for customers and clients, or other data that is not under audit but is important for public consumption.
What Are SOC 1 and SOC 3?
The above discussion about SOC 2 raises the question, “What about SOC 1 and SOC 3?” These reports also exist, and they perform radically different functions.
- A SOC 1 report outlines business processes, IT controls, and business and technical objectives related to financial reporting. More importantly, this report can include associated risks and vulnerabilities related to these processes and controls. While this is not a security or technical audit, it is an attestation, with an audit, that an organization is operating with transparency and full disclosure. This report is often requested by clients or stakeholders requiring organizations to attest their risk profile and business operations, typically when they are financial in nature.
- A SOC 3 report is similar to the other reports in that it is an attestation of an organization’s security, availability, integrity, confidentiality, and privacy. However, SOC 3 audits contain much less information and usually omit the sections containing lists of controls and assessments. It usually contains the auditor’s opinion, some findings, and the overall outcome of their audit.
Want to Learn More About SOC 2?
SOC 2 is a prominent security framework even outside of the financial industry because it provides organizations with an additional layer of security and cyber hygiene. When it comes to sensitive content moved into, out of, and within your organization, SOC 2 compliance is an important consideration.
To learn more about how Kiteworks unifies, tracks, controls, and secures sensitive content in compliance with SOC 2, check out our webpage that provides an overview. Or, simply schedule a demo of Kiteworks to see the platform in action–across email, file sharing, file transfer and automation, application programming interfaces (APIs), and web forms.

