FIPS Compliance Requirements Overview
What are the requirements for FIPS compliance, and how do FIPS, NIST, and FISMA relate? We’ve covered all the important points for a complete FIPS overview.
What does FIPS stand for? FIPS stands for Federal Information Processing Standards, and it is a program overseen by NIST and the Department of Commerce that requires specific security standards for data and encryption.

What Are FIPS and Why Are They Important for Cybersecurity?
Federal Information Processing Standards (FIPS) are security standards for federal and defense cybersecurity compliance, specifically focusing on data encryption.
Encryption is a necessary part of almost every cybersecurity compliance framework, including the National Institute of Standards and Technology Cybersecurity Framework (NIST CSF), and it is no different for government agencies and their contractors. Encryption, including email encryption, protects data from unauthorized viewing either at rest or in transit and serves as one of the major bulwarks against data theft.
Organizations implementing encryption should not use outdated or compromised algorithms that fail to protect data meaningfully. To support modern, effective encryption for protected data under use by government agencies, and even private organizations, the U.S. government distributed these standards for public use. These standards focus on several different topic areas, primarily encryption and cryptography, and are overseen by the National Institute of Standards and Technology (NIST). These regulations serve an essential purpose of filling gaps for encryption standards when no acceptable industry standards exist for a particular application.
Are these regulations always required for government agencies? Not necessarily. Some federal compliance standards will not include any processing standards, while others may include several. Additionally, these standards are available for use by anyone, and often private organizations adopt these standards above and beyond their own industry compliance requirements.
How Are FIPS Developed and Maintained?
The development and maintenance of Federal Information Processing Standards (FIPS) follow a structured life-cycle managed by the National Institute of Standards and Technology (NIST), under the authority of the Secretary of Commerce.
The process begins with identifying the need for a standard, often driven by federal agency requirements, emerging technologies, or evolving security threats. NIST then typically issues a proposal or draft standard, opening a public comment period where feedback is solicited from federal agencies, industry stakeholders, academia, and the public.
All submitted comments are reviewed, and NIST may revise the draft standard accordingly. After addressing feedback and ensuring the standard meets its objectives, NIST publishes the final FIPS publication.These standards are subject to periodic review, typically every five years, to ensure they remain relevant and effective.
Based on this review, NIST may reaffirm, revise, or withdraw a standard. For example, the Data Encryption Standard (DES), FIPS 46-3, was withdrawn due to vulnerabilities, while FIPS 140-2 is currently being superseded by the updated FIPS 140-3 to align with international standards like ISO/IEC 19790 and address modern cryptographic needs.
Understanding this life-cycle is crucial for organizations aiming for long-term FIPS compliance, as it helps anticipate changes and plan technology roadmaps accordingly.
Who Needs to Be FIPS Compliant?
Organizations or companies that must follow the Federal Information Processing Standards (FIPS) are typically those that handle confidential or sensitive data. This includes federal agencies, institutions that receive federal funding, and private sector organizations that must comply with specific regulations, such as the Health Insurance Portability and Accountability Act (HIPAA). Other organizations may benefit from FIPS compliance, such as those that handle personal information, banks, healthcare organizations, and financial institutions.
What Does It Mean to Be FIPS Compliant?
FIPS compliance means a product meets all the necessary security requirements established by the U.S. government for protecting sensitive information. To be FIPS-compliant, a product must adhere to rigid standards, pass rigorous testing, and be certified by NIST.
What Are Current FIPS Standards?
There are several updated FIPS in practice today. These FIPS cover different encryption standards and can be used together or individually to shore up encryption standards or as part of larger compliance frameworks.
Some of the current FIPS in practice right now include the following:
FIPS 140-2
Initially published in 2001, FIPS 140-2 is perhaps one of the more widespread implementations of cryptographic controls. It defines appropriate levels of cryptography to protect federal data and assure that cryptographic modules produced by private organizations can meet those levels of protection. Furthermore, FIPS 140-2 breaks down cryptographic security into four distinct levels, each with increasing privacy, data isolation, and management controls. This standard does not refer to specific encryption algorithms but, due to evolving security challenges, an appropriate encryption algorithm would need to meet the criteria in the document. Currently, AES-128, AES-192, and AES-256 all meet standards.
Often, documents refer to FIPS 140-2 compliance. This does not refer to an organization being compliant, but rather the cryptography an organization has implemented as part of its products or systems.
FIPS 140-3: Modernizing Cryptographic Module Validation
FIPS 140-3 represents the latest evolution in standards for validating the effectiveness of cryptographic modules, superseding FIPS 140-2. Its primary goal is to align U.S. government requirements more closely with international standards, specifically ISO/IEC 19790:2012.
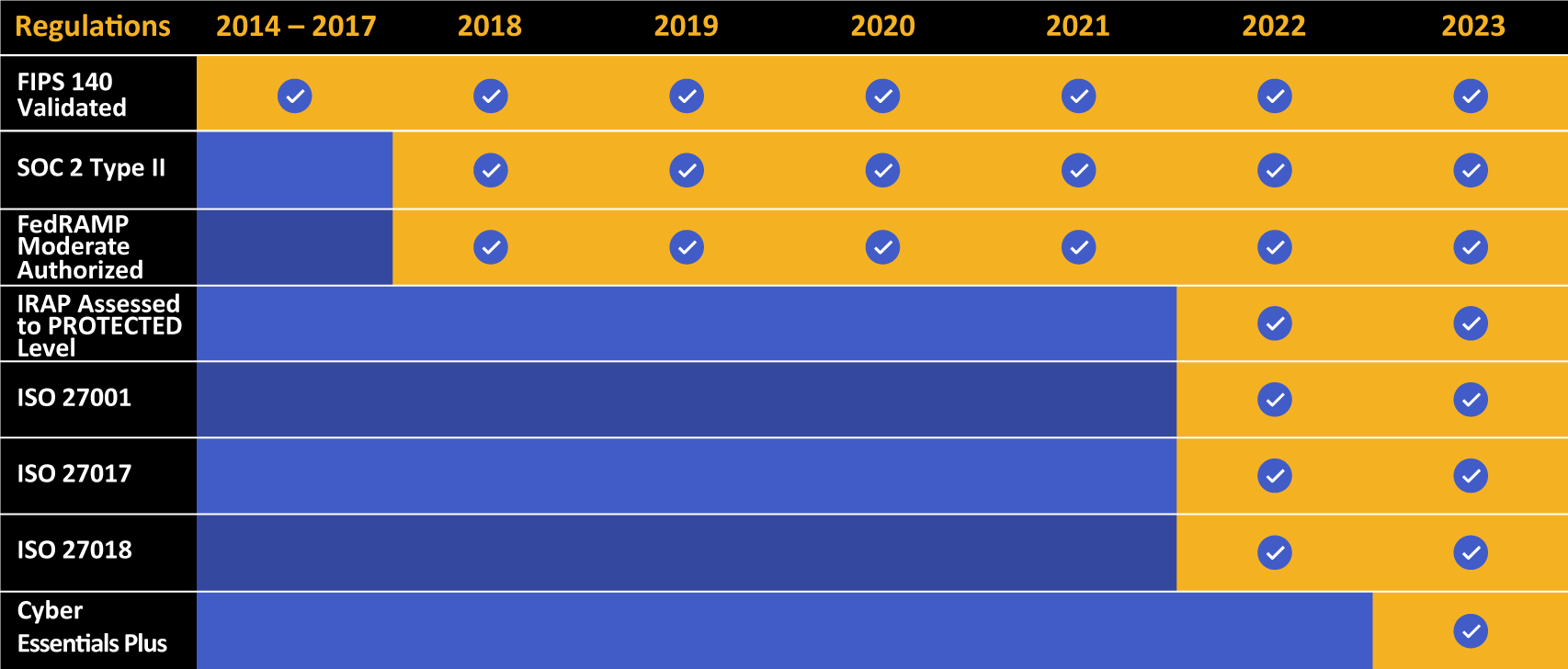
Kiteworks offers FIPS 140-3 Level 1 validation. Learn more about Kiteworks and FIPS-validated encryption.
Key changes from FIPS 140-2 include modified requirements across all security levels, updated authentication standards, and a greater emphasis on non-invasive attack testing. FIPS 140-3 also introduces the concept of “algorithm agility,” encouraging modules to support transitions to new cryptographic algorithms over time.
The transition period is well underway; NIST stopped accepting FIPS 140-2 submissions for new validation certificates in September 2021, although existing FIPS 140-2 certificates remain active for up to five years from their validation date.
Organizations seeking new solutions requiring FIPS compliant encryption should prioritize selecting FIPS 140-3 validated modules. For systems currently relying on FIPS 140-2 validated products, organizations must plan for migration to FIPS 140-3 validated alternatives before the relevant 140-2 certificates expire to maintain FIPS compliance.
How Do You Become Compliant With FIPS 140-2?
To become compliant with FIPS 140-2, organizations must employ cryptography-based security products and services that have been validated as compliant with the specific requirements outlined by NIST. This includes purchased products and services, as well as any in-house developed solutions. To become compliant, organizations must also maintain effective security policies and procedures, and use only approved cryptographic algorithms and approved cryptographic keys. Lastly, they must also follow applicable government regulations and laws that may be applicable to their specific industries.
Recently, FIPS 140-3 was approved. However, it is still being implemented in government settings, and as such, FIPS 140-2 is still the standard most referenced by compliance documents.
FIPS 180-4
FIPS 180-4, originally published in 2008 and recently updated in 2015, specifies appropriate hash algorithms to develop digests of messages. In cryptography, a “digest” is an alphanumeric string created by hashing a piece of information. This digest is unique to the content in question and will only change if the core content changes. These digests are a critical part of ensuring the integrity of transmitted information.
FIPS 186-4
Published in 2013, FIPS 186-4 defines a suite of algorithms for developing digital signatures. Much like hashing, digital signatures can help authenticate that data has not been modified. Furthermore, signatures can also be used to verify the identity of the sender. This publication defines signature algorithms using three techniques: Digital Security Algorithm (DSA), Elliptic Curve Digital Signature Algorithm (ECDSA), and Rivest–Shamir–Adleman (RSA).
FIPS 197
FIPS 197 defines the Advanced Encryption Standard (AES). AES uses symmetric block cipher techniques for encryption with the capability of generating cryptographic keys of various sizes (128, 192, and 256 bits). Larger cryptographic keys correspond to more complex encryption standards. AES encryption standards are considered FIPS 140-2 compliant and more than suitable for many private sector compliance requirements.
FIPS 198-1
Published in 2008, FIPS 198-1 defines a hash key authentication method using shared secret keys called message authentication codes alongside cryptographic hash functions called hash message authentication codes.
FIPS 199
FIPS 199 is a 2004 publication that defines how IT experts and technology leaders should organize federal systems based on their relative levels of required confidentiality, integrity, and availability. The impact levels define how critical the information contained in these systems is and how damaging the loss of that data would be to agencies and constituents. FIPS 199 breaks information systems into low, moderate, and high impact levels, each with increasing security requirements. Other frameworks, namely FedRAMP, rely on FIPS 199 for their own compliance and security level designations.
FIPS 200
FIPS 200 is a 2006 publication that superseded SP 800-26 and defines minimum security requirements for government agencies under the Information Technology Management Reform Act of 1996 (FISMA). It serves as a cornerstone, along with NIST SP 800-53, for national cybersecurity, including the Cybersecurity Framework (CSF) and the Risk Management Framework.
FIPS 201-2
Released in 2013, FIPS 201-2 is a set of standards used to verify the identities of federal employees and contractors. Identification and authentication are challenging practices, and this document introduces requirements for practices like physical identification, biometric authentication, and identity proofing. It also contains standards (or refers to outside standards) for practices like securing authentication information.
FIPS 202
FIPS 202 defines Secure Hash Algorithm 3 for hashing, digital signatures, and other cryptographic applications. This hash algorithm supplements the Secure Hash Algorithms outlined in FIPS 180-4 to support strong information authentication and integrity maintenance.
These rules are not set in stone. As technology evolves and new security challenges arise, standards are often withdrawn, revised, and replaced with more advanced standards. For example, FIPS 46-3 (Data Encryption Standard) was withdrawn in 2005 because it no longer met the minimum requirements expected in federal security. As publications are withdrawn, new ones are typically added to address the limitations.
Windows FIPS Mode: Implementation Considerations
Windows includes an optional security setting known as “FIPS mode” or more formally, “System cryptography: Use FIPS compliant algorithms for encryption, hashing, and signing.”
When enabled, typically via Group Policy or a local security policy setting, it restricts the operating system and associated components to using only cryptographic algorithms that have been validated against FIPS 140 standards.
It’s crucial to understand that enabling this mode does not make the entire Windows system FIPS 140 certified; rather, it ensures that specific cryptographic operations performed by the OS utilize FIPS-validated modules.
A common misconception is equating this mode with full system FIPS compliance. Enabling FIPS mode can sometimes cause compatibility issues with older applications that rely on non-FIPS-approved cryptographic algorithms, potentially leading to application failures. While performance impacts are generally minimal, they can occur.
Organizations considering activating FIPS mode, particularly in government or highly regulated environments requiring strict FIPS security, should conduct thorough testing across all critical applications before widespread deployment. It should primarily be enabled only when explicitly required by contract or regulation, ensuring it doesn’t inadvertently disrupt necessary operations.
What’s the Difference Between FIPS 140-2 and FIPS 197?
FIPS 140-2 is the standard for cryptographic modules established by NIST. It establishes the security requirements that must be met for a cryptographic module to be certified for use in certain secure applications. FIPS 197 by contrast is the specific standard for the Advanced Encryption Standard (AES), setting out the standard for the encryption and decryption of electronic data using the AES algorithm. It is a subset of FIPS 140-2, used to specify only one type of cipher and its associated parameters.
What Are FIPS Compliance Requirements?
The truth is that compliance can mean a lot of different things, and these things can change over time. More often than not, any compliance frameworks with specific encryption standards will refer to a publication. For example, almost all government compliance standards include one or more requirements (often FIPS 140-2 and some include FIPS 199) to help define different levels of compliance.
Compliance often only applies to certain parts of a compliance framework. An organization may never actually worry about compliance for itself, but it may look for technology vendors or products that adhere to some specifications. For example, a business in an industry that requires certain types of encryption may purchase and use FIPS 140-2 compliant products and services.
FIPS Compliant vs. FIPS Certified
FIPS compliant means that a product or system meets the requirements outlined in a FIPS publication. The manufacturer of the product or system has declared that their product or system meets the FIPS standards. However, no independent testing or verification is required for a product or system to claim FIPS compliance.
FIPS certified, by contrast, means that a product or system has undergone independent testing and verification by a NIST-accredited testing laboratory. If the product or system meets all the requirements outlined in a FIPS publication, it can be certified by NIST as compliant. Therefore, FIPS certification provides a higher level of assurance that a product or system meets the FIPS standards.
Consider FIPS Compliance and Compliant Technology
FIPS is not just for government agencies. The techniques and technologies outlined in these documents are useful for private organizations as well. Many choose to follow guidelines to offer clients strong technology or IT infrastructure to protect customer data.
Check out more about Kiteworks and FIPS compliance. To learn more about how Kiteworks is FIPS compliant and provides comprehensive governance for content moving into, within, and out of your organization, schedule a demo.


