FIPS Compliance: An Essential Component for Secure File Sharing
FIPS 140-3 compliance ensures that any cryptographic technology being used to protect sensitive information meets specific security requirements that have been tested and validated by NIST. FIPS 140-3 compliance also provides a level of assurance to customers and partners that their information is being protected by reliable and secure cryptographic technology. Kiteworks offers a FIPS 140-3 Level 1 validated module for secure file sharing and secure file transfer, available in both on-premises and hosted deployments. All data in transit is encrypted, featuring TLS 1.3, with cryptographic algorithms and FIPS-validated cipher suites. Algorithms for symmetric and asymmetric message authentication and hashing are also covered.
FIPS Compliance: Secure Data Sharing and Transfers With Advanced Encryption
While encryption provides a basic level of protection, advanced encryption provides a higher level of security and is typically used for securing highly sensitive data that, if leaked, could be catastrophic. FIPS 140-3 validated solutions employ advanced encryption techniques like key stretching, salting, and robust algorithms such as AES-256 and RSA 4096, ensuring superior data protection. The Kiteworks Private Data Network secures sensitive email and file attachment data with AES-256-bit encryption at rest and TLS 1.3 encryption for data in transit and every file shared is encrypted with its own unique encryption key. In addition, organizations have sole ownership of their encryption keys and rotate those keys whenever they want; Kiteworks cannot access any organization’s data.

FIPS Compliance: Meet Government Security Standards and Stay in Good Standing With Government Agencies
If you need to comply with FedRAMP, NIST 800-171, or CMMC 2.0, you must use FIPS 140-3 certified encryption. Why? FIPS 140-3 validated encryption assures CUI remains confidential and minimizes the risk of data breaches, legal, and financial penalties. When government contractors use Kiteworks’ FIPS 140-3 certified Private Data Network, they meet critical federal security standards for data security. This means the data they send, receive, share, and collaborate on is encrypted and secure, preserving CUI and mitigating the risk of a data breach or cyberattack. And because Kiteworks is FIPS 140-3 certified, government contractors who use Kiteworks take a step closer to demonstrating compliance with FedRAMP, NIST 800-171, and CMMC 2.0.
FIPS Compliance: Protect CUI When Sharing It With Partner Agencies and Constituents
It is critical for government agencies to use a FIPS 140-3 certified file sharing solution when sharing CUI with partner agencies and constituents, as it ensures that the data remains secure and confidential during transit and at rest. FIPS 140-3 certification, a trusted industry standard, assures partner agencies and constituents that their sensitive data is secure against unauthorized access, alteration, or disclosure, complying with regulatory frameworks and best practices. Kiteworks’ FIPS 140-3 certified Private Data Network provides government agencies with better control over their CUI, including the ability to set permissions and access controls, as well as track and monitor user and file activity. This helps public sector organizations identify potential security threats and take proactive measures to protect their private citizen constituents and prevent exposure of valuable CUI.

FIPS Compliance: Show Clients, Consumers, and Patients Their Privacy Is a Top Priority
Many industries, such as healthcare and financial services, require organizations to ensure patient and client privacy. When these and other businesses use FIPS 140-3 validated encryption, they protect their customers’ privacy, and also demonstrate compliance, avoiding costly fines and litigation. FIPS 140-3 certification also requires that cryptographic modules have auditing and monitoring capabilities to track and report security events. Businesses that use Kiteworks’ FIPS 140-3 certified Private Data Network leverage these and other capabilities to showcase their commitment to data security and customer privacy, build trust with customers, and enhance their positioning in the marketplace. Kiteworks’ extensive security, monitoring, and reporting capabilities enable organizations to protect their file and email communications in transit and at rest, set role-based permissions and access controls, track and monitor user activity, and finally, demonstrate compliance with GDPR, HIPAA, GLBA, PCI DSS, and other data privacy regulations.
FIPS Compliance: More Than Just a Certification
FIPS compliance is not just a regulatory requirement but a strategic advantage for organizations aiming to enhance their data security posture. FIPS 140-3 compliance is in fact considered a best practice. Organizations that demonstrate FIPS compliance achieve the highest levels of data security, assurance, and dependability. They protect the data they share with advanced encryption. They protect the data they store with role-based permissions and access controls. They track and monitor user activity. As a FIPS 140-3 certified solution, Kiteworks has been independently evaluated for security. Using Kiteworks’ FIPS 140-3 compliant platform for secure file sharing and secure file transfer allows organizations to build trust with customers and gain a distinct advantage in a competitive marketplace, as customers are more likely to do business with organizations that can demonstrate their commitment to data security.
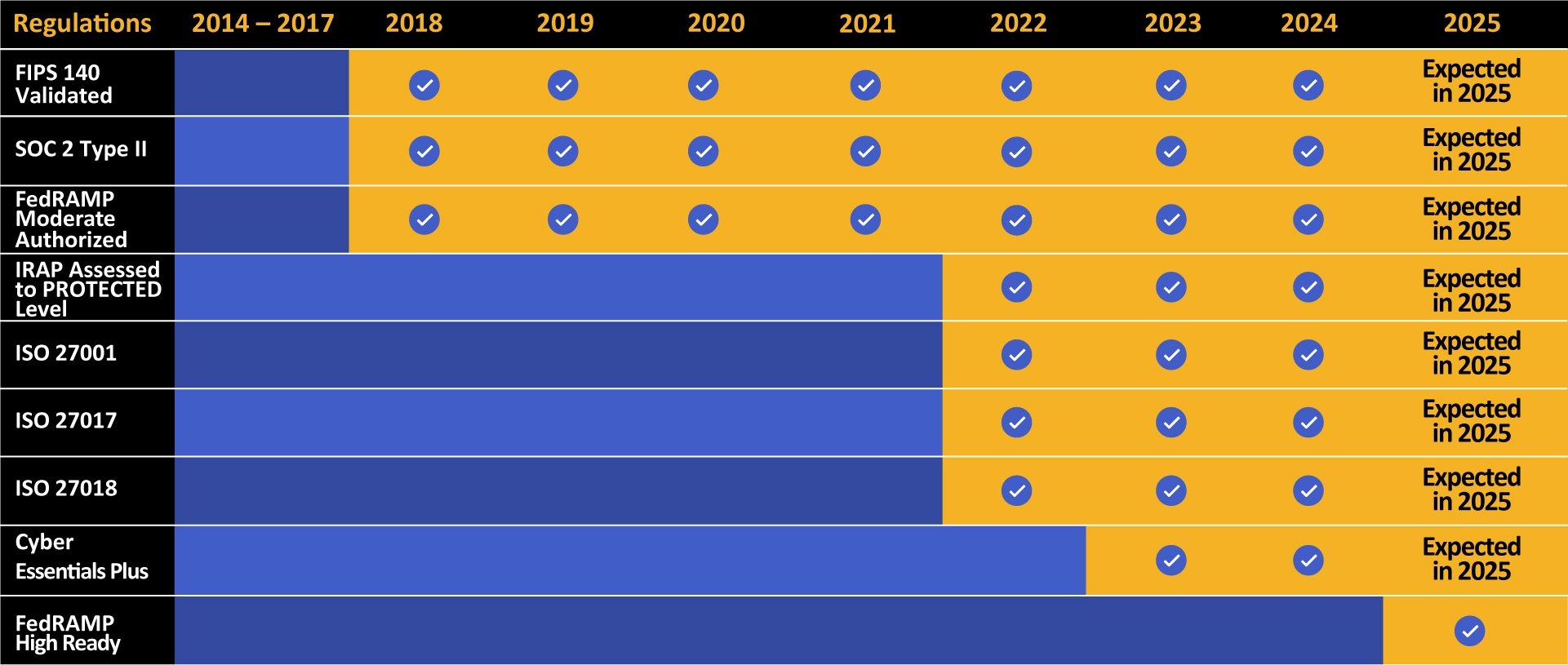
Kiteworks is committed to maintaining a robust portfolio of compliance and certification achievements, underscoring our dedication to data security and privacy.
FIPS Compliance FAQs
Yes, if you’re work requires FedRAMP, NIST 800-171, or CMMC compliance, FIPS 140-3 certified encryption is mandatory for protecting Controlled Unclassified Information (CUI). Government contractors must use validated encryption to minimize data breach risks and avoid legal and financial penalties. The Kiteworks Private Data Network features FIPS 140-3 Level 1 validated encryption, including AES-256-bit encryption at rest and TLS 1.3 for data in transit, helping you and other contractors meet critical federal security standards for CUI protection.
FIPS 140-3 validated encryption uses cryptographic modules that have been independently tested and certified by NIST, ensuring they meet specific security requirements. Regular encryption may use the same algorithms but lacks third-party validation and auditing capabilities. The Kiteworks Private Data Network features FIPS 140-3 Level 1 validated encryption, providing advanced encryption with AES-256, unique encryption keys for every file, sole customer ownership of encryption keys, and comprehensive auditing capabilities that regular encryption solutions don’t guarantee or validate.
Yes, FIPS 140-3 validated encryption ensures personally identifiable and protected health information (PII/PHI) receive the highest level of cryptographic protection while supporting HIPAA requirements. Healthcare organizations using FIPS validated encryption demonstrate commitment to patient privacy, avoid costly fines, and build patient trust. The Kiteworks Private Data Network features FIPS 140-3 Level 1 validated encryption, providing role-based access controls (RBAC), comprehensive audit logs, and secure collaboration like Kiteworks secure email, Kiteworks secure file sharing, Kiteworks secure web forms, and secure secure MFT that protect patient information in transit and at rest while enabling compliant collaboration with partners, insurers, and other healthcare providers.
Yes, FIPS 140-3 validated encryption supports multiple compliance frameworks including GLBA, PCI DSS, and SOX requirements for protecting sensitive financial data. FIPS certification provides the cryptographic foundation needed for comprehensive data protection programs. The Kiteworks Private Data Network features FIPS 140-3 Level 1 validated encryption, enabling financial institutions to protect your clients’ data, your communications with clients, transaction data, and regulatory filings while demonstrating compliance across multiple frameworks through validated encryption, access controls, and detailed audit logs.
FIPS encryption isn’t necessarily stronger algorithmically than other types of encryption, but it provides verified implementation and independent validation that other encryption lacks. The key difference is assurance. FIPS modules undergo rigorous testing, auditing, and continuous monitoring requirements that standard encryption doesn’t guarantee. The Kiteworks Private Data Network features FIPS 140-3 Level 1 validated encryption, ensuring cryptographic modules meet strict security standards with validated key management, tamper resistance, and comprehensive audit capabilities. This third-party validation provides confidence that encryption is properly implemented and maintained, reducing implementation vulnerabilities.
FEATURED RESOURCES

2025 Managing Private Content Exposure Risk Forecast Report: Highlights




