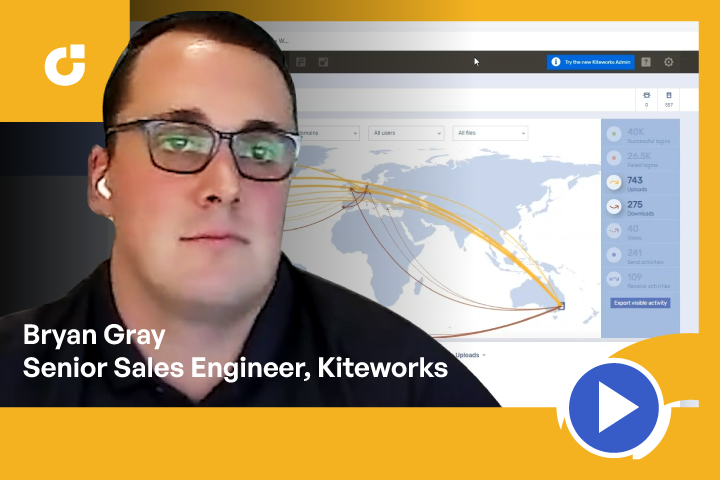
See All Data Exchanged with Third Parties
CISO Dashboard | Unified Visibility
- Visualize all sensitive information entering and leaving the firm
- Understand who’s sending what to whom, when, where and how
- Dynamically track the inventory of digital assets in motion
- Detect suspicious activity and take action on anomalies
- Pass audits and comply with industry regulations
- Create custom dashboards and reports in your SIEM
Inspect Every Communication for Complete Compliance and Control
Real-time Inspection | Unified Visibility
- The more you see, the stronger your defense
- Apply policy, investigate incidents, isolate threats and formulate responses
- Leverage user, app, device, network, protocol and file data
- Automatically respond to failed DLP, ATP, IDS, and logins
- Manually drill down to fine-grained transaction details

Detect Anomalies to Prevent Breaches Before They Happen
Security Analytics | Unified Visibility
- Analyze behavior and data, not just traffic and packets
- Aggregate and analyze transactions across communication channels
- Establish baselines to separate legitimate communications from leaks and threats
- Automatically detect threats with advanced machine learning
- Create alerts to respond rapidly to incidents in real-time
Centralized Reporting Across Communication Channels
Consolidated Syslog | Unified Visibility
- Normalized logging across all communication channels, including email, file sharing, mobile, MFT, SFTP, etc.
- Detailed, trusted audit logs lay the foundation for threat prevention and compliance
- Preserve all files, versions, emails, and activity traces for litigation
- Feed your SIEM with clean, pre-correlated log data
- Analyze historical data for continuous improvement
Frequently Asked Questions
Organizations benefit greatly by having visibility into the location of all their files. This visibility allows organizations to enforce policies to protect sensitive information and maintain data governance. By knowing where all files—especially files containing sensitive data like PII, customer information, and intellectual property—are located, organizations can ensure data integrity, prevent unauthorized access, implement appropriate security measures, and adhere to data privacy regulations and standards. Additionally, file visibility streamlines collaboration by enabling teams to locate and access the most up-to-date files, improving productivity.
File visibility plays a crucial role in helping organizations protect their sensitive data and demonstrate compliance with data privacy regulations and standards. By monitoring who is accessing, downloading, uploading, editing, or sharing files, organizations can proactively detect and respond to suspicious activities and prevent potential data breaches. With file visibility, organizations can also enforce access control policies, ensuring that only authorized individuals have access to sensitive data. Furthermore, file visibility enables organizations to identify files containing sensitive data and apply appropriate classification, encryption, and access measures. This ensures that sensitive data remains safeguarded throughout its life cycle, reducing the risk of exposure or misuse.
With comprehensive visibility into where files are stored, organizations can provide evidence of data protection measures, facilitate regulatory audits, and demonstrate their commitment to compliance. IT security, risk, and compliance professionals leverage comprehensive visibility to generate detailed audit logs and reports showing the organization has applied the necessary safeguards and controls to protect sensitive data. In the event of a security incident, file visibility facilitates incident response and investigation efforts, helping organizations assess the impact, report the incident to regulatory bodies, and take necessary remedial actions.
Unified file visibility can indeed help identify insider threats and data leaks. By monitoring user behavior, tracking file interactions, and analyzing user activities across communication channels, unified visibility enables organizations to identify anomalous or suspicious behavior that may indicate insider threats or data leaks. This includes unauthorized access attempts, unusual data transfers, abnormal file sharing patterns, or other indicators of potential data breaches. Additionally, unified file visibility allows organizations to enforce data loss prevention (DLP) policies and monitor data movement to detect potential data leaks.
Organizations can leverage unified file visibility to improve their overall security posture in several ways. First, unified file visibility enables comprehensive monitoring and analysis of data interactions across multiple communication channels. By aggregating and correlating data from different sources, organizations gain a holistic view of their security landscape, identifying vulnerabilities, detecting threats, and enabling proactive incident response. Second, unified file visibility helps organizations streamline their security operations by providing centralized reporting and analysis capabilities. This allows security teams to identify patterns, analyze historical data, and continuously improve their security measures.
FEATURED RESOURCES
15 Risks of Private Content Exposure You Need to Know About in 2023 

15 Risks of Private Content Exposure You Need to Know About in 2023
Microsoft 365 Purview Comparison to Kiteworks
Microsoft 365 Purview Comparison to Kiteworks
Customer Use Cases: Kiteworks Private Content Network Innovations