
Provide Litigation Support
Legal holds and law enforcement requests require businesses to collect, review, and produce electronic documents and data. With Kiteworks, organizations preserve and protect all data for litigation. Collect data sent or received through all file communication channels. Archive every file, version, email, and activity trace. Integrate legal hold archives with eDiscovery systems via REST APIs. Maintain chain of custody, and prove it with an audit log of all administrative, access, and transfer activities.
Demonstrate Regulatory Compliance
Nearly every organization must comply with some form of data privacy regulation or standard, including GDPR, HIPAA, CCPA, PIPEDA, ISO 27001, and others. They must demonstrate to auditors and regulators where all PII and PHI is stored and who has access to it. Role-based policies ensure that only authorized personnel can access sensitive files and folders, and all file activity—who sends what to whom, when, and how—is tracked via an immutable audit log to demonstrate adherence to legal and regulatory requirements.
LEARN MORE ABOUT ACHIEVING REGULATORY COMPLIANCE WITH SECURE FILE SHARING


Assist in Internal Investigations
In the event of suspected misconduct, organizations need efficient search, preservation, and analysis of electronic communications and documents to help uncover evidence, support fact-finding endeavors, and ensure a defensible investigation process. Kiteworks secure data access provides a single view to all connected systems like ECMs, file shares, and enterprise applications to streamline identification, preservation, and retrieval of relevant electronically stored information (ESI). Cut through large volumes of data with advanced search and filtering functions. Export all emails to archiving systems automatically via SMTP. Export audit logs of all file activity, including file access, access control changes, privilege changes, and failed and successful logins, into any SIEM solution that reads syslogs.
Protect Intellectual Property
Intellectual property (IP) is the lifeblood of many companies and therefore requires the highest levels of protection. Kiteworks helps organizations safeguard their intellectual property rights with advanced DRM capabilities. Set and enforce who can access sensitive data according to individual needs and roles. Add an additional layer of security with multi-factor authentication. Send watermarked files, file previews, or view-only files. FIPS 140-2 validation and end-to-end encryption mean IP at rest and in transit meets the highest levels of security and confidentiality.


Respond Quickly to Security Incidents
eDiscovery plays a crucial role in identifying compromised data, assessing the extent of the breach, and analyzing affected systems or accounts so organizations respond promptly, meet legal obligations, and gather evidence for potential litigation. Kiteworks enables organizations to analyze behavior and data, not just traffic and packets. Leverage user, app, device, network, protocol, and file data to detect or investigate security incidents. Manually drill down to file transaction details. Create alerts to respond rapidly to incidents in real time.
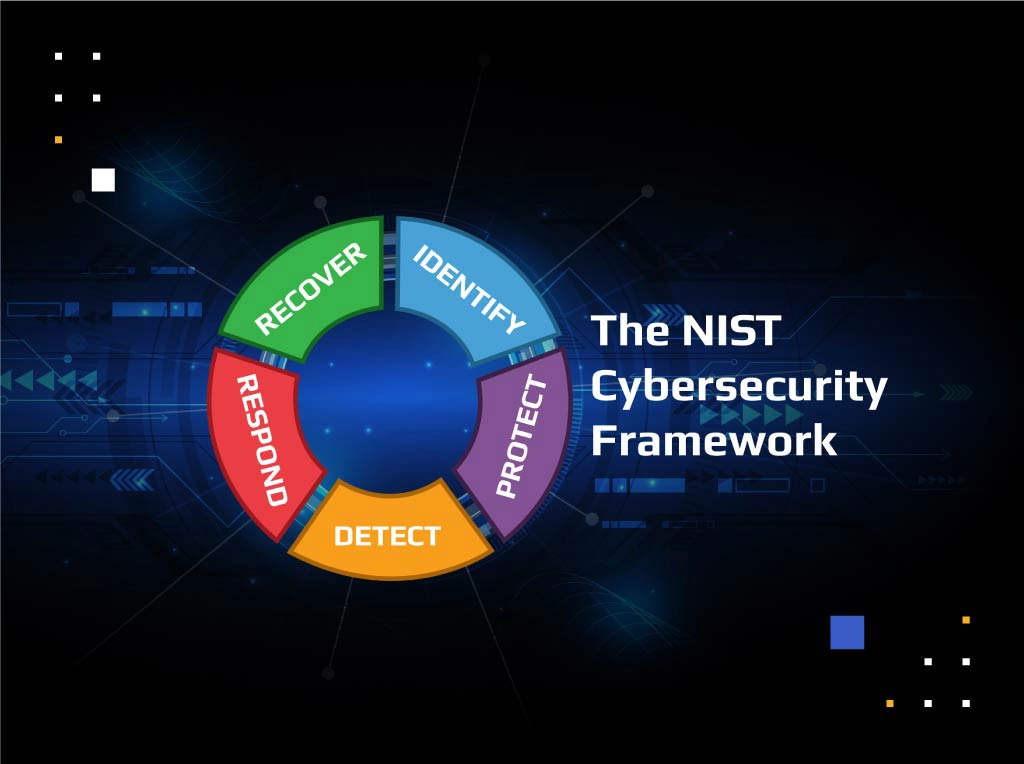
Classify Data for Risk Mitigation and Adherence to NIST CSF
Knowing which data is sensitive, where it’s stored, and who has access to it are critical for regulatory compliance, risk mitigation, and adherence to NIST CSF and other data protection best practices. Kiteworks’ unified view into all connected data repositories, including ECMs, file shares, enterprise apps, and other sources, helps businesses find, organize, categorize, and index electronic data, in accordance with the NIST CSF’s Identify core tenet. Ensure proper retention policies and enforce security policies to limit access to files containing sensitive data, also in adherence to the NIST CSF.
LEARN MORE ABOUT PROTECTING SENSITIVE DATA IN ADHERENCE TO THE NIST CYBERSECURITY FRAMEWORKS
Frequently Asked Questions
eDiscovery, or electronic discovery, is the process of locating, preserving, collecting, and producing electronically stored information, or ESI, for use as evidence in civil litigation, criminal proceedings, or internal investigations. It involves searching for, extracting, and analyzing information from various electronic sources such as emails, databases, social media, and cloud servers. The goal of eDiscovery is to locate and produce any electronically stored information that could be used in legal proceedings.
A legal hold (also known as a litigation hold) is a process used in eDiscovery to ensure that all relevant documents, data, and other information are preserved so they can be used in the event of a legal dispute or investigation. It is an obligation imposed on organizations to preserveall relevant data and information when litigation, an investigation, or an audit is reasonably anticipated. This helps to ensure that all information, regardless of where it is stored, is identified and preserved in an accessible form.
Organizations must preserve all potentially relevant electronically stored information (ESI) in a legal hold. This includes emails, documents, and databases, as well as electronic versions of paper documents, such as scanned documents, photographs, and videos. In addition, organizations must preserve metadata, which provides valuable information about the documents and their related history (e.g., when the document was created, shared with whom and when, opened by whom, and where it is stored).
The legal hold process typically consists of several steps. First, the organization must identify and track custodians, the individuals in possession of potentially relevant electronically stored information (ESI). Second, the organization must collect, preserve, and secure the ESI. Third, organizations must ensure that any legal holds issued remain in effect throughout the duration of the case or investigation. Finally, organizations must review and monitor the ESI to ensure its accuracy and completeness.
Failure to adequately execute a legal hold may result in serious consequences for an organization. These consequences can include sanctions, fines, and other penalties imposed by a court, regulatory body, or other authority. It may also lead to an unfavorable outcome in a legal dispute due to the destruction of evidence or other violations.
Organizations should adopt best practices for a legal hold to ensure compliance with applicable laws and regulations. This includes establishing clear policies and procedures for identifying, collecting, and preserving relevant electronically stored information (ESI). Organizations should also deploy technology solutions to automate and streamline the legal hold process. These solutions should include features to easily identify and track custodians (people who personally possess and are in charge of the information that needs to be preserved), securely collect and preserve data, and monitor and enforce legal holds.
FEATURED RESOURCES

Achieving Zero Trust Security With Kiteworks: A Comprehensive Approach to Data Protection

Secure Protocol Package: Strengthening Data Exchange With SFTP and SMTP

Kiteworks Complies With ISO 27001, 27017, and 27018

Top 5 Ways Kiteworks Secures Microsoft 365 Third-party Communications

