FedRAMP Compliance & Certification | Why It Is Important
FedRAMP compliance is extremely important if you want to provide cloud services to a federal government office, but how should you start this process?
What does FedRAMP stand for? FedRAMP stands for the Federal Risk and Authorization Management Program, which is run by the Office of Management and Budget (OMB) and the Joint Authorization Board (JAB), and it authorizes cloud services that the federal government can use.
What Is FedRAMP and Who Needs to Follow It?
The Federal Risk and Authorization Management Program (FedRAMP) is a unique compliance framework targeting managed service and cloud providers working with federal agencies.
Unlike other frameworks, like Cybersecurity Maturity Model Certification (viz., targeted toward defense contractors working with agencies under the U.S. Department of Defense), FedRAMP applies specifically to anyone providing cloud-based products to government agencies.
What Is FedRAMP?
FedRAMP was established by the Office of Management and Budget in 2011 to orient cloud security around “cost-effective, risk-based” approaches to cybersecurity. According to the OMB, any cloud system transmitting or holding federal data falls under their jurisdiction.
To administer the compliance standard and provide organizations with their Authorization to Operate (ATO), several executive branch entities manage compliance. These entities include the following:
- The Office of Management and Budget: The governing body of the FedRAMP program.
- The Joint Authorization Board: The body tasked with governance and decision-making, comprised of Chief Information Officers from several other entities:
- Department of Homeland Security
- General Services Administration
- The Department of Defense
- The FedRAMP Program Management Office (PMO): An office located within the General Services Administration tasked with managing the day-to-day operations of the compliance framework.
- The National Institute of Standards and Technology (NIST): Responsible for developing the standards used for compliance.
- Department of Homeland Security: Outside of consulting and governance, DHS provides management for the continuous monitoring strategies.
Under these governing bodies, regulations are approved, refined, revised, and implemented. FedRAMP draws its actual technical and physical requirements from a few primary documents:
- NIST Special Publication 800-53: NIST SP 800-53 defines security controls that organizations can put into place to better secure their systems, particularly in alignment with the Federal Information Security Management Act (FISMA). More relevant to organizations seeking compliance, NIST 800-53 defines escalating levels of security controls based on the sensitivity of that information. FedRAMP leverages NIST 800-53 to define controls and best practices that organizations must meet for compliance.
- NIST Special Publication 800-37: This document established the Risk Management Framework (RMF), a unique set of regulations that apply directly to how organizations implement risk assessment and management controls. Depending on the impact level, FedRAMP will require certain types of risk management and adherence to aspects of RMF.
- Federal Information Processing Standards (FIPS) 140-2: FIPS 140-2 defines requirements for federal agencies and contractors when implementing cryptographic modules and encrypting data.
- FIPS 199: This document defines the security impact levels used by FedRAMP to determine security, privacy, and risk management requirements.
To earn ATO designation, cloud providers must undergo a rigorous auditing process. One of the most important aspects of audits is the participation of Third Party Assessor Organizations (3PAOs).
Under federal regulations, all cloud providers undergoing audits must do so through an impartial and authorized third-party assessor. A security firm certified in audits, a 3PAO fills that role under the guidance and supervision of the PMO and JAB. An organization seeking ATO at any level can only achieve ATO once it has undergone a full audit from a 3PAO, which provides attestation as to its compliance with regulations.
Why Is FedRAMP Compliance Important?
FedRAMP compliance is important because it provides a standardized approach to security assessment, authorization, and continuous monitoring for cloud products and services used by the federal government. It helps to ensure that any cloud solution implemented by a government agency meets the government’s strict security requirements, providing greater security and more efficient onboarding of cloud solutions. Additionally, FedRAMP certification ensures that agencies can easily identify and compare multiple cloud solutions to find the best option for their needs.
Of course, organizations enjoy many benefits by becoming FedRAMP compliant.
- Improved Security: FedRAMP compliance requires organizations to implement a standardized security program across all cloud-based services, allowing organizations to prevent and better respond to threats.
- Risk Management: FedRAMP-compliant processes and procedures provide organizations with the ability to proactively identify, assess, and manage risks associated with the use of cloud-based services.
- Cost-Saving Structure: Becoming FedRAMP compliant eliminates the need for multiple levels of security review for each cloud service provider, reducing the administrative costs associated with cloud-based services.
- Efficiency: FedRAMP compliance reduces the time and effort required to set up and maintain cloud-based services, making it easier to stay ahead of the competition.
- Federal Mandate: For organizations that provide cloud-based services to the US Federal Government, FedRAMP compliance is mandatory, leading to a higher level of trust and wider acceptance.
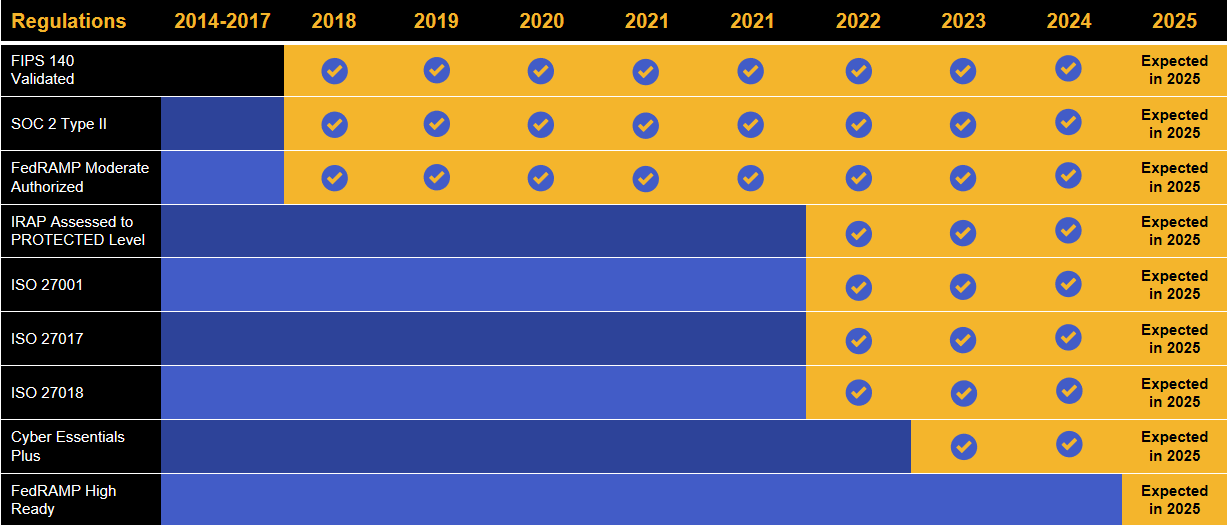
Kiteworks touts a long list of compliance and certification achievements.
What Types of Businesses Need to Be FedRAMP Compliant?
Businesses that store, process, or transmit federal government or mission-critical data or systems must be FedRAMP compliant. This includes cloud service providers, Software-as-a-Service (SaaS) providers, Infrastructure-as-a-Service (IaaS) providers, and Platform-as-a-Service (PaaS) providers. Companies that provide services such as hosting, software development, email and file sharing, mobile application management, security and compliance, virtual private networks (VPNs), or any other IT service that could interact with federal government data must also comply. In addition, any business that works with suppliers or contractors who store or handle controlled unclassified information (CUI) or other federal government data must also comply with FedRAMP requirements.
FedRAMP, however, isn’t just for government contractors. By obtaining FedRAMP authorization, any private sector business can demonstrate to their customers, partners, and other stakeholders that their cloud computing solutions are secure and compliant with federal regulations. This can help private sector businesses increase customer trust and confidence, reduce legal risk, and improve their competitive standing. Of course, a FedRAMP authorized solution is also a great way for private sector businesses to gain access to more lucrative contracts among federal, state, and local government agencies.
What Are the Categories of FedRAMP Compliance?
The FedRAMP compliance process includes three categories of compliance: security, operations, and documentation.
- Security compliance: covers authentication and authorization, access control, encryption, and incident response.
- Operations compliance: covers system availability and performance, software patching, monitoring, and backups.
- Documentation compliance: covers system and service documentation, data flow diagrams, and authorization packages.
FedRAMP ATO, Impact Levels, and Audits
FedRAMP authorization is divided into three impact levels, and 3PAOs assess cloud providers based on the requirements of these levels.
The impact levels of FedRAMP are outlined in FIPS 199 and include the following:
- Low Impact: At this level, a cloud provider’s IT systems handle information that, while publicly available through the Freedom of Information Act (FIA), is still deemed sensitive and important to the operation of a given agency. The loss, theft, or damage of this information could negatively impact the agency’s operation and negatively impact constituents.
- Moderate Impact: A cloud provider’s systems handle data that will seriously impact the agency or its constituents. This can include operational harm to the agency assets, financial losses for the agency, or harm to individuals (including damage to finances, privacy, or security).
- High Impact: At this level, if data managed by the provider is stolen, lost, or damaged, the result can be a catastrophic impact on agencies and their constituents. Adverse effects can include the financial ruin of the agency and its constituents, complete loss of privacy of critically sensitive data (like health records or personally identifiable information), or even the potential for physical harm.
Finally, there are some standard documents that most organizations pursuing ATO must provide throughout their audit process. These include the following:
- The System Security Plan (SSP): While the government agency sets requirements and controls, the cloud service provider must kick off the process by providing their SSP. This report outlines the provider’s existing infrastructure and the controls and measures they must implement to meet their desired ATO.
- The Control Implementation Summary (CIS): The provider documents and outlines security responsibilities they would assume for the agency, with the agency reviewing the summary for accuracy.
- The Security Assessment Plan (SAP): The SAP is based on the SSP. The cloud provider and the 3PAO prepare the SAP, which outlines all procedures, methodologies, and tests used as part of the audit.
- The Security Assessment Report (SAR): The SAR reports on the results of the audits. Prepared exclusively by the 3PAO, the SAR details what was tested, what was not, what controls met compliance requirements, and what failed to do so. The SAR also suggests any remediation steps.
- The Plan of Action and Milestones (POA&M): This report, prepared by the cloud provider, outlines any remedial steps and timelines required to correct noncompliant systems. Under compliance rules, if the 3PAO determines that an organization is prepared for its ATO with relatively straightforward remediation steps, the POA&M can stand in as a sort of binding agreement that the provider will implement those steps within a reasonable period of time.
What Are the Paths to FedRAMP Authorization?
This article has focused on general approaches to authorization, but it is important to note that these approaches fall into one of two primary paths toward ATO. The path that an organization decides to pursue can dramatically affect how they proceed with their compliance audits.
The two paths that an organization can take toward authorization are as follows:
- Agency Authorization: Under most circumstances, a cloud provider will respond to a Request for Proposal from a government agency or otherwise partner with them. In turn, the agency will sponsor and support that provider through the authorization process. As part of this path, the agency defines the requirements of their authorization.
Because it is an agency determining the details of compliance and security, the agency will have more latitude in determining if unconventional infrastructure meets their requirements under FedRAMP. Furthermore, agencies will often have additional requirements for cloud providers above and beyond baseline impact levels.
Finally, the provider is not authorized to work with other agencies. Providing a cloud product to another agency would require another audit and authorization process with that organization.
- JAB Authorization: Conversely, an organization can undergo a Provisional ATO (P-ATO) under JAB’s jurisdiction. JAB and the PMO directly approve audits and authorizations.
The advantage of a P-ATO is that it is more generalized. While the JAB will not accept responsibility for agency-specific security needs, agencies can use a P-ATO package to consider a provider for specific authorization. The cloud provider with a P-ATO is generally ready to work with more agencies.
However, the process is a bit longer. First, the provider seeking P-ATO must apply for consideration through the FedRAMP Connect program. Once approved, the provider must also provide a Readiness Assessment Report completed by a 3PAO that attests to the provider’s ability to complete the audit.
In either case, best practices typically revolve around thoroughness and completeness:
- Work With an Expert 3PAO: These organizations are listed under the FedRAMP Marketplace, and a skilled and knowledgeable 3PAO can go a long way toward effective audit preparation and reporting.
- Prepare for Continuous Monitoring: The last step in compliance auditing is continuous monitoring and annual audits. Once compliance is implemented, it is up to the provider to maintain these standards even as threats and best practices change.
- Understand Templates and Documentation: The PMO provides a set of templates that providers and 3PAOs use to provide standardized reports. Download these reports and understand how they will be used as part of the audit process.
How Long Will It Take to Achieve FedRAMP Authorization?
The time it takes to achieve FedRAMP authorization depends on various factors, such as the complexity of the cloud security controls the organization has implemented, the scope of the organization’s workload, and the organization’s engagement with the FedRAMP Program Management Office (PMO) during the authorization process. Organizations that already have robust cloud security controls in place can expect the authorization process to take from 6-12 months. However, organizations that are new to cloud security or whose cloud security controls are more complex may require more time, depending on the steps they need to take to meet the FedRAMP security requirements. Engaging with the FedRAMP PMO during this process is strongly encouraged, as their expertise and experience can help expedite the authorization process.
What Tools Can Make It Easier to Manage Your FedRAMP Compliance Effort?
With the increasing complexity of FedRAMP requirements, there are a number of tools available to help make it easier to manage FedRAMP compliance efforts. These include:
- FedRAMP Software: There are a number of FedRAMP-specific tools available today that can help automate and streamline the compliance process. These tools often include automation support for risk assessment, documentation creation, policy management, training and knowledge management, and ongoing monitoring and reporting.
- FedRAMP Compliance Dashboard: Many cloud service providers offer a centralized dashboard to monitor and manage compliance efforts across multiple projects. These dashboards usually provide one-click access to compliance-related information and activities, making it easier to organize, track, and manage compliance efforts over time.
- FedRAMP Checklists: A number of checklists are available for cloud service providers to ensure that all the necessary steps are taken toward FedRAMP compliance. These checklists provide a clear and concise view of the process, helping to keep track of progress and ensure that all steps have been taken toward compliance.
- Third-party Assessors: Third-party assessors are often used to review compliance activities and determine if the cloud provider is meeting all security controls. These assessors can be invaluable in helping to identify gaps, suggest corrective actions, and provide guidance on best practices.
- Training and Education: As part of any compliance effort, it’s important to provide ongoing training and education to all staff. This allows teams to stay up to date on the latest requirements and provides a guideline for staying compliant as changes and updates are made.
What Is the FedRAMP Marketplace?
Agencies must be able to verify that providers are authorized, and it is critical that providers undergoing audits can find 3PAOs certified under regulations. The FedRAMP Marketplace solves this problem by providing a searchable database of providers that have earned their ATO, 3PAOs certified to provide audits, and specific platforms and products that can meet or support compliance.
Those interested in these topics can use the searchable FedRAMP Marketplace website to discover compliant products, cloud providers, and third-party assessors.
Leverage FedRAMP-compliant Cloud Platforms to Expand Your Client Base
While federal regulations are strict, they are so for a reason—to protect critical information from attack. For organizations willing to undergo the rigors of an ATO or P-ATO audit, they will almost always find themselves more secure and better able to offer products and services to important government agencies.
Readers can learn more about the FedRAMP private cloud and why organizations should use FedRAMP authorized cloud service providers in order to protect sensitive content moving into, within, and out of their organizations.
