
Assessing the Maturity of Sensitive Content Communications Privacy and Compliance in Financial Services
Any organization collecting confidential customer information data is obligated to secure it and maintain its privacy. When it comes to collecting, storing, processing, and sharing personally identifiable information (PII), the financial services sectors are at the top of the list. PII is crucial for the day-to-day operations of nearly every financial services firm.
In addition to being shared and sent across different internal systems, networks, and applications, PII is also sent and shared with countless third parties. Both internal and external digital communications of sensitive content can create serious risks, and financial services organizations must ensure that they have the right cyber risk management strategies in place to address them. To help ensure PII is not breached through accident or malicious hack, the financial industry and government agencies have instituted regulatory compliance requirements to govern the digital exchange of information.
Financial services is a broad industry sector consisting of commercial and wholesale banking, retail banks, insurance, and wealth management. Use cases are extensive. Just some of them include:
- Safeguard processing of business payrolls, credit card transactions, and wealth manager moves
- Securely share customer financial information with other banks to syndicate large commercial loans
- Protect and audit content transfers when delivering statements and clients’ application documents
- Protect PII sent to outsourced firms for non-core tasks like mortgage servicing or collections
- Consolidate SFTP communications in a secure, scalable deployment with unified governance and admission
- Create and manage complaints, automated flows like AML reports to regulations and statements to customers
Demonstrating regulatory compliance and protecting your data is increasingly difficult due to the growing complexity and volume of cyberattacks by foreign states, organized cybercriminal syndicates, lone malicious actors, and other bad actors. They all understand the value of the data financial institutions share and hold.
Because of the risk involved, financial services firms must ensure they have the mechanisms in place to benchmark the maturity of their governance controls and security strategies. This blog post examines the broader picture of digital communications privacy and compliance in financial services and spells out recommendations on what financial firms can do to address the gaps. The post also examines FinTech business disruption and how it introduces new cybersecurity risks that financial services organizations must address in their cyber-risk management approaches.
Prevalence of Third Parties in Financial Services
The supply chain for financial services often consists of hundreds of organizations and thousands of users. There are many different third parties when it comes to financial services, which ultimately increases cybersecurity risk and makes compliance more challenging. These third parties include software vendors, information technology firms, legal firms, accounting firms, and human resource firms, among others.
Some third parties critical to the financial system are not financial institutions and fall outside of many financial regulatory frameworks. Yet, due to the nature of the service or solution they provide, these third parties are critical for many financial services firms.
These third parties provide vital solutions that increase efficiency in how we conduct business. However, outsourcing some services to a third party often means they need to access some sensitive data you hold. Even if you sign a contract with them, the responsibility for protecting this data lies with your organization. In these instances, organizations must institute third-party risk management (TPRM) strategies.
The transfer of sensitive data with these third parties creates big loopholes for malicious threat actors to exploit. In fact, according to the latest Verizon Data Breach Investigations Report (DBIR), 62% of data breaches this past year were related to the supply chain. One reason is that third parties often do not have as robust security measures as their customers.
Even if the bad actor is unable to access an organization’s supply chain and exploit downstream data, disruptions to the operations of a third party that result in downtime can have a negative impact on hundreds, thousands, or even tens of thousands of customers of the third party. This, in turn, can have financial repercussions. In response, organizations need to have the right supply chain risk management approach in place.
Compliance requirements for many organizations extend to their supply chain. The tools they use in their supply chain must meet regulatory compliance. For example, a bank that shares customer personally identifiable information (PII) of employees with a third-party payroll provider must do so over a file sharing solution that meets regulatory FIPS (Federal Information Processing Standards) 140-2. Failure to do so can result in fines and/or penalties, and may even have a negative impact on the organization’s brand.
Third-party Sensitive Content Communications Risk Management
Before onboarding any third party, it is prudent for a financial organization to audit its security infrastructure to gain some confidence that its security posture is adequate. But even after onboarding, ongoing due diligence is a good practice for all the third-party vendors of an organization.
Due diligence aims to quickly notice any gaps that malicious threat actors can exploit and remediate them beforehand. According to the latest IBM and Ponemon Institute “Cost of a Data Breach Report,” the average cost of a data breach in financial services last year was $5.97 million, the second highest for all industry segments (only healthcare is higher).
A critical step in a third-party risk management protocol is comprehensive vendor inventory to correctly identify all your third-party vendors. This list should always be kept up to date to help in risk assessment.
The challenge many organizations face in ensuring regulatory compliance when it comes to third-party processes is the fragmented nature of their risk assessment efforts. Some organizations are investing in technological solutions to consolidate and automate their processes.
How FinTech Disruption Creates New Cyber Targets
FinTech firms have evolved at a fast pace over the past few years to create new targets for cybercriminals beyond traditional financial services firms. While the disruption opens up new opportunities, it also opens up new risks.
64% of consumers indicate they have used two or more FinTech platforms in the past year. This penetration creates disruption across the financial services sector: 22% of insurance, asset, and wealth management companies and 28% of banking and payment services companies are at risk of being disrupted and losing revenue.
This trend is observed within the funding landscape where $1 of every $5 in venture funding across all industries goes to FinTech. While much opportunity exists for financial services organizations to drive improved efficiencies, lower costs, and enhanced customer service, risk also exists when it comes to cyber threats. Specifically, based on one report, 98 out of the top 100 global FinTech companies are vulnerable to cyberattacks today.
Regulations and standards have not kept pace with these new disruptive technologies. This creates fertile ground for threat actors to find and attack FinTech firms handling sensitive data. In response, regulatory bodies are seeking ways to institute new standards that require organizations to implement appropriate data privacy tracking and controls.
Sensitive Content Communications Privacy and Compliance in Financial Services
With that background in mind, a few important questions come to mind.
- How are the financial services and FinTech industry sectors coping with cybersecurity threats?
- How are they ensuring compliance?
- How are they responding to the cyber risks posed by third parties?
To answer these questions and others, I suggest we turn to Kiteworks’ “2022 Sensitive Content Communications Privacy and Compliance Report” to examine the maturity of digital communications privacy and compliance in financial services.
Data is at the heart of every financial services institution and FinTech firm. Their business models rely heavily on capturing, sharing, transferring, and storing client PII and financial data for day-to-day operations and long-term innovation.
All the activities and processes are governed by strict security and compliance standards. Privacy regulations, such as the EU’s General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), and the California Consumer Privacy Act (CCPA), control how personally identifiable information (PII) and protected health information (PHI) are captured, shared, used, and stored.
The fact that financial institutions share a lot of customer information with each other means that compliance must also come into play when data is transferred and shared. TPRM is a critical element of the financial industry when it comes to data security, privacy, and compliance.
Ensuring this takes place is not an easy undertaking, per findings in the Kiteworks report. Unsurprisingly, the biggest challenge was sharing and transferring data with third parties. 51% of respondents said they are inadequately protected against third-party security and compliance risks related to sensitive content communications, whereas only 53% encrypt all sensitive content communications with third parties.
Considering that 57.5% of the financial services respondents share private information with over 1,000 third parties and 58% have not implemented controls to measure third-party risk, we can start painting a picture of the challenges this sector faces in terms of compliance with relevant regulations as well as protection of sensitive data from malicious threat actors.
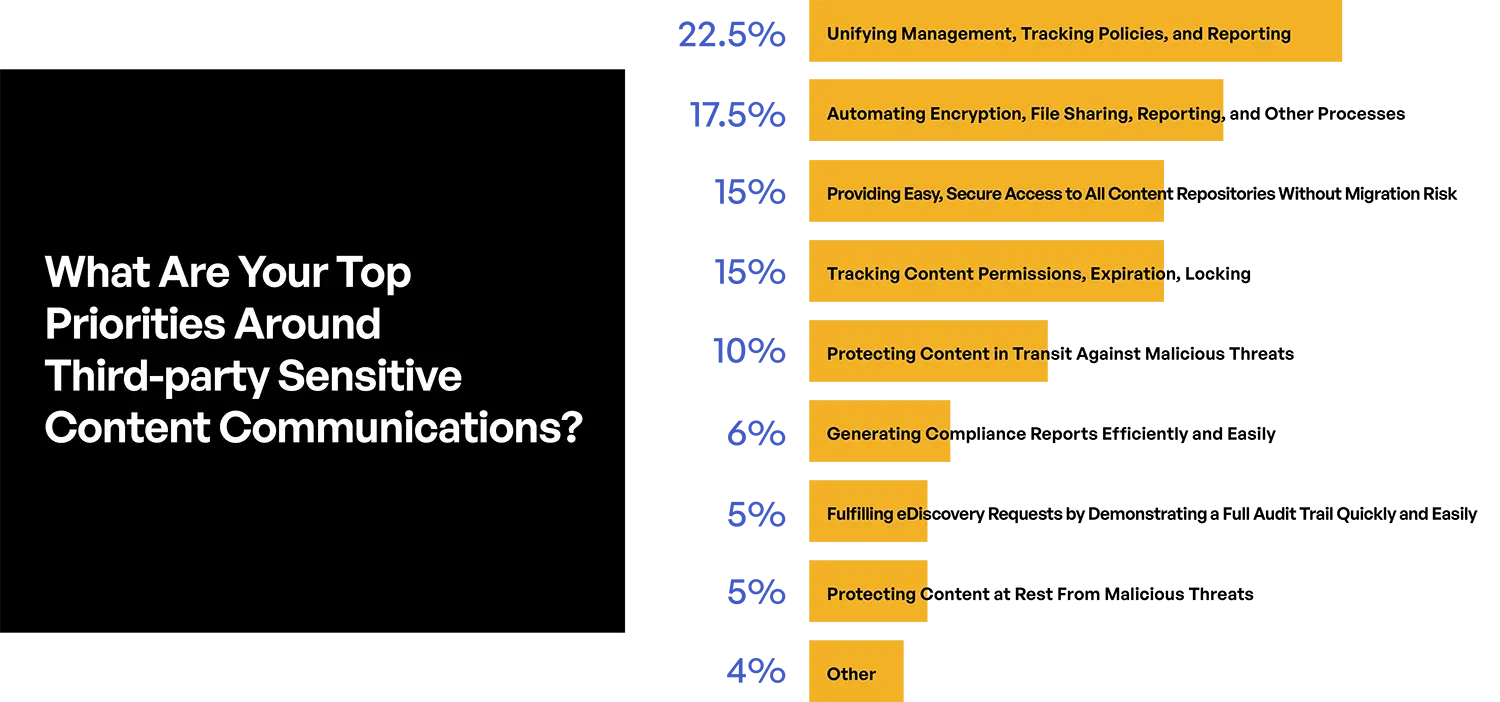
Table 1. Top priorities around third-party sensitive content communications in financial services.
Governance, Risk Management, and Compliance in Financial Services
When asked to rank their priorities, management of sensitive content communications rose to the top of the list. For example, 22.5% of financial services respondents ranked unifying management, tracking policies, and reporting on digital communications of content at the top of their list. This was followed by 17% who said automating encryption, file sharing, reporting, and other processes was their top priority.
These rely on a robust governance, risk management, and compliance approach:
Governance in Financial Services
Organizations globally must have comprehensive governance tracking and controls in place to achieve and demonstrate compliance with all the data privacy regulations that are in place. When it comes to financial services and data privacy, the financial sector is the most regulated industry in the world. A survey of countries globally, for example, revealed that 86% of countries have laws and regulations relevant to the security and transmission of data, 87% of them have regulations or rules related to cybersecurity, 78% have regulations related to the sharing of customer data, and 65% have digital ID systems and regulations related to electronic PII ID.
Another important question regarding financial services from Kiteworks’ “2022 Sensitive Content Communications Privacy and Compliance Report” relates to whether the current privacy and compliance approaches hamper the growth. Almost one-third of financial services respondents believe that governance and protection of third-party content communications either requires a new approach or significant improvement. Seven out of 10 respondents indicate they use four or more systems for tracking, controlling, and securing sensitive data communications with third parties. This bifurcation of tools used for digital content communications makes it difficult to implement one set of policies for standardized governance across each channel—email, file sharing, automated file transfer, web forms, and application programming interfaces (APIs). It thus is no surprise that only 35% have technologies and processes in place to measure risk associated with third-party content communications (see Table 1).
Risk Management in Financial Services
Managing risk of sensitive content communications is a challenge for financial services organizations. The report revealed significant gaps:
- Only slightly more than half (52%) use antivirus and antispam technologies to verify incoming data communications from third parties (though the most mature of all industries).
- 4 in 10 organizations do not use DLP for file sharing and transfer with third parties (though also the most mature of all industries; 33% higher than the next industry).
- Only slightly more than half encrypt their content communications with third parties.
- Almost half either do not or only manage or monitor some content communications in the cloud.
In light of these deficiencies, respondents lack confidence in their risk management. Over 4 in 10 said their risk management security of third-party content communications requires either a new approach or significant improvement. Half, as a result, admitted their organizations are not well-protected against third-party content communications risks.
Compliance in Financial Services
Financial services organizations are spending an increasing amount of time and resources managing compliance regulations. Respondents said they must generate more than seven compliance reports annually. Over half said each report consumes over 40 hours to generate each of the reports. However, despite these efforts, only 20% of respondents believe these reports are accurate and another 18.5% noted they are only somewhat accurate or inaccurate in various places.
Financial Services Turns to Kiteworks-enabled Private Content Network
As the annual IBM and Ponemon Institute “Cost of a Data Breach Report” details, failure to track, control, and secure sensitive data communications can result in deleterious impact, including financial penalties, brand damage, and IP loss. And in the case of ransomware attacks, one can add the cost of ransom.
In response, financial services firms require a unified approach to sensitive content communications. It requires Private Content Networks that employ content-defined zero trust because content does not stay in today’s “controlled” applications and workloads. This assumes that all users are not to be trusted by default, all content is not to be trusted by default, and enforcement of least privilege. Doing so enables financial firms to ensure private PII, IP, client financial records, insurance claims, and more remain private and in compliance with global regulations.
Additional Resources
- Report Benchmark Your Sensitive Content Communications Maturity Against Others in the Financial Services Industry
- Blog Post Takeaways You Need to Know from Kiteworks 2022 Sensitive Content Communications Report
- Brief Key Report Highlights on Financial Services and Sensitive Content Communications
- GlossaryPCI Regulatory Compliance
- GlossaryThe Importance of Third-party Risk Management
- Blog PostData Compliance
- Blog PostPCI Compliance
- Blog PostEmail Compliance Solutions