Data Privacy, Protection, and Security Best Practices
Data privacy is not just a business problem; it affects every user, employee, or customer who trusts you to handle or store their private information.

What is data privacy? Data privacy is part of data protection that requires sensitive data, like personally identifiable information and protected health information, to be protected and handled appropriately. Data privacy is important because it demonstrates that your organization can be trusted to handle sensitive information.
How Does Data Privacy Work?
Data privacy refers to how information is protected against unauthorized disclosure based on its perceived importance. Different forms of information often call for varying levels of security and protection and use different contexts to determine the levels of technical, physical, and administrative protections required to keep that information private and confidential.
The three primary elements of data privacy are as follows:
- Individuals have the right to be left alone and maintain control over their information.
- Organizations have a responsibility to develop procedures for properly processing, handling, collecting, and sharing of personal information.
- Organizations must also maintain compliance with relevant protection laws.
One of the most common forms of protected information is referred to as personally identifiable information. PII is information that can lead to the identification of an individual, either directly or indirectly. This information can include the following items:
- First and Last Names
- Addresses
- Social Security Numbers
- Telephone Numbers
- Email Addresses
- Driver’s License Numbers
- Bank Account Numbers
- Credit or Debit Card Numbers
- Passport Information
Privacy has become a vital focus of IT and business infrastructure as well as an ethical concern in the digital age of networked, always-on systems. Having PII be stolen or made public could be catastrophic—either financially, physically, or reputationally—to both the individual and the company. Most compliance frameworks include some form of explicit data protection.
Data privacy incorporates several layers of protection and best practices:
- Encryption and Cryptography: Protected data must be made unreadable by outside parties, and encrypting data at rest in servers or during transmission is an important part of privacy.
- Physical Safeguards: Even in a digital world, data is stored and maintained in physical locations. It is up to organizations managing that information to have physical safeguards in place protecting data centers, workstations, and mobile devices.
- Administrative Measures: Complex privacy and protection laws require administration and policy implementation. Organizations must train employees against exposing data, develop information governance policies to protect information, and create practices that help fight against challenges like insider threats.
- Risk-based Security: Ad hoc security is not enough to actually secure complex systems, but risk-based assessments and compliance can help organizations develop comprehensive governance and privacy policies that protect user information in line with regulations and the best interests of customers.
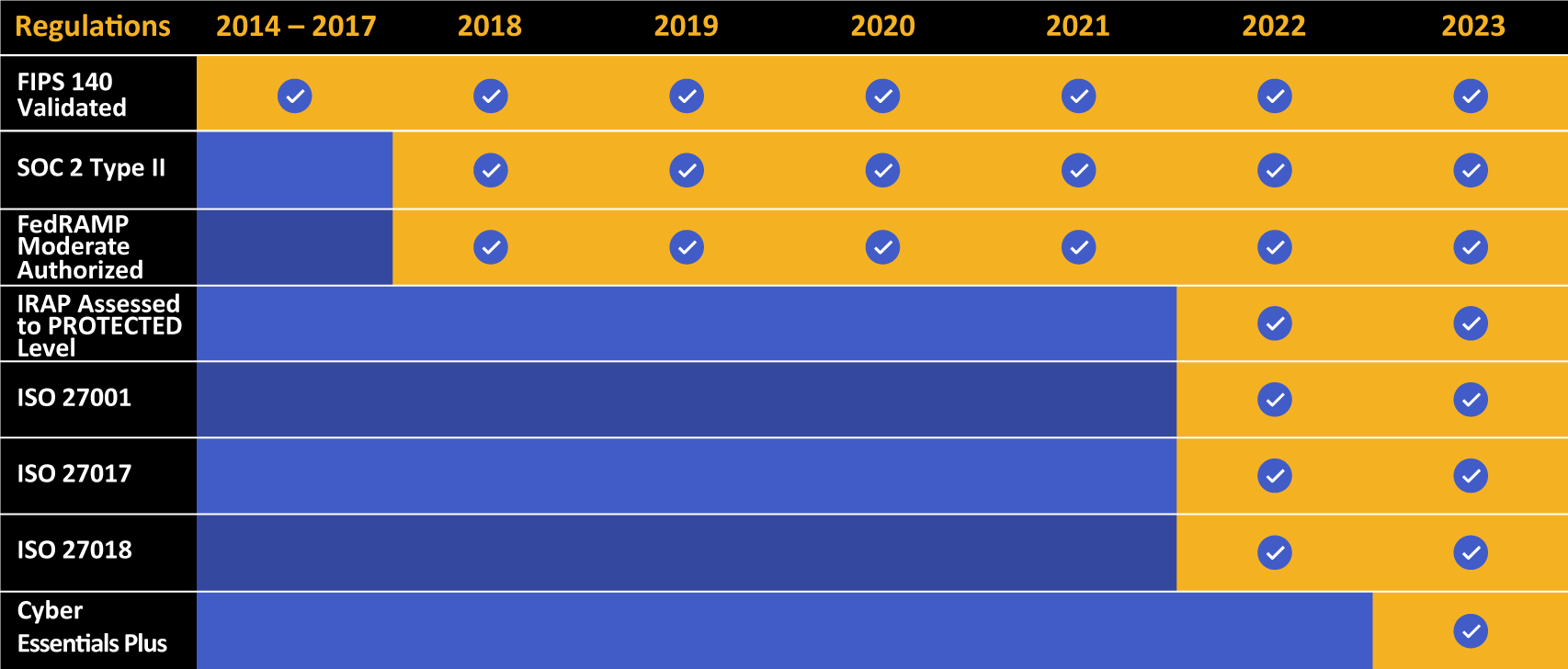
Kiteworks touts a long list of compliance and certification achievements.
What Laws Govern Data Privacy?
While there are some core tenets of privacy, most industries have their own set of regulations and practices addressing their unique industry challenges. Different types of data call for different types of protections, and various compliance laws apply to different industries.
Some of the major laws that govern privacy around the world include the following:
HIPAA
The Health Insurance Portability and Accountability Act (HIPAA) governs the healthcare industry and patient information. Healthcare information is often considered one of the most important forms of data—it calls for stringent privacy and security controls.
Under HIPAA, patient information is defined as "Protected Health Information" and covers any and all information that refers to a patient’s healthcare or payment thereof. This includes doctors’ reports, patient responses to internal documents, and payment information given as part of provided healthcare services, among others.
All security measures (including encryption, IT controls, risk management , physical protection, and administrative policies) are centered around ensuring that PHI is not exposed beyond the patient’s permission.
HIPAA applies to what are known as "Covered Entities," which include hospitals, doctors, and health insurance providers. HIPAA also equally applies to "Business Associates," or vendors that provide services to Covered Entities. Under HIPAA, Businesses Associates handling PHI are equally responsible for patients’ privacy as their Covered Entity partners.
Penalties for unauthorized disclosure under HIPAA are strict, with the potential for millions of dollars in fees per year for breaches of compliance and possible jail time for individuals depending on the type of exposure. In cases of breaches, organizations must provide detailed, often quite public, disclosures about the breaches over websites, local news reports, and notifications to the Department of Health and Human Services.
FISMA
The Federal Information Security Modernization Act requires federal agencies to implement controls to protect PII used as part of government operations. Based on the National Institute of Standards and Technology guidelines, FISMA calls for these agencies to implement basic security principles based on key specifications, including the National Institute of Standards & Technology (NIST) Special Publication 800-53, SP 800-171, Federal Information Processing Standards (FIPS) 199, and FIPS 200.
ISO 27000 Series
The International Organization for Standardization provides specifications and standardized best practices on a number of technical and professional topics in order to help public and private organizations better utilize technology. One of these series of standards is known as the ISO 27000 series, a continuum of documents outlining best practices in protecting information through technical and administrative controls.
Perhaps the best known of this series is ISO 27001, an international standard that details how organizations can implement information security management systems. These systems bring together security controls, business policies, and logistical processes to foreground privacy and security in complex IT infrastructure.
ISO 27001 is not typically required of any organization, as the ISO is a private organization. Many private businesses and public agencies choose to undergo ISO 27001 audits simply to better secure their customer or business data.
GDPR
The General Data Protection Regulation is a body of regulations that holds jurisdiction over member states of the European Union. Perhaps one of the most expansive and detailed set of laws related to privacy, GDPR ensures that consumers (referred to as "data subjects") have as much ownership over their data as possible, that laws protect that information from unauthorized disclosure anywhere it could be jeopardized, and that businesses cannot use that data without consent from the subject.
GDPR law gives subjects the right to demand complete knowledge of their data and how businesses use it. At any time, a subject may demand a complete record of their PII on file with a business and how it is used. Furthermore, a subject must give explicit consent for data to be used in any way (whether for business processing, marketing, or other services). The business must delete all that data upon the consumer’s request.
American companies like Google, Apple, and Microsoft have faced significant legal losses in the EU for noncompliance. Under GDPR, fines can range from millions of euros to up to 4% of a company’s global annual revenue, whichever is higher.
SOX
The Sarbanes-Oxley Act is a unique law. After a series of massive fraud cases in major enterprises across the United States (including the famous cases of WorldCom and Enron), Congress passed SOX to require enterprise businesses to report their technical systems and financial information. Namely, the law requires that the business leaders of a company sign off on financial statements and technical reports provided to the government annually, with legal ramifications for fraudulent statements.
Part of SOX reporting requires notification and documentation of data security policies, including controls for privacy regarding the financial information of any business clients or consumers.
CCPA
The California Consumer Privacy Act is similar to GDPR in that it places more of the onus for reporting, protection, and consent on businesses. Furthermore, it more concretely states the rights of consumers to their data, including the right to know about stored data and data uses, the right to have data deleted, and the right to opt out of any business or marketing use of their information. This law only applies to businesses operating in California and residents of California.
Ensure Data Privacy With Secure, Compliant Tools
One of the best approaches to ensuring privacy is to use technology that supports privacy. Encryption, data management and visibility, automated controls, and technical implementations of governance, risk, and compliance policies can go far in supporting such efforts. Businesses must understand both their legal obligations and their ethical posture when it comes to protecting the privacy of user data.
To learn how the Kiteworks platform delivers data privacy for sensitive content communications, schedule a demo today.

