Regulatory Compliance
Regulatory compliance is essential for any business and can actually be financially rewarding by avoiding fines and finding vulnerable areas in your company.

What Is Regulatory Compliance?
Regulatory compliance is the process of adhering to laws, regulations, standards, and other rules set forth by governments and other regulatory bodies. It is an important aspect of doing business, as companies are required to follow certain laws and regulations to maintain their operations.
Regulatory compliance helps ensure that companies do not engage in unethical or illegal practices, and can be used to protect both their employees and customers, often by protecting their data, namely personally identifiable information and protected health information (PII/PHI). These compliance standards are specific to industries and locations and can result in large penalties if not followed correctly.
Why is Regulatory Compliance Critical for Modern Businesses?
Understanding ‘what is regulatory compliance’ goes far beyond merely avoiding penalties. Rather, regulatory compliance is foundational to operational integrity, risk mitigation, and sustainable growth.
Failure to adhere to applicable laws and standards can lead to severe financial repercussions, crippling lawsuits, operational disruptions, and irreparable damage to a company’s reputation. For instance, hefty fines under GDPR for data privacy violations or the operational halts faced by financial institutions failing SOX requirements underscore the tangible risks.
Conversely, robust compliance programs build significant customer trust and enhance brand value, as consumers increasingly prioritize data privacy and ethical operations.
The regulatory landscape is constantly evolving, with new compliance regulations emerging globally and existing ones being updated frequently. This complexity demands a proactive, strategic approach to compliance, integrating it into the core business strategy rather than treating it as a peripheral checklist activity. It has become a competitive differentiator and a fundamental aspect of corporate responsibility.
What Benefits Can Organizations Gain by Ensuring Regulatory Compliance?
There are many benefits to an organization for achieving or demonstrating regulatory compliance. A major benefit is business continuity and improved trust in the industry and among customers. Some other benefits include:
- Improved Operational Efficiency: Adhering to regulatory compliance can help organizations ensure all operations are conducted efficiently and in accordance with the set regulations. This, in turn, helps organizations streamline procedures and processes, leading to improved operational efficiency and reduced costs.
- Reduced Risk and Liability: Regulatory compliance helps organizations stay up to date with the changing laws and regulations and abide by them, thus reducing the risk of penalties, fines, and other forms of liabilities.
- Improved Public Image: Organizations that comply with regulations gain a positive public image, as they demonstrate a commitment to safe and ethical operations. This can lead to improved public trust and increased confidence, which can lead to increased brand value.
- Greater Resilience: Organizations that are compliant are more resilient to changing regulations, as they already have systems in place to meet regulatory demands. This helps organizations plan better for future change, promoting greater business continuity.
- Increased Efficiency: By establishing clear procedures, processes, and systems to ensure regulatory compliance, organizations can become more efficient in the way they operate, which leads to improved productivity and cost savings.
How Does Regulatory Compliance Work?
In any industry, there are regulations, and organizations operating in those industries must comply with these regulations. Compliance can cover a variety of different practices, processes, and operations within an organization. An organization will likely have more than one area of compliance.
Some of the different kinds of compliance include the following:
- Financial Compliance: Organizations must maintain fair, transparent financial records and refrain from unethical or illegal financial practices that harm stakeholders or consumers.
Examples of such regulations are the Federal Deposit Insurance Corporation (FDIC) rules for consumer protection and the Sarbanes-Oxley Act (SOX) that requires financial reporting and transparency for corporations to mitigate fraud.
Additionally, Service Organization Control 2 (SOC 2) compliance is an attestation to investors and insurers regarding the security of systems holding customer data. It is administered by the American Institute of Certified Public Accountants.
- Cybersecurity Compliance: Cybersecurity regulations focus on the security and privacy of data in IT systems, including regulations covering the implementation of encryption, firewall security, network controls, breach prevention, and remediation efforts.
Many modern regulations include cybersecurity requirements,such as Health Insurance Portability and Accountability Act (HIPAA) regulations, the Federal Risk and Authorization Management Program (FedRAMP), and Payment Card Industry Data Security Standard (PCI DSS).
- Regulatory Compliance: This unique form of compliance emphasizes the legal obligations an organization faces as part of its operation. Regulations are a legal form of governance that is predicated on legislation and oversight, typically from a governmental or adjacent regulatory body.
This form of regulation can often overlap with the others. Compliance usually includes financial, IT, reporting, and audit logging requirements in many cases.
Because there are significant overlaps between different types of regulations, it is essential to understand where such laws come from. For example, HIPAA is a regulatory requirement for all healthcare providers, insurance companies, and associated vendors instituted and administered by federal and local governments. HIPAA, however, contains several provisions for cybersecurity and financial protection.
Conversely, SOC 2, while containing several provisions governing data management, security, and privacy, is not a regulatory requirement. It is not governed by law and is not required as part of any industry standards.
What Are Some Regulatory Compliance Regulations?
Different industries will typically include unique regulations. Some regulations will transcend industry and apply to a wide swath of common organizational types.
Some of the common regulations include:
|
| Organizations Applies To | Organization Governed By | Areas of Coverage | Requirements |
| Health Insurance Portability and Accountability Act (HIPAA) | Covered entities (hospitals, doctors, insurance companies) and their business associates | Department of Health and Human Services (HHS) | Protecting Private Health Information (PHI) from unauthorized disclosure | Cybersecurity controls; physical and administrative privacy controls |
| Sarbanes-Oxley Act (SOX) | Publicly traded corporations | U.S. Securities and Exchange Commission (SEC) | Requiring transparency in corporate financial reporting | Corporations must implement security, transparency, and accountability into financial reporting to stakeholders and the government |
| General Data Protection Regulation (GDPR) | All businesses collecting consumer data in the European Union | The EU Information Commissioner’s Office (ICO) | Protecting consumer information in EU jurisdictions | Businesses must implement privacy, security, and consent controls to protect consumer data from disclosure or abuse |
| California Consumer Privacy Act (CCPA)* | Midsize and large businesses in California | California Privacy Protection Agency (CPPA) | Protecting consumer information in California jurisdictions | Businesses must implement privacy, security, and consent controls to protect consumer data from disclosure or abuse |
| Federal Risk and Authorization Management Program (FedRAMP) | Cloud service providers working with federal agencies | The Joint Authorization Board (JAB) and Program Management Office (PMO) | Securing cloud systems used by federal agencies through third-party vendors | CSPs must implement NIST 800-53 and other controls to meet minimum standards |
| Cybersecurity Maturity Model Certification (CMMC) | Digital contractors working with Department of Defense agencies | The Department of Defense | Securing defense-related IT systems in the DoD supply chain | Contractors must implement NIST 900-171 and NIST 800-172 controls to work in the supply chain |
*As of January 1, 2023, the CCPA was amended into the California Privacy Rights Act (CPRA) with expanded regulations and controls.
Additionally, several standards are not required or governed by law but apply specifically to either industry practices or optional adoption by a company:
|
| Organizations Applies To | Organization Governed By | Areas of Coverage | Requirements |
| Service Organization Control (SOC) 2 | Any who adopt the standard | American Institute of Certified Public Accountants (AICPA) | Data security, privacy, confidentiality, and integrity | Organizations must meet minimum security and privacy standards and undergo regular audits |
| International Organization for Standardization (ISO) 27000 Series | Any who adopt the standard | International Organization for Standardization (ISO) | Data and IT infrastructure security | Organizations design, develop, implement, and maintain Information Security Management Systems (ISMS) |
| Payment Card Industry Data Security Standard (PCI DSS) | Retailers and merchants accepting credit card payments | Payment Card Industry (including credit card companies like Visa, Mastercard, American Express, etc.) | Credit card and payment information | Payment processors and merchants must implement security practices to secure payment information from theft |
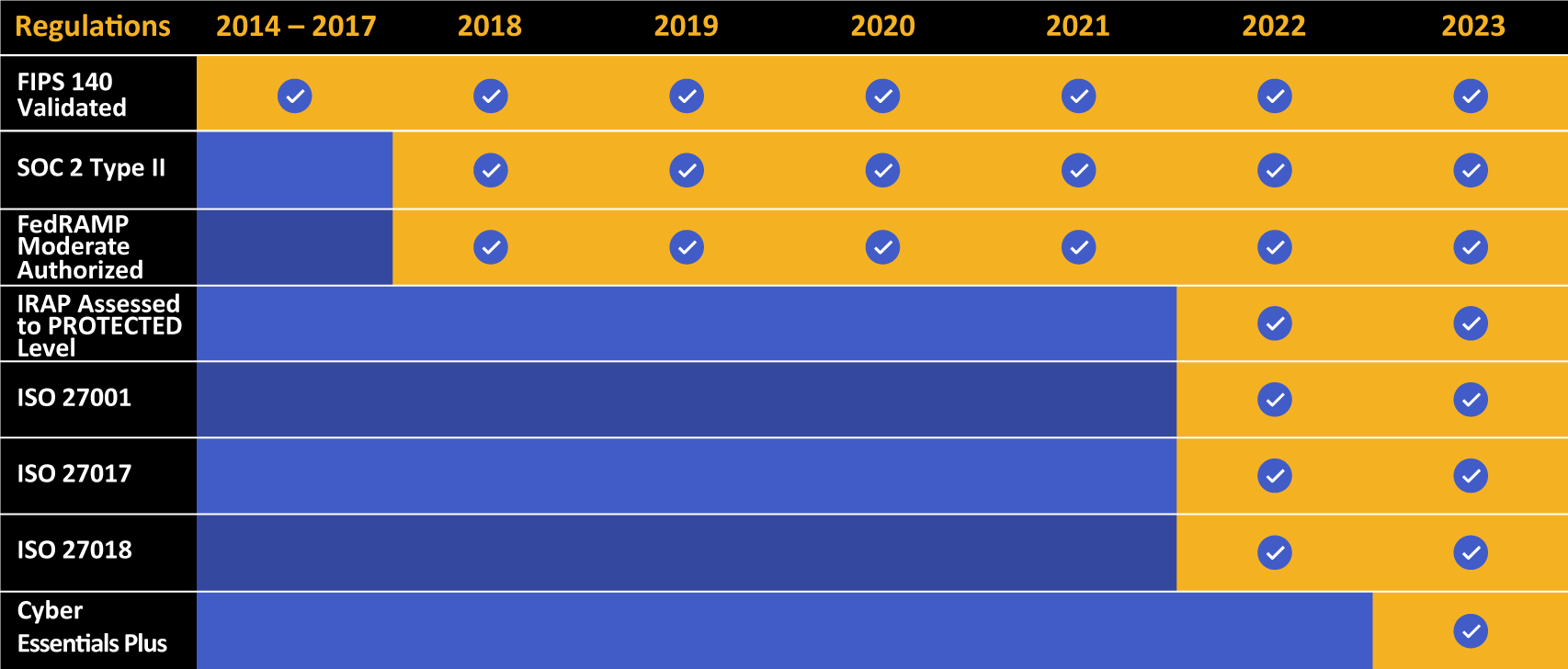
Kiteworks touts a long list of compliance and certification achievements.
Common Challenges in Achieving Regulatory Compliance
Regulatory compliance is relatively easy to achieve, in theory. Organizations are presented with a list of requirements and a deadline to meet those requirements. Easier said than done. Organizations are complex, filled with processes and nuances. As a result, demonstrating regulatory compliance is quite complex, time consuming, and often fairly expensive. These are just a few of the challenges organizations typically face when faced with regulatory compliance requirements:
- Keeping Pace with Evolving Regulations: The landscape of `compliance regulations` is dynamic. New laws are enacted (e.g., state-level privacy acts), existing ones are amended (e.g., GDPR interpretations), and industry standards shift, requiring continuous monitoring and adaptation, which can be particularly challenging for global organizations facing diverse jurisdictional rules.
- Resource Constraints: Implementing and maintaining robust compliance programs requires significant investment in terms of budget, technology, and skilled personnel (legal, IT security, compliance officers). Smaller organizations often struggle to allocate sufficient resources.
- Complexity and Cross-Jurisdictional Requirements: Multinational corporations face the immense challenge of navigating and reconciling differing, sometimes conflicting, compliance requirements across various countries and regions.
- Integrating Compliance Across Departments: Compliance is not solely an IT or legal function. Effectively embedding compliance practices into daily operations requires buy-in and collaboration across all departments (HR, finance, marketing, operations), overcoming organizational silos.
- Technology Implementation and Management: Selecting, implementing, and managing the right technology solutions for monitoring, auditing, data protection, and reporting can be complex and costly. Integrating these tools with existing legacy systems often presents significant technical hurdles.
- Data Management and Security: Ensuring the security, privacy, and integrity of sensitive data across disparate systems and throughout its lifecycle is a major technical challenge, especially with increasing data volumes and sophisticated cyber threats.
- Lack of Organizational Buy-in: Without strong support and clear communication from leadership, fostering a true culture of compliance throughout the organization can be difficult, leading to inconsistent adherence and increased risk.
Regulations and Regulatory Compliance Outside the U.S.
Regulations and regulatory compliance vary significantly from nation to nation. Most nations outside the U.S. have established laws, regulations, and guidelines for business activities, including environmental, health, and safety laws and regulations. Nations may also have laws and regulations that impact the labor and employment practices of businesses. This includes data privacy laws such as the European Union’s General Data Protection Regulation (GDPR), Canada’s Personal Information Protection and Electronic Documents Act (PIPEDA), the United Kingdom’s Data Protection Act of 2018, Australia’s Information Security Registered Assessors Program (IRAP), and many more. Companies doing business in different countries may have to comply with other regulations, such as anti-bribery laws, export control laws, and restrictions on foreign investment.
The laws and regulations of a particular country will depend on its own laws and the global treaties and conventions that it has signed. It is important for businesses to understand the laws, regulations, and standards of a country in which they are operating or that they are exporting to. Companies should also understand their obligations when it comes to regulatory compliance and how these obligations may differ in different countries.
In addition to understanding the laws and regulations of a particular nation, companies should also be aware of the enforcement capabilities of the nation’s regulatory authorities. Companies must comply with the laws and regulations of the nation and may face inspections, fines, and other penalties if they do not. It is also important for companies to understand how a nation’s laws and regulations may change over time and the implications of those changes on their operations.
Companies should also be aware of how the laws of a particular nation may interact with laws and regulations of other nations. For example, a company operating in multiple countries may be subject to both the regulations of their home country and those of the countries in which they are operating. It is important to understand the implications of any conflicts between these regulations and how to comply with all applicable regulations.
What Is Governance, Risk, and Compliance?
Regulations often fall under a larger umbrella of strategies and practices that businesses follow, generally known as governance, risk, and compliance.
GRC includes the following practices:
- Governance: Integrated strategies and capabilities around governing business practices, data management, and security. Governance includes high-level planning and execution of business processes and objectives.
- Risk: Risk assessment and management are the practice of measuring financial risks, security vulnerabilities, or other potential hazards and using that information to make decisions around cybersecurity, IT infrastructure, administration, and other business decisions.
- Compliance: Governance and risk practices must be used to fuel compliance now and into the future.
The Role of Regulatory Compliance Management
Regulatory compliance management is the systematic and structured approach an organization takes to ensure it adheres to all relevant laws, compliance regulations, standards, and internal policies. It involves a continuous cycle of activities designed to identify applicable requirements, assess compliance risks, implement controls and procedures, monitor their effectiveness, conduct audits, and report on the organization’s compliance status.
This function typically involves designated compliance managers or officers who coordinate efforts across departments. Effective regulatory compliance management is deeply integrated with overall corporate governance and risk management frameworks.
Its scope includes developing and maintaining compliance policies, training employees, responding to regulatory inquiries, and managing incident responses. By embedding compliance into the organizational fabric, effective management not only prevents legal issues and penalties but also enhances operational efficiency, builds stakeholder trust, and supports long-term business sustainability and strategic growth.
Why Is It Important to Have a Regulatory Compliance Policy in Place?
Having a regulatory compliance policy in place is important to ensure that a business is operating in accordance with all applicable laws and regulations. A regulatory compliance policy outlines what specific regulations the business must comply with, as well as the steps it needs to take to remain compliant. Having a regulatory compliance policy in place also helps to protect the business from liability and provides assurance to customers and stakeholders that the business is operating within the law.
Effective Strategies for Meeting Regulatory Compliance Requirements
While every regulatory compliance regulation is unique, there are many similarities between them, which is a godsend for organizations that must demonstrate compliance with several different regulations. And, to be clear, most organizations must demonstrate compliance with several different regulations. So, following these strategies go a long way in setting organizations up for success in terms of meeting, and ideally maintaining, regulatory compliance:
- Establish a Strong Governance Framework: Define clear roles, responsibilities, and accountability for compliance across the organization, ensuring executive sponsorship and oversight.
- Conduct Comprehensive Risk Assessments: Regularly identify applicable compliance regulations based on industry, location, and business activities. Assess the risks associated with non-compliance for each requirement.
- Develop and Document Policies and Procedures: Create clear, accessible policies that translate regulatory requirements into actionable steps for employees. Maintain thorough documentation of all compliance activities.
- Implement Technology Solutions: Leverage technology for automating compliance tasks, monitoring controls, managing data security, and generating audit trails. Platforms like the Kiteworks Private Data Network centralize, control, and track sensitive content communications, aiding organizations to meet regulatory compliance mandates like HIPAA, GDPR, CMMC, FedRAMP, and PCI DSS through features like granular policy controls, comprehensive logging, and secure file sharing.
- Train Staff on Cybersecurity Awareness: Conduct periodic security awareness training sessions to educate employees at all levels about relevant regulations, internal policies, and their specific compliance responsibilities.
- Implement Robust Monitoring and Auditing: Continuously monitor the effectiveness of compliance controls and conduct regular internal and external audits to identify gaps and areas for improvement.
- Foster a Culture of Compliance: Promote ethical behavior and integrate compliance awareness into the company’s values and daily operations, encouraging employees to report potential issues without fear of retribution.
- Stay Informed and Adapt: Continuously monitor the regulatory landscape for changes and proactively adapt policies, procedures, and controls to remain compliant.
What Are Some of the Penalties for Noncompliance?
Compliance, often governed by law, can carry significant penalties. Even frameworks governed in the private sector can affect how a company does business.
Some potential penalties include the following:
- Financial Penalties: Financial penalties range from smaller fees to crippling fines. HIPAA compliance requirements, for example, scale financial penalties based on the severity of the breach. GDPR, on the other hand, only allows for two different tiers of penalties, each containing significant financial obligations on the part of the noncompliant organization.
- Loss of Licensing or Authorization: Some frameworks, like FedRAMP or CMMC, come with a baseline loss of certification for severe noncompliance. Here, organizations can no longer only operate in their industry.
- Legal Liability: If noncompliance leads to severe harm to an organization or individuals, organizations may find themselves legally liable. HIPAA contains several tiers of legal penalties, including jail time, for severe breaches or in cases of fraud.
- Impact on Business Operations: Some non-government regulations, like PCI DSS, work because the governing body can control how companies function in a business market.
For example, if a merchant fails to comply with PCI DSS, there is not a default legal repercussion. Instead, the PCI (made up of all the major credit card providers like Visa, Discover, American Express, Mastercard, etc.) can levy fines for continued use of the credit card payment networks.
Continuing noncompliance can force the PCI to label merchants with a negative rating, including higher fees and limited payment processing capabilities.
Finally, the PCI can simply close a merchant’s account and make processing payments impossible.
Operationalize Regulatory Compliance
Regulatory compliance is a significant part of any business and must play a role in business strategy and IT infrastructure. Any company operating in regulated industries with standards must use technology to support regulations.
Sensitive content communications is involved in virtually every compliance regulation, and organizations must ensure they have the right policy controls and security processes in place. Learn how Kiteworks unifies, tracks, controls, and secures critical data as it moves into, within, and out of an organization for compliance across myriad regulations, such as HIPAA, PCI DSS, FedRAMP, and others, by scheduling a custom demo.


