
Over 60% of GAO Data Privacy Recommendations Have Not Been Implemented Across 24 US Federal Agencies
US Federal Government Data Privacy Recommendations Date Back to 1997
Data privacy and protecting personally identifiable information (PII) are activities that nearly every organization must take seriously—and this includes United States federal government agencies. The mandate to protect information goes back to 1997, when the U.S. Government Accountability Office (GAO) identified information security as a high-risk area for all federal agencies. It followed this mandate with another one in 2003, which expanded high risk to include critical cyber infrastructure. It was expanded again in 2015 to include the privacy of personal information.
The GAO takes data privacy and the protection of PII seriously. Since 2010, the GAO has issued 236 different recommendations around the privacy of PII.
Assessing How Well Federal Agencies Are Doing With Data Privacy
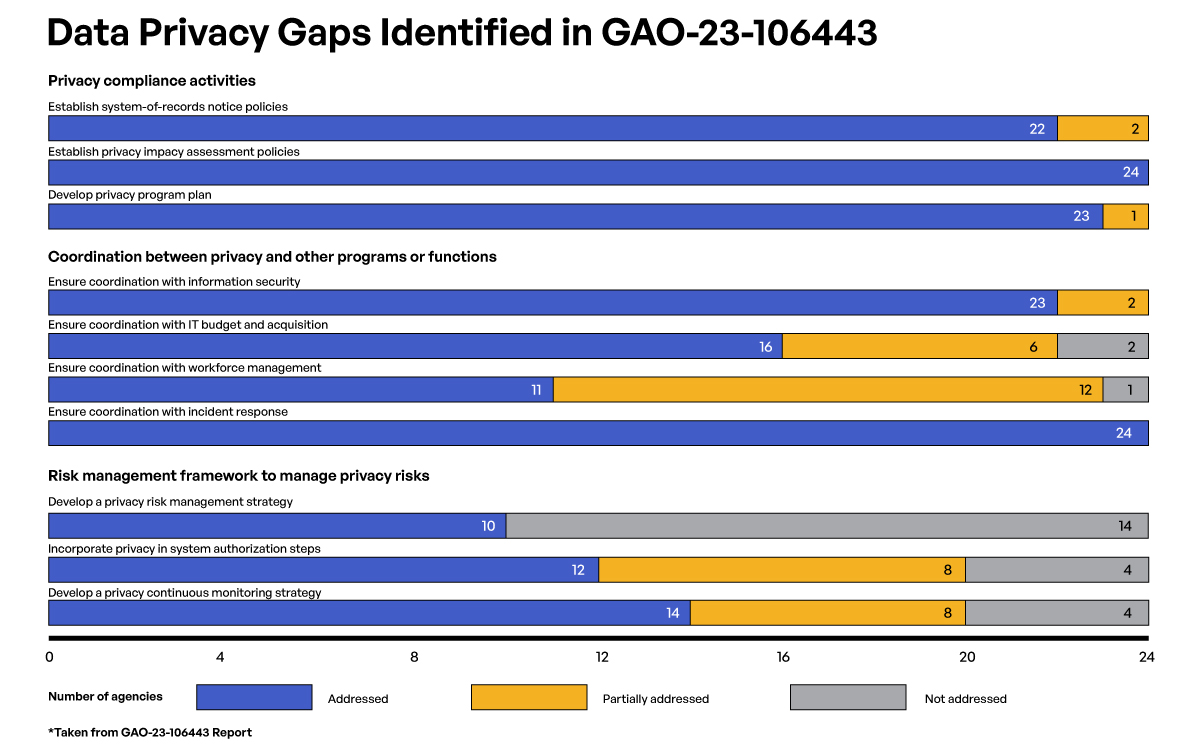
Seeking to determine how well federal agencies are faring in implementing them, the GAO assessed each of the 236 recommendations across 24 different agencies. In GAO-23-106443 Report, the GAO discovered that 140 of the recommendations have still not been implemented. Many of the agencies, according to the report, did not fully incorporate privacy into their cybersecurity risk management strategies, provide for privacy officials’ input into the authorization of systems containing PII, or develop a continuous monitoring strategy for privacy.
Lack of data privacy exposure risk controls, tracking, and security places private data at risk. Cybercriminals can exploit vulnerabilities in networks and applications to gain access to sensitive content, holding agencies hostage through ransomware attacks or stealing it for competitive or nation-state gain.
Digital Transformation of Federal Agencies Creates a Bigger Target for Cyberattacks
The use of technological systems by federal agencies and critical infrastructure owners has become increasingly vital to government operations—within agencies, between agencies, and with third parties. However, with an increase in cyberattacks, the security of these systems has become a matter of concern. Malicious actors are becoming more willing and capable of carrying out cyberattacks that can result in serious harm to human safety, national security, the environment, and the economy. The confidentiality, integrity, and availability of these systems must be protected to ensure the well-being of the nation.
GAO data privacy recommendations address gaps in governance and security controls and tracking that are intended to make it immensely more difficult for cybercriminals and rogue nation-states to gain access to PII and other types of sensitive content. Unfortunately, with 60% of the GAO’s recommendations since 2010 unimplemented, the risk to sensitive content sent, shared, received, and stored by U.S. federal agencies is substantial.
This blog post will review GAO-23-106443 and some of its biggest revelations as well as pinpoint key takeaways found within the report—both for the public and private sectors.
Why Cyber Bad Actors Target PII
As part of the move toward digital transformation, federal agencies have ramped up the amount of sensitive content that they share, send, and receive within their agencies, between agencies, and with external third parties. In addition to the growing volume of email being sent, secure file sharing and managed file transfer (MFT) have become increasingly vital to federal agencies. As a result, file sharing and MFT are prime targets for cybercriminals and rogue nation-states. If the appropriate security controls and tracking are missing, then the sensitive content being shared, received, and stored presents a significant risk and cost. This sensitive content not only includes PII but financial records and account numbers, intellectual property, and other government secrets.
Cybercriminals target sensitive content and PII for financial gain. PII in certain industries, such as healthcare, is more lucrative than PII from other industries. File sharing and MTF tools can be exploited to steal usernames and passwords, which can then be used to gain access to other accounts within the organization. Additionally, many of these systems are vulnerable to malware and ransomware attacks, which can be used to disable networks and encrypt content within them.
Unfortunately, the potential threat to PII is not limited to federal agencies, as government agencies frequently share important information with third parties, such as contractors, consultants, and other external entities. This creates an opportunity for malicious actors to gain access to sensitive information as it is shared and transmitted via file sharing, managed file transfer systems, web forms, and email. Because of the nature and growth of the supply chain, PII exposure risk is multitudes higher. One weak link in the supply chain can expose PII for hundreds or even thousands of organizations.
What Federal Agencies Need to Do to Protect PII
Because of their importance, it is imperative that federal agencies employ the latest security measures to protect PII when using these systems. For example, they should ensure that all data transmissions are encrypted, and that they use strong authentication measures. They should also regularly audit the networks and systems that are used to share and store these documents, to ensure that any potential issues are identified and addressed quickly. Ultimately, protecting PII via email, file sharing, MFT, and web forms is a continuous and ongoing effort for federal agencies and other organizations.
Data Privacy Deficiencies Identified by the GAO
The GAO report summarizes the data privacy deficiencies found in the different federal agencies. They break into the following areas:
- Lack of effective data management practices. Federal agencies lack effective data management practices, which make it difficult to identify, categorize, and secure sensitive data.
- Insufficient security controls. Federal agencies have inadequate security controls to protect sensitive data, including encryption, multi-factor authentication, and access controls.
- Incomplete or inaccurate inventory of PII. Federal agencies lack complete or accurate inventories of PII, which make it difficult to identify and secure sensitive data.
- Inadequate incident response planning. Federal agencies lack adequate incident response planning, which hinders their ability to respond effectively to cyberattacks and protect sensitive data.
The GAO report found several areas most lacking on the part of federal agencies. For example, 14 of the 24 have not developed a privacy risk management strategy, only half have incorporated privacy in system authorization steps, and 10 out of the 24 have either not developed or have only partially developed a privacy continuous monitoring strategy. One of the areas in the report that details the cause behind risk relates to the lack of controls and tracking around private data shared and sent to third parties. Organizations, per the GAO, must ensure the privacy of PII they collect, use, and share.
GAO PII Privacy Recommendations
To address the above deficiencies, the GAO report spells out a series of recommendations that include:
- Develop effective data management practices. Federal agencies need to develop effective data management practices to identify, categorize, and secure sensitive data. They should also implement data minimization practices to reduce the amount of sensitive data stored.
- Improve security controls. Federal agencies should improve security controls to protect sensitive data. This includes implementing encryption, multi-factor authentication, and access controls to ensure that only authorized personnel have access to sensitive data.
- Maintain accurate inventories of PII. Federal agencies should maintain accurate inventories of PII to enable the identification and protection of sensitive data. They should also implement regular audits of their inventories to ensure that they are complete and accurate.
- Develop comprehensive incident response plans. Federal agencies should develop comprehensive incident response plans to respond effectively to cyberattacks and protect sensitive data. These plans should include procedures for identifying and mitigating cyber threats, notifying affected individuals, and preserving evidence for investigations.
- Increase cybersecurity training. Federal agencies should increase cybersecurity training for their employees to raise awareness about the importance of data privacy and security. This includes providing training on how to identify and respond to cyber threats, as well as best practices for data protection.
- Collaborate with other agencies and stakeholders. Federal agencies should collaborate with other agencies and stakeholders to share information and best practices for data privacy and security. This includes sharing threat intelligence, collaborating on incident response planning, and engaging with the private sector to promote cybersecurity awareness.
- Increase accountability. Federal agencies should increase accountability for data privacy and security. This includes implementing regular audits of their data privacy practices, establishing metrics to measure their progress in addressing deficiencies, and holding individuals and organizations accountable for data breaches.
Wake-up Call to Protect Sensitive Data at the Federal Level
The protection of sensitive data is critical to safeguarding individual privacy, national security, and the nation’s well-being. The federal government has identified information security as a high-risk area and has been making recommendations to address deficiencies in data privacy and security. However, the latest GAO report highlights that there are still significant deficiencies in implementing these recommendations.
Federal agencies must take urgent action to address these deficiencies, including developing effective data management practices, improving security controls, maintaining accurate inventories of PII, developing comprehensive incident response plans, increasing cybersecurity training, collaborating with other agencies and stakeholders, and increasing accountability for data privacy and security.
Until these recommendations are fully implemented, federal agencies will be more limited in their ability to protect private and sensitive data entrusted to them. The protection of sensitive data is essential to ensure the well-being of the nation and must be a top priority for federal agencies and critical infrastructure owners.
Using Kiteworks to Track, Control, and Secure PII
Just as zero trust is critical in protecting the network, infrastructure, and applications from malicious cyberattacks, it is just as important in protecting sensitive content, including PII. Content-defined zero trust uses least-privilege access and always-on monitoring and policies to track and control who accesses content, who can edit it, and to whom and where it can be shared or sent.
FedRAMP Authorized. Kiteworks is FedRAMP Authorized to Moderate Level Impact, which means the Private Content Network meets stringent security standards. Through its policy framework, agencies can quickly and easily set up user-specific permissions and access controls for data stored in the network. This ensures that only authorized users can access PII and that each user is only given access to the data they need.
Kiteworks hardened virtual appliance. In addition to the privacy policy framework, Kiteworks also offers a hardened virtual appliance. The appliance provides an additional layer of security and reliability by limiting access to the network and protecting user data from potential malicious actors. Kiteworks’ hardened virtual appliance helps to ensure that PII and other sensitive content that is digitally send and shared.
Double encryption at the file and volume levels. To ensure that PII is protected from potential threats, Kiteworks uses double encryption. Double encryption is a process that encrypts data twice—at rest with AES-256 encryption at the file level and then again at the volume level before writing it to the disk. By using this process, users can be sure that their data is protected from malicious actors, even if data is intercepted in transit.
AI-enabled anomaly detection. The Kiteworks Private Content Network uses AI-enabled anomaly detection to detect malicious activity and protect PII. Anomaly detection is a process where machine-learning algorithms identify possible threats, such as malicious software, and alert users to potential breaches or unauthorized access attempts.
Content Network is an excellent option. With Kiteworks, federal agencies can unify, track, control, and secure PII while meeting FedRAMP requirements. Kiteworks also accelerates CMMC (Cybersecurity Maturity Model Certification) Level 2 compliance, supporting nearly 90% of CMMC 2.0 Level 2 requirements out of the box.
Federal agencies and other government entities seeking help to protect PII and other sensitive content, in addition to countless private sector entities, can schedule a custom-tailored demo today to see the Kiteworks Private Content Network in action.
Additional Resources
- Webinar Why Security Best Practices Aren’t Enough in the Era of Data Privacy
- Webinar What DoD Suppliers Need to Know About CMMC 2.0
- Blog Post Get a Roadmap for CMMC 2.0 Compliance for DoD Contractors
- Blog Post Discover Data Governance and Digital Transformation in the Public Sector
- Report What You Need to Know About Managing Your Data Privacy Exposed Risk in the New Year