What Are ISO 27001, ISO 27017, and ISO 27018 Standards?
Every year, security breaches cost companies millions of dollars in losses and put their clients at risk. Data breaches will continue as organizations produce more sensitive data, share it with trusted third parties, and store it in the cloud. Businesses as a result must work harder than ever to ensure their data and systems are secure.

Need for Information Security Management
The average organization collects a great deal of data. This data includes sensitive customer data, intellectual property, and other data vital to an organization’s competitive edge and its ability to operate.
This data is so valuable that it is under constant threat of being stolen by cybercriminals, rogue nation-states, disgruntled employees, or some other type of bad actor. Having an effective security management strategy and architecture is critical because organizations need to protect themselves and their customers.
Information Security Standards
One way for businesses to improve their information security and protect their sensitive data is ISO certification. There are in fact several ISO standards, including, but not limited to, ISO 27001, ISO 27017, and ISO 27018. What’s the difference between these standards? Read on to learn about these three standards in detail.
Overview of the ISO 27000 Series of Standards
The ISO/IEC ISO 27000 series, often referred to as the ISO 27000 family, is a collection of internationally recognized information security standards. Developed jointly by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC), its primary purpose is to help organizations of any size and industry protect their information assets in a systematic and cost-effective way.
The cornerstone of the series is the ISO 27001 standard, which specifies the requirements for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS).
Other standards in the family provide guidance and support. For example, ISO 27002 offers a code of practice for implementing the controls listed in ISO 27001. Standards like ISO 27017 and ISO 27018 are extensions that address specific environments; ISO 27017 provides security controls for cloud services, while ISO 27018 focuses specifically on protecting Personally Identifiable Information (PII) in public cloud environments. Together, these ISO 27000 standards form a comprehensive framework for robust information security management.
Advantages of Adopting the ISO 27000 Series
- Improved Risk Management: The framework provides a systematic process for identifying information security risks and implementing controls to manage or reduce them, which is critical when using cloud services for operations or data storage.
- Enhanced Customer and Partner Trust: Certification, especially to standards like ISO 27018, signals a strong commitment to protecting sensitive data, including PII. This builds confidence and provides a significant competitive advantage.
- Stronger Compliance Posture: Adherence helps organizations meet a wide range of legal, statutory, regulatory, and contractual requirements, including data protection laws like Brazil’s LGPD and Europe’s GDPR.
- Global Recognition: As international standards, ISO certifications are recognized worldwide, facilitating business with partners and customers across the globe who demand proven security best practices.
ISO Standards Development Process Explained
ISO and IEC standards are developed through a formal, multi-stage process driven by expert consensus. It begins when a need is identified, and a proposal is made to a technical committee, such as JTC 1/SC 27 for information security standards.
If accepted, a working group of experts drafts the standard. This draft goes through several review stages: Committee Draft (CD), Draft International Standard (DIS), and Final Draft International Standard (FDIS). At each stage, ISO member bodies from around the world vote and provide comments. A standard is only published after achieving sufficient consensus at the FDIS ballot.
Understanding this rigorous and transparent process is crucial because it helps organizations anticipate future changes to key standards like ISO 27001, ISO 27017, and ISO 27018. By monitoring the development pipeline, businesses can proactively plan for transition periods, allocate resources, and adapt their management systems to stay compliant with the latest security and privacy best practices.
Explore Other Standards Within the ISO 27000 Family
- ISO/IEC 27002: A supplementary standard that provides a detailed reference set of generic information security controls and implementation guidance based on the controls in ISO 27001 Annex A.
- ISO/IEC 27005: This standard provides guidelines for information security risk management, supporting the general concepts specified in ISO 27001 and helping organizations conduct thorough risk assessments.
- ISO/IEC 27701: A critical privacy extension to ISO 27001, it specifies requirements for a Privacy Information Management System (PIMS) to help organizations protect PII and demonstrate compliance with data privacy regulations.
ISO/IEC 27001 Certification
The ISO/IEC 27001 certification is simply referred to as ISO 27001 certification. It is considered the international standard for information security. ISO 27001 sets out the specification for an information security management system (ISMS). It was first published in 2005 by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC). The certification was revised in 2013 and the latest version is officially ISO/IEC 27001:2013.
ISO 27001, part of the ISO 27000 series of information security standards, is a framework that helps organizations establish, implement, operate, monitor, review, maintain, and continually improve an ISMS.
ISO 27001’s best-practice approach helps organizations manage their information security by addressing people, processes, and technology. Certification to the ISO 27001 standard is recognized worldwide and indicates your ISMS is aligned with information security best practices.
ISO 27001 and ISO 27002: 2022 Updates and Future Changes
The 2022 revisions marked a significant modernization of the ISO 27000 series. ISO/IEC 27002:2022 was updated first, consolidating its 114 controls into 93 and restructuring them into four themes: Organizational, People, Physical, and Technological. It also introduced 11 new controls to address modern threats, including threat intelligence, data leakage prevention, and security for cloud services.
Subsequently, ISO/IEC 27001:2022 was published, aligning its Annex A with this new control set. Organizations certified to the 2013 version have a standard three-year transition period (until October 2025) to update their ISMS. Practical steps for transition include conducting a gap analysis between their current controls and the new ones, updating the Statement of Applicability (SoA) and risk treatment plan, and implementing any new controls required to address identified risks.
ISO 27017 Certification
ISO/IEC 27017:2015 provides information security guidelines for organizations that use cloud services. This international standard recommends and assists cloud service providers with the information security controls applicable to their cloud service. This code of practice also supplements the guidance of ISO/IEC 27002 and ISO/IEC 27001 standards by including implementation guidance and additional controls specific to cloud services. ISO/IEC 27017 provides a framework that advises aligning security management for cloud service and virtual and physical networks.
Purpose of ISO 27017
The main purpose of ISO 27017 is to address the specific information security risks associated with cloud computing. When people ask, “what is ISO 27017?”, the simplest answer is that it’s a code of practice offering additional, cloud-specific implementation guidance on top of the controls in ISO 27002.
It is designed for both cloud service providers (CSPs) and cloud service customers. For CSPs, it offers a framework for providing secure services. For customers, it provides guidance on what to expect and demand from their providers.
It clarifies the often-complex shared responsibility model in the cloud by recommending controls for virtual machine hardening, segregation in multi-tenant environments, and defining how customers and providers should manage security incidents and configurations collaboratively. Its ideal adopters are any SaaS, IaaS, or PaaS providers, as well as enterprises that rely heavily on these services for their operations.
Benefits of ISO 27017 Compliance
- Enhanced Customer Trust: An ISO 27017 certification demonstrates to customers that a cloud provider has implemented internationally recognized security controls specific to the cloud, boosting confidence in the service.
- Reduced Cloud Security Risks: By implementing targeted controls, organizations can better mitigate threats unique to cloud environments, such as insecure APIs, data segregation failures, and account hijacking.
- Simplified Vendor Due Diligence: For cloud customers, a provider’s adherence to ISO 27017 simplifies vendor assessments, as it confirms that a baseline of cloud security best practices is already in place.
- Clearer Security Responsibilities: The standard helps define and delineate the security roles of the cloud provider and the cloud customer, preventing critical gaps in security coverage.
ISO 27018 Certification
ISO 27018 is an international standard created specifically for data privacy in cloud computing. It is the standard for protecting personally identifiable information (PII) in cloud storage. The standard gives further implementation guidance to ISO 27002 for the controls published in ISO/IEC 27001 and provides extra guidance on PII protection requirements for the public cloud.
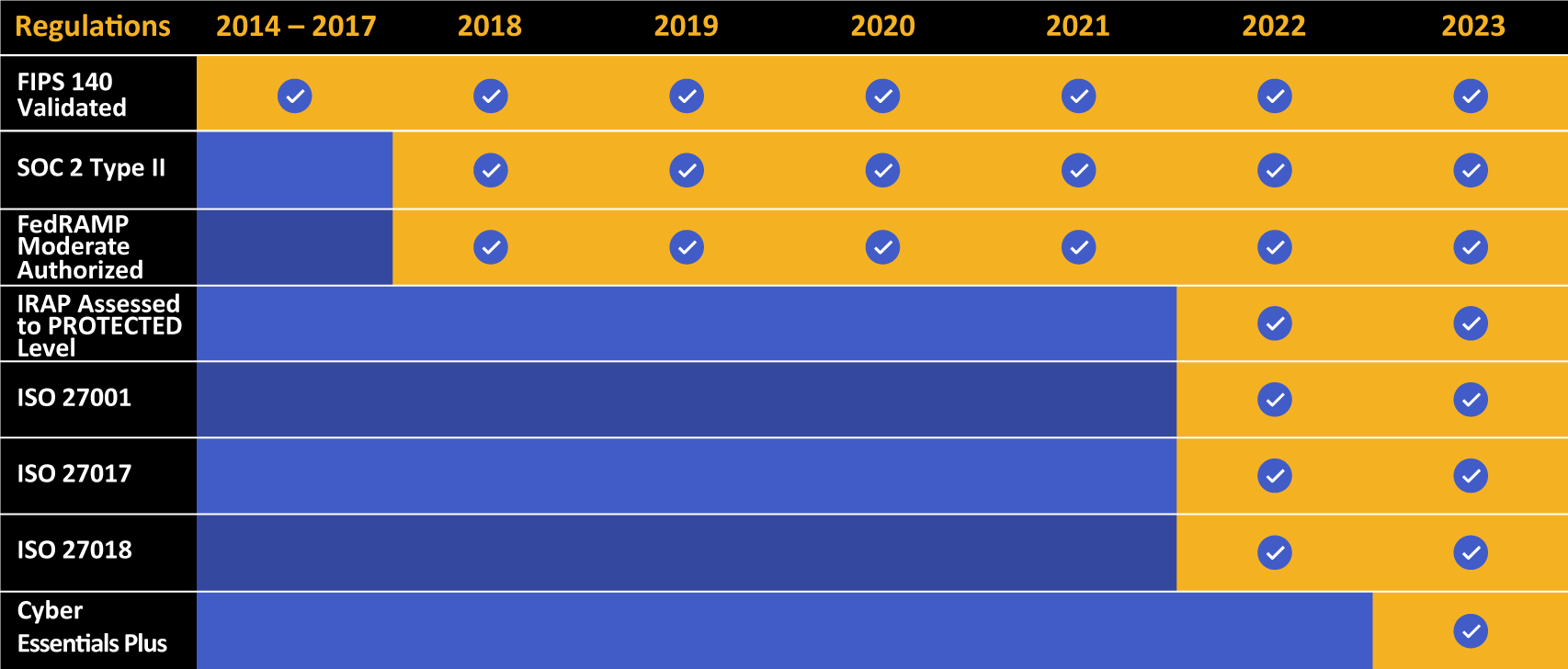
Kiteworks touts a long list of compliance and certification achievements.
ISO 27018 Controls List
- Consent and Choice: The standard mandates that the cloud provider (PII processor) cannot use personal data for marketing or advertising without explicit consent from the data subject. This places control directly in the hands of the individual.
- Purpose Limitation and Data Minimization: Providers must only process PII as instructed by their customer (the PII controller) and should not store more data than is necessary for the stated purpose, reducing the attack surface.
- Transparency: Providers must be transparent about their operations, including disclosing the geographic locations of data storage and the identity of any sub-processors, which is vital for data sovereignty and compliance assessments.
- Data Subject Rights: The full iso 27018 controls list ensures providers have procedures to help their customers fulfill data subject requests for access, correction, and erasure of their PII.
- Security and Breach Notification: ISO 27018 requires strong security measures, such as encryption of PII in transit and at rest, and mandates prompt notification to the customer following a data breach.
ISO 27701 and Its Relationship to ISO 27001/27018
ISO 27701 is a privacy extension to ISO 27001, providing requirements for a Privacy Information Management System (PIMS). An organization cannot achieve ISO 27701 certification without first implementing an ISO 27001 ISMS.
While ISO 27018 provides a code of practice for protecting PII specifically in public cloud services, ISO 27701 is much broader. It offers a comprehensive, certifiable management system for privacy that applies to all of an organization’s data processing activities, regardless of the environment. It provides separate guidance for PII controllers and PII processors.
Organizations seeking to demonstrate robust compliance with privacy laws like GDPR or Brazil’s LGPD should pursue ISO 27701, as it provides a more holistic and verifiable framework than ISO 27018 alone.
How Does ISO 27001 Work?
As ISO 27001 is considered the international standard for information security, let’s focus on this certification.
The ISO 27001 standard provides companies a framework to protect the organization’s confidentiality, integrity, and availability of information. The standard is designed to help organizations determine its risk assessment requirements and then define what needs to be done to manage those risks. The standard requires a company to list all controls implemented in the Statement of Applicability document.
The ISO 27001 standard is separated into two parts. The first part consists of 11 clauses, and the second part, Annex A, provides a guideline for 114 control objectives and controls. The first four clauses introduce the ISO 27001 standard. They include:
- Introduction
- Scope
- Normative references
- Terms and definitions
Clauses 5 through 11 provide ISO 27001 requirements that are mandatory for an organization that wants to comply with the standard.
What Are the Domains and Controls of the ISO 27001 Standard?
The ISO 27001 controls or safeguards are the practices to be implemented by organizations to reduce risks to acceptable levels. The controls can be technical, organizational, legal, physical, or human. There are also 14 domains listed in Annex A of the ISO 27001 standard. These domains are organized in sections A.5 to A.18. They cover the following:
Information security policies
This first domain has two controls that ask whether your organization has a clear set of policies about keeping its information systems secure. This domain sets the tone regarding the information security processes in place and how the organization’s personnel are informed of such processes. The controls include:
- Information security policy document
- Review of the information security policy
Organization of information security
The seven controls in this section provide the basic framework for implementing and operating information security by defining its internal organization. The controls include:
- Management commitment to information security
- Information security coordination
- Allocation of information security responsibilities
Human resource security
The nine controls in this section ensure that employees in an organization are hired, trained, and managed securely. These controls require every employee to be clearly aware of their information security responsibilities. The controls include:
- Roles and responsibilities
- Terms and conditions of employment
- Management responsibilities
- Screening
- Information security awareness, education, and training
- Disciplinary process
- Termination responsibilities
- Return of assets
- Removal of access rights
Asset management
ISO 27001 certification requires an organization to identify its information assets, assign ownership, classify them, and apply management processes based on those classifications. The 10 controls in this section ensure that the information security assets are identified, responsibilities for their security are designated, and that employees know how to handle these assets according to the predefined classification levels. The controls include:
- Inventory of assets
- Ownership of assets
- Acceptable use of assets
- Classification guidelines
- Information labeling and handling
Access control
The asset control domain is one of the largest sections with 14 controls. These controls limit access to information and information assets according to business needs. The controls provide for both physical and logical access. The controls include:
- Access control policy
- User registration
- Privilege management
- User password management
- Review of user access rights
- Unattended user equipment
- Clear desk and clear screen policy
- User authentication for external connections
- Equipment identification in networks
- Segregation in networks
- Secure log-on procedures
- User identification and authentication
- Password management system
- Limitation of connection time
Cryptography
An organization should have a documented policy for managing encryption. The two controls in this section provide the basis for properly using encryption solutions to protect information confidentiality, authenticity, and integrity. The controls include:
- Policy on the use of cryptographic controls
- Key management
Physical and environmental security
This is the largest domain that includes 15 controls to protect the organization’s information against real-world risks. The 15 controls provide for the prevention of unauthorized access to physical areas. They also provide for the protection of equipment and facilities from being compromised either by human or natural intervention. This domain also includes controls for employees who work remotely. The controls include:
- Physical entry controls
- Protecting against external and environmental threats
- Securing offices, rooms, and facilities
- Working in secure areas
- Public access, delivery, and loading areas
- Equipment siting and protection
- Supporting utilities
- Cabling security
- Equipment maintenance
- Security of equipment off-premises
- Secure disposal or reuse of equipment
- Removal of property
Operations security
This domain requires a company to secure the information processing facilities and systems constituting its ISMS. The 14 controls in this section ensure that the systems are secure and protected against data loss. The controls also address an organization’s need to record events, generate evidence, periodically verify vulnerabilities, and take actions to prevent audit activities from affecting operations. The controls include:
- Documented operating procedures
- Change management
- Segregation of duties
- Separation of development, test, and operational facilities
- Service delivery
- Monitoring and review of third-party services
- Managing changes to third-party services
Communications security
This domain has seven controls divided into two sections:
- The controls that prevent attackers from accessing sensitive information by exploiting vulnerabilities in the organization’s network security
- The controls for information transfer
Some examples of technical controls that help protect information within an organization’s systems and applications include firewalls, access control lists, logical or virtual segregation, and intrusion detection systems. The controls include:
- Information exchange policies and procedures
- Exchange agreements
- Physical media in transit
- Electronic messaging
- Business information systems
System acquisition, development, and maintenance
This domain covers how an organization manages information system changes over time. The 13 controls in this domain ensure that information security is considered (if not prioritized) when purchasing new or upgrading existing systems. The controls include:
- Information Security Requirements Analysis & Specification
- Securing Application Services on Public Networks
- Protecting Application Services Transactions
Supplier relationships
When seeking ISO 27001 certification, businesses often focus on internal operations and operational systems and overlook vendor risk management. The five controls in this section ensure that outsourced actions performed by vendors also use appropriate information security controls. The controls include:
- Information Security Policy for Supplier Relationships
- Addressing Security Within Supplier Agreements
- Information & Communication Technology Supply Chain
Information security incident management
In the event an organization is impacted by a security threat or incident, an incident management process should be in place to facilitate the report, assess, respond, and lessons learned to prevent a recurrence. The controls include:
- Reporting information security events
- Reporting security weaknesses
- Responsibilities and procedures
- Learning from information security incidents
- Collection of evidence
Information security aspects of business continuity management
This domain recognizes that information security can easily be forgotten when business is disrupted. The five controls in this domain ensure the continuity of information security management during such disruptions. The controls include:
- Including information security in the business continuity management process
- Business continuity and risk assessment
- Developing and implementing continuity plans including information security
- Business continuity planning framework
- Testing, maintaining, and reassessing business continuity plans
Compliance
This final domain details how an organization complies with information security laws. The eight controls in this section provide a framework to prevent legal, statutory, regulatory, and contractual breaches. The controls include:
- Identification of applicable legislation
- Intellectual property rights (IPR)
- Protection of organizational records
- Data protection and privacy of personal information
- Prevention of misuse of information processing facilities
- Compliance with security policies and standards
- Technical compliance checking
Why You Need a Third-party Organization to Get ISO 27001 Certified
ISO 27001 certification through an independent third-party registrar is a good approach to demonstrate your company’s compliance. The third-party organization can certify an organization’s information security management system against the requirements or the certification of individuals who are to implement or audit an organization against the ISO 27001 requirements.
Documenting and implementing information security-related requirements (such as risk assessment) are only part of the tasks if an organization wants ISO 27001 certification. The standard also requires organizations to perform internal audit management reviews and treat nonconformities and corrective actions.
How Long Does It Take an Organization to Become ISO 27001 Certified?
The time for the ISO 27001 certification process, from starting implementation to finishing the certification audit, depends on different variables such as the available resources, expertise, experience with the standard’s requirements, and others. However, the whole process generally takes from three to 12 months.
How Kiteworks Can Help Your Organization Achieve ISO/IEC 27001 certification
Kiteworks provides the framework to help organizations get the ISO/IEC 27001 certification. Kiteworks customers can demonstrate to their suppliers and customers their commitment to keep sensitive content communications private and compliant with global standards.
Kiteworks also meets several global compliance standards, including FedRAMP, General Data Protection Regulation (GDPR), SOC 2, Cybersecurity Maturity Model Certification (CMMC), and Federal Information Processing Standards (FIPS), among others.
Schedule a custom demo of Kiteworks to see how it works and to learn more about how it provides the framework for organizations to get ready for certification.



