IRAP Compliance | Australian Cybersecurity Standard
What is the Information Security Registered Assessors Program? What does it mean to be compliant with IRAP? Keep reading to find out.
What is IRAP? Information Security Registered Assessors Program (IRAP) assessors assist businesses doing work for the Australian government by independently assessing their cybersecurity posture, identifying risks, and suggesting mitigation measures. This helps ensure that those businesses have the right policies and controls for security to meet Australian Government Information Security Manual requirements.

What Is IRAP?
Australia, like other countries, has implemented significant cybersecurity laws and regulations to address the increasing challenges of hacking, fraud, and state-sponsored attacks. Like any other set of rules, qualified organizations must assess these regulations that can understand the law and how it is applied in real-world situations.
The Information Security Registered Assessors Program is a unique compliance program that attests to the ability of private and public organizations to meet cybersecurity requirements. Independent assessors employ two different sets of guidelines:
- The Information Security Manual: A document of guidelines focused on helping organizations build internal security frameworks based on risk assessment.
- The Protective Security Policy Framework (PSPF): A set of regulations that apply to Australian government agencies that emphasize common security standards.
IRAP sets policies and procedures in place for assessing the assessors against these security standards so that there is a standard of auditing that maintains high-quality security.
In order to earn IRAP certifications, applicants must adhere to several different qualifications:
- Be Australian citizens
- Behave ethically
- Meet all requirements to apply for Negative Vetting Level 1 (NV1), which provides “secret” level clearance
In addition to the above, each applicant must be able to demonstrate qualifications from two different categories, one per category:
Finally, the assessor must have five years of technical information and communication technology, with two years of experience securing systems against Australian government information security regulations. They must then complete the IRAP New Starter Training and assessor examinations.
As can be inferred from the table, it is clear that the potential IRAP assessor should be well-versed in several assessment techniques and certifications. Furthermore, the standard requires, above and beyond the knowledge of Australian cybersecurity law, potential understanding of CISSP, ISO assessment guidelines, Payment Card Industry (PCI) assessment standards, and other frameworks.
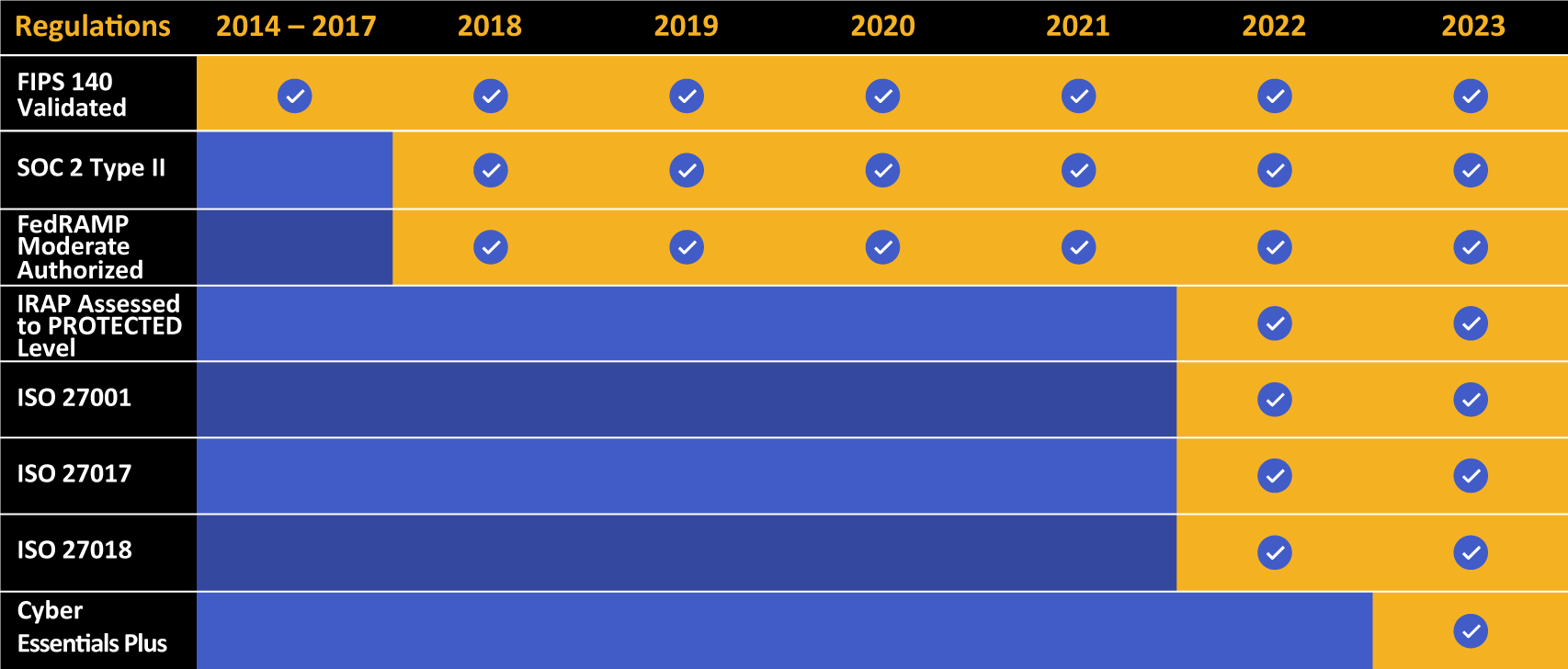
Kiteworks touts a long list of compliance and certification achievements.
Benefits of IRAP Accreditation
IRAP is a program that provides cybersecurity certification and accreditation for organizations that handle sensitive information. IRAP accreditation offers several benefits, including:
1. Increased Credibility and Trust With IRAP
IRAP accreditation is a recognized and trusted standard for cybersecurity. Organizations that are accredited are recognized as having met high standards for information security.
2. Compliance With Regulations With IRAP
IRAP accreditation helps organizations comply with government regulations and industry standards, such as the Australian Government Information Security Manual (ISM) or the Payment Card Industry Data Security Standard (PCI DSS).
3. Better Risk Management With IRAP
IRAP accreditation involves a rigorous risk assessment process that helps organizations identify and manage potential cybersecurity risks.
4. Improved Security Posture With IRAP
IRAP accreditation helps organizations improve their cybersecurity posture by identifying weaknesses and recommending and implementing security measures.
5. Competitive Advantage With IRAP
IRAP accreditation can give organizations a competitive advantage when bidding for contracts that require high levels of information security. It can also demonstrate to customers and partners that an organization takes data security seriously.
6. Cost Savings With IRAP
IRAP accreditation can lead to cost savings in the long run by preventing security incidents and avoiding the associated expenses of data breaches.
7. Access to Government Contracts With IRAP
IRAP accreditation is a requirement for organizations that want to work with the Australian government or organizations that require ISM compliance.
Overall, IRAP accreditation can help organizations establish a strong cybersecurity framework, build trust with stakeholders, and achieve compliance with regulations and industry standards.
What Is the Information Security Manual?
Part of what an IRAP assessor looks for is adherence to the ISM. The core focus of the ISM is to help organizations implement a cybersecurity framework based on risk management practices.
The ISM is codified cybersecurity advice provided by the Australian Cyber Security Centre as part of the Australian Signals Directorate, targeting chief information security officers and chief information officers in businesses and other enterprises. ISM is not strictly required by law unless the organization is working with the government or in another capacity where the law compels them to adhere to the ISM guidelines.
The ISM provides guidelines on an extensive set of IT and cybersecurity infrastructure. Much like the National Institute of Standards and Technology in the United States, the ISM covers guides for security in the following areas:
Roles in ISM
Addresses how organizations staff and maintain positions related to cybersecurity—most prominently, the CISO.
Incident Response in ISM
Pertains to how the organization detects, manages, and reports hacks or breaches.
Outsourcing in ISM
Covers how an organization selects and implements third-party services like cloud infrastructure and applications securely.
Documentation in ISM
Relates to how an organization documents security plans, policies, and implementations.
Physical Security in ISM
Addresses how organizations physically secure resources like data centers, workstations, offices, and IT equipment.
Personnel Security in ISM
Covers how to safely and securely hire, onboard, train, allow access, and terminate employees.
Communications Infrastructure in ISM
Relates to how the organization installs and protects communications technology, specifically cabling and Wi-Fi/RF communications.
Communication Systems in ISM
Covers how organizations protect communication technology like telephones, videoconferencing, fax machines, and digital VoIP services.
Enterprise Mobility in ISM
Details how organizations secure the use of IT systems connected to mobile devices, how those devices are secure, and how those devices are provisioned.
System Management in ISM
Covers how an organization logs events in a system, including incidents, and maintains secure logs for reporting and forensics.
Database Systems in ISM
Pertains to how databases are managed and secured as well as how those database platforms are selected.
Email in ISM
Relates to the use of secure email platforms, secure email with encryption, and avoidance of disclosing sensitive information via email.
Cryptography in ISM
Addresses minimum approved requirements for cryptography, including the use of Transport Layer Security (TLS), Secure Shell, and S/MIME.
For a complete list of guidelines, review the core ISM documentation.
What Is an IRAP Assessment?
An IRAP assessment is authorized and required under ISM for organizations either 1) required by law to seek ISM certification or 2) if an organization wants to achieve certification outside of any legal requirements.
Generally speaking, IRAP assessments are broken into two stages:
Stage 1 in an IRAP Assessment
The assessor consults with the assessed party to define the scope of the assessment, understand their IT systems, and reviews a series of documents related to the assessment, including:
- An overarching Information Security Policy and Threat Risk Assessment
- A System Security Plan
- A Security Risk Management Plan
- An Incident Response Plan
- A Standard Operating Procedures document
In addition, the assessor investigates the organization’s IT infrastructure as it relates to these documents and the scope of the assessment, highlighting compliance or lack thereof and documenting ways to mitigate systems that fall short of requirements.
Stage 2 in an IRAP Assessment
While Stage 1 is rather thorough, Stage 2 takes that further by digging deeper into the organization’s IT systems. This includes a site visit where the assessor interviews personnel, investigates actual system implementation, audits physical security measures, and generally determines if the actual reality of those systems matches the documentation from Stage 1. Additionally, the assessor provides a Stage 2 Security Assessment report that describes the state of the system and further suggestions for remediation.
Different categories of data call for more thorough assessments based on their classifications.
Latest Changes in IRAP
The Australian Signals Directorate (ASD) conducted an independent review of the program and released an updated policy and new IRAP Assessor Training on December 15, 2020. The changes to the program were made to improve the quality of cybersecurity advice provided by IRAP assessors and to enhance governance arrangements to provide additional assurance that assessors are performing their roles as independent third parties.
One of the major changes to the program is the requirement for IRAP assessors to maintain and demonstrate up-to-date cybersecurity knowledge. This helps ensure the advice provided by assessors is accurate, relevant, and reflective of the latest threats and trends in the industry. Additionally, IRAP assessors are required to maintain a Negative Vetting Level 1 security clearance, further ensuring their suitability for the role.
The revised five-day IRAP training course covers both IRAP and ISM fundamentals, providing a comprehensive understanding of the program and the standards required. The updated IRAP policy and training were co-designed by ASD with government and industry representatives through a series of consultative forums to improve the culture and governance of the program.
In conjunction with the release of the updated policy and IRAP Assessor Training, ASD is now accepting applications for IRAP assessors. Current IRAP assessors will have 24 months to meet the new requirements outlined in the updated policy.
Kiteworks IRAP Compliance Addressing Australian Cybersecurity Standard
The Australian government recognizes the threats to its federal and state agency supply chain, and IRAP plays an important role in ensuring that technology providers and suppliers use technologies that comply with a set of strict governance and security standards. Kiteworks is the only global vendor in the sensitive content communications space to be IRAP assessed to PROTECTED level controls.
For federal and state Australian agencies as well as companies conducting business with the Australian government, Kiteworks helps ensure that they retain control of privacy of their data hosted in single-tenancy clouds. The outcome is that there is no intermingling of data, metadata, or shared application resources. Kiteworks also enables third-party risk management (TPRM) by ensuring that sensitive content communications with third parties is protected and governed according to prescribed policies.
IRAP compliance is just one of a number of global compliance standards met by Kiteworks, which includes FedRAMP, General Data Protection Regulation (GDPR), SOC 2, Cybersecurity Maturity Model Certification (CMMC), Federal Information Processing Standard (FIPS), among others. Kiteworks’ single pane of glass through its CISO Dashboard provides organizations with a real-time view on what confidential content is being accessed and by whom, to whom it is being shared and transferred, over what communication channels, and when it occurred.
Schedule a custom demo of Kiteworks to see how it works and to learn more about Kiteworks’ IRAP assessment to PROTECTED level controls.


