CMMC Roadmap: Your Ultimate Guide for CMMC 2.0 Compliance
CMMC 2.0 provides the U.S. Department of Defense (DoD) with the means to protect private data from malicious attacks on its supply chain. It maps NIST 800-171 requirements to each of its Level 2 practices plus 24 additional NIST 800-172 requirements for Level 3.
DoD contractors must demonstrate compliance with the Cybersecurity Maturity Model Certification (CMMC) 2.0 through self-assessments as well as utilization of CMMC Third Party Assessor Organizations (C3PAOs). A phased implementation of CMMC 2.0 is expected to begin in Q1 2025 with CMMC in all DoD contractor and subcontractor contracts by 2028. In preparation for the final CMMC rule being published and going into effect Q1 2025, some DoD contractors are beginning to require their subcontractors to demonstrate compliance now.
About CMMC
The Cybersecurity Maturity Model Certification (CMMC) is a regulation put in place to enhance the cybersecurity procedures and standards within the Defense Industrial Base (DIB). It was created in response to growing concerns over the security of controlled unclassified information (CUI) within the supply chain.
CMMC impacts all organizations that contract with the Department of Defense (DoD), including small businesses, commercial item contractors, and foreign suppliers. According to the regulation, these organizations must be certified across five different maturity levels, each having specific cybersecurity practices and processes.
The regulation is crucial in providing a unified standard for implementing cybersecurity across the DIB that deals with sensitive information. It is designed to ensure complete protection of critical proprietary, strategic, and operational data from breaches and cyberattacks.
The benefits of demonstrating CMMC compliance include improved national security by ensuring data protection, increasing company credibility and marketability due to enhanced cybersecurity practices, and allowing continued eligibility for DoD contracts. It also helps organizations identify their cybersecurity strengths and weaknesses, resulting in more efficient and effective operations.
Assessing the Threat to the DoD Supply Chain
While CUI is not classified, the government believes CUI must be protected, as its breach could pose a threat to national security. In particular, DoD computer systems contain huge amounts of sensitive data, which includes CUI, that is sent, shared, received, and stored internally as well as with hundreds of thousands of contractors and subcontractors.
This data, both in transit and in motion, can be vulnerable to cyberattacks. A DoD contractor’s well-implemented cybersecurity posture, astute procurement due diligence, and contracting provisions may not necessarily eliminate all vulnerabilities associated with the sending, sharing, receiving, and storing of CUI and potential impact on the DoD and its contractors and subcontractors.
CMMC 2.0 simplifies what was originally released in CMMC 1.0, going from five levels to three and mapping each of the areas in Level 2 to NIST 800-171.
KEY TAKEAWAYS
-
CMMC 2.0 Compliance Roadmap
Phased implementation starting Q1 2025 involves self-assessments and third-party assessments, crucial for DoD contractors.
-
Impact on DoD Supply Chain
CMMC 2.0 ensures robust cybersecurity standards across the DoD supply chain, safeguarding sensitive information from breaches.
-
CMMC 2.0 Simplification
Condensing levels from five to three enhances accessibility, aligning with NIST standards and tailoring security measures to organizational needs.
-
Small Business Considerations
Small businesses face unique challenges complying with CMMC 2.0; resources and assistance programs are available to help meet requirements.
-
CMMC Certification Process
Certification process involves thorough planning, self-assessment, control implementation, and continuous monitoring.
CMMC 2.0: Who’s Impacted
All civilian organizations that do business with the government must comply with CMMC 2.0. The list of entities includes:
- DoD prime contractors
- DoD subcontractors
- Suppliers at all tiers in the Defense Industrial Base (DIB)
- DoD small businesses suppliers
- Commercial suppliers that process, handle, or store CUI
- Foreign suppliers
- Team members of DoD contractors that handle CUI such as IT managed service providers
CMMC level compliance is assigned to contractors and subcontractors based on the type of CUI and FCI that they handle and exchange.
CMMC 2.0 Jurisdiction: How Far Down the DoD Supply Chain Does CMMC Extend?
The CMMC standard applies to all entities within the DoD supply chain, including organizations that handle federal contract information (FCI), controlled unclassified information (CUI), and other sensitive information regardless of the specific organization with which the contract is placed. This includes both prime contractors and their subcontractors at any tier, including suppliers, vendors, and consultants.
CMMC 2.0 Levels: What’s Changed
Once again, CMMC 2.0 simplifies what was originally released in CMMC 1.0 and reduces the maturity level from five levels to three. The decision to reduce the five maturity levels to three was taken after rigorous evaluation and feedback from the industry. This was done for a multitude of reasons, the primary one being the aim to simplify the implementation process for defense contractors, particularly small to medium-sized businesses. The previous model with five levels was found to be overly complex and burdensome for some companies, often leading to confusion and hindering efficient compliance.
By condensing the framework to three distinct levels: Foundational, Advanced, and Expert, CMMC 2.0 aims to provide a more streamlined, manageable, and cost-effective solution for organizations. This ranged model allows for a more gradual progression in the implementation of security measures, making it easier for businesses to understand and fulfill their compliance requirements.
Another significant advantage is that the new three-tier structure correlates more appropriately to the diverse range of threats different organizations might face. It offers a more tailored approach to cybersecurity, aligning the level of security controls to the level of sensitivity and criticality of the information that a company handles.
Lastly, the reduction to three levels in CMMC 2.0 could lead to improved standardization across the defense industry. A simpler framework is more likely to be adopted consistently, thereby enhancing the overall cyber hygiene and resilience of companies within the supply chain.
In essence, the transition toward fewer maturity levels in CMMC 2.0 is an effort to balance the necessity of robust cyber defenses with the practical realities of business operations in the defense supply chain. The goal is to achieve a model that encourages compliance, reduces complexity, and accommodates the needs of a diverse set of organizations.
We’ll explore each level in much further depth below.
CMMC 2.0 Levels Explained
CMMC 1.0 had five maturity levels, but CMMC 2.0 reduced them to three tiers. CMMC 2.0 eliminates all maturity processes and unique CMMC 1.0 security practices and aligns closely to NIST 800 standards.
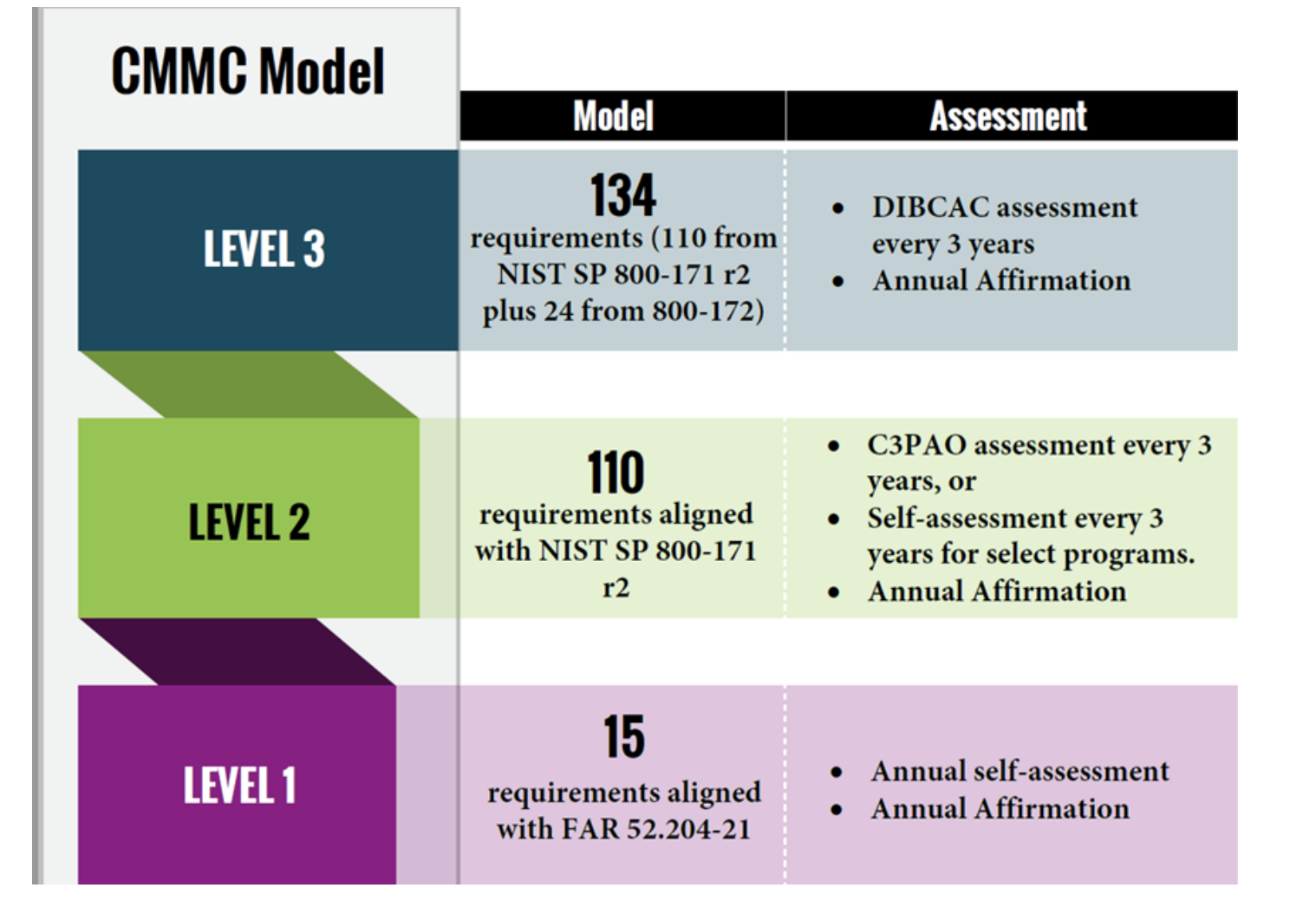
Table 1. CMMC 2.0 reduced the number of tiers from five to three and mapped Level 2 to NIST SP 800-171.
CMMC 2.0 contains three tiers of assessments based on the level of information access (see Table 1). They include:
CMMC 2.0 Level 1: Foundational
CMMC Level 1 requires annual self-assessment that has attestation from a corporate executive. This level encompasses the basic safeguarding requirements for FCI specified in FAR Clause 52.204-21.
CMMC 2.0 Level 2: Advanced
CMMC Level 2 is aligned with NIST SP 800-171. It requires triennial third-party assessments for contractors that send, share, receive, and store critical national security information. These third-party assessments are conducted by C3PAOs. Select contractors that fall into Level 2 only require annual self-assessments with corporate attestation.
This level encompasses the security requirements for CUI specified in NIST SP 800-171 Rev 2 per DFARS Clause 252.204-7012 [3, 4, 5].
CMMC 2.0 Level 3: Expert
CMMC Level 3 is aligned with NIST SP 800-172 and will require triennial government-led assessments. Level 3 will contain 24 requirements from NIST SP 800-172.
14 Core Security Domains of CMMC 2.0 Level 2
The 14 Core Security Domains of CMMC 2.0 represent the security practices and processes that organizations must conform to when handling CUI. The 14 domains are considered essential to protecting CUI and are the foundation on which the various levels of CMMC certification are built.
The 14 domains are:
1. Access Control (AC) – Restrict Access to CUI
A security practice that restricts access to CUI based on the need-to-know principle. Access Control also helps to ensure that only authenticated and authorized individuals, processes, and other entities have access to CUI by using different methods such as identification, authentication, authorization, and non-repudiation. Access Control also monitors and logs all access to CUI.
2. Audit and Accountability (AA) – Track and Report Who Accesses CUI
The process of verifying and tracking activities of users, processes, and other entities that access CUI. It involves logging access to CUI, tracking changes to CUI, and conducting periodic reviews of CUI to ensure integrity. The objective of Audit and Accountability is to ensure that the security of CUI is maintained, and to detect, investigate, and prevent unauthorized access and use of CUI.
3. Awareness and Training (AT) – Develop and Reinforce Proper CUI Handling
The practice of providing employees and contractors with security awareness training and other security-related education and training. This training should cover at least the basics of the organization’s security program, such as identifying security threats, handling and protecting CUI, proper data disposal, and responding to security incidents.
4. Configuration Management (CM) – Maintain Information System Integrity
A practice that establishes and maintains the integrity of an information system’s hardware, software, and documentation over its life cycle. It includes establishing and maintaining a baseline configuration, maintaining an inventory of components, monitoring changes to the baseline, and ensuring configuration accuracy. Configuration Management also includes securing and protecting system components and ensuring they are available when needed.
5. Identification and Authentication (IA) – Verify Only Authorized Personnel Can Access CUI
A security practice that involves verifying the identity of an individual, process, or other entity and ensuring that it is authorized to access CUI. It typically includes the use of passwords, biometrics, or tokens to authenticate and identify users, processes, or devices. It is important to ensure that only authorized individuals and processes gain access to CUI.
6. Incident Response (IR) – Detect and Respond to Security Incidents
The practice of identifying, responding to, and mitigating security incidents. Incident response involves detecting and responding to security breaches and other malicious activities, analyzing the impact of the incident, establishing a containment plan, and developing and implementing a plan for recovery. Incident Response also includes restoring systems to normal operation, investigating the source of the incident, and implementing measures to prevent similar incidents from happening in the future.
7. Maintenance (MA) – Keep Information Systems Running Optimally
The practice of maintaining the operational state of an information system, including its components and environment, to ensure that the system remains secure and operational. This includes preventive maintenance, corrective maintenance, and administrative maintenance. Preventive maintenance involves ensuring that system components and software are up to date and that security policies, procedures, and safeguards are properly implemented. Corrective maintenance involves identifying, responding to, and mitigating security incidents and other malicious activities. Administrative maintenance involves ensuring that system access rights are up to date and that security controls are being implemented properly.
8. Media Protection (MP) – Safeguard CUI Stored on Removable Media
The practice of protecting CUI stored on removable media, such as USB flash drives, CD-ROMs, and other types of external storage media. It includes protecting media from unauthorized access and modification, ensuring that media is not exposed to potential threats, and ensuring that media is disposed of properly. Media Protection also involves encrypting CUI stored on media and enforcing access control policies for media.
9. Personnel Security (PS) – Vet and Protect Employees Who Handle CUI
The protection of the security posture of personnel, both inside and outside the organization, who are associated with the handling or processing of CUI. It includes protecting personnel from potential threats, such as unauthorized access, modification, destruction, or theft of CUI. It also involves the implementation of policies and procedures that ensure personnel have the knowledge, skills, and abilities to protect CUI, and have the necessary background checks and other security-related qualifications.
10. Physical Protection (PE) – Maintain Proper Physical Security of Equipment and Facilities
A security practice that involves the protection of physical resources and assets, such as computers, networks, and other hardware and equipment, against unauthorized access, modification, destruction, or theft. It includes the implementation of various physical and logical security controls such as locks, guards, cameras, barriers, authentication devices, and firewalls. Physical Protection also involves enforcing access control policies and monitoring physical access to CUI.
11. Risk Assessment (RA) – Identify and Evaluate Risks to Information Systems
This practice involves conducting regular risk assessments to detect potential threats, vulnerabilities, and their impact on an organization. This domain ensures that risks are managed and mitigated effectively by establishing a baseline for risk management activities. Key practices include assessing cybersecurity risks, implementing risk response strategies, and updating risk assessments periodically to address evolving threats. This domain is critical for maintaining robust cybersecurity measures and protecting sensitive information within an organization’s infrastructure.
12. Security Assessment (CA) – Evaluate Security Requirements and Make a Plan to Meet the Requirements
The process of identifying the security requirements and determining that appropriate security controls are in place to meet those requirements. It includes identifying potential threats, conducting vulnerability and risk assessments, implementing appropriate security controls, and monitoring systems and networks for potential threats. Security Assessment also includes developing and implementing security policies, procedures, and guidelines, and monitoring compliance with these policies. Additionally, Security Assessment involves conducting periodic reviews of systems and networks to ensure that security controls are working as expected.
13. System and Communication Protection (SC) – Implement Controls to Identify and Repel Potential Threats
The security practice of protecting systems and communications from unauthorized access, modification, destruction, or theft. It involves the implementation of various physical and logical security controls, such as firewalls, encryption, authentication devices, access control policies, and monitoring systems and networks for potential threats. System and Communication Protection is a key aspect of security, as it helps to ensure that CUI is protected from unauthorized access, modification, destruction, or theft.
14. System and Information Integrity (SI) – Protect Information and Information Systems From Threats
An essential component of the CMMC 2.0 model that involves ensuring the accuracy, completeness, and reliability of information and systems. This includes implementing effective security controls to protect systems from malicious activities, monitoring systems for potential threats, and conducting periodic reviews to ensure information and systems remain secure and unaltered. In addition, System and Information Integrity involves preventing unauthorized access to information and systems, and protecting the confidentiality, integrity, and availability of information.
Which CMMC 2.0 Level Should DoD Contractors Pursue?
There are three levels of CMMC 2.0, ranging from basic cybersecurity hygiene to advanced cybersecurity practices. These levels are designed to be cumulative, meaning that each class builds upon the requirements of the previous story. The higher the group, the more rigorous the cybersecurity requirements.
To bid on DoD contracts requiring cybersecurity compliance, contractors must be certified at the appropriate level. This means that contractors must assess their cybersecurity practices and take steps to ensure that they meet the necessary level of compliance. For DoD contractors, the CMMC 2.0 levels mean that they must meet specific cybersecurity requirements to be eligible to bid on contracts with the DoD.
CMMC 2.0 and Small Business Contractors
Small businesses are a vital part of the Defense Industrial Base (DIB) and play a significant role in the economy. However, the implementation of CMMC 2.0 presents a unique set of challenges and considerations for these contractors. Small businesses face the same requirements as larger contractors, but they may not have the same resources and capabilities to comply with the standards. The CMMC 2.0 framework requires contractors to have adequate cybersecurity measures in place to protect CUI stored in their systems. Small businesses must understand the impact of CMMC 2.0 on their operations and take action to ensure regulatory compliance.
Small businesses face unique challenges and considerations when it comes to complying with the requirements of CMMC 2.0. The small business community needs to understand the impact of CMMC 2.0 on their operations and take proactive steps to meet the requirements. Small businesses must consider the cost of implementing adequate cybersecurity measures and training, the availability of cybersecurity expertise, and the need for regular assessments.
Impact of CMMC 2.0 on Small Businesses
The CMMC 2.0 framework requires contractors to undergo third-party assessments to verify that they have implemented adequate cybersecurity measures in their systems. Small businesses need to understand their level of readiness for these assessments and develop a plan to meet the requirements. Small businesses will need to invest in cybersecurity measures and training to ensure that they are prepared for the assessments. Failure to comply with the requirements of CMMC 2.0 could result in loss of existing contracts, inability to bid on new contracts, or even fines and penalties.
To learn more, read our blog post on CMMC compliance for small businesses.
CMMC Compliance Resources for Small Businesses
The DoD recognizes the importance of small businesses in the DIB and has developed resources and assistance programs to help them comply with the requirements of CMMC 2.0. The Small Business Administration (SBA) offers several programs, including the Small Business Innovation Research (SBIR) and Small Business Technology Transfer (STTR) programs, which provide funding for small businesses to develop new technologies and capabilities that can be used to meet the requirements of CMMC 2.0.
The CMMC Certification Journey: What to Expect
Accreditation for CMMC 2.0 Level 2 requires preparation and time to complete, both the self-assessment as well as the assessment completed by a C3PAO.
Understanding CMMC Self-Assessment vs. Third-Party Assessment Requirements
CMMC 2.0 utilizes different assessment types depending on the required level and the sensitivity of the information handled.
A self-assessment is an internal review conducted by the Organization Seeking Certification (OSC) against the applicable CMMC requirements. It involves documenting how controls are met and submitting results, along with an executive affirmation, to the DoD’s Supplier Performance Risk System (SPRS). Level 1 compliance requires an annual self-assessment. Some contracts requiring Level 2 compliance may also only require an annual self-assessment.
A third-party assessment, or certification assessment, is required for most contracts involving CUI at Level 2. This assessment must be conducted by an accredited CMMC Third-Party Assessment Organization (C3PAOs). C3PAOs are independent entities authorized by the CMMC Accreditation Body (CMMC AB) to perform CMMC assessments.
This process is significantly more rigorous than a self-assessment, involving detailed evidence review, interviews, and testing by certified assessors to verify the implementation and effectiveness of all 110 NIST 800-171 controls. A successful CMMC compliance audit results in a CMMC Level 2 certification valid for three years, subject to annual affirmations.
Level 3 assessments are conducted by government assessors from the Defense Industrial Base Cybersecurity Assessment Center (DIBCAC), not C3PAOs. Preparation for a third-party or government-led assessment requires more extensive documentation, mature processes, robust evidence collection, and coordination with the assessment team, compared to the internal focus of a self-assessment. Understanding the required assessment type early is crucial for planning the appropriate resources and effort for the CMMC certification timeline.
Documentation for CMMC Compliance
Accreditation requires establishment of periodic assessment of security controls to determine if they are effective in their application, documentation and updates to the system security plan (SSP), and documentation of a remediation plan (POA&M) to address practice control areas that failed the initial audit and timelines and resource requirements needed to rectify identified issues.
Due to these requirements, CMMC 2.0 experts recommend that organizations initiate an audit at least six months in advance. With Final Rule 32 CFR Part 170 published to the Fedral Register on October 15, 2024, phased implementation is starting in Q1 2025 and the time for DoD contractors and subcontractors to start is now.
The current DoD methodology for NIST SP 800-171—to which CMMC 2.0 Level 2 is mapped—self-assessment provides three scores for each of the 110 Level 2 practices with a weight of 1, 3, or 5.
Though final details on CMMC 2.0 scoring have not been released yet, indications are that the scoring and weighting methodology for NIST SP 800-171 will likely be reflected in those guidelines. Most importantly, of the 110 security controls in CMMC 2.0 (and NIST SP 800-171), 50 have a weight of 1, whereas the other 60 are worth 3 or 5 points.
Based on information released by a CMMC director at a cybersecurity event in April 2022, only practice controls with 1 point will be permitted a POA&M. Thus, for practice controls with weights of 3 or 5, no POA&M will be required; the deficiency must be remediated before business with the DoD can be conducted.
The DoD also plans to establish a minimum Supplier Performance Risk Score (SPRS) that must be achieved when POA&Ms are used to attain accreditation. At the same time, organizations will have a specified timeframe to address deficiencies, as POA&Ms will be time-bound with strictly enforced limits (likely 180 days).
Cost Considerations for CMMC Certification
Achieving CMMC certification involves various costs that organizations must budget for. These costs vary significantly based on the target CMMC level, the organization’s size and complexity, and its current cybersecurity maturity. Key cost components include:
- Assessment Costs: For Level 2 Certification, fees paid to a C3PAO for the formal assessment can range from $ tens of thousands to over $100,000, depending on scope complexity. Level 1 and some Level 2 require self-assessments, which have lower direct costs but still require internal resource allocation. Level 3 assessment costs are borne by the government (DIBCAC).
- Remediation & Preparation Costs: This is often the largest expense category. It includes investments in new security technologies (e.g., endpoint security, SIEM, MFA solutions), hardware upgrades, software licenses, developing or updating policies and procedures, and staff time dedicated to implementation. These costs can range from minimal (for mature organizations) to substantial (hundreds of thousands) if significant gaps exist.
- Consulting & Advisory Fees: Many organizations hire CMMC consultants, Registered Practitioners (RPs), or Registered Provider Organizations (RPOs) for gap analyses, readiness assessments, implementation support, and assessment preparation. Fees vary widely based on the scope of engagement.
- Internal Resources: Significant internal staff time is required for project management, documentation, training, control implementation, and supporting the assessment itself.
- Ongoing Maintenance: Compliance is continuous. Costs include annual affirmations, potential software subscription renewals, continuous monitoring tools/services, ongoing training, and triennial recertification assessments (for Level 2/3). While Level 1 costs are relatively low, achieving Level 2 certification can be a significant investment, particularly for small to medium-sized businesses.
Viewing CMMC as solely a cost center, however, overlooks the ROI: enhanced cybersecurity posture reducing breach risk, eligibility for DoD contracts essential for business continuity in the DIB, and potential competitive advantages. Organizations can optimize spending by leveraging existing compliant tools, conducting thorough gap analyses early, prioritizing remediation efforts, and utilizing available resources like those from the CMMC-AB and NIST.
The Benefits of CMMC 2.0
While few of us may be looking forward to another long journey when it comes to information security, the move from CMMC 1.0 to 2.0 is a critical and necessary one. The new requirements reflect an increased focus on protecting FCI and CUI.
This heightened level of protection is essential in today’s business environment, where data breaches are becoming more common and cyberattacks are growing in sophistication—elements that can pose a serious risk to the DoD supply chain.
The good news is that there are significant benefits to implementing CMMC 2.0. A few include:
- Reducing cyber risk across the DoD supply chain by establishing supply chain risk management standards to which all contractors and subcontractors must adhere.
- Building upon existing regulations (e.g., DFARS 252.204-7012, NIST SP 800-171) used to build trust by adding a verification standard for cybersecurity.
- A cost-effective means for small businesses—of which most DoD contractors and subcontractors are—to implement cybersecurity controls that reduce risk for themselves as well as the DoD and other public and private sector entities with whom they conduct business. Accreditation can afford a competitive advantage to a small business by helping them stand out from competitors that lack CMMC 2.0 certification.
CMMC 2.0 Compliance: Recipe for Success
As with CMMC 1.0, CMMC 2.0 is all about protecting FCI and CUI is paramount. With the transition to CMMC 2.0 complete, organizations must implement new controls and processes to safeguard this information.
While this may seem daunting, many resources are available to help you prepare for the transition. Taking the time to familiarize yourself with the new requirements will pay off in the long run and help ensure a smooth transition for your organization.
Build a CMMC 2.0 Compliance Strategy
Building a CMMC 2.0 compliance strategy requires careful planning and execution. Contractors must establish a compliance plan, define roles and responsibilities, and identify necessary resources and tools.
Establish a Compliance Plan and Policies
Developing a compliance plan is the first step toward achieving CMMC 2.0 compliance. It is essential to identify the scope of the compliance program, including the assets and systems that require protection. Additionally, it is essential to identify the level of CMMC maturity required for compliance. The compliance plan should include policies that outline data protection procedures, access controls, and data handling procedures. Policies should be consistent with the required CMMC level and the contractor’s operations. In addition, policies should be reviewed regularly to ensure compliance with the evolving CMMC standards.
Define Roles and Responsibilities
Roles and responsibilities should be defined clearly to ensure compliance with CMMC 2.0 standards. The compliance team should be made up of individuals who are knowledgeable about the CMMC standards and have experience in implementing compliance programs. It is essential to assign roles to individuals who have the authority to enforce compliance policies and procedures. The team should also include individuals from different areas of the organization, including IT, legal, human resources, and finance, to manage compliance issues effectively.
Identify Necessary Resources and Tools
To achieve CMMC 2.0 compliance, contractors need to identify and invest in the necessary resources and tools. For instance, contractors should invest in security tools, such as firewalls, antivirus software, and intrusion detection systems. Further, contractors should consider training employees on security awareness, vulnerability assessments, and incident response. These resources and tools should be aligned with the CMMC level and the contractor’s operations. Contractors should also consider working with third-party vendors to provide expertise and tools to achieve compliance.
Mapping CMMC Requirements
When building a CMMC 2.0 compliance strategy, DoD contractors and subcontractors must also map CMMC requirements, identify gaps, and implement controls. The contractors must adopt a continuous monitoring and improvement approach to maintain compliance with the evolving CMMC standards.
Gap Analysis Methodology for CMMC Compliance
A CMMC gap analysis systematically compares an organization’s current cybersecurity posture against the specific requirements of the target CMMC level. A methodical approach includes:
- Define Scope: Clearly identify the CMMC Assessment Scope (CAS), including all assets (people, processes, technology) that process, store, or transmit FCI or CUI. Use the official CMMC Scoping Guidance.
- Identify Target Level & Requirements: Determine the required CMMC level (1, 2, or 3) based on contract obligations and data handled. Gather the corresponding requirements (FAR Clause 52.204-21 for Level 1; NIST SP 800-171 Rev 2 for Level 2; NIST SP 800-171 + select NIST SP 800-172 controls for Level 3).
- Assess Current State: Review existing policies, procedures, configurations, and practices relevant to each CMMC requirement/assessment objective. Use the official CMMC Assessment Guides for detailed criteria.
- Map Controls: Align existing security controls to the CMMC requirements they address. Identify where controls are fully implemented, partially implemented, or missing.
- Collect Evidence: Gather objective evidence (e.g., policy documents, system configurations, log files, training records, interview notes) to substantiate the current state assessment for each requirement.
- Identify & Document Gaps: Clearly record each requirement that is not fully met. Detail the specific deficiency, the associated risk, and the CMMC practices/objectives affected. Common gaps often involve incomplete documentation (SSP, policies), inconsistent implementation of controls (like MFA or audit logs), lack of formal procedures, or insufficient security awareness training.
- Prioritize Gaps: Rank the identified gaps based on factors like the associated CMMC control weighting (for Level 2/3), potential risk impact, cost and effort required for remediation, and dependencies between controls.
- Develop Remediation Plan: Use the prioritized gap list to create or update the Plan of Action & Milestones (POA&M), outlining specific remediation tasks, responsible parties, resources needed, and target completion dates.
Identify Gaps and Implement Controls
Gaps identified during the mapping process should be addressed by implementing controls that need to be consistent with the required CMMC level and the contractor’s or subcontractor’s operations. Controls should be documented, tested, and monitored to ensure they effectively mitigate risk and meet the CMMC requirements. For instance, contractors may need to implement access controls to restrict access to sensitive data, implement data backup procedures, ensure the use of secure software development practices, and implement incident response procedures.
Commit to Continuous Monitoring and Improvement
Achieving CMMC 2.0 compliance is not a one-time event; it requires continuous monitoring and improvement of policies, procedures, and controls. The contractors should establish a continuous monitoring system to detect and respond to security incidents and identify any gaps that require remediation. Contractors should also conduct periodic assessments to ensure systems and policies are up to date with the evolving CMMC standards. Continuous improvement efforts can help contractors to maintain compliance and avoid costly security incidents.
Tools and Resources for CMMC Requirements Mapping
Mapping existing security controls to CMMC requirements can be complex, but several tools and resources can assist organizations:
- Official CMMC Documentation: The primary resources are the CMMC Model Overview, Scoping Guidance, and specific Assessment Guides for Level 1, Level 2, and Level 3, available on the official DoD CMMC website. These guides detail the assessment objectives for each practice, crucial for accurate mapping.
- NIST Publications: Since CMMC Level 2 aligns with NIST 800-171 Rev 2, and Level 3 incorporates elements of NIST 800-172, these documents are essential. NIST provides control catalogs, mappings, and supplementary guidance (like NIST SP 800-171A, the assessment objectives). These are available on the NIST website.
- Spreadsheet Templates: Many organizations start with spreadsheet templates (either custom-built or sourced from consultants/online resources) to list CMMC requirements, map existing controls, track evidence, document gaps, and manage POA&M items. While flexible, they can become cumbersome for complex environments.
- Governance, Risk, and Compliance (GRC) Platforms: Commercial GRC software often includes pre-built CMMC frameworks. These tools can automate mapping, centralize documentation and evidence, manage workflows for gap remediation, track progress, and generate reports for assessments and internal reviews. Options range in price and complexity, suitable for medium to large organizations seeking automation and integration.
- CMMC AB Marketplace: The Cyber AB maintains a marketplace listing authorized C3PAOs, RPOs, RPs, and licensed tool providers. This can help organizations find validated third-party tools and services specifically designed for CMMC preparation and assessment.
Choosing the right tools depends on factors like budget, internal expertise, the complexity of the IT environment, and the required CMMC level. Utilizing the official Assessment Guides alongside appropriate tools can significantly streamline the mapping process and improve the accuracy of the gap analysis.
Creating an Effective CMMC Compliance Roadmap
An effective CMMC compliance roadmap is a strategic project plan detailing the journey to achieving and maintaining the required certification level. Creating one involves these key steps:
Phase 1: Assessment & Planning
- Determine Level & Scope: Confirm the target CMMC level and precisely define the CMMC Assessment Scope (CAS).
- Conduct Gap Analysis: Perform a thorough assessment against the CMMC requirements for your target level (using official Assessment Guides and NIST SP 800-171/172 as applicable).
- Develop POA&M: Document all identified gaps, prioritize them, and outline remediation steps, responsibilities, and timelines.
- Resource Allocation: Estimate budget needs (tools, consulting, assessment fees) and allocate internal personnel resources.
- Secure Sponsorship: Obtain explicit buy-in and support from executive leadership.
Phase 2: Implementation & Remediation
- Execute POA&M: Systematically implement required technical controls, develop/update policies and procedures, and close identified gaps.
- Conduct Training: Train relevant personnel on new policies, procedures, and their CMMC responsibilities.
- Gather Evidence: Collect and organize objective evidence demonstrating compliance for each requirement.
- Update SSP: Maintain a living System Security Plan (SSP) reflecting the current implementation status of all controls.
Phase 3: Validation & Assessment
- Internal Review/Readiness Assessment: Conduct internal audits or engage a third party (like an RPO) for a readiness assessment to validate preparedness.
- Select C3PAO (if applicable): For Level 2 Certification, select an authorized C3PAO from the Cyber AB Marketplace.
- Undergo Formal Assessment: Participate in the self-assessment (Level 1/some Level 2) or the C3PAO/DIBCAC assessment (Level 2/Level 3 Certification).
Phase 4: Certification & Maintenance
- Address Findings: Remediate any assessment findings within the allowed POA&M timeframe (180 days for Level 2/3).
- Achieve Certification/Affirmation: Receive formal certification (Level 2/3) or submit annual affirmation (all levels).
- Continuous Monitoring: Implement processes for ongoing monitoring, regular reviews, and security posture maintenance.
- Plan for Recertification: Prepare for the triennial recertification assessment (Level 2/3). The roadmap should include clear milestones, realistic timelines (considering the overall CMMC timeline for implementation), assigned owners for tasks, dependencies, and regular progress reviews involving a cross-functional team (IT, Security, Legal, Contracts, HR). Flexibility is key, as the CMMC landscape and organizational needs may evolve.
How to Prepare for CMMC 2.0
A webinar featuring Optiv’s VP (and former FBI CIO) James Turgal and Kiteworks’ CISO and SVP of Operations Frank Balonis examined what DoD contractors and subcontractors need to do to prepare for CMMC 2.0. Following are some of the things they recommend DoD contractors and subcontractors keep in mind when building a roadmap to CMMC 2.0:
1. Unify File and Email Data Communications Onto One Platform
Identification of a technology platform and/or tools for sending, sharing, receiving, and storing FCI and CUI will address many of the Level 2 practice requirements. Having the right sensitive content communications platform in place for email, file sharing, automated file transfer, web forms, and application programming interfaces (APIs) will significantly streamline the accreditation process.
2. Know Your Private Data: FCI, CUI, or Both
Review your contracts and determine what information is classified FCI or CUI, if any. CUI is information relevant to the interests of the U.S. and includes sensitive, unclassified information that requires controls to safeguard or disseminate it. Specific categories of CUI can be found in the DoD CUI Registry.
3. Determine the Appropriate CMMC 2.0 Level
FCI is information provided by or generated under a government contract that has not been or is not intended for public release. Any company with FCI must achieve CMMC 2.0 Foundational Level 1 certification. This includes DoD contractors and subcontractors that do not even handle CUI. For those that handle CUI, CMMC 2.0 Level 2 certification is likely required.
4. Understand Your SSP and POA&M
RReview your system security plan (SSP) and POA&M documents. You should pose the following, among other, questions. Does your SSP cover the scope of where you have FCI and CUI? What changes have happened to your environment that need to be reviewed? What actions on your POA&M do you still need to complete? Plan out which of these you will do when and where the money will come from. (Important Reminder: POA&Ms will likely be eligible for only Level 2 practice requirements with a weighted score of 1.)
5. Get Your Documentation in Order
Get your integrated risk management documentation in order. Do you have written cybersecurity policies and procedures in place? Are they being followed? When was the last time you reviewed them? If you were to be audited, would your policies and procedures stand up to scrutiny?
6. Test and Validate Your Controls
Test and validate the controls you already indicate that you’ve implemented. Remember that security is a process, not a destination, and you should reassess your controls (preferably at least annually). Review your documented policies and procedures to be sure they are effective, efficient, and being followed.
7. Go Beyond the Basic Cybersecurity Controls
Go beyond basic compliance steps to perform effective cybersecurity for your critical business information. For example, CMMC doesn’t require that you back up your data, but ignoring backups in pursuit of compliance controls won’t provide any comfort if your business is the victim of ransomware. CMMC experts often tout, very accurately, that the required controls are just a minimum standard and aren’t necessarily indicative of providing active security of your company’s data.
Common CMMC Assessment Pitfalls to Avoid
Anything worth having requires work. And CMMC certification requires a lot of work as you have concluded. Complicating matters are the various pitfalls, or traps, defense contractors can fall into when pursuing CMMC compliance and ultimately CMMC certification. These are just a few of them:
- Misunderstanding or Incorrectly Defining Scope: Failing to accurately identify all assets (systems, people, facilities, external providers) that process, store, or transmit CUI/FCI leads to an incomplete assessment. Therefore, carefully follow CMMC Scoping Guidance and document the CMMC Assessment Scope (CAS) meticulously.
- Insufficient or Inaccurate Documentation: Lack of a comprehensive System Security Plan (SSP), missing policies/procedures, or outdated documentation are major failure points. Develop and maintain thorough, accurate documentation that clearly describes how each control is implemented to mitigate this risk.
- Policies vs. Practice (“Shelfware”): Having well-written policies that are not actually implemented or consistently followed in practice. Assessors verify implementation, not just documentation. As a result, ensure procedures are practical, trained on, and regularly audited internally.
- Inadequate Evidence Collection: Providing disorganized, incomplete, or irrelevant evidence to assessors wastes time and demonstrates unpreparedness. So use the CMMC Assessment Guides to understand required evidence types and collect/organize objective proof for each assessed objective beforehand.
- Weak Control Implementation: Technical controls (e.g., MFA, encryption, logging, access controls) may be deployed but misconfigured, inconsistently applied, or easily bypassed. Regularly testing and validating control effectiveness through internal audits and vulnerability scanning therefore becomes critical.
- Lack of Stakeholder Buy-in & Involvement: Treating CMMC as solely an IT problem without involving leadership, legal, HR, contracts, and end-users leads to gaps and resistance. As a result, form a cross-functional CMMC team with executive sponsorship.
- Treating Compliance as a One-Time Project: Failing to plan for continuous monitoring, annual affirmations, POA&M management, and recertification efforts. Therefore, build CMMC requirements into ongoing security operations and budget cycles.
- Underestimating Time and Resources: Rushing the process or not allocating sufficient budget and personnel leads to cutting corners and assessment failure. Developing a realistic CMMC timeline and budget based on a thorough gap analysis goes a long way in avoiding this pitfall.
CMMC Implementation Timeline
Based on what has been said and published by the CMMC body, the phased implementation for CMMC 2.0 begins soon. DoD contractors and subcontractors must begin today in determining if Level 1, 2, or 3 apply to their organizations. Self-assessments and third-party risk assessments by C3PAOs need to commence shortly, if not already.
Understanding the Four Phases of CMMC Implementation
The CMMC Final Rule (48 CFR) outlines a phased rollout for including CMMC requirements in DoD contracts, starting after the rule becomes effective. This gradual approach aims to allow the Defense Industrial Base (DIB) time to prepare. The four phases are:
Phase 1: Initial Implementation (Begins upon 48 CFR rule effectiveness, expected early 2025)
During this phase, DoD may include requirements for CMMC Level 1 Self-Assessment or Level 2 Self-Assessment in select solicitations and contracts. Organizations awarded these contracts must perform the required self-assessment, achieve a specific SPRS score, and submit results and affirmation annually. Monitor solicitations, conduct required self-assessment if applicable, develop SSP and POA&M.
Phase 2: (Begins ~12 months after Phase 1 starts)
DoD will begin incorporating requirements for CMMC Level 2 *Certification* Assessment into select solicitations involving CUI. Organizations bidding on or awarded these contracts will need to undergo an assessment by an authorized C3PAO and achieve Level 2 certification. Prepare for and schedule C3PAO assessment if pursuing relevant contracts.
Phase 3: (Begins ~24 months after Phase 1 starts)
DoD will start including requirements for CMMC Level 3 Certification Assessment in select solicitations involving CUI associated with critical DoD programs. These assessments are conducted by the government (DIBCAC). Prepare for DIBCAC assessment if handling high-value CUI under relevant contracts.
Phase 4: Full Implementation (Begins ~36 months after Phase 1 starts)
At this stage, it is expected that all DoD solicitations and contracts involving FCI or CUI will include the applicable CMMC level requirement (Level 1 Self-Assessment, Level 2 Self-Assessment, Level 2 Certification, or Level 3 Certification). Ensure full compliance at the required level for all relevant DoD business. It’s crucial to understand that the CMMC rulemaking timeline sets the start dates for these phases, indicating when DoD can include requirements. The specific timing for any given contractor depends on the contracts they pursue. Preparation should begin well before these phases impact specific contracts, considering the lengthy CMMC implementation process.
CMMC 2.0 Timeline: When Will CMMC Be in Contracts?
With Final Rule 32 CFR Part 170 published to the Federal Register on October 15, 2024, it is effective on December 16, 2024 and expected to show up in contracts in Q1 2025.
Starting in 2021, the DoD began incorporating CMMC requirements into requests for information (RFIs) and requests for proposals (RFPs) for select procurements. In other words, the DoD started including CMMC requirements as part of the evaluation criteria for some contracts.
While phased implementation of CMMC 2.0 will not be started until Q1 2025, this does not mean that DoD contractors and subcontractors can wait another year or two before concerning themselves with the order.
In addition, it is very likely that proposals by contractors and subcontractors will be evaluated based on their level of compliance with CMMC 2.0 Level 2 practices—certainly when the phased implementation begins. Indeed, Kiteworks is already finding that some DoD contractors are evaluating proposals from subcontractors based on CMMC 2.0 compliance. (See Table 2 for a quick timeline for CMMC.)
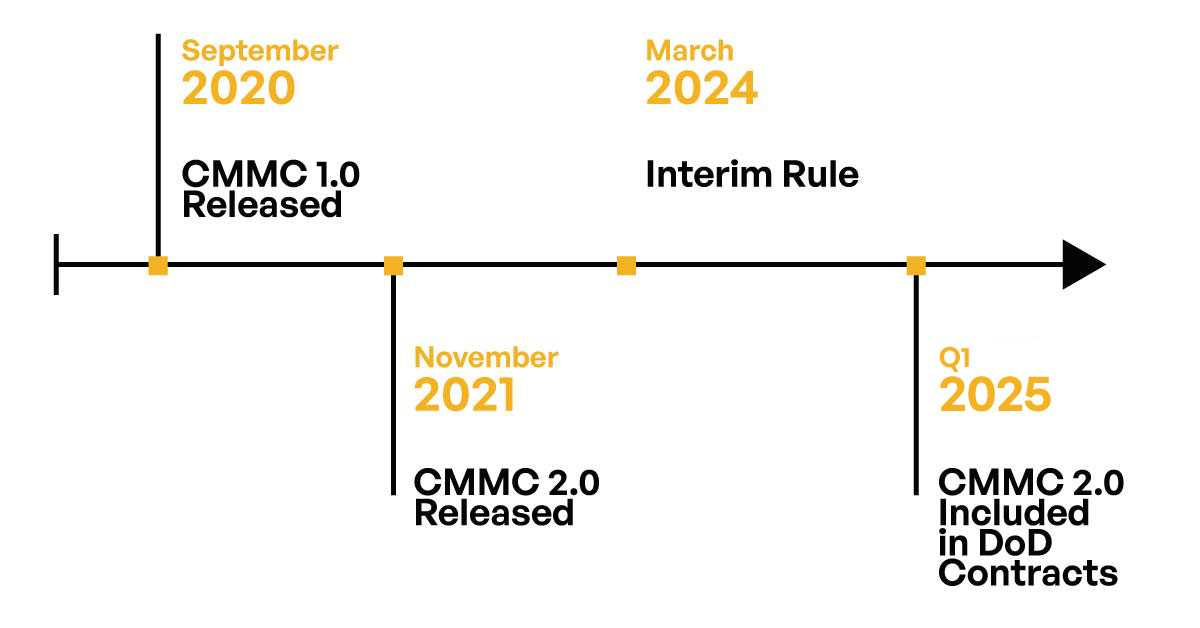
Table 2. Key milestones on the CMMC timeline.
Step-by-Step Guide to CMMC Certification
Consider these steps to accelerate the CMMC certification process:
- Determine Required Level & Scope: Identify the CMMC level (1, 2, or 3) mandated by your contracts or potential contracts. Use CMMC Scoping Guidance to define the precise boundaries (people, technology, facilities, processes) of your assessment environment (CMMC Assessment Scope – CAS). Est. Time: Weeks.
- Conduct Gap Analysis: Assess your current cybersecurity posture against the specific requirements/practices and assessment objectives detailed in the CMMC Assessment Guide for your target level. Identify all areas where requirements are not fully met. Est. Time: Weeks to Months.
- Develop System Security Plan (SSP): Create or update your SSP to document how each CMMC requirement within your scope is met or planned to be met. This is a mandatory document for all levels. Est. Time: Ongoing, initial draft Weeks to Months.
- Create/Update Plan of Action & Milestones (POA&M): Document all identified gaps from the analysis. Detail the remediation task, resources needed, responsible person, and scheduled completion date. (Note: POA&Ms have limitations, especially for higher-weighted controls, and must be closed within 180 days post-assessment for Level 2/3 Certification). Est. Time: Weeks.
- Implement Controls & Remediate Gaps: Execute your POA&M. Implement necessary security controls (technical, administrative, physical), update configurations, finalize policies and procedures, and conduct required training. Est. Time: Months to Year+ depending on gaps.
- Gather & Organize Evidence: Collect objective proof (e.g., logs, screenshots, policy documents, training records, interview notes) demonstrating that each required control is implemented effectively and consistently. Organize this evidence logically, mapping it to specific CMMC requirements/objectives. Est. Time: Ongoing during remediation.
- Perform Self-Assessment & Affirmation: Conduct a formal self-assessment against the CMMC requirements. For all levels, an annual affirmation by a senior company official is required, submitted to SPRS along with the assessment score. Est. Time: Weeks.
- (If Required) Select C3PAO/Prepare for DIBCAC: For Level 2 Certification, select an accredited C3PAO via the Cyber AB Marketplace. For Level 3, prepare for assessment by the government’s DIBCAC team. Est. Time: Weeks.
- Undergo Formal Assessment: Cooperate fully with the C3PAO or DIBCAC assessors. Provide access to documentation, systems, personnel, and facilities as needed. Est. Time: Weeks to Months, depending on scope & assessor schedule.
- Address Assessment Findings (if any): If the assessment identifies deficiencies allowing for a POA&M, remediate them and provide evidence of closure to the assessor within 180 days.
- Achieve Certification/Maintain Compliance: Upon successful assessment (and POA&M closure, if applicable), receive CMMC certification (valid 3 years for Level 2/3). Continue performing annual affirmations, maintain your security posture, and prepare for future recertification. Est. Time: Ongoing. The entire CMMC certification timeline from initial planning to certification can take anywhere from 6 months to 2 years or more, heavily dependent on starting maturity and resources.
CMMC Certification Process and Timeline
The CMMC certification process is typically arduous for most organizations, requiring time, money, and manpower. The process nevertheless favors organizations that are organized, focused, and nimble. The following list provides an overview of the CMMC certification process:
Prepare for CMMC Certification
Before a company can pursue its CMMC certification, they must understand the fundamentals and the requirements of the CMMC framework. Also, they must assess their current security posture against the requirements of the CMMC standard and identify any gaps.
Assign a Champion for CMMC Certification
Organizations must designate a champion to lead the process of securing CMMC certification. This champion should have the authority and responsibility to manage the entire process and drive it from start to completion.
1. Develop a Plan for CMMC Certification
A thorough plan should be in place that outlines the timeline for achieving certification. This plan should cover all activities, from mapping their system environment to CMMC requirements to training their personnel.
2. Perform Self-assessment for CMMC Certification
Organizations must perform a self-assessment to identify any gaps between the current system environment and the CMMC requirements. This will help guide the development of their security program.
3. Implement Required Controls for CMMC Certification
After performing their self-assessment, the organization must implement any required controls to address the gaps identified. This step may include purchasing additional security hardware or software, as well as establishing appropriate policies and procedures.
4. Conduct a CMMC Readiness Assessment
Organizations may need to hire an independent third-party assessor to conduct a readiness assessment to ensure they are prepared for the formal certification process.
5. Obtain CMMC Certification
After the organization has satisfied all of the CMMC requirements, they should complete the certification process and receive their CMMC certification.
6. Maintain CMMC Certification
Organizations must ensure they are continuously and regularly monitoring their systems to ensure they remain compliant with CMMC requirements.
Generally, organizations can expect the process to take approximately 6-9 months, depending on the organization’s resources and the complexity of the system environment. After the initial preparation, the organization should spend 3-4 months mapping their system environment, implementing controls, and conducting a readiness assessment. The certification process should take another 3-4 months, including the assessment, certification, and any necessary remediation. Finally, the organization should plan for ongoing monitoring of their system environment to ensure they remain in compliance.
The costs associated with obtaining CMMC certification vary depending on the size and complexity of the organization. Smaller organizations may be able to keep costs relatively low by relying primarily on internal resources. For larger organizations, costs can range from tens of thousands to several hundred thousand dollars. This includes expenses for hiring a third-party assessor, purchasing new security hardware or software, and providing training for personnel.
Despite the cost, process, and timeline involved in achieving CMMC certification, it is worth the effort, as it can help organizations protect their network and information. CMMC certification also increases an organization’s credibility and trust with their clients, as certified organizations can demonstrate that they are taking information security seriously and are committed to protecting their data. Additionally, obtaining CMMC certification may give an organization a competitive edge in the marketplace, as the certification is becoming increasingly important for organizations seeking to do business with DoD contractors.
Timeline Expectations for Different Organization Sizes
The time required to achieve CMMC certification varies significantly based on organization size, complexity, target level, and starting cybersecurity maturity. Here are general expectations for the CMMC certification timeline:
Small Businesses (e.g., < 50 employees, Level 1 or basic Level 2 scope)
- Preparation & Remediation: If starting with low maturity, expect 6-12 months to understand requirements, perform gap analysis, implement basic controls (Level 1) or NIST SP 800-171 controls (Level 2), and develop documentation (SSP).
- Assessment: Level 1 self-assessment might take days/weeks. Level 2 C3PAO assessment scheduling and execution could take 1-3 months, plus up to 180 days for POA&M closure if needed.
- Total Estimated CMMC Timeline: 8-18 months for Level 2 certification readiness and assessment. Level 1 readiness can be quicker.
Medium Businesses (e.g., 50-500 employees, standard Level 2 scope)
- Preparation & Remediation: 9-18 months is common, involving more complex gap analysis, potentially significant control implementation or upgrades, policy development, and evidence gathering across more systems/users.
- Assessment: C3PAO assessment process (scheduling, assessment, reporting, POA&M closure) might take 3-5 months.
- Total Estimated CMMC Timeline: 12-24 months for Level 2 certification.
Large Businesses (e.g., 500+ employees, complex Level 2 or Level 3 scope)
- Preparation & Remediation: 12-24+ months due to complex environments, multiple locations, legacy systems, extensive documentation needs, and coordination across large teams. Level 3 adds NIST SP 800-172 requirements, extending prep time.
- Assessment: Level 2 C3PAO or Level 3 DIBCAC assessment processes can take 4-6+ months, factoring in complexity and potential POA&Ms.
- Total Estimated CMMC Timeline: 18-36+ months. These are estimates. Factors like using experienced consultants, leveraging compliant platforms, strong project management, and high initial maturity can shorten the timeline. Conversely, significant gaps, limited resources, or scope complexity can extend it. Organizations must factor this lengthy preparation CMMC timeline into their strategic planning, especially considering the phased rollout starting in 2025.
What is the Deadline for CMMC 2.0 Compliance?
There is no single, universal CMMC compliance deadline by which all DoD contractors must be certified. Instead, CMMC 2.0 compliance requirements are being phased into DoD contracts over several years, starting in 2025. The deadline for a specific organization depends on when CMMC requirements appear in the contracts they hold or bid on. Key dates shaping the timeline:
- December 16, 2024: The CMMC Program Final Rule (32 CFR Part 170) becomes effective. This allows the DoD to begin the implementation process outlined in the corresponding (forthcoming) 48 CFR rule.
- Q1 2025 (Expected): Phased implementation begins (Phase 1). DoD can start including CMMC Level 1 or Level 2 self-assessment requirements in select new contracts. This is effectively when CMMC goes into effect for some contractors.
- ~Q1 2026 (Expected): Phase 2 begins. DoD can start including CMMC Level 2 Certification Assessment requirements in select new contracts. This is when CMMC certification will be required for organizations pursuing these specific contracts.
- ~Q1 2028 (Expected): Phase 4 (Full Implementation) begins. At this point, CMMC requirements are expected to be included in all applicable new DoD contracts involving FCI or CUI. This represents the closest thing to an ultimate “CMMC 2.0 deadline” for the entire DIB to be prepared for new contract requirements. Therefore, the critical “deadline” is contract-dependent.
However, because the preparation and assessment CMMC certification timeline can take 6-24+ months, organizations must start preparing now. Waiting until a CMMC clause appears in a solicitation will likely be too late to meet the requirement and successfully compete for the contract.
The effective CMMC compliance deadline is driven by business necessity and contract pursuit strategies, necessitating proactive preparation aligned with the phased rollout.
Final CMMC Rule: What You Need to Know for 2025
With the CMMC 2.0 Final Rule (32 CFR Part 170) effective December 16, 2024, and phased implementation via contract clauses (48 CFR) expected to begin in Q1 2025, here’s what DIB organizations need to prioritize for 2025:
- Phased Rollout Starts: Expect CMMC requirements to begin appearing in *select* new DoD solicitations starting early in 2025 (Phase 1). Initially, this will likely involve Level 1 Self-Assessment (for FCI) and Level 2 Self-Assessment (for CUI in some contracts).
- Self-Assessments are Key: If you handle FCI or CUI and pursue contracts included in Phase 1, you’ll need to conduct an accurate self-assessment against the required level (Level 1 = 15 FAR controls; Level 2 = 110 NIST SP 800-171 controls), calculate your SPRS score, and submit it annually with an executive affirmation.
- SSP is Mandatory: A comprehensive System Security Plan (SSP) detailing how you meet (or plan to meet) each required control is essential for both self-assessments and certification assessments. Start developing or refining yours now.
- POA&M Understanding: Plans of Action & Milestones (POA&Ms) are allowed for Level 2 (self-assessment and certification) but not Level 1. They have strict requirements, including a 180-day closure deadline post-assessment for certification and potential limitations on which controls can be on a POA&M. Plan remediation actively.
- Prepare for Level 2 Certification: While Level 2 *Certification* requirements (via C3PAO assessment) aren’t expected in contracts until Phase 2 begins (~Q1 2026), the long preparation timeline means organizations needing Level 2 certification should use 2025 for intensive preparation: gap remediation, evidence gathering, and potentially engaging RPOs for readiness reviews.
- Focus on NIST SP 800-171: For any organization handling CUI (targeting Level 2), mastering the 110 controls in NIST SP 800-171 Rev 2 is the core technical task for 2025 preparation efforts.
- Monitor Contracts: Closely monitor RFIs, RFPs, and contract modifications for the inclusion of CMMC clauses (DFARS 252.204-7021 and others). Prime contractors will also begin flowing down requirements.
In summary, 2025 marks the beginning of the contractual CMMC implementation. Prioritize understanding your required level, scoping, conducting self-assessments accurately, developing robust documentation (SSP/POA&M), and actively remediating gaps, especially if Level 2 Certification is anticipated for future contracts.
Accelerate Your CMMC 2.0 Level 2 Compliance Process With Kiteworks
The CMMC 2.0 framework includes far-reaching practice controls. DoD contractors and subcontractors—certainly those requiring Level 2 accreditation—must seek out CMMC experts that can help aid them on their journey.
Consulting practices like Optiv have the expertise to map Level 2 practice requirements to your existing controls and technology and guide you through the process of remediating POA&Ms and engaging with a C3PAO for assessment and accreditation.
At the same time and as noted above, DoD contractors and subcontractors can accelerate their CMMC 2.0 Level 2 accreditation process by ensuring they have the right sensitive content communications platform in place.
Many organizations admit to using numerous tools when it comes to sending, sharing, receiving, and storing private content like CUI and FCI. For example, Kiteworks found in our Sensitive Content Communications Privacy and Compliance Report that over two-thirds of organizations rely on four or more systems of record. This increases complexity and inefficiencies as well as risk.
Rather than using a disaggregated set of tools for digital exchange of private content like CUI and FCI, growing numbers of organizations—at 3,800 and counting today—use the Kiteworks platform. Because Kiteworks is FedRAMP Authorized, unlike many other solution options in the marketplace, it complies with or partially complies with a higher number of CMMC 2.0 Level 2 practice areas than those competitive options. Rather than demonstrating compliance with around 50% of CMMC practice requirements, DoD contractors and subcontractors using Kiteworks-enabled Private Content Networks benefit from support for nearly 90% of Level 2 requirements out of the box.
DoD contractors and subcontractors looking to surge out of the gate and achieve CMMC 2.0 Level 2 accreditation ahead of their competitors need to take a serious look at Kiteworks. Schedule a custom demo tailored to your needs today.
FAQs
CMMC Level 1 (Foundational): Focuses on the protection of Federal Contract Information (FCI) and consists of 15 basic safeguarding requirements from FAR Clause 52.204-21. CMMC Level 2 (Advanced): Focuses on the protection of Controlled Unclassified Information (CUI) and incorporates all 110 security requirements from NIST 800-171 Rev 2. CMMC Level 3 (Expert): Focuses on protecting CUI with enhanced requirements, encompassing a subset of 24 NIST 800-172 security requirements with DoD-approved parameters.
CMMC 2.0 implementation begins with Phase 1 (Initial Implementation), which starts when the 48 CFR Rule becomes effective and requires Level 1 or 2 Self-Assessment requirements. Phase 2 commences 12 months after Phase 1 begins and introduces the requirement for CMMC Level 2 Certification. Next, Phase 3 starts 24 months after Phase 1 and adds the requirement for CMMC Level 3 Certification. The final stage, Phase 4 (Full Implementation), begins 36 months after Phase 1 and represents complete implementation, where all solicitations and contracts must include applicable CMMC Level requirements. The DoD maintains the flexibility to implement CMMC requirements ahead of these planned phases for specific procurements as needed.
Organizations in the Defense Industrial Base (DIB) sector that process, store, or transmit Federal Contract Information (FCI) or Controlled Unclassified Information (CUI) must comply with CMMC. This includes over 220,000 companies that support the Department of Defense (DoD) supply chain – from prime contractors to subcontractors. These organizations contribute to DoD systems, networks, installations, capabilities, and services, and must meet CMMC requirements to protect sensitive defense information.
CMMC Level 2 focuses on protecting Controlled Unclassified Information (CUI) and incorporates 110 security requirements specified in NIST 800-171 Rev 2. This level covers key domains like access controls, incident response, security assessment, and system integrity.
There are 14 domains in the CMMC 2.0 framework. Each domain has specific requirements that defense contractors must meet in order to demonstrate CMMC compliance. These domains/requirements include: Access Control, Awareness and Training, Audit and Accountability, Configuration Management, Identification & Authentication, Incident Response, Maintenance, Media Protection, Personnel Security, Physical Protection, Risk Assessment, Security Assessment, System & Communications Protection, and System and Information Integrity.
Additional Resources
- Webinar What Optiv and Kiteworks Recommend for DoD Contractors and Subcontractors for CMMC 2.0
- Guide A Detailed CMMC 2.0 Guide for DoD Contractors and Subcontractors
- Video What Kiteworks CISO Frank Balonis Thinks About CMMC 2.0
- Article What Is Cybersecurity Maturity Model Certification?
- Blog Post What Is CMMC Security Compliance?
