FedRAMP Certification Process
The Federal Risk and Authorization Management Program, or FedRAMP, is a government-wide program that provides a standardized approach to security assessment, authorization, and continuous monitoring for cloud-based services. This program is designed to help organizations and industries that handle sensitive content communications ensure that their data is protected and secure. This article will provide an overview of FedRAMP and its certification process, including its purpose, certification requirements, assessment and authorization, security controls, benefits, and cost and time.
FedRAMP Overview
The Federal Risk and Authorization Management Program (FedRAMP) is a government-wide program that provides a standardized approach to security assessment, authorization, and continuous monitoring for cloud products and services used by the U.S. federal government. The goal of the program is to ensure that cloud solutions used by the federal government meet a minimum-security standard and are sufficiently secure to protect the confidentiality, integrity, and availability of the data. FedRAMP uses the NIST CSF (National Institute of Standards and Technology Cybersecurity Framework) to provide a common baseline across government agencies. The program requires cloud service providers to go through a three-step process that includes assessment, authorization, and continuous monitoring. FedRAMP also provides a common set of policies, processes, and procedures that help agencies manage the risk associated with cloud services.
Use of FedRAMP in Sensitive Content Communications
FedRAMP is used by organizations and industries to ensure secure data sharing. With FedRAMP Authorization, organizations can ensure that their data is protected and in adherence to the highest standards.
One of the critical elements of FedRAMP that sets it apart from other security frameworks is its thorough and rigorous security assessment process. Before a cloud provider can receive FedRAMP Authorization, it must undergo an independent, third-party assessment of its security controls (by a C3PAO). This assessment covers not only the technical aspects of security, such as data encryption and network architecture but also the operational aspects, such as incident response and change management.
Another critical factor that makes FedRAMP highly secure is its focus on continuous monitoring. FedRAMP-authorized cloud providers must regularly monitor their systems and report any security incidents or changes to their environment. This helps to ensure that vulnerabilities are identified and addressed promptly and that the security posture of the cloud environment remains strong over time.
In addition to these technical and operational elements, FedRAMP also considers the broader regulatory environment. It is designed to align with other government security frameworks, such as the National Institute of Standards and Technology (NIST) 800-171 and the Federal Information Security Management Act (FISMA), and industry standards, such as ISO 27001. This helps to ensure that technology providers meet the highest security standards, both in terms of their technical controls and general security practices.
FedRAMP Certification Requirements
To become FedRAMP certified, an organization must meet specific requirements, including developing a security assessment plan, completing a security assessment, and submitting an authorization package. The security assessment plan must outline the security controls and processes to protect sensitive information. An authorized third-party assessor must conduct the security assessment session. The authorization package must include security assessment results and be reviewed and approved by a FedRAMP-authorized third-party assessor.
FedRAMP Assessment and Authorization
The FedRAMP assessment and authorization process begins with developing a security assessment plan, which outlines the security controls and procedures used to protect sensitive information. The authorization package must be reviewed and approved by a FedRAMP-authorized third-party assessor. It must consist of the security assessment results, a plan for continuous monitoring, and a statement of authorization to operate. An authorized third-party assessor must conduct the security assessment, and the evaluation results must be included in the authorization package.
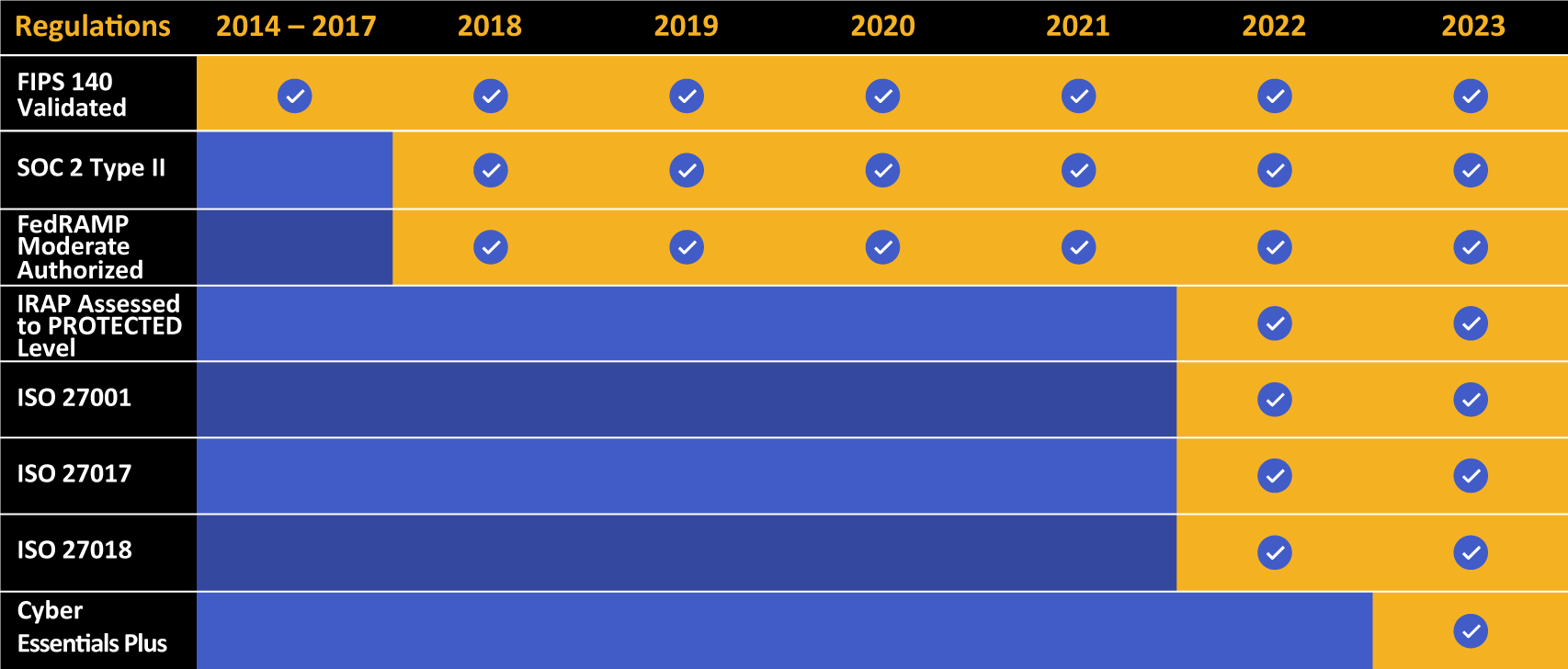
Kiteworks touts a long list of compliance and certification achievements.
FedRAMP Security Controls
The security controls used in FedRAMP are designed to provide a comprehensive approach to security assessment, authorization, and continuous monitoring. Organizations must demonstrate that they have implemented these controls and have the processes in place to ensure the security of sensitive information. Here is brief overview of each FedRAMP security control:
Access Control
Access control is a security measure that enforces rules to protect information and resources. Access control is a key element of the Federal Risk and Authorization Management Program (FedRAMP) and is commonly used to implement the standards set by FedRAMP to protect government data. Access control includes identifying, authenticating, and authorizing users, limiting and controlling access to systems, and managing changes, such as granting and revoking access rights. Access control is used to prevent unauthorized users from accessing systems, applications, and data. Additionally, access control ensures that only authorized individuals can access, modify, or delete information, thus preserving the confidentiality, integrity, and availability of resources.
System Maintenance
System maintenance involves regularly updating and patching systems and software to address any potential vulnerabilities and ensure that they remain secure. This includes monitoring systems for potential security threats and taking proactive measures to mitigate them. System maintenance helps organizations to prevent security breaches, protect sensitive information, and maintain the integrity of their systems.
Incident Response
Incident response refers to the processes and procedures that organizations have in place to respond to security incidents and minimize their impact. This includes developing a plan for responding to security incidents, identifying the resources and personnel required to respond, and ensuring that all stakeholders are aware of the incident response procedures. By having a well-defined incident response plan in place, organizations can quickly and effectively respond to security incidents and minimize their impact.
Backup and Recovery
Backup and recovery involve creating regular backups of sensitive information and ensuring that it can be recovered in the event of a disaster or security breach. This includes establishing backup procedures, testing backups to ensure that they are effective, and having a plan in place for restoring data in the event of a failure. By having robust backup and recovery procedures in place, organizations can ensure that their data is protected and recoverable in the event of a disaster or security breach.
System and Information Integrity
System and information integrity involves ensuring that systems and information remain intact and protected from unauthorized access, tampering, or corruption. This includes implementing security measures to protect systems and information, regularly monitoring systems for potential security threats, and having procedures in place to detect and respond to security incidents. By maintaining system and information integrity, organizations can ensure that their systems and data remain secure and protected from potential threats.
Configuration Management
Configuration management involves establishing and maintaining a consistent configuration of systems and software throughout the organization. This includes documenting configurations, monitoring changes, and controlling access to systems and software. By implementing effective configuration management, organizations can ensure that their systems and software remain secure and that unauthorized changes are prevented.
Security Assessment and Authorization
Security assessment and authorization involves regularly assessing the security of systems and information and ensuring that they remain in compliance with FedRAMP standards. This includes conducting regular security assessments, performing vulnerability scans, and implementing security controls to address any identified vulnerabilities. By regularly conducting security assessments and authorization, organizations can ensure that their systems and information remain secure and protected.
Contingency Planning
Contingency planning involves developing a plan for continuing critical operations in the event of a disaster or security breach. This includes identifying critical operations, determining the resources required to continue operations, and having a plan in place for restoring systems and data in the event of a failure. By having a robust contingency plan in place, organizations can ensure that their critical operations continue even in the event of a disaster or security breach.
Media Protection
Media protection involves protecting sensitive information stored on electronic media, such as hard drives, flash drives, and tapes. This includes implementing physical and logical security controls to prevent unauthorized access, as well as regularly backing up and protecting stored information to ensure that it remains recoverable in the event of a disaster. By implementing effective media protection controls, organizations can ensure that their sensitive information remains secure and protected from potential threats.
Security Awareness and Training
Security awareness and training involves educating employees and other stakeholders about the importance of security and the specific security measures in place to protect sensitive information. This includes providing training on security policies and procedures, as well as regular reminders and updates on the latest security threats and best practices. By providing regular security awareness and training, organizations can ensure that all stakeholders understand the importance of security and are equipped to help protect sensitive information.
Other Controls
In addition to the specific security controls outlined above, FedRAMP also includes a range of other controls to ensure the security of systems and information. These may include additional access controls, encryption of sensitive information, and regular monitoring of systems and networks for potential security threats. By implementing a comprehensive set of security controls, organizations can ensure that their systems and information remain secure and protected from potential threats, and compliant with FedRAMP.
Benefits of FedRAMP Certification
Becoming FedRAMP certified benefits organizations and industries, as they demonstrate to customers and partners they have invested in the highest levels of security and protection for sensitive information, improved credibility and reputation, increased efficiency and cost savings, and a competitive advantage in the market.
FedRAMP certification offers a number of benefits for organizations looking to secure their sensitive information. By becoming FedRAMP certified, organizations demonstrate their commitment to meeting the highest standards for information security and protection.
One of the main benefits of FedRAMP certification is the ability to streamline security assessments and authorization processes. Organizations can reduce the time and resources required to complete security assessments, as they are already in compliance with FedRAMP standards. This also makes it easier for government agencies to do business with these organizations, as they can be confident that their data is secure.
Another benefit of FedRAMP certification is the increased trust it provides to customers and stakeholders. By demonstrating their commitment to information security, organizations can build credibility and establish trust with their customers, who are more likely to do business with them knowing that their data is secure.
In addition, FedRAMP certification helps organizations stay ahead of potential security threats. With regular audits and assessments, organizations can identify and address any potential vulnerabilities, which helps to reduce the risk of security breaches. This not only protects their own data, but also the sensitive information of their customers.
Ultimately, FedRAMP certification provides organizations with a comprehensive security framework that helps them protect their sensitive information, reduce risk, and establish trust with their customers. By becoming FedRAMP certified, organizations can focus on their core business activities, knowing that their information is secure and protected.
Cost and Time for FedRAMP Certification
The cost and time required for FedRAMP certification can vary depending on the size and complexity of the organization and the services being offered. Generally, becoming FedRAMP certified can take several months, and organizations should expect to invest significant resources to meet the certification requirements. The cost of FedRAMP certification can include the cost of the security assessment, the authorization package, and the cost of ongoing monitoring and maintenance.
Accelerate Your FedRAMP Certification Process With Kiteworks
The FedRAMP certification process provides a comprehensive and standardized approach to security assessment, authorization, and continuous monitoring for cloud-based services. Whether you are a government agency, a cloud service provider, or an industry that handles sensitive content communications, FedRAMP certification is essential for protecting your data and securing sensitive information. By becoming FedRAMP certified, organizations can ensure that their data is protected and secure and that their sensitive information is protected when shared between organizations.
The Kiteworks-enabled Private Content Network has been FedRAMP Authorized for Moderate Impact Level information for a number of years. This is important for both public and private sector organizations that rely on Kiteworks to unify, track, control, and secure their sensitive content communications. To retain its FedRAMP Authorization status, Kiteworks must pass annual audits consisting of 400-plus controls in personnel, IT, and physical security, continuously monitor for vulnerabilities and cyberattacks, conduct ongoing training and certification of employees, and thoroughly document security processes and assessments of related systems.
To learn how the FedRAMP Authorized Kiteworks Private Content Network is the right choice for your organization, schedule a tailored demo today.

