
4 Biggest Digital Rights Management Challenges
Digital rights management (DRM) plays a crucial role in protecting valuable information and data within organizations. It ensures that sensitive content is accessed and shared securely, providing a shield against unauthorized use and distribution. However, while DRM offers significant benefits, it also presents several challenges that organizations must address to achieve efficient and effective data protection.
In this blog post, we discuss the four most significant challenges faced by organizations in implementing DRM solutions and explore the importance of overcoming them.
How Digital Rights Management Works
Digital Rights Management (DRM) technology is designed to protect digital content from unauthorized access and distribution. DRM typically encrypts content, allowing only authorized users to decrypt and access it. This is achieved through a licensing system that verifies user credentials and rights to the content. DRM can restrict the number of devices on which the content can be accessed, prevent copying or sharing, and control how long content can be used. Implemented at various levels in software, firmware, or hardware, DRM aims to safeguard intellectual property and ensure content creators and distributors maintain control over their digital products.
Digital Rights Management Use Cases
Digital Rights Management (DRM) is crucial for organizations to protect and control the distribution of their digital content. Here are three typical use cases where DRM is applied:
- Protecting Video and Audio Content: Companies that produce or distribute movies, music, and other forms of multimedia content use DRM to prevent unauthorized copying and distribution. DRM technologies restrict the number of devices on which the content can be accessed and prevent users from sharing downloaded files with non-subscribers.
- E-book Protection: Publishers and authors use DRM to protect e-books from piracy and unauthorized distribution. This typically involves limiting the number of devices on which an e-book can be read and restricting the ability to print or copy text.
- Software Licensing and Activation: Software developers use DRM to enforce licensing agreements and prevent unauthorized use of their software applications. This can include mechanisms like requiring product keys for activation, online validation checks, and limiting the number of installations allowed per license. By employing DRM technologies, software companies can reduce piracy, ensure compliance with licensing terms, and protect their intellectual property.
In each of these cases, DRM technologies help organizations safeguard their digital assets, secure revenue streams, and maintain control over how their content is used and distributed.
Limitations of DRM: Challenges Limiting DRM Adoption
Digital Rights Management (DRM), conceptually, makes sense. Many (most?) digital content creators and intellectual property owners are grateful for the technology as it makes sure they are compensated properly for the use and distribution of their work against piracy and other forms of intellectual property theft. DRM technology does however have distinct limitations that inhibit wider adoption.
A prominent DRM challenge is the need to balance robust security with ease of use for end-users, ensuring that copyrighted material and sensitive content are protected without impeding productivity. And no matter how secure a DRM solution is or claims to be, it’s only as effective as the people using it. Insider threats, whether accidental or malicious, continue to expose sensitive material to unauthorized users despite being protected by DRM technology. Next, while businesses choose DRM to secure their IP to protect revenues, data privacy regulations are increasingly requiring DRM or DRM-like solutions to protect personally identifiable and protected health information (PII/PHI) Penalties, fines, litigation, and reputational damage all await businesses that fail to comply with data privacy laws.
Similarly, 55% of survey respondents in the 2023 Kiteworks Sensitive Content Communications Privacy and Compliance Report cited challenges with finding a DRM tool that aligns with compliance standards, tying access to users, roles, and content classes. Additionally, 53% mentioned the need for agents on third-party clients to open unencrypted content, while 50% highlighted the necessity to view and edit any type of content.
Despite these issues, most organizations recognize the significance of DRM and have to adjust their strategies to incorporate it. By focusing on overcoming these DRM challenges, organizations can better secure their valuable data assets, streamline content management, and enhance both security measures and user accessibility. We’ll take a closer look at these and other challenges below.
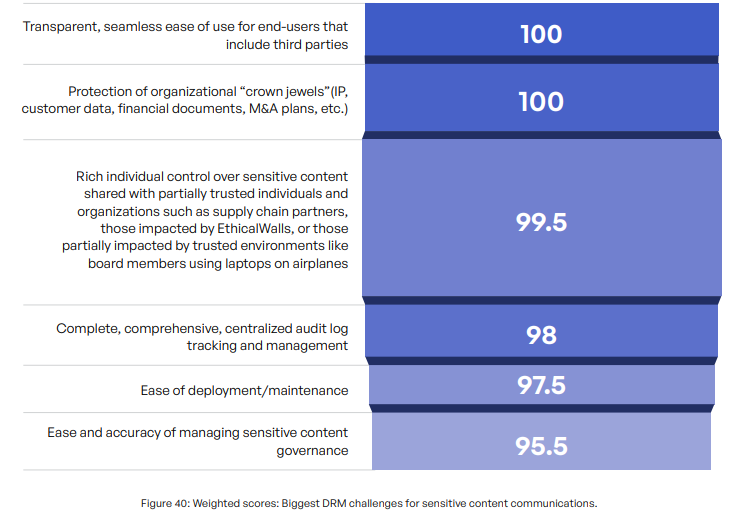
DRM Challenge #1: Ease of Use for End-users
One of the primary challenges faced by organizations is providing a transparent and seamless digital rights management experience for end-users, including employees and trusted third parties, who need to access the protected content. The main goal of DRM solutions is to safeguard intellectual property and sensitive information, but these solutions should not become obstacles that hinder legitimate access to data or disrupt workflow efficiency. If they do, employees will find unsecure workarounds.
To achieve this delicate balance, DRM systems need to prioritize user experience. This means implementing user-friendly interfaces that are intuitive and easy to navigate, even for individuals with limited technical knowledge. Clear and concise instructions, along with informative error messages, should be provided to guide users through the authentication and access process.
Further, transparency is essential in DRM implementations. Users should be informed about the purpose and scope of the DRM protection, how their data will be used, and what restrictions might apply. By fostering an open and honest approach, organizations can build trust with their end-users and third-party stakeholders.
By focusing on user needs and designing DRM solutions with a commitment to transparency and ease of use, organizations can encourage widespread adoption of DRM technology and ensure compliance with intellectual property protection standards.
Complexities With End-user Authentication
Another major obstacle in DRM implementation is the complex authentication process that end-users often encounter when attempting to access protected content. Traditional authentication methods, such as cumbersome login procedures or frequent requests for credentials, can lead to frustration and may even prompt users to find alternative ways to bypass DRM restrictions.
To address this challenge, DRM providers need to explore innovative and secure authentication techniques that streamline the user login process without compromising on security. Technologies such as multi-factor authentication (MFA), biometrics, and single sign-on (SSO) can offer a balance between user convenience and data protection.
KEY TAKEAWAYS

KEY TAKEAWAYS
- Challenges in DRM Implementation:
An effective DRM strategy is hindered by common challenges like: compliance alignment, user access issues, and compatibility concerns. - Ease of Use for End-users:
Prioritizing user experience with intuitive interfaces and clear instructions fosters trust and encourages compliance with DRM policies. - Complexities With End-user Authentication:
Implementing innovative authentication techniques like MFA and contextual authentication balances security and user convenience. - Ensuring Compatibility Across Devices and Platforms:
Adopting industry standards and conducting regular testing and updates ensure seamless access to protected content across diverse devices and platforms. - Protecting Organizational “Crown Jewels” With a DRM Strategy:
Safeguarding critical assets requires a comprehensive DRM strategy addressing technological, legal, and security challenges.
Additionally, leveraging contextual information during authentication can enhance the user experience. For example, incorporating device recognition or geolocation data can help identify trusted devices and reduce the frequency of authentication prompts for recognized devices, making access to protected content smoother.
It is crucial to strike the right balance between security and user experience. A frictionless authentication process that doesn’t overwhelm users with excessive hurdles will contribute to higher user satisfaction and encourage compliance with DRM policies.
It is crucial to strike the right balance between security and user experience. A frictionless authentication process that doesn’t overwhelm users with excessive hurdles will contribute to higher user satisfaction and encourage compliance with DRM policies.
Ensuring DRM compatibility across a diverse range of devices and platforms is essential to cater to a broad user base effectively. Users may access protected content from various operating systems, web browsers, and devices, making it critical to eliminate compatibility issues that can hinder productivity and discourage users from embracing DRM solutions.
To achieve compatibility, DRM providers should adopt industry standards and technologies that are widely supported across platforms. Using open standards ensures that the protected content can be accessed seamlessly on different devices, regardless of their manufacturers or operating systems.
Regular testing and updates are necessary to stay ahead of evolving technologies and ensure ongoing compatibility. This involves monitoring changes in device specifications, browser updates, and operating system advancements to promptly address any compatibility challenges that may arise.
Moreover, providing clear guidelines and system requirements to end-users can help them identify whether their devices and software are compatible with the DRM system. When users are well-informed about compatibility, they can make informed decisions and avoid potential frustrations.
DRM Challenge #2: Relying on DRM to Protect “Crown Jewels” Without a DRM Strategy
The protection of an organization’s most critical and sensitive assets, often referred to as “crown jewels,” is typically a top priority for most companies. These assets may include intellectual property (IP), customer data, financial documents, merger and acquisition (M&A) plans, and other proprietary information that holds immense value for organizations.
A sound DRM strategy plays a vital role in safeguarding these assets from unauthorized access, theft, or data breaches. A proper DRM strategy provides organizations a systematic approach to control, monitor, and manage the use, distribution, and modification of digital content. This DRM strategy involves employing various technological restrictions to prevent unauthorized use and ensure the copyright holder’s rights are not compromised. Robust DRM solutions contain access controls, encryption, and other security measures to ensure that only authorized personnel can view, edit and download an organization’s priceless crown jewels.
Creating, implementing, and maintaining a DRM strategy, however, can be challenging due to several reasons:
- Technological Evolution: As technology keeps advancing, DRM strategies need to evolve constantly. This requires substantial resources, expertise, and time.
- User Friendliness: Striking a balance between protection of digital rights and user-friendliness is difficult. Overly restrictive DRM can inconvenience legitimate users and potentially drive them toward illegal alternatives.
- Legal Challenges: Laws and regulations regarding digital rights vary greatly across jurisdictions. Therefore, a DRM strategy that works in one country may not be applicable or legal in another.
- Security: DRM systems are often targeted by hackers. Keeping these systems secure and ahead of malicious entities requires continuous effort and advanced security measures.
- Interoperability: DRM systems often lack interoperability, which means content protected by one system’s DRM may not be accessible on another. This makes it challenging for users to access their purchased content across different devices and platforms.
- Consumer Perception: Many consumers view DRM as an impediment to their rights to use and enjoy the content they’ve legally purchased. This negative perception can affect the adoption and long-term effectiveness of DRM strategies.
A comprehensive DRM strategy should include regular security assessments and updates to stay ahead of emerging threats. By consistently monitoring and improving the DRM infrastructure, organizations can effectively protect their crown jewels and maintain a competitive advantage in their respective industries.
DRM Challenge #3: Mitigating Insider Threats
One of the most significant challenges in DRM implementation is addressing insider threats. Employees and other authorized personnel with access to sensitive information pose a potential risk to data security, whether intentionally or unintentionally. Insider threats may arise from disgruntled employees, careless handling of data, or falling victim to social engineering attacks.
A comprehensive DRM solution should encompass several key elements to mitigate insider threats effectively:
- Access Controls: Implementing granular access controls ensures that employees can only access information relevant to their roles and responsibilities. Role-based access and the principle of least privilege restrict unnecessary access, reducing the likelihood of data misuse.
- User Activity Monitoring: DRM systems should include robust monitoring capabilities to track user activity and detect suspicious behavior. Unusual access patterns, multiple login attempts, or attempts to access unauthorized resources can trigger alerts, allowing security teams to respond promptly.
- Employee Training: Security awareness training about the importance of data security, the risks of insider threats, and best practices for handling sensitive information is crucial. Regular training sessions can raise awareness and foster a security-conscious culture within the organization.
- Data Loss Prevention (DLP): Integrating DLP solutions with DRM can add an extra layer of protection. DLP tools can detect and prevent data exfiltration attempts, whether through email, removable media, or cloud services.
- Incident Response Plan: Having a well-defined incident response plan in place allows organizations to react swiftly and effectively in the event of a suspected data breach or insider threat incident. The plan should include steps for investigation, containment, eradication, and recovery.
By combining these measures, organizations can significantly reduce the risk of insider threats and strengthen their data security posture.
Securing Data in Transit and at Rest
Digital data is vulnerable not only when it is being accessed but also during transmission and storage. DRM solutions must address both aspects to ensure comprehensive data protection.
- Data in Transit: DRM should employ robust encryption and secure communication protocols when data is transmitted over networks. Technologies like Transport Layer Security (TLS) and Secure Sockets Layer (SSL) encrypt data during transit, preventing unauthorized interception and eavesdropping.
- Data at Rest: When data is stored on servers, databases, or other storage media, it needs to be encrypted to safeguard against unauthorized access. Advanced encryption algorithms like AES encryption ensure that even if physical media are compromised, the data remains indecipherable without the appropriate decryption keys.
- Key Management: Effective key management is essential for secure encryption and decryption processes. DRM solutions should implement strong key management practices, including key rotation and secure key storage, to prevent unauthorized access to encryption keys.
- Secure Authentication: Secure authentication mechanisms are critical to prevent unauthorized users from accessing encrypted data. Multi-factor authentication (MFA) and strong password policies help ensure that only authorized individuals can decrypt and access sensitive information.
- Regular Audits: Periodic security reviews should be conducted to assess the effectiveness of encryption and data protection measures. Audits and audit logs can identify potential vulnerabilities or configuration issues that may compromise data security. Audit logs also play a critical role in demonstrating regulatory compliance.
By implementing a comprehensive approach to securing data in transit and at rest, DRM solutions significantly reduce the risk of data breaches and unauthorized access. Organizations can instill confidence in their customers, partners, and stakeholders by demonstrating their commitment to data security and privacy.
DRM Challenge #4: Controlling Sensitive Content Shared With Supply Chain Partners
Organizations often need to collaborate and share sensitive content with trusted third parties, such as contractors, consultants, or supply chain partners. Your organization may have robust cybersecurity solutions and processes in place but your partners may not. Many cyberattacks involving large enterprises, in fact, originate with a smaller supply chain partner with a smaller cybersecurity budget and few cybersecurity tools at their disposal. Organizations not surprisingly invest extensive resources in third-party risk management to mitigate this risk. Every organization therefore must ensure that only the right individuals and partners have access to the appropriate content while maintaining control over that access.
DRM plays a crucial role in enabling organizations to share information with confidence, even with trusted third parties. One of the key features that DRM solutions should provide is rich individual control over access permissions. Fine-tuning access permissions ensures that only relevant individuals have access to the sensitive information they require for their specific roles or projects.
Further, time-limited access and dynamic access revocation are vital components of this control. With time-limited access, organizations can set specific periods during which the content is accessible to designated users. This feature is particularly useful when sharing time-sensitive information or temporary collaboration projects. Dynamic access revocation allows organizations to revoke access to shared content instantly if the need arises, such as in cases of security breaches, contract terminations, or project completion.
By offering rich individual control over sensitive content, DRM empowers organizations to share information securely, mitigating the risk of data leaks and unauthorized access.
Fine-grained Access Controls for Sensitive Files
To address the challenges associated with sharing sensitive content, DRM solutions should incorporate fine-grained access controls. These controls allow organizations to customize access permissions at a granular level, ensuring that only authorized users can access specific pieces of content.
Fine-grained access controls enable organizations to define not only who can access the content but also what actions they can perform with it. For instance, organizations can restrict users from printing, copying, or downloading sensitive documents, ensuring that the content remains within the intended boundaries.
Moreover, DRM should support access controls based on user attributes, roles, and privileges. This means that access permissions can be dynamically adjusted based on changes in an individual’s role or status within the organization, providing flexibility while maintaining security.
Combining fine-grained access controls with time-based access further enhances security. Organizations can set access periods, ensuring that content is only available for a specific duration, reducing the risk of prolonged exposure to potential threats.
Digital Watermarking and Tracking for Traceability
To discourage unauthorized distribution and maintain traceability, DRM systems can employ digital watermarking and tracking technologies. Digital watermarks are imperceptible markers embedded within sensitive content, allowing the source of leaked or improperly shared information to be traced back to the origin.
Watermarks act as a powerful deterrent, as individuals are less likely to engage in unauthorized sharing when they know their actions can be traced. This can be especially crucial when sharing content with third-party organizations, as it adds an additional layer of accountability.
In addition to watermarking, DRM solutions can incorporate tracking capabilities to monitor user activities and content access. By logging and analyzing access patterns and user behavior, organizations can identify suspicious activities or potential security breaches in real time, enabling swift response and mitigation.
Protect Your Crown Jewels With Kiteworks DRM
Kiteworks provides organizations with a Private Content Network (PCN) that is designed to deliver content governance, compliance, and protection. This platform is designed to manage sensitive content that moves within, into, and out of an organization. The Private Content Network unifies, tracks, controls, and secures sensitive content, significantly improving risk management and ensuring regulatory compliance on all sensitive content communications.
Leveraging SafeVIEW and SafeEDIT capabilities, Kiteworks delivers next-generation digital rights management that enables attribute-based access control for secure document viewing and editing. SafeVIEW allows users to view documents securely within a protected environment, enforcing access policies based on user and document attributes. It prevents unauthorized actions such as downloading, printing, or sharing sensitive information. In contrast, SafeEDIT enables authorized users to collaboratively edit documents while maintaining the same granular access control. It ensures that only users with the appropriate attributes can modify specific sections of a document. Both SafeVIEW and SafeEDIT leverage administrator-defined policies that dynamically adjust access rights based on attributes, ensuring that sensitive data remains secure throughout its lifecycle.
To learn more about Kiteworks’ DRM capabilities, schedule a custom demo today.
Additional Resources
- Report Benchmark Your Sensitive Content Communications Privacy and Compliance
- Article Digital Rights Management (DRM): Protecting Intellectual Property in the Digital Age
- Kitecast Connecting GRC With DRM
- Webinar Master Digital Rights Management: A Webinar Roundtable on Kiteworks’ 2023 Sensitive Content Communications Report
- Blog Post It’s Time for a DRM “Do-over:” Findings and Takeaways in Kiteworks’ 2023 Sensitive Content Communications Report
