
Top 5 Requirements for an Effective DRM Solution
Data sharing is an integral part of business operations. However, when this sharing involves sending sensitive content outside the perimeter, to customers, vendors, partners, and other trusted third parties, the risk of a data breach increases. A robust digital rights management (DRM) solution plays a critical role in mitigating the risk of unauthorized access.
Unfortunately, not all DRM solutions are created equally. In this blog post, we will define a top-rate DRM solution and share the top five requirements for an effective DRM solution, as well as the barriers that hinder its deployment.
The Significance of DRM for Protecting Sensitive Content
DRM is emerging as a crucial addition to organizations’ efforts to safeguard their sensitive content. DRM, however, is not entirely new; its roots trace back several decades. But as DRM technology has evolved in parallel with organizations increasingly sharing and distributing sensitive information, the need to protect this content from unauthorized access has become paramount. DRM addresses these concerns by providing organizations with a robust framework to protect sensitive information, especially intellectual property.
Digital Rights Management: A Refresher
At its core, DRM refers to a set of technologies, strategies, and policies aimed at controlling access to digital content and managing its usage rights. It provides organizations with the means to enforce restrictions on how sensitive content can be used, ensuring that only authorized individuals or entities can access, copy, modify, or distribute the sensitive content.
The adoption of DRM by various entities is a step forward in mitigating the risks associated with unauthorized data breaches, intellectual property theft, and illegal distribution of sensitive information. Sensitive content may include confidential business data, proprietary software, classified government documents, copyrighted media, and other valuable intellectual property.

KEY TAKEAWAYS
- Significance of DRM for Protecting Sensitive Content:
DRM is essential for safeguarding sensitive information like intellectual property, customer data, and classified documents, preventing unauthorized access and distribution. - Top 5 Requirements for an Effective DRM Solution:
Ease of use, content protection, audit logging, alignment with compliance regulations like GDPR, HIPAA, and ISO 27001, and viewing and editing flexibility to balance between security and productivity. - DRM Deployment Challenges and Solutions:
Challenges include enabling access to encrypted content, and supporting diverse content types. Successful implementation requires understanding of requirements and adherence to compliance regulations. - Steps for a Successful DRM Implementation:
Identify sensitive content, select appropriate technology, implement encryption and decryption, manage user privileges, enforce authentication, turn on watermarking and tracking, and more.
DRM can encompass various protection mechanisms, such as encryption, watermarking, access controls, and licensing models. By implementing these measures, content owners can regulate the usage of their content, limiting its accessibility to specific devices, authorized users, or predetermined usage scenarios.
One of the key benefits of DRM is that it allows organizations to strike a balance between sharing information with third parties while still maintaining control over its usage. This becomes especially relevant when collaborating with external partners, vendors, or customers who may require access to sensitive content but should not have unfettered freedom to exploit it.
Moreover, DRM enables content owners to track and monitor how their content is being used, providing insights into potential security breaches or unauthorized activities. It also serves as a deterrent to potential pirates, making it more challenging for unauthorized users to profit from illegal distribution.
Top 5 Requirements for an Effective DRM Solution
An effective DRM solution serves as a fortified fortress, guarding valuable digital assets from unauthorized access, distribution, and manipulation. However, not all DRM solutions are created equal, and choosing the right one can significantly impact an organization’s data protection strategy.
When considering a DRM solution, there are several key factors to evaluate, ensuring you select the right one to meet your specific needs and security requirements. Here are five essential requirements of an effective DRM solution that should be considered non-negotiable when vetting different DRM product offerings.
DRM Requirement #1: Ensures User Adoption Through Ease of Use
The primary and most crucial requirement for any effective DRM solution is ease of use. Complicated and convoluted DRM systems can frustrate users, leading to the adoption of workarounds or neglect of security protocols altogether. Therefore, it is essential for a DRM solution to have a user-friendly interface that seamlessly integrates into existing workflows. When users find the DRM system easy to navigate and understand, they are more likely to comply with security measures and protect sensitive content effectively.
DRM Requirement #2: Protects Sensitive Content
At its core, DRM’s main objective is to safeguard sensitive content. Therefore, an effective DRM solution must employ robust encryption methods to ensure the data remains protected both at rest and during transit. This level of encryption ensures that even if unauthorized individuals gain access to the content, it remains unreadable and unusable to them. By securing the content, organizations can prevent data breaches and protect their valuable intellectual property and private information.
DRM Requirement #3: Records All Information Sharing With Audit Logs
A crucial aspect of any DRM system is maintaining a comprehensive audit log that tracks all user activities related to the protected content. This detailed log provides valuable insights into any content or file that may have been accessed without permission. Activities that are logged include user actions like file access attempts, file downloads, content edits, and any attempts to share sensitive content or files containing sensitive content. By analyzing audit logs, organizations can identify suspicious behavior, detect security vulnerabilities, and take timely action to mitigate a data breach and enhance their overall security posture.
DRM Requirement #4: Aligns With Compliance Standards
For a DRM solution to be truly effective, it must align with relevant compliance standards and regulations, like GDPR, HIPAA, PCI DSS, ISO 27001, and many more. This involves tying access permissions to specific users, roles, and content classes in accordance with the established guidelines. A well-aligned DRM system ensures that content is accessed and used only by authorized personnel, which helps organizations avoid legal complications and demonstrate their commitment to data privacy.
DRM Requirement #5: Enables Viewing and Editing Flexibility
A successful DRM solution should offer flexibility in viewing and editing protected content. Authorized users should be able to access and modify content seamlessly without unnecessary restrictions. By providing this versatility, organizations can strike a balance between protecting sensitive information and maintaining (or even enhancing) productivity. Restricting usability too much may lead to user resistance, hindering workflow efficiency, while overly lax controls could compromise the security of the content.
The Need for Enhanced DRM Solutions
Organizations are increasingly recognizing the importance of moving beyond simple data classification and controls, driven by requirements set forth by frameworks like the National Institute of Standards and Technology Cybersecurity Framework (NIST CSF), and the necessity to better safeguard sensitive content. As a result, many of them are turning to DRM solutions to elevate their content protection efforts. While DRM tools have been in existence for decades, their implementation has often fallen short of expectations, leaving digital assets vulnerable to internal and external threats due to a lack of adequate governance and security measures.
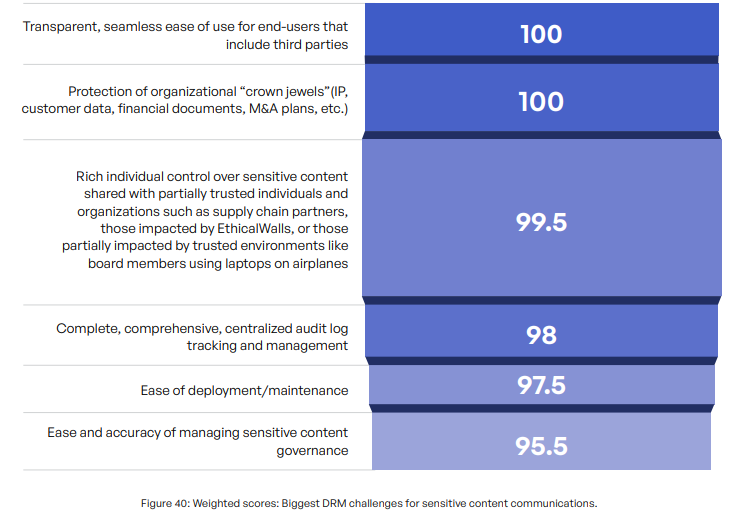
To gain insights into the preferences and challenges faced by organizations with DRM solutions, we included some questions from our Kiteworks 2023 survey and report. Respondents were asked to rank their top requirements for an effective DRM solution among six options. The responses were diverse, but when weighted, “ease of use” emerged as the clear winner, closely followed by the protection of the organization’s most valuable assets, commonly referred to as the “crown jewels,” and comprehensive audit log tracking.
DRM Deployment Challenges
Deploying, rolling out, and driving adoption of a DRM solution can be complicated, based on business needs, compliance requirements, and other factors. Among the challenges encountered in deploying a DRM solution, the most commonly cited issue in our survey, by 55% of respondents, was finding a DRM tool that efficiently managed information access based on user roles and content categories in alignment with compliance standards. Two additional challenges were the need for third-party client agents to access encrypted content (53% of respondents) and the capability to view and edit diverse types of content (50%).
Certain industries faced more pronounced hurdles when it came to DRM compliance features. For example, energy and utilities, legal, state government, technology, and professional services organizations experienced a more substantial challenge, with 72%, 62%, 61%, 61%, and 60% of respondents, respectively, listing it as a top issue. On the other hand, the need for agents proved to be especially burdensome for professional services (70%), local government (69%), and technology (61%) respondents.
As organizations strive to protect sensitive content and adhere to compliance standards, DRM presents organizations with an opportunity to “kill two birds with one stone.” DRM’s success, however, hinges on its ability to deliver ease of use, protection of critical assets, and adherence to various industry-specific requirements. If DRM can effectively address these challenges, organizations can significantly fortify their digital content against potential threats.
What a Successful DRM Implementation Looks Like
A successful DRM implementation requires careful planning, consideration of various factors, and adherence to best practices. The following table summarizes the attributes of a successful DRM implementation:
| Step | Description | Action |
|---|---|---|
| 1 | Identify Sensitive Content | Clearly identify the sensitive content that needs protection. |
| 2 | Understand Your Requirements | Determine the specific requirements of the DRM solution, including access controls and platform support. |
| 3 | Select an Appropriate DRM Technology | Research and choose a suitable DRM technology that aligns with your requirements. |
| 4 | Implement Encryption and Decryption | Ensure encryption for sensitive content at rest and during transmission. Set up decryption processes for authorized users. |
| 5 | Manage User Privileges With Rights Management | Develop and implement mechanisms to control user access, viewing, modification, and sharing of content based on user privileges. |
| 6 | Enforce User Authentication | Establish strong user authentication methods, such as passwords or multi-factor authentication (MFA). |
| 7 | Protect Encryption Keys | Safeguard encryption keys and ensure secure distribution to authorized users. |
| 8 | Turn on Watermarking and Tracking | Integrate watermarking and tracking technologies to trace unauthorized distribution. |
| 9 | Schedule Regular Updates and Maintenance | Stay updated with DRM advancements and security patches. Regularly review and update the DRM solution. |
| 10 | Adhere to Compliance Regulations | Ensure the implementation complies with relevant regulations and legal requirements. |
| 11 | Educate Users | Train users on proper content usage and the importance of keeping their credentials secure. Raise awareness of the consequences of unauthorized distribution. |
| 12 | Test and Audit | Thoroughly test the DRM implementation and conduct regular security audits. |
| 13 | Implement Backup and Disaster Recovery | Establish a comprehensive backup and disaster recovery strategy. |
| 14 | Set Up Monitoring and Incident Response | Set up monitoring mechanisms to detect suspicious activities. Have a well-defined incident response plan. |
| 15 | Strive for Continuous Improvement | Stay informed about the latest developments and continuously improve the DRM solution. |
Kiteworks Helps Organizations Protect Their Sensitive Content With Advanced DRM Capabilities
The Kiteworks Private Content Network (PCN) is a comprehensive solution designed to secure third-party content communications. It offers a suite of advanced features and capabilities that ensure the protection of sensitive data during transmission and storage.
One of the key features of the Kiteworks PCN is its robust DRM capabilities. Kiteworks allows organizations to control who can access sensitive information, with whom they can share it, and how third parties can interact with (and for how long) the sensitive content they receive. Together, these advanced DRM capabilities mitigate the risk of unauthorized access and data breaches.
In addition to DRM, the Kiteworks PCN also provides robust email encryption capabilities for both data at rest and data in transit. The Kiteworks PCN also offers robust access control mechanisms. These mechanisms ensure that only authorized individuals have access to sensitive data.
Finally, Kiteworks provides comprehensive audit logging capabilities for tracking all activities related to sensitive data. This includes who accessed the data, when it was accessed, and what actions were taken. This level of visibility is crucial for detecting and responding to potential security incidents and demonstrating regulatory compliance with GDPR, CMMC, HIPAA, and other regulations.
To learn more about the Kiteworks Private Content Network and its extensive, advanced DRM capabilities, schedule a custom-tailored demo today.
Additional Resources
- Article Digital Rights Management (DRM): Protecting Intellectual Property in the Digital Age
- Blog Post NIST Privacy Framework for Protecting Sensitive Data
- Report Benchmark Your Sensitive Content Communications Privacy and Compliance
- Webinar Master Digital Rights Management: A Webinar Roundtable on Kiteworks’ 2023 Sensitive Content Communications Report
- Case Study MiTek Industries Replaces FTP for Faster Performance, Improved Security, and Complete Data Privacy