
Data Classification–What It Is, Types, and Best Practices
What Is Data Classification?
Data classification organizes data into categories, allowing it to be more easily analyzed and managed. It involves assigning tags or names to data according to specific rules or patterns, allowing it to be sorted and searched more efficiently. Data classification is an essential component of data governance and management, and it ensures data is properly handled and secured. Data classification also helps organizations identify the sensitive or confidential data that resides in their systems and devices, allowing for enhanced security and privacy protection. As data volumes and complexity increase and organizations rely more on data-driven decisions, data classification becomes an increasingly vital tool to ensure successful data management.
What Is Business Data and What Are the Types of Business Data?
Business data refers to all the information about a company’s customers, operations, marketing efforts, and financials. This data can be used to gain insight into a company’s performance and make decisions about improving certain aspects of the business. Some of the different types of business data include customer data, operational data, market data, and financial data.
Customer data relates to the information a company has on its customers. This data can include customer contact information, purchase history, and customer preferences or feedback. A better understanding of customer data can help a business tailor their product offerings, marketing messages, or customer service to meet its customers’ needs better.
Operational data refers to the data related to the day-to-day activities of a business. This can include the number of products produced or shipped, the number of employees, or the number of orders processed. This data allows companies to understand the internal operations of their business to identify areas for improvement.
Types of Data Classification
Data can be classified in several ways, depending on its intended use and the context in which it is being managed and accessed. Common examples of data classifications include public, internal, confidential, and restricted; structured and unstructured; and person, location, and event-based. Data classification can also involve grouping data into privacy categories, such as financial, healthcare, and team member records. Data classification aims to ensure that the correct data is used correctly at the right time and that sensitive data is properly managed and secured. Organizations can more easily protect and collect the data that matters most to them by organizing data into groups with similar characteristics.
To start, let’s go through the main data classification types. The four main classifications for data are:
- restricted
- confidential
- internal
- public
However, these types may vary depending on organization. Each of these levels determines who has access to the data and how long the data must be retained.
This post, the first of three, will help organizations create a data classification program, including program prerequisites and task member responsibilities to ensure proper governance. I will detail the development process in a future post.
Conversations and meetings around what data classification is and how to define it in organizations have occurred for the past two decades. It is the classic “Coke can” experiment; a group of people sit around a Coke can and describe what they see, without saying “it’s a Coke can.” Everyone will have a unique view and no two descriptions will be the same.
“Data classification is difficult, boring, and unglorified but …”
Now imagine the same exercise but replace the Coke can with your organization’s data. Data classification becomes extremely complicated for an organization with different business functions, deliverables, and different needs. It can make you want to look for other things to do with your day. Data classification is difficult, boring, and unglorified. You will, however, need to embrace it to create an effective cybersecurity program.
Any article on data classification will tell you it must factor into an organization’s information security and compliance program. This generic statement will garner universal acceptance with your management team, but data classification requires a lot of heavy lifting. Data classification desires, needs, and even definitions vary between groups in an organization.
Data classification typically includes a three- or four-layer system akin to the below:
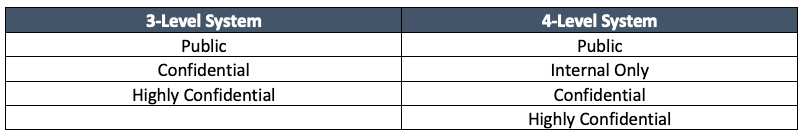
If you are new to data classification, begin with the 3-level system.
I recommend organizations new to data classification begin with the 3-level system as these levels and their corresponding actions and controls can be challenging to define. The 3-level system considers all internal data confidential so you can clearly communicate your goals across the business, including locations, processes, and applications. First, create the processes and procedures needed to support confidential data. You can identify the limited amount of Public and Highly Confidential data later through interviews and technical discovery.
Why It’s Essential to Learn the Data Classification Levels or Types
Data classification is a system for organizing data into different categories depending on its criticality, sensitivity, and value to an organization. Its purpose is to ensure data security, reliability, and compliance with relevant laws and regulations. Ensuring that data is correctly classified is an essential step in an organization’s data governance process, as it defines its data management and protection policies.
Learning the data classification levels is essential for organizations to distinguish between data of varying value, sensitivity, and risk. By assigning data to the appropriate classification level, organizations can implement the necessary controls to manage who can access the data and how it is used. For example, organizations can set different access control levels depending on the data classification level, ensuring that only authorized personnel can access the data.
Steps for Effective Data Classification
Effective data classification can be done manually or through automated processes. By understanding the types of data the organization deals with, the company can classify and group data according to those categories. This might include the age of the data, the impact of a data breach, and the likelihood of a data breach. Once these categories are established, the organization can then define the level of sensitivity and importance of each data type and assign a corresponding data classification label.
Data classification is organizing and structuring data based on its importance and sensitivity. It involves an audit to identify and categorize data, establish objectives, create a data classification scheme and policies, implement the strategy, and monitor and maintain it. Organizations can protect data, ensure compliance with regulations and industry standards, and improve operational efficiency by performing this process.
Organizations must identify their privacy requirements before they can classify data. This will help ensure that all data is protected to meet privacy, security, legal, and regulatory requirements. When determining data classification, consider the potential consequences of a data breach, the need to protect trade secrets, and the overall risk the data poses to the organization.
Data Classification Challenges
Data classification poses several challenges to most organizations. Organizations must consider the complexity and sensitivity of the data, the resources required to manage the data securely, and the security protocols that need to be in place. Data classification is also tricky due to the ever-growing data volume, the data’s complexity, and the time required to assess the data thoroughly. Data is often stored in multiple locations and systems, making it difficult to classify and protect accurately. Additionally, organizations must ensure that the classification is consistently and accurately applied to ensure all data is securely stored and protected. Lastly, organizations must ensure authorized personnel have access to sensitive data and that data is protected from unauthorized access.
What’s the Difference Between Data Classification and Data Categorization?
Data classification and data categorization are two essential concepts in data management. Data classification consolidates data into meaningful clusters of information based on specific criteria such as characteristics, attributes, behavior, pattern, and more. It helps to organize data for more efficient storage and retrieval.
Data categorizes data into categories based on specific criteria such as similarity, relationships, or purpose. It is used to organize data for more accessible analysis and understanding. It is often used to manage a large data volume into smaller information sets. For instance, data can be classified in a customer survey, such as age, gender, geographical location, etc.
Classification and categorization techniques are now utilized in many areas, such as business intelligence, analytics, natural language processing, and machine learning. It helps enterprises to quickly and accurately analyze large amounts of data. This, in turn, allows them to make better-informed decisions and improve efficiency.
Real-life Use Cases
Organizations classify and categorize extensive amounts of data, regardless of company size, industry, or geography. For example:
Data Classification: A bank can use data classification to categorize customer data into high-risk and low-risk customers. This can help the bank identify customers more likely to default on their loans so they can be flagged for further investigation.
Data Categorization: Retailers can use data categorization to categorize customer purchases into products, brands, price ranges, and more. This enables retailers to target their marketing activities better and drive sales.
Before You Start Your Data Classification Program
A data classification program cannot be created and deployed in a vacuum. The following cybersecurity program components must be in place before any data classification planning can begin:
- Asset Management – Owned by IT. The organization needs to know what systems contain the highly sensitive, Confidential, or Highly Confidential data. A data classification program without an effective asset management process already in place won’t work; you won’t get past the drawing board stage.
- Incident Response (IR) – Owned by Cybersecurity. You must have a plan and process in place in the event Confidential or Highly Confidential data has been breached. Organizations with immature cyber programs often struggle with Incident Response as data breaches containing different data types require different response levels. These response levels must be established prior to starting a data classification program.
- Regulated Data Sets – Owned by Compliance. Most data is regulated (e.g., financial data, intellectual property, etc.). You must determine what regulated data you have before you begin a data classification program. These data sets, once defined, will also help you establish your DLP rules and location search.
- Privacy Data Sets – Owned by Privacy. Much like the regulated data sets, privacy data needs to be predetermined. Don’t cut corners here. A blanket statement like “Well, it’s just personally identifiable information” will spell disaster. Your Cyber and Privacy teams must align on privacy data definitions and rules including:
- Will the organization classify Customer IDs as personally identifiable information (PII)?
- Are any PII data types more sensitive than others?
- Do any regulations require data to be contained to any specific location or jurisdiction?
Organizations must demonstrate compliance with several additional privacy requirements to ensure a successful data classification program.
The Relationship Between Data Classification and Compliance
Compliance refers, naturally, to adhering to laws, rules, regulations, and standards while data classification organizes and labels data according to its sensitivity, value, purpose, or context.
It’s an integral part of data security and helps organizations protect their sensitive data. For example, a company that processes personal data must comply with the EU General Data Protection Regulation (GDPR).
Data classification and compliance are closely related. For example, organizations must understand how data is classified to comply with relevant regulations. For example, a company that processes personal data must ensure that it is properly organized and protected in accordance with the GDPR. In addition, data classification can help organizations comply with industry-specific regulations. For example, a financial institution must classify data according to the Financial Industry Regulatory Authority (FINRA) guidelines.
Data classification and compliance benefits go beyond simply adherence to the law. A well-implemented data classification system can help organizations improve the security of their data, ensure data integrity, and reduce their risk exposure. It can also help organizations optimize their data security policies and processes and improve their overall security posture. Finally, data classification can help organizations reduce the costs associated with data breaches and other security incidents.
Create a Data Classification Taskforce
A highly effective data classification program will have input from numerous business verticals.
You will find some departments more cooperative than others. You will for example not need to convince IT to participate. Virtually any CIO will want a mature data classification program as it allows IT departments to automatically prioritize the systems, business processes, and applications they provide and maintain.
“Get all the teams on the same page.”
I recommend you start with the Regulators. They usually understand the program’s importance and also know their data sets very well. Next, engage with Risk and Legal. They too know their data but will probably require some training on their role and their deliverables. You can work much more efficiently and effectively once all the teams are on the same page. Make them a part of the program development process going forward. Define the data classifications together. Co-develop the training materials required to inform the business units about the program. Then communicate (rather than dictate) procedural changes in handling certain data types to ensure compliance with the new classification program.
The Taskforce: Deliverable, Role, Motivation
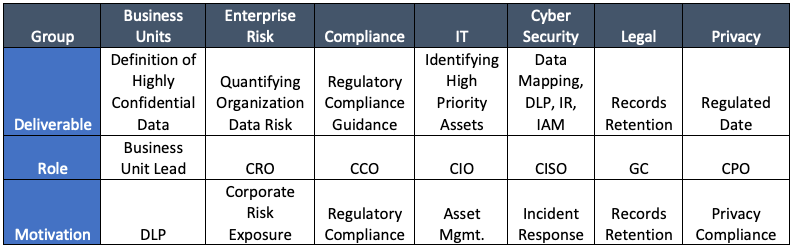
Data classification programs frequently fail in their implementation unless each group contributes something to make the program successful.
What Is a Data Classification Standard?
A data classification standard is an organized system for classifying data regarding its sensitivity, level of protection, and other characteristics. This system helps organizations store, manage, and protect data based on the sensitivity and importance it holds for the organization. The most common standard for data classification has four levels, ranging from public or unclassified data to highly confidential data. These levels are often labeled as public, hidden, secret, and top secret, depending on the size and complexity of the organization. Adherence to data classification standards helps organizations ensure that their data is appropriately managed and protected while complying with applicable laws and regulations.
What Are the Benefits of a Data Classification Policy?
A data classification policy can provide significant benefits by helping organizations effectively protect their data, mitigate security risks, and comply with applicable laws and regulations.
Data classification policies help organizations protect sensitive data such as personal information, intellectual property, and financial data. By clearly defining the categories of data to be covered and specifying the appropriate controls for each type, organizations can ensure that the proper measures are taken to protect their data from unauthorized access or misuse. This can include access controls, encryption, and other actions tailored to the information’s sensitivity.
Data classification policies can also help mitigate security risks by providing a consistent and uniform approach to handling and storing data. This helps ensure that data is stored in the most secure manner possible while assisting organizations in identifying potential vulnerabilities in their environment.
Finally, data classification policies can help organizations comply with applicable laws and regulations such as the EU General Data Protection Regulation and the California Consumer Privacy Act (CCPA).
What’s Next
In my next post, we will take a deep dive into the classification schema and best practices for defining data.
Additional Resources

