
Strengthening Data Exchange Security: Key Findings from the 2025 Data Security & Compliance Survey
The Data Security and Compliance Buyer Behavior Survey, conducted by Centiment on behalf of Kiteworks, provides critical insights into how organizations are navigating these challenges. This comprehensive study reveals why regulated industries are increasingly selecting Kiteworks’ Private Data Network to meet their critical security and compliance needs.
In this blog post, you’ll discover the key factors driving security decisions based on compelling evidence from the survey. We’ll examine the evolving threat landscape, analyze compliance drivers, and reveal what security leaders prioritize when selecting data protection solutions.
Why Attackers Are Targeting Enterprise Data Exchange Systems in 2025
What makes data exchange systems vulnerable to zero-day attacks?
These vulnerabilities are particularly dangerous because they target the infrastructure specifically designed to handle an organization’s most sensitive information. Kiteworks’ zero trust data exchange architecture directly addresses these vulnerabilities by ensuring that all data exchanges are authenticated, encrypted, and monitored—regardless of the communication channel or endpoint.
How have third-party data breaches evolved in the past year?
According to the Verizon 2025 Data Breach Investigations Report, third-party breaches have doubled to 30% of all incidents, with attacks specifically targeting legacy file sharing and transfer solutions leading the surge.
The survey findings reveal a troubling governance gap: Nearly 60% of organizations lack comprehensive governance tracking and controls for their third-party data exchanges. This governance deficit creates blind spots that attackers actively exploit, making third-party data transfers an increasingly critical vulnerability.
Top Compliance Factors Driving Security Decisions in Regulated Industries
Which regulatory requirements are reshaping security priorities in 2025?
The survey clearly demonstrates that organizations are increasingly prioritizing regulatory compliance capabilities when selecting vendors, with 31% of respondents identifying compliance as a decisive factor in their final vendor selection. This focus is driven by the need to navigate complex regulations like GDPR, HIPAA, CMMC 2.0, the EU Data Act, and the EU AI Act, effective September 2025.
Organizations now face a complex regulatory landscape with significant penalties for noncompliance. The survey findings highlight the central role compliance now plays in security decision-making processes, particularly for organizations operating in highly regulated industries.
Why are security certifications becoming a make-or-break factor?
The importance of compliance is further highlighted by several key findings from the survey:
- 56% of respondents rate security certifications as “extremely important” during the vendor discovery phase
- More than half struggle to obtain adequate security information during vendor evaluations
- 63% of respondents actively seek detailed security and compliance information before even engaging with potential vendors
- Nearly one-quarter reject vendors over security concerns often tied to compliance failures
Kiteworks addresses these pain points with a robust compliance framework, including FedRAMP Moderate and High, SOC 2 Type II, ISO 27001, ISO 27017, ISO 27018, and IRAP validations, ensuring seamless adherence to global standards.
Key Takeaways From the 2025 Data Security & Compliance Survey
-
Third-Party Data Governance Reveals Critical Security Gaps
Nearly 60% of organizations lack comprehensive governance tracking and controls for their third-party data exchanges, creating exploitable blind spots for attackers. The Verizon 2025 Data Breach Investigations Report confirms this vulnerability, showing third-party breaches have doubled to 30% of all incidents, particularly through attacks on legacy file sharing solutions.
-
Compliance Capabilities Now Drive Vendor Selection Decisions
Regulatory compliance has evolved from a checkbox exercise to a strategic imperative, with 31% of respondents identifying compliance as a decisive factor in their final vendor selection. This prioritization reflects the growing complexity of navigating regulations like GDPR, HIPAA, CMMC 2.0, the EU Data Act, and the EU AI Act, which impose significant penalties for noncompliance.
-
Security Certification Requirements Create Pre-Engagement Filtering
Security certifications have become critical trust signals, with 56% of respondents rating them as “extremely important” during the vendor discovery phase and 63% seeking detailed security information before even engaging vendors. This pre-engagement research creates a “shadow evaluation” where vendors may be eliminated without their knowledge, emphasizing the importance of transparent security documentation.
-
Integration Capabilities Have Become Deal-Breakers
While security and compliance form the foundation of vendor selection, 42% of respondents identify integration capabilities as a key value driver in their decision-making process. The significance of seamless integration is further highlighted by the 39% of organizations that eliminate vendors specifically due to inadequate integration capabilities, demonstrating how this factor has evolved from a preference to a requirement.
Security Information Gap: What Buyers Need Before Making Decisions
How are security leaders researching vendors before engagement?
The survey reveals that 63% of respondents actively seek detailed security and compliance information before even engaging with potential vendors. This pre-engagement research phase has become increasingly important as security leaders work to narrow their options before investing time in vendor discussions.
This information-gathering process typically occurs early in the buying journey, creating a “shadow evaluation” period where vendors may be eliminated from consideration without their knowledge. Organizations that provide comprehensive, accessible security documentation gain a significant advantage in this critical phase.
What security information obstacles are undermining vendor evaluations?
Despite the critical importance of security information, more than half of survey respondents report struggling to obtain adequate security details during vendor evaluations. This information gap creates significant friction in the buying process and often leads to delays or vendor disqualification.
Nearly one-quarter of respondents report rejecting vendors specifically over security concerns, often tied to compliance failures. This high rejection rate underscores the importance of transparent, comprehensive security information throughout the vendor evaluation process.
What Security Leaders Prioritize in 2025
Why integration capabilities have become a decisive selection factor
While security and compliance form the foundation of vendor selection, the survey reveals that practical implementation concerns also heavily influence buying decisions. Seamless integration capabilities prove critical for customer satisfaction and long-term success, with 42% of survey respondents identifying integration capabilities as a key value driver.
The importance of integration is further emphasized by the 39% of respondents who reported eliminating potential vendors from consideration specifically due to inadequate integration capabilities. This high elimination rate underscores how integration has evolved from a “nice-to-have” feature to a core requirement.
Organizations considering Kiteworks benefit from its comprehensive integration capabilities, including enterprise authentication and security integration, productivity suite and legacy system support, automation and administration tools, and API extensibility.
How vendor reputation and stability influence long-term security strategy
Vendor reputation and stability remain key factors in the security decision-making process, with nearly two-thirds of respondents prioritizing these attributes during the vetting process, including 30% indicating vendor stability is a high priority.
This focus on stability stems from the recognition that security implementations represent long-term commitments. Organizations increasingly view vendor stability as a risk management consideration, seeking partners with proven track records and clear business continuity.
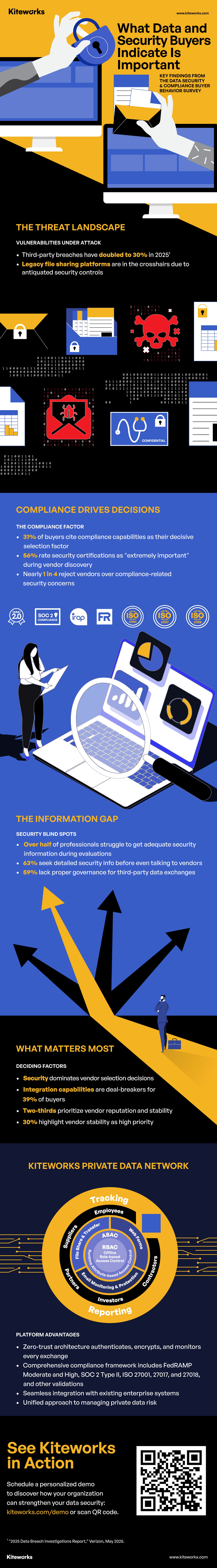
Zero Trust Architecture: The Foundation of Modern Private Data Security
What elements comprise an effective zero trust data exchange framework?
Zero trust architecture represents a fundamental shift from traditional perimeter-based security to a model that assumes no user or system should be inherently trusted. For data exchange specifically, this approach ensures that all data transfers are authenticated, encrypted, and monitored at every stage.
How do organizations implement zero trust for private data protection?
Organizations implementing zero trust for data protection typically follow a phased approach that prioritizes high-value data exchanges while gradually expanding protection across all communication channels. Kiteworks’ Private Data Network simplifies this implementation by providing a unified platform that implements zero trust principles specifically for data exchange.
The survey findings indicate that organizations adopting zero trust architectures for data exchange experience significant improvements in their security posture and compliance stance. This architectural approach aligns directly with the priorities identified in the survey, addressing both security concerns and compliance requirements.
Kiteworks’ Private Data Network: Meeting the Needs of Regulated Industries
What makes Kiteworks’ architecture uniquely suited for regulated industries?
Kiteworks’ Private Data Network architecture directly addresses the security and compliance challenges identified in the survey through a comprehensive approach to data protection. This unified platform provides centralized visibility and control across all communication channels, implementing zero trust principles throughout the data exchange process.
As the survey findings indicate, organizations are seeking solutions that combine robust security controls with practical integration capabilities and strong compliance frameworks. The Private Data Network architecture delivers on these requirements while simplifying the implementation of zero trust principles.
How does Kiteworks support compliance across regulatory frameworks?
The survey clearly demonstrates that compliance has become a decisive factor in vendor selection. Kiteworks addresses this priority through its comprehensive compliance framework, which includes support for a wide range of regulatory requirements and security certifications.
This robust compliance approach directly addresses the finding that 56% of respondents rate security certifications as “extremely important” during the vendor discovery phase. By providing comprehensive certification coverage, Kiteworks enables organizations to streamline their compliance processes while strengthening their security posture.
Conclusion: Data Security and Compliance Takeaways
Key survey findings highlight several trends that security leaders must address:
- The growing importance of compliance capabilities in vendor selections (31%)
- The critical role of security certifications as trust indicators (56%)
- The emergence of integration capabilities as decisive factors (42%)
- The increasing focus on vendor stability and reputation (over two-thirds)
To discover how your organization can strengthen its data security posture while simplifying compliance, schedule a personalized Kiteworks demo today. Our security experts will provide a customized assessment of your current data exchange security and demonstrate how Kiteworks’ Private Data Network can address your specific challenges.
Frequently Asked Questions
Zero trust architecture protects against third-party data breaches by implementing continuous authentication, least-privilege access, comprehensive encryption, and detailed monitoring across all data exchanges. This approach ensures that even if a third party’s systems are compromised, attackers cannot easily access your data or move laterally within your network.
The survey indicates that 42% of respondents identify integration capabilities as a key value driver, with 39% eliminating vendors due to inadequate integration. Security leaders should prioritize integration with identity and access management systems, security monitoring platforms, data loss prevention systems, and core business applications that handle sensitive data.
Kiteworks’ Private Data Network addresses the survey findings by implementing zero trust architecture to mitigate the vulnerabilities targeting data exchange systems. It provides comprehensive compliance capabilities to satisfy the 31% of buyers who cite compliance as decisive. The platform includes robust integration options to meet the needs of the 42% who identify integration as a key value driver, while its established market position addresses stability concerns.
With the survey finding that nearly 60% of organizations lack comprehensive governance for third-party data exchanges, improving this area is critical. Organizations should implement comprehensive third-party risk assessments, establish clear data handling requirements in contracts, implement technical controls for all exchanges, maintain an inventory of all third-party data flows, and establish incident response procedures specific to third-party breaches.
Additional Resources
- Blog Post Zero Trust Architecture: Never Trust, Always Verify
- Video How Kiteworks Helps Advance the NSA’s Zero Trust at the Data Layer Model
- Blog Post What It Means to Extend Zero Trust to the Content Layer
- Blog Post Building Trust in Generative AI with a Zero Trust Approach
- Video Kiteworks + Forcepoint: Demonstrating Compliance and Zero Trust at the Content Layer