
Who Needs SOC 2 Compliance? Checklist for CISOs
As a CISO, IT management executive, CIO, or cybersecurity compliance and risk management leader of a large enterprise, you understand the importance of SOC 2 compliance. But who exactly needs SOC 2 compliance? In today’s digital landscape, where data breaches and cyber threats are rampant, SOC 2 compliance is crucial for any organization that handles sensitive customer data, financial information, or intellectual property.
When it comes to cybersecurity, there are several terms that you should be familiar with. Electronic Data Interchange (EDI), secure FTP (SFTP), Managed File Transfer (MFT), advanced encryption standard (AES), Encrypting File System (EFS), Enterprise File Protection (EFP), Secure Hypertext Transfer Protocol (HTTPS), File Transfer Protocol (FTP), and file transfer protocol over secure sockets layer (FTPS) are all important components of a secure data transfer process.
Risk management compliance is another critical aspect of maintaining a secure environment. Understanding terms such as HTTP, GDPR, FISMA, CMMC, Health Insurance Portability and Accountability Act (HIPA), and Federal Risk and Authorization Management Program will help you navigate the complex landscape of compliance requirements.
| Topics | Discussions |
|---|---|
| Understanding SOC 2 Compliance: Essential Guide for Businesses | Learn about the essential guide for businesses to understand SOC 2 compliance and its importance in today’s cybersecurity landscape. |
| Unlocking the Power of SOC 2 and ISO 27001 for Large-Scale Industries | Discover how SOC 2 and ISO 27001 can benefit large-scale industries and enhance their cybersecurity posture. |
| Essential Features and Technical Specs for Your SOC 2 Compliance Checklist | Get insights into the essential features and technical specifications that should be included in your SOC 2 compliance checklist. |
| Understanding the Risks: Non-Compliant Protocols in SOC 2 Compliance | Explore the risks associated with non-compliant protocols in SOC 2 compliance and how to mitigate them. |
| Unlocking Key Compliance Advantages: SOC 2 Versus ISO 27001 Explained | Learn about the key compliance advantages of SOC 2 versus ISO 27001 and which framework is best suited for your organization. |
| Unveiling Eye-Opening Corporate Cybersecurity Statistics You Need to Know | Discover eye-opening corporate cybersecurity statistics that highlight the importance of SOC 2 compliance and robust cybersecurity measures. |
| Mastering SOC 2 Compliance: Essential Industry Standards for Streamlined Workflows | Master the essential industry standards for SOC 2 compliance and streamline your cybersecurity workflows. |
| Kiteworks Private Content Network for SOC 2 Vs ISO 27001 | Explore how Kiteworks Private Content Network can help you achieve SOC 2 compliance and compare it with ISO 27001. |
| FAQs About SOC 2 Compliance Checklist | Find answers to frequently asked questions about SOC 2 compliance checklist and ensure you have a comprehensive understanding of the requirements. |
| Additional Resources | Access additional resources to further enhance your knowledge of SOC 2 compliance and cybersecurity best practices. |
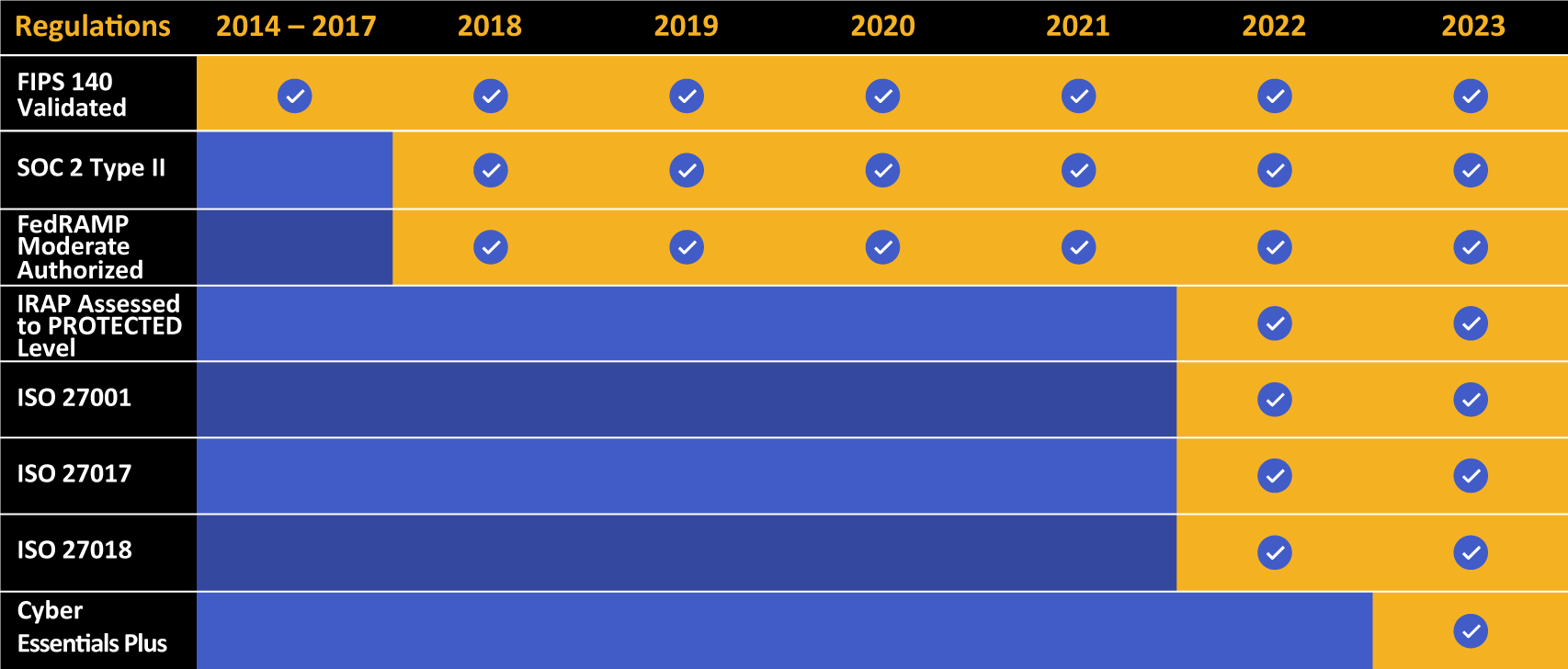
Kiteworks touts a long list of compliance and certification achievements.
Understanding SOC 2 Compliance: Essential Guide for Businesses
SOC 2 compliance is a crucial aspect of cybersecurity for businesses that handle sensitive customer data. It provides assurance to clients and stakeholders that an organization has implemented effective controls to protect their data. According to the essential guide on SOC 2 compliance by Intruder, this framework is based on five trust service criteria: security, availability, processing integrity, confidentiality, and privacy.
Security is the cornerstone of SOC 2 compliance, serving as the bedrock for safeguarding information and systems against unauthorized access, both physical and logical. Robust access controls, fortified network security measures, and vigilant monitoring systems are imperative to thwart potential threats. Availability is equally crucial, ensuring seamless accessibility and uninterrupted operation of systems and services, thereby minimizing downtime and disruptions. Processing integrity plays a pivotal role in guaranteeing accurate, complete, and timely data processing, fortified by stringent controls to prevent errors or unauthorized alterations.
Protecting sensitive information is of utmost importance in today’s digital landscape. Ensuring confidentiality and privacy is crucial to safeguarding data from unauthorized access. Confidentiality guarantees that only authorized individuals or entities can access the data, while privacy focuses on the proper collection, use, and disclosure of personal information in compliance with relevant laws and regulations.
Organizations striving for SOC 2 compliance must establish and maintain comprehensive policies, procedures, and controls across five essential trust service criteria. These criteria form the foundation for maintaining the highest standards of security, availability, processing integrity, confidentiality, and privacy.
Key considerations for SOC 2 compliance
- Identify and classify sensitive data: Understand the types of data your organization handles and categorize them based on their sensitivity.
- Implement access controls: Establish strong authentication mechanisms, role-based access controls, and regular access reviews to ensure only authorized individuals can access sensitive data.
- Monitor and detect security incidents: Implement robust monitoring systems to detect and respond to security incidents promptly. This includes intrusion detection systems, log monitoring, and security information and event management (SIEM) solutions.
- Regularly assess and test controls: Conduct regular internal and external audits, vulnerability assessments, and penetration testing to identify weaknesses in your security controls and address them promptly.
- Establish incident response and data breach notification procedures: Develop a comprehensive incident response plan that outlines the steps to be taken in the event of a security incident or data breach. Ensure you have mechanisms in place to notify affected individuals or entities as required by applicable laws and regulations.
Unlocking the Power of SOC 2 and ISO 27001 for Large-Scale Industries
Having useful technical knowledge about SOC 2 compliance, soc 2 compliance checklist, and soc 2 vs iso 27001 can provide significant advantages and benefits for those who need to ensure their organization’s cybersecurity posture. Understanding the intricacies of SOC 2 compliance allows businesses to establish and maintain robust security controls, safeguard sensitive data, and build trust with their clients and partners. By following a comprehensive soc 2 compliance checklist, organizations can systematically assess their security practices, identify vulnerabilities, and implement necessary improvements. Additionally, comparing SOC 2 with ISO 27001 helps organizations determine the most suitable framework for their specific security requirements. This knowledge empowers businesses to make informed decisions, enhance their security posture, and effectively mitigate cyber risks.
Understanding the importance of SOC 2 compliance in government operations
SOC 2 compliance plays a critical role in the operations of government entities, ensuring that they meet the necessary security and privacy requirements. As highlighted by Vanta, SOC 2 compliance is instrumental in establishing trust and confidence in government operations, showcasing their unwavering commitment to safeguarding sensitive data. This is particularly crucial for government agencies entrusted with handling citizens’ personal information, financial data, and other highly sensitive data.
Adhering to SOC 2 compliance standards is crucial for government organizations to effectively manage risks and ensure the confidentiality, integrity, and availability of data. The Vanta resource emphasizes the significance of SOC 2 compliance as it provides a robust framework for implementing stringent security controls, conducting regular audits, and continuously monitoring and improving security practices. By aligning government operations with industry best practices and regulatory requirements, SOC 2 compliance significantly reduces the risk of data breaches and unauthorized access.
Unlocking the power of SOC 2 and ISO 27001 for industrial suppliers and manufacturers
Unlocking the potential of SOC 2 and ISO 27001 can revolutionize the cybersecurity landscape for industrial suppliers and manufacturers. These two robust cybersecurity frameworks lay a solid foundation for elevating security practices and fostering trust among customers. A recent study conducted by Vanta reveals that an overwhelming 78% of customers consider SOC 2 compliance as an essential requirement when assessing potential suppliers. This statistic underscores the significance of SOC 2 certification in providing industrial suppliers with a distinct competitive advantage.
ISO 27001, on the other hand, stands as a globally recognized standard for information security management systems. Its implementation showcases the unwavering dedication of industrial suppliers and manufacturers to safeguarding sensitive data and upholding the confidentiality, integrity, and availability of information. This commitment not only fosters trust among customers and partners but also bolsters the overall cybersecurity posture of organizations.
Unlocking the power of SOC 2 compliance for high performance in banking and finance
The banking and finance industry operates within a highly regulated environment, necessitating strict adherence to compliance standards to safeguard the security and privacy of customer data. One such imperative is SOC 2 compliance, which places emphasis on the security, availability, processing integrity, confidentiality, and privacy of customer data. Complying with SOC 2 can unlock a myriad of advantages for banking and finance organizations.
SOC 2 compliance is a critical demonstration of an organization’s unwavering commitment to safeguarding data security and privacy. By implementing robust controls and safeguards, it assures customers and stakeholders that sensitive information is protected with utmost care. This unwavering dedication to data security not only enhances the organization’s reputation but also fosters trust among clients, leading to heightened customer loyalty and retention.
Moreover, the implementation of SOC 2 compliance can provide a significant advantage to banking and finance organizations. In an industry plagued by rampant data breaches and relentless cyber threats, achieving SOC 2 compliance sets an organization apart from its competitors. It serves as a potent marketing tool, demonstrating the organization’s unwavering commitment to safeguarding data and instilling confidence in potential clients, ultimately leading them to choose their services over others.
Easily customize SOC 2 and ISO 27001 for your business and ecommerce needs
The SOC 2 and ISO 27001 frameworks stand as pillars of trust and recognition when it comes to safeguarding the security and privacy of data within organizations. By tailoring these frameworks to align with your business and ecommerce operations, you can fortify your security posture and gain a competitive edge in the ever-evolving market.
Implementing SOC 2 allows you to customize controls and requirements to align with your unique business processes and industry-specific regulations. This demonstrates to your customers and partners that you have implemented robust security measures to safeguard their sensitive data. Similarly, ISO 27001 offers a flexible framework that can be tailored to address the specific risks and compliance requirements of your ecommerce operations. By adopting ISO 27001, you establish a systematic approach to managing information security, fostering trust with your customers.
Streamlining soc 2 implementation over iso 27001 for enhanced healthcare cybersecurity
The healthcare industry must prioritize the implementation of robust cybersecurity measures to safeguard sensitive patient data and maintain the integrity of healthcare systems. When it comes to selecting the most suitable framework for bolstering healthcare cybersecurity, organizations often find themselves at a crossroads between SOC 2 and ISO 27001. While both frameworks offer valuable security controls, opting for streamlined SOC 2 implementation can yield distinct advantages within the healthcare sector.
SOC 2, a robust framework tailored for service organizations, proves to be an ideal solution for healthcare providers that heavily rely on multiple third-party vendors and service providers. By implementing SOC 2 controls, healthcare organizations can effectively ensure that their vendors meet the essential security requirements, thereby mitigating the risk of potential data breaches and other detrimental cybersecurity incidents.
Moreover, SOC 2 places a strong emphasis on safeguarding the security, availability, processing integrity, confidentiality, and privacy of sensitive data, aligning seamlessly with the unique requirements of the healthcare sector. This robust framework offers a holistic approach to cybersecurity, encompassing critical aspects such as stringent access controls, robust data encryption, swift incident response, and continuous monitoring.
When it comes to cybersecurity in the healthcare industry, organizations have two popular frameworks to choose from: SOC 2 and ISO 27001. While both frameworks offer valuable guidance, healthcare organizations can benefit from a more targeted and industry-specific approach by streamlining SOC 2 implementation.
SOC 2 places a strong emphasis on service organizations, making it particularly relevant for healthcare providers. Its alignment with healthcare requirements ensures that organizations can enhance their cybersecurity measures and effectively protect patient data.
Choosing between SOC 2 and ISO 27001 for enhanced corporate law and paralegal sustainability
When it comes to bolstering corporate law and paralegal sustainability, the choice between SOC 2 and ISO 27001 carries significant weight. Both frameworks offer invaluable security controls and certifications that enable organizations to safeguard sensitive data and showcase their unwavering dedication to data privacy and security. It is imperative to grasp the fundamental distinctions between SOC 2 and ISO 27001 to make an astute decision.
SOC 2, developed by the American Institute of Certified Public Accountants (AICPA), is a comprehensive framework that focuses on safeguarding the security, availability, processing integrity, confidentiality, and privacy of customer data. It is specifically tailored for service organizations that store and process customer data in the cloud. SOC 2 compliance serves as a testament to an organization’s commitment to implementing robust controls that effectively protect customer data and adhere to specific trust service criteria.
ISO 27001, an internationally recognized standard, offers a systematic approach to effectively managing sensitive company information. Its primary focus lies in establishing, implementing, maintaining, and continually improving an information security management system (ISMS). By obtaining ISO 27001 certification, organizations demonstrate their commitment to implementing a comprehensive set of controls that effectively manage information security risks and safeguard sensitive data.
When it comes to choosing between SOC 2 and ISO 27001, there are several factors to consider. These frameworks offer valuable guidance for organizations, but the decision ultimately depends on industry requirements, customer expectations, and regulatory compliance needs.
Organizations that provide cloud-based services often prefer SOC 2. This framework allows them to demonstrate the security and privacy of customer data, providing assurance to their clients. On the other hand, ISO 27001 is globally recognized and may be required by specific industries or jurisdictions.
Essential Features and Technical Specs for Your SOC 2 Compliance Checklist
Ensuring SOC 2 compliance is an absolute necessity for organizations entrusted with sensitive customer data. To guarantee a comprehensive compliance checklist, it is imperative to incorporate essential features and technical specifications. These crucial elements establish a robust security framework and unequivocally demonstrate your unwavering commitment to safeguarding customer information.
Access controls are a critical component of SOC 2 compliance. To ensure unauthorized access is prevented, it is imperative to implement robust authentication mechanisms, such as multi-factor authentication (MFA). This adds an extra layer of security by requiring users to provide multiple forms of identification. Additionally, role-based access controls (RBAC) should be established to restrict user privileges and safeguard sensitive data from unauthorized individuals.
Data encryption is a critical component of SOC 2 compliance. Safeguarding sensitive information from unauthorized access requires the implementation of robust encryption measures. It is imperative to employ strong encryption algorithms and ensure the proper management and protection of encryption keys.
Ensuring SOC 2 compliance necessitates the implementation of robust monitoring and logging practices. By establishing a comprehensive logging system, you gain the ability to track and analyze system activities, detect anomalies, and thoroughly investigate potential security incidents. It is of utmost importance to establish and enforce log retention policies while regularly reviewing logs to identify any suspicious activities.
- Implementing intrusion detection and prevention systems (IDPS) helps detect and mitigate potential security breaches. These systems monitor network traffic, identify malicious activities, and take proactive measures to prevent unauthorized access.
- Regular vulnerability assessments and penetration testing are essential for SOC 2 compliance. These tests help identify and address potential vulnerabilities in your systems and applications. It’s important to conduct these assessments regularly and remediate any identified vulnerabilities promptly.
- Establishing incident response and management processes is crucial for SOC 2 compliance. Having a well-defined incident response plan helps ensure that security incidents are promptly detected, contained, and resolved. It’s important to regularly test and update your incident response plan to address emerging threats.
- Continuous monitoring and auditing of your systems and controls are essential for SOC 2 compliance. Regularly reviewing and assessing your security controls helps ensure that they are effective and aligned with industry best practices. It’s important to document and track any changes made to your systems and controls.
Understanding the Risks: Non-Compliant Protocols in SOC 2 Compliance
SOC 2 compliance is an absolutely critical element in safeguarding the security and privacy of sensitive data within organizations. It is imperative to fully comprehend and address the risks associated with non-compliant protocols. One particular risk that demands attention is the utilization of outdated or unsupported protocols.
Outdated protocols present a grave risk to SOC 2 compliance. These protocols often lack the essential security features and updates needed to safeguard against emerging threats. Exploiting the known vulnerabilities in these protocols, attackers can gain unauthorized access, compromise data, and jeopardize compliance.
One of the critical risks associated with SOC 2 compliance lies in the utilization of non-encrypted protocols. The significance of encryption cannot be overstated when it comes to protecting data during transmission. It ensures the confidentiality and integrity of information, shielding it from unauthorized interception and eavesdropping. However, the use of non-encrypted protocols can expose sensitive data, compromising its confidentiality and integrity.
Moreover, the utilization of non-compliant protocols can lead to compatibility issues and impede seamless integration with other systems and services. This, in turn, can result in operational inefficiencies, heightened complexity, and potential security vulnerabilities. It is imperative for organizations to ensure that the protocols they employ align with the stringent requirements of SOC 2 compliance in order to effectively mitigate these risks.
Unlocking Key Compliance Advantages: SOC 2 Versus ISO 27001 Explained
When CISOs, IT management professionals, CIOs, cybersecurity risk management engineers, and user privacy compliance leaders of enterprise-level organizations in various industry sectors possess a deeper understanding of the advantages of complying with data security standards and user privacy regulations, they gain a significant edge in safeguarding their organizations’ sensitive information. With enhanced technical knowledge, these professionals can effectively implement robust cybersecurity measures, identify potential vulnerabilities, and mitigate risks. By staying informed about the latest industry trends and best practices, they can proactively address emerging threats and ensure compliance with evolving regulations. This technical expertise empowers them to make informed decisions, implement appropriate security controls, and protect their organizations from potential data breaches and regulatory penalties. Moreover, by understanding the benefits of compliance, they can effectively communicate the importance of data security and privacy to stakeholders, fostering a culture of security awareness and accountability throughout the organization.
Affordable SOC 2 compliance essentials for thriving businesses and ecommerce platforms
SOC 2 compliance is an increasingly vital requirement for businesses and ecommerce platforms that handle sensitive customer data. While ISO 27001 certification focuses on information security management, SOC 2 certification specifically addresses the security, availability, processing integrity, confidentiality, and privacy of customer data. Both certifications hold significant value, but SOC 2 compliance is particularly pertinent for organizations that store and process customer data in the cloud.
SOC 2 compliance offers a multitude of benefits, making it an essential framework for evaluating and enhancing an organization’s internal controls pertaining to customer data. By implementing SOC 2 controls, businesses can showcase their unwavering dedication to safeguarding customer information and adhering to industry best practices. This not only fosters trust among customers and partners but also sets the organization apart from its competitors, establishing a strong competitive edge.
When it comes to achieving SOC 2 compliance, businesses and ecommerce platforms must prioritize a number of essential considerations. One of the first steps is to conduct a comprehensive risk assessment, which plays a critical role in identifying potential vulnerabilities and developing an effective risk management strategy. This assessment encompasses evaluating the security of both physical and logical access controls, as well as assessing the efficacy of existing security policies and procedures.
Implementing robust access controls and employing stringent encryption measures are imperative for safeguarding customer data. It is crucial to establish multi-factor authentication, role-based access controls, and encryption protocols for data both in transit and at rest. Additionally, continuous monitoring and comprehensive logging of access attempts and system activities play a pivotal role in promptly identifying and mitigating potential security incidents.
Unlocking the importance of SOC 2 compliance for stability in US government offices and contractors
The stability and security of U.S. government offices and contractors are paramount, particularly in safeguarding sensitive data and ensuring compliance with industry regulations. One critical element in achieving this stability is SOC 2 compliance. SOC 2, or Service Organization Control 2, is a certification that prioritizes the security, availability, processing integrity, confidentiality, and privacy of data within service organizations.
Obtaining SOC 2 compliance is crucial for government offices and contractors to showcase their unwavering dedication to protecting sensitive information. This certification serves as a testament to stakeholders that the organization has implemented robust controls and processes to safeguard data from unauthorized access, disclosure, and alteration. SOC 2 compliance also aids organizations in meeting the requirements of regulatory frameworks like the Health Insurance Portability and Accountability Act and the Gramm-Leach-Bliley Act (GLBA).
When it comes to certification, SOC 2 and ISO 27001 have a key difference in their assessment scope. While ISO 27001 focuses on an organization’s overall information security management system, SOC 2 specifically evaluates controls and processes related to data security and privacy. Independent auditors conduct SOC 2 assessments, meticulously evaluating adherence to the Trust Services Criteria (TSC). These criteria encompass security, availability, processing integrity, confidentiality, and privacy.
Government offices and contractors can greatly benefit from achieving SOC 2 compliance. This crucial certification not only enhances the organization’s reputation and instills confidence in stakeholders, but it also plays a vital role in mitigating the risk of data breaches and non-compliance with industry regulations. By fully understanding and embracing the significance of SOC 2 compliance, government offices and contractors can ensure the stability and security of their operations, thereby contributing to the overall stability of the U.S. government ecosystem.
Boost your Soc 2 compliance with our customizable workflow for manufacturers and global distributors
Enhancing your SOC 2 compliance is absolutely essential for manufacturers and global distributors who prioritize the security and privacy of sensitive data. Achieving SOC 2 certification showcases your unwavering dedication to implementing robust controls and safeguards to safeguard customer information. By leveraging our highly adaptable workflow, you can streamline your compliance efforts and efficiently attain SOC 2 certification.
Our highly adaptable workflow is specifically tailored to meet the unique demands and complexities faced by manufacturers and global distributors. We understand the challenges and requirements of your industry, and our solution provides a comprehensive framework that encompasses all the essential steps for achieving SOC 2 compliance. This includes conducting thorough risk assessments, developing robust policies, implementing effective controls, and maintaining continuous monitoring.
Our customizable workflow empowers you to align the compliance process with your organization’s unique needs and objectives. This unparalleled flexibility enables you to prioritize the areas that are most critical to your business, ensuring seamless adherence to SOC 2 requirements while minimizing unnecessary efforts and costs. By seamlessly integrating our workflow, you can bolster your security posture, foster trust with your valued customers, and gain a distinct competitive advantage in the dynamic market.
Fast track your Soc 2 compliance checklist for enhanced scalability in healthcare facilities
When it comes to safeguarding the security and privacy of sensitive data within healthcare facilities, adherence to industry standards becomes paramount. In this context, two certifications that hold significant recognition are ISO 27001 and SOC 2. While both certifications primarily focus on information security, they do exhibit notable distinctions.
ISO 27001, the internationally recognized standard, serves as a robust framework for establishing, implementing, maintaining, and continuously enhancing an information security management system (ISMS). It encompasses a wide array of security controls, necessitating organizations to conduct comprehensive risk assessments and deploy appropriate measures to mitigate identified risks.
SOC 2, however, stands apart as a certification established by the esteemed American Institute of Certified Public Accountants (AICPA). Its primary focus lies in safeguarding the security, availability, processing integrity, confidentiality, and privacy of invaluable customer data. Independent auditors conduct SOC 2 audits, meticulously evaluating an organization’s controls and processes against predefined criteria.
When it comes to expediting SOC 2 compliance for healthcare facilities, there are a number of strategic measures that can be taken. To begin, a comprehensive evaluation of existing security controls should be conducted, with a focus on identifying any potential gaps or areas in need of enhancement. This evaluation can be carried out through internal audits or by enlisting the expertise of a reputable third-party cybersecurity firm.
First and foremost, it is imperative for healthcare facilities to prioritize the development and implementation of policies and procedures that align seamlessly with the SOC 2 criteria. This entails establishing crystal-clear guidelines encompassing data access, encryption, incident response, and comprehensive employee training. To ensure ongoing compliance, it is crucial to rigorously enforce these requirements and conduct regular monitoring and testing of the controls in place.
Simplifying SOC 2 compliance checklist for law firms and paralegal service providers
Ensuring the security and privacy of sensitive client data is of utmost importance for law firms and paralegal service providers. One critical requirement in this regard is Soc 2 compliance. By simplifying the Soc 2 compliance checklist, these organizations can streamline their efforts and achieve certification more efficiently, thereby safeguarding their clients’ information.
When it comes to ensuring compliance with Soc 2 standards, one area that demands utmost attention is the establishment of robust policies and procedures governing the protection of valuable client data. This entails the implementation of stringent access controls, robust encryption measures, and well-defined incident response plans to effectively mitigate the ever-looming threats of data breaches and unauthorized access.
One crucial element to consider in the checklist is the evaluation of physical and environmental controls implemented to protect client data. It is imperative to ensure that data centers and server rooms are equipped with robust security measures, including access controls, surveillance systems, and fire suppression systems.
Furthermore, it is imperative to underscore the significance of continuous monitoring and rigorous testing of security controls to promptly identify vulnerabilities and take immediate action. This entails conducting regular penetration testing, vulnerability assessments, and comprehensive security awareness training for all personnel.
Lastly, it is crucial to emphasize the significance of comprehensive documentation and meticulous record-keeping for all security-related activities and incidents. This encompasses the diligent tracking of security policies, procedures, and incident response plans, alongside the meticulous maintenance of logs that capture security events and incidents, serving as invaluable resources for auditing purposes.
Easy guide to SOC 2 compliance for banks and financial institutions
Financial institutions, such as banks, face mounting pressure to showcase their unwavering commitment to safeguarding data security and privacy. One effective approach to achieving this is by obtaining SOC 2 compliance—a widely recognized certification that places emphasis on the security, availability, processing integrity, confidentiality, and privacy of customer data. SOC 2 provides customers and stakeholders with the assurance that the organization has implemented robust controls to protect their sensitive information.
Obtaining SOC 2 compliance can be a highly intricate and demanding process, particularly for banks and financial institutions. These entities handle vast volumes of sensitive financial data, underscoring the criticality of implementing robust security measures. To facilitate the navigation of the SOC 2 compliance journey, presented below is an exclusive guide meticulously tailored for banks and financial institutions:
1. Gain a Clear Understanding of the Scope: Begin by thoroughly defining the scope of your SOC 2 compliance initiatives. It is crucial to identify the systems, processes, and data that fall within the scope and require assessment against the SOC 2 criteria. This step will enable you to concentrate your efforts and allocate resources efficiently.
2. Perform a Comprehensive Gap Analysis: Evaluate your existing security controls and practices against the SOC 2 requirements with meticulous attention to detail. Identify any deficiencies or areas that necessitate enhancement. This in-depth analysis will serve as a strategic roadmap for implementing the requisite controls and processes to achieve full compliance.
3. Strengthen Your Security: Take immediate action to fortify your organization’s defenses based on the results of the comprehensive gap analysis. Address the identified vulnerabilities by implementing robust security controls. These controls encompass a range of measures, such as access controls, encryption protocols, incident response procedures, data backup and recovery strategies, and employee training initiatives. It is imperative to meticulously document and maintain evidence of these controls to ensure compliance during audits.
4. Continuously Monitor and Assess: SOC 2 compliance is an ongoing process. It is crucial to consistently monitor and assess your security controls to ensure their effectiveness and alignment with SOC 2 requirements. Conduct regular internal audits and assessments to identify emerging risks or areas that require improvement.
5. Engage a Third-Party Auditor: It is crucial to involve a qualified third-party auditor to achieve SOC 2 compliance. This auditor will thoroughly evaluate your organization’s controls and practices against the SOC 2 criteria, providing an independent assessment of your compliance. To ensure a comprehensive understanding of the unique challenges and requirements of the industry, it is recommended to select an auditor with a proven track record in auditing banks and financial institutions.
Unveiling Eye-Opening Corporate Cybersecurity Statistics You Need to Know
Understanding the implications of cybersecurity compliance and risk management strategy is vital for enterprise-level organizations across various industry sectors. Monitoring and analyzing relevant statistics play a crucial role in gaining valuable insights into data security, risk management, and compliance of sensitive content communications.
- Kiteworks’ Sensitive Content Communications Privacy and Compliance Report for 2023 reveals that 90% of enterprises use 4+ channels to share sensitive content, with 46% using six or more tools, systems platforms, and channels. This comprehensive global survey of IT, cybersecurity, and compliance professionals at enterprise-level organizations highlights the widespread use of multiple channels for sharing sensitive content.
- The report also indicates that more than 90% of corporations share sensitive content with 1,000 to 2,500 external organizations and third parties. This finding emphasizes the need for robust security measures to protect sensitive data when shared with a large number of external entities.
- Furthermore, the survey reveals that professionals across various industries, geographies, and job grades are concerned about a wide range of attack methods targeting sensitive data, including personally identifiable information (PII) and intellectual property (IP). This underscores the importance of implementing comprehensive security measures to safeguard sensitive content.
- Additionally, compliance remains a challenge for organizations, particularly in Europe where the EU’s General Data Protection Regulation (GDPR) imposes significant fines for noncompliance. The report highlights that most respondents are subject to data privacy regulations in at least one jurisdiction and are audited against industry standards. Moreover, 99% of respondents do business with government entities, necessitating compliance with special requirements for sharing private data and sensitive content.
For a comprehensive understanding of the latest insights and discoveries, we highly recommend consulting the Sensitive Content Communications Privacy and Compliance Report by Kiteworks.
Mastering SOC 2 Compliance: Essential Industry Standards for Streamlined Workflows
Implementing SOC 2 compliance is a crucial element in maintaining secure and efficient workflows across industries. The standards can be overwhelming, particularly when considering the five Trust Service Criteria: security, availability, processing integrity, confidentiality, and privacy. However, conquering these standards is not an insurmountable challenge. By acquiring the right knowledge and adopting a strategic approach, organizations can effectively navigate the complexities of SOC 2 compliance, ensuring streamlined workflows and robust security.
One of the most critical challenges faced in achieving SOC 2 compliance is the widespread lack of understanding surrounding the scope and requirements of these standards. Misconceptions can lead to inadequate preparation, resulting in failed audits and potential security breaches. Hence, it is imperative to develop a comprehensive grasp of the SOC 2 standards, encompassing the specific requirements for each of the five Trust Service Criteria. This knowledge will establish a robust foundation for implementing effective compliance strategies.
One of the key obstacles faced in achieving SOC 2 compliance is the scarcity of resources and expertise. Numerous organizations grapple with limited resources, be it personnel or budgetary constraints. This scarcity can pose challenges in dedicating the necessary time and effort towards compliance endeavors. Nevertheless, by employing strategic planning and prioritization, organizations can effectively allocate their resources, ensuring that compliance efforts remain uncompromised.
Undoubtedly, the perpetual nature of SOC 2 compliance can appear overwhelming to numerous organizations. Compliance is not a singular occurrence, but an ongoing procedure that necessitates consistent monitoring and updates. This can prove to be particularly arduous in the face of ever-evolving technology and the persistent emergence of security threats. Nevertheless, by adopting a proactive approach and demonstrating unwavering commitment to continuous improvement, organizations can effectively stay ahead of the curve, ensuring perpetual compliance and fortified security.
Kiteworks Private Content Network for SOC 2 Vs ISO 27001
Discover the immense power of a unified Private Content Network that seamlessly integrates secure email, secure file sharing, secure web forms, and MFT onto a single, robust platform. This exceptional solution empowers enterprise-level organizations to exert complete control, ensure utmost protection, and maintain comprehensive visibility over every file that enters and exits their network. Streamline your cybersecurity strategy and elevate your data security compliance with our unparalleled secure file transfer capabilities.
Discover the immense power of a robust solution that empowers you to effectively manage access to sensitive data, ensuring its utmost protection when shared externally. This unparalleled level of security is achieved through the seamless integration of automated end-to-end encryption, multi-factor authentication, and a comprehensive security infrastructure integration. Gain unparalleled visibility into all file activity, providing you with detailed insights into the who, what, when, and how of data sharing.
Moreover, leverage the exceptional capabilities of our cutting-edge email protection gateway that seamlessly automates email encryption and decryption, adding an extra layer of security to your data sharing processes.
It is of utmost importance for CISOs, IT management executives, CIOs, and leaders in cybersecurity risk management and data security compliance within enterprise-level organizations to ensure unwavering adherence to critical regulations and standards. These include GDPR, HIPAA, CMMC, Cyber Essentials Plus, IRAP, and others.
Experience the revolutionary capabilities of a state-of-the-art Private Content Network powered by Kiteworks. Transform your organization’s potential—book a custom demo now.
FAQs About SOC 2 Compliance Checklist
Understanding the implications of non-compliance with SOC 2 standards can aid organizations in risk mitigation and the avoidance of potential legal and financial repercussions. While not mandated by regulation, SOC 2 is frequently sought by clients and business associates to ensure the security and privacy of their data. Entities that manage sensitive client data—such as service providers, data centers, and cloud service providers—must adhere to SOC 2. This standard is applicable to any organization that stores, processes, or transmits client data. Possessing a SOC report signifies an organization’s dedication to security and compliance, thereby boosting trust and credibility with clients and stakeholders.
What are the consequences of not complying with SOC 2 requirements?
Failure to comply with SOC 2 requirements can have severe repercussions for organizations. To begin with, it can result in significant damage to their reputation, eroding the trust of clients and partners in the company’s ability to safeguard their sensitive data. Moreover, non-compliance can expose organizations to legal and regulatory entanglements, including the imposition of fines and penalties. Additionally, inadequate security controls stemming from non-compliance can heighten the risk of cyber threats and potential data breaches. Lastly, without SOC 2 compliance, companies may miss out on valuable business opportunities, as many clients demand adherence to these standards before establishing partnerships. Prioritizing SOC 2 compliance is imperative for organizations to mitigate these risks and ensure the security and trustworthiness of their systems and data.
Is SOC 2 a requirement by regulation?
SOC 2, while not mandated by regulation, serves as a widely recognized framework for evaluating and disclosing an organization’s system and data security, availability, processing integrity, confidentiality, and privacy. Its purpose is to provide customers and stakeholders with the assurance that the organization has implemented robust controls to safeguard their data. According to Imperva, SOC 2 compliance showcases an organization’s unwavering commitment to data security and can serve as a competitive advantage in the market.
Who needs to be compliant with SOC 2?
SOC 2 compliance is a critical requirement for organizations entrusted with sensitive customer data or those providing services to clients demanding robust data security measures. As highlighted by Reciprocity, several industries, including technology, healthcare, finance, and professional services, must adhere to SOC 2 compliance standards. By achieving SOC 2 compliance, these organizations demonstrate their commitment to safeguarding customer data against unauthorized access, disclosure, and misuse. This not only fosters trust with clients but also underscores their dedication to upholding data security and privacy. Maintaining SOC 2 compliance necessitates regular audits and assessments to evaluate the efficacy of security controls and processes.
To whom does SOC 2 apply?
SOC 2 compliance is a critical requirement for organizations that handle customer data, whether it’s stored in the cloud or on-premises. This compliance framework is particularly relevant for service providers, including SaaS companies, data centers, and managed service providers. It also applies to organizations in sensitive industries such as financial institutions, healthcare providers, and e-commerce platforms. The primary objective of SOC 2 compliance is to ensure that these organizations have implemented and maintained robust security controls to safeguard customer data from unauthorized access, disclosure, and misuse.
Who needs to have a SOC report?
Organizations that handle sensitive data and wish to demonstrate their unwavering commitment to security must possess a SOC report. A SOC report, also known as a System and Organization Controls report, offers an independent evaluation of an organization’s controls pertaining to security, availability, processing integrity, confidentiality, and privacy. This report holds immense significance for organizations that provide services to other companies, including data centers, cloud service providers, and managed service providers. By obtaining a SOC report, these organizations can provide their clients with the assurance that they have implemented robust controls to safeguard their data and systems. SOC reports also serve as a valuable asset for organizations seeking compliance with industry regulations and standards, such as the Health Insurance Portability and Accountability Act or the Payment Card Industry Data Security Standard (PCI DSS).
Additional Resources
- Case Study: Mandiant Uses Kiteworks to Protect the Sensitive Content That Helps Protect Businesses Worldwide
- Brief: Kiteworks Hardened Virtual Appliance
- Brief: Achieve Zero Trust Security with Kiteworks: A Comprehensive Approach to Data Protection
- Top 5: Top 5 Ways Kiteworks Secures Microsoft 365 Third-party Communications
- Webinar: How Automated Email Encryption Delivers Improved Privacy Protection and Compliance