
Mastering FIPS Compliance: Essential Guide for Cybersecurity Professionals
Are you a cybersecurity professional looking to enhance your knowledge of FIPS Compliance? In this comprehensive guide, we will explore the essential aspects of FIPS Compliance, including FIPS 140-3 and FIPS 197, to help you stay ahead in the ever-evolving cybersecurity landscape.
What Data Compliance Standards Matter?
Let’s start by introducing some key cybersecurity terms that you should be familiar with. Enterprise File Protection (EFP) solutions, such as secure FTP (SFTP) and file transfer protocol over secure sockets layer (FTPS), play a crucial role in securing data during file transfers. Advanced encryption standard (AES) is a widely used encryption algorithm that ensures data confidentiality. Managed File Transfer (MFT) solutions, like File Transfer Protocol (FTP) and Secure Hypertext Transfer Protocol (HTTPS), provide secure and reliable file transfer capabilities. Electronic Data Interchange (EDI) enables the exchange of structured data between organizations. Encrypting File System (EFS) provides file-level encryption for Windows operating systems.
Now, let’s delve into risk management compliance terms that are essential for cybersecurity professionals. The Health Insurance Portability and Accountability Act (HIPA) ensures the security and privacy of healthcare information. The GDPR sets guidelines for the protection of personal data of individuals within the European Union. HTTP is the foundation of data communication on the World Wide Web. The Federal Risk and Authorization Management Program provides a standardized approach to security assessment, authorization, and continuous monitoring for cloud products and services. The CMMC is a unified standard for implementing cybersecurity across the defense industrial base. The FISMA establishes a framework for protecting government information and assets.
| Topics | Discussions |
|---|---|
| All About FIPS Compliance: Essential Guide for IT Professionals | Explore the essential aspects of FIPS Compliance, including FIPS 140-3 and FIPS 197. |
| Unlocking the Power of FIPS 197: A Key to Enhanced Cybersecurity for Large Industries | Discover how FIPS 197 compliance can enhance cybersecurity in large industries. |
| Unlocking Key Features and Technical Specifications in FIPS 140-3: A Comprehensive Guide | Learn about the key features and technical specifications of FIPS 140-3. |
| Overcoming FIPS Compliance Challenges in Non-Compliant Protocols: A Comprehensive Guide | Find solutions to overcome FIPS Compliance challenges in non-compliant protocols. |
| Unlocking Key Benefits of FIPS 197 Compliance for Enhanced Cybersecurity | Discover the key benefits of FIPS 197 compliance for enhanced cybersecurity. |
| Unveiling the Latest Intriguing Trends in Enterprise Cybersecurity | Stay updated with the latest intriguing trends in enterprise cybersecurity. |
| Mastering FIPS Compliance: Essential Industry Standards for Effective Workflows | Understand the essential industry standards for effective workflows in FIPS Compliance. |
| Kiteworks Private Content Network for FIPS 197 | Explore the Kiteworks Private Content Network for FIPS 197 compliance. |
| FAQs About FIPS 140-3 | Get answers to frequently asked questions about FIPS 140-3. |
| Additional Resources | Access additional resources to further expand your knowledge of FIPS Compliance. |
All About FIPS Compliance: Essential Guide for IT Professionals
FIPS compliance is a critical requirement for cybersecurity professionals working in the government and defense sectors. The FIPS compliance standards are established by the National Institute of Standards and Technology and are designed to ensure the security and integrity of sensitive information. Mastering FIPS compliance is essential for cybersecurity professionals to protect classified data and maintain the trust of their stakeholders.
The process of achieving FIPS compliance entails the implementation of a comprehensive set of security controls and guidelines. These controls are crucial for safeguarding information systems and networks against potential threats. They encompass a wide range of cybersecurity aspects, such as access control, encryption, authentication, and auditing. It is imperative for cybersecurity professionals to possess a profound understanding of these controls and their application to meet their organization’s specific requirements.
To achieve FIPS compliance, cybersecurity professionals must adhere to a systematic approach encompassing risk assessment, security planning, implementation, and continuous monitoring. This entails identifying potential vulnerabilities, implementing appropriate security measures, and regularly evaluating and updating the security posture. It is imperative for professionals to remain abreast of the latest FIPS standards and guidelines to ensure ongoing compliance and safeguard against emerging threats.
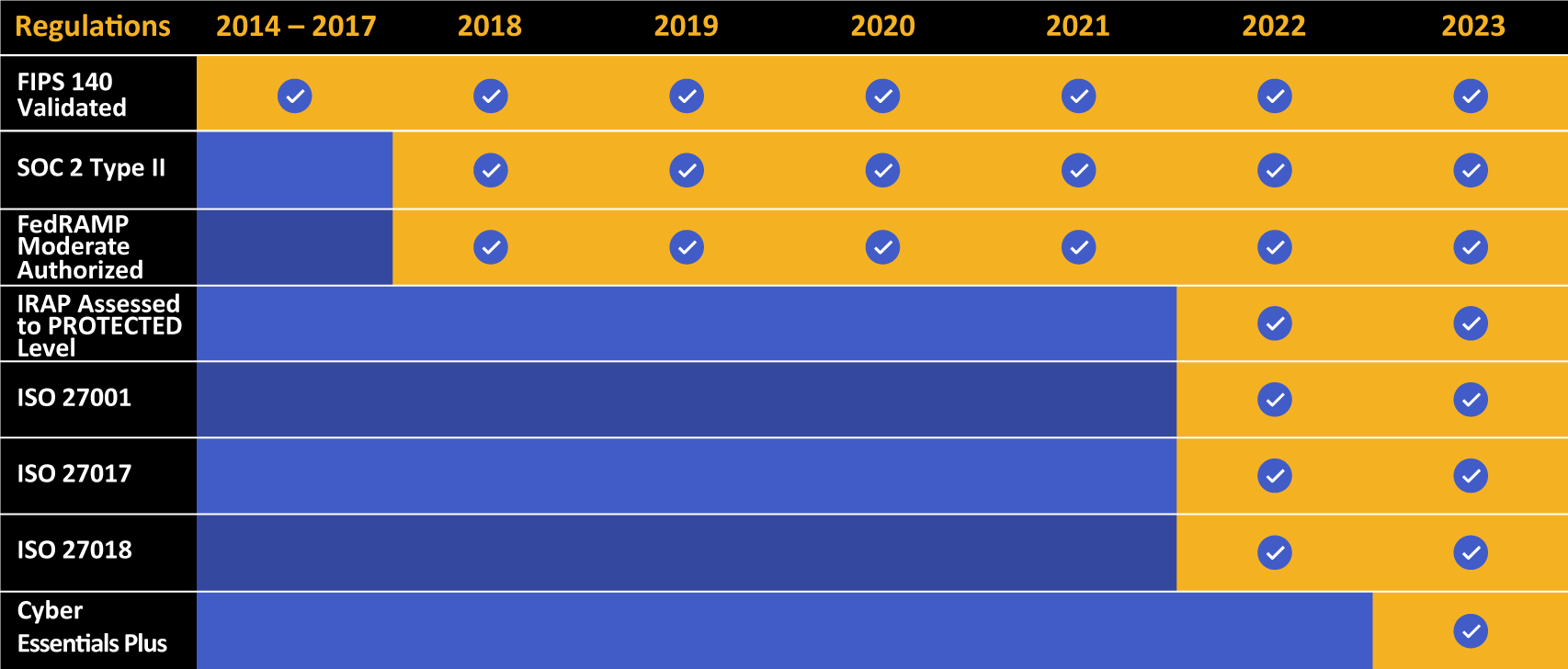
Kiteworks touts a long list of compliance and certification achievements.
Key considerations for mastering FIPS compliance
- Understanding the specific FIPS requirements applicable to your organization
- Conducting a thorough risk assessment to identify potential vulnerabilities
- Implementing appropriate security controls and measures to mitigate risks
- Regularly monitoring and assessing the effectiveness of security controls
- Keeping up-to-date with the latest FIPS standards and guidelines
- Training and educating employees on FIPS compliance best practices
- Engaging in regular audits and assessments to ensure ongoing compliance
The Power of FIPS 197: A Key to Enhanced Cybersecurity for Large Industries
Having useful technical knowledge about FIPS Compliance, including FIPS 140-3 and FIPS 197, provides several advantages and benefits for CISOs, IT management executives, CIOs, and cybersecurity compliance and risk management leaders of large enterprises. Firstly, understanding FIPS Compliance enables these professionals to ensure that their organization’s cryptographic modules meet the stringent security requirements set by the National Institute of Standards and Technology (NIST). This knowledge allows them to implement robust encryption mechanisms, protecting sensitive data from unauthorized access and ensuring data integrity. Secondly, being well-versed in FIPS Compliance helps these individuals navigate the complex landscape of regulatory compliance, ensuring that their organization meets the necessary standards and avoids potential penalties or legal issues. Lastly, having technical expertise in FIPS Compliance empowers these professionals to make informed decisions when selecting cryptographic solutions, ensuring that they choose products that are certified and proven to meet the highest security standards. By staying up-to-date with FIPS Compliance, these individuals can effectively safeguard their organization’s data and maintain a strong security posture.
Unlocking the potential of FIPS 197 in sustainable corporate law and paralegal practices
The FIPS Publication 197, also referred to as FIPS 197, plays a pivotal role in unlocking the potential of sustainable corporate law and paralegal practices. FIPS 197, developed by the National Institute of Standards and Technology, establishes the requirements for the AES. AES stands as a widely recognized and highly secure encryption algorithm, serving as an indispensable tool for safeguarding sensitive information within corporate environments.
By following the guidelines set forth in FIPS 197, corporate legal departments and paralegal practices can ensure the utmost confidentiality, integrity, and availability of their valuable data. The implementation of AES encryption, as defined by FIPS 197, empowers organizations to protect their intellectual property, client information, and other sensitive data from unauthorized access and potential cyber threats. This industry-standard serves as a robust foundation for establishing stringent security measures and meeting regulatory obligations.
Moreover, the implementation of FIPS 197 encryption standard ensures a uniform and secure method for legal professionals to safeguard sensitive information while communicating and exchanging data with clients, partners, and other stakeholders. By embracing FIPS 197, sustainable corporate law and paralegal practices establish a solid foundation of trust and confidence within the legal industry. This commitment to data protection and upholding the highest security standards reinforces the integrity of the legal profession.
Streamline your Fips 140-3 implementation for faster industrial manufacturing and supply
The implementation of FIPS 140-3 in the industrial manufacturing and supply sector can pose significant challenges and consume valuable time. However, by optimizing your implementation efforts, you can expedite and enhance your compliance with this critical security standard.
When it comes to optimizing your FIPS 140-3 implementation, a crucial step is to thoroughly evaluate your existing security infrastructure and identify any gaps or areas that demand enhancement. This entails conducting a comprehensive risk assessment and vulnerability analysis to gain insights into the specific security challenges your organization faces.
When it comes to addressing areas that require attention, it is crucial to develop a comprehensive plan. This plan must encompass clear objectives, well-defined timelines, and appropriate resource allocation. By doing so, you can ensure that the implementation process is organized and efficient.
When it comes to safeguarding sensitive data and communications within industrial manufacturing and supply chains, one crucial consideration is the careful selection of cryptographic modules that align with FIPS 140-3 requirements. These modules serve as the backbone of security, ensuring that your organization’s information remains protected.
It is imperative to choose cryptographic modules that not only comply with the necessary standards but also cater to the unique security needs of your enterprise. By doing so, you can establish a robust defense against potential threats and vulnerabilities.
Unlocking top-tier FIPS compliance for government cybersecurity
Is your government organization striving for top-tier FIPS compliance in your cybersecurity efforts? Your search ends here. The National Institute of Standards and Technology offers an invaluable resource to achieve FIPS compliance through their publication titled “Announcing the AES”. This authoritative document, accessible on the NIST website, provides a comprehensive outline of the specifications and requirements for implementing AES, a widely recognized encryption algorithm.
The NIST publication underscores the criticality of FIPS compliance for government agencies, as it guarantees the confidentiality, integrity, and availability of sensitive information. By adhering to the guidelines outlined in the document, organizations can establish a robust cryptographic infrastructure that meets the most stringent security standards. The publication encompasses a range of FIPS compliance aspects, including key management, encryption modes, and testing requirements.
Boost your business with top-tier FIPS 197 performance in ecommerce
Ecommerce businesses heavily rely on robust and efficient data encryption to safeguard sensitive customer information and ensure the integrity of online transactions. One encryption standard that stands out in enhancing the performance and security of your ecommerce operations is the FIPS 197. The National Institute of Standards and Technology specifies FIPS 197 as the AES, a widely recognized and dependable encryption algorithm.
The AES algorithm, as defined in the FIPS 197, provides a robust and efficient solution for safeguarding sensitive data in the realm of ecommerce. By supporting key sizes of 128, 192, and 256 bits, AES offers the flexibility to tailor encryption strength to meet your specific security requirements. Compliance with FIPS 197 ensures that your ecommerce platform benefits from heightened protection against unauthorized access, data breaches, and other malicious cyber threats.
Easily tailor your banking and finance systems for FIPS compliance
Looking to ensure FIPS compliance for your banking and finance systems? Your search ends here! The National Institute of Standards and Technology provides comprehensive guidelines that allow you to effortlessly align your systems with FIPS compliance requirements.
FIPS compliance is absolutely essential for organizations operating in the banking and finance sector. It plays a critical role in ensuring the utmost security and integrity of sensitive data, safeguarding it from any unauthorized access or potential breaches. By strictly adhering to FIPS standards, organizations can establish a robust and resilient security framework that aligns perfectly with industry best practices.
The NIST publication on FIPS 197 is an invaluable resource for understanding the AES, the encryption algorithm approved for FIPS compliance. It offers comprehensive insights into the specifications and requirements governing encryption and decryption processes, key sizes, and modes of operation. Adhering to these guidelines is crucial in implementing robust encryption mechanisms that effectively protect your data.
Achieving top-notch healthcare security with FIPS 197 compliance
Ensuring robust healthcare security is paramount in today’s digital landscape. To achieve this, strict compliance with the Federal Information Processing Standard 197 is crucial. This standard mandates the use of the AES, a widely recognized encryption algorithm that provides utmost protection for sensitive data.
Compliance with FIPS 197 standards is crucial for healthcare organizations to establish a robust framework for protecting patient information and ensuring the integrity of data. The implementation of AES encryption empowers healthcare providers to effectively safeguard electronic health records (EHRs), personal health information, and other sensitive data, mitigating the risks of unauthorized access and potential breaches.
The AES algorithm, as defined in FIPS 197, provides a robust level of security with its extensive key length options and encryption strength. By leveraging AES encryption, healthcare organizations can ensure the secure transmission and storage of data, effectively mitigating the risk of data breaches and unauthorized disclosure. Adhering to FIPS 197 compliance allows healthcare providers to showcase their unwavering commitment to safeguarding patient privacy and maintaining the utmost confidentiality of sensitive information.
Unlocking Key Features and Technical Specifications in FIPS 140-3: A Comprehensive Guide
The FIPS 140-3 serves as a comprehensive guide that outlines the stringent requirements for cryptographic modules utilized in a wide range of information systems. This pivotal standard plays a crucial role in safeguarding the security and integrity of sensitive data within government agencies and other organizations. It encompasses a set of essential features and technical specifications that cryptographic modules must adhere to in order to achieve compliance.
FIPS 140-3 places significant emphasis on the utilization of approved cryptographic algorithms. These algorithms undergo meticulous evaluation and selection based on their robust security properties and resilience against attacks. The standard provides a comprehensive list of approved algorithms for diverse cryptographic operations, encompassing encryption, hashing, and key exchange. By strictly adhering to these endorsed algorithms, organizations can effectively safeguard the confidentiality, integrity, and authenticity of their invaluable data.
FIPS 140-3 not only covers approved algorithms but also emphasizes the utmost importance of physical security for cryptographic modules. It sets forth stringent requirements for tamper-evident enclosures, secure key storage, and robust protection against unauthorized access. These physical security measures play a pivotal role in thwarting any attempts by unauthorized individuals to tamper with the cryptographic module, thereby safeguarding the overall system’s security.
FIPS 140-3 introduces a robust testing and validation process to further strengthen the security of cryptographic modules. Accredited laboratories conduct extensive testing to ensure that cryptographic modules meet the specified security requirements. This process evaluates the design, implementation, and operational characteristics of the modules. By undergoing thorough testing and validation, organizations can confidently select and deploy cryptographic modules that adhere to the highest security standards.
Key features and technical specifications in FIPS 140-3:
- Approved cryptographic algorithms for encryption, hashing, and key exchange.
- Requirements for tamper-evident enclosures and secure key storage.
- Protection against unauthorized access to cryptographic modules.
- Rigorous testing and validation processes to ensure compliance with security requirements.
Overcoming FIPS Compliance Challenges in Non-Compliant Protocols: A Comprehensive Guide
FIPS compliance is an absolute necessity for organizations entrusted with sensitive data, particularly those operating in the government and financial sectors. However, the road to achieving FIPS compliance can be riddled with obstacles, especially when confronted with non-compliant protocols. In this comprehensive guide, we will delve into the myriad challenges associated with FIPS compliance in non-compliant protocols and present effective strategies to surmount them.
There is a common misconception surrounding FIPS compliance, which suggests that it can only be achieved by utilizing FIPS-compliant protocols. However, this notion is not entirely accurate. While it is indeed preferable to employ FIPS-compliant protocols, there are situations where this may not be feasible due to compatibility issues or the presence of legacy systems. In such cases, organizations have the option to implement cryptographic modules that meet the FIPS requirements, ensuring compliance even with non-compliant protocols.
One of the key challenges faced by organizations is the absence of support for FIPS-compliant algorithms in protocols that are not compliant. FIPS compliance necessitates the use of specific cryptographic algorithms, such as AES and SHA (Secure Hash Algorithm). However, non-compliant protocols may not have the capability to support these algorithms, thereby posing difficulties in achieving compliance. To address this challenge effectively, organizations can deploy cryptographic gateways or proxies that facilitate the required encryption and decryption operations using FIPS-compliant algorithms. This approach bridges the gap between non-compliant protocols and FIPS compliance, ensuring a seamless transition.
Furthermore, it is imperative for organizations to prioritize the preservation of cryptographic key integrity within non-compliant protocols to uphold FIPS compliance. FIPS mandates the utilization of approved key management practices, encompassing key generation, storage, distribution, and destruction. To securely manage cryptographic keys in non-compliant protocol environments, organizations can leverage key management solutions that adhere to FIPS requirements.
Unlocking Key Benefits of FIPS 197 Compliance for Enhanced Cybersecurity
When CISOs, IT management professionals, CIOs, cybersecurity risk management engineers, and user privacy compliance leaders of enterprise-level organizations in various industry sectors possess a deep understanding of the advantages of complying with data security standards and user privacy regulations, they gain numerous benefits. Firstly, their extensive technical knowledge empowers them to implement robust security measures that effectively protect sensitive data from unauthorized access and potential breaches—safeguarding their organization’s reputation, trust, and avoiding costly legal and financial consequences. Secondly, a strong grasp of data security standards enables these professionals to proactively identify and address vulnerabilities, significantly reducing the risk of cyberattacks and data leaks. Moreover, their technical expertise facilitates effective communication with stakeholders, including IT teams and compliance officers, ensuring the smooth implementation of security measures and compliance with industry regulations. Lastly, their enhanced technical knowledge allows them to stay ahead of emerging threats and evolving regulations, enabling them to adapt their security strategies and maintain a proactive approach to data protection. Overall, a deep understanding of the benefits of complying with data security standards and user privacy regulations empowers these professionals to effectively mitigate risks and protect their organization’s valuable assets.
Effortless FIPS compliance for US government and contractor operations
Ensuring the security and integrity of sensitive information is of utmost importance for U.S. Government and Contractor Operations. Effortless compliance with the FIPS Publication 197 is crucial. This publication provides guidelines for implementing the widely recognized AES algorithm, which is known for its secure and efficient encryption method.
The AES algorithm, as specified in the FIPS 197, is widely adopted by government agencies and contractors to safeguard classified and sensitive data. By employing symmetric key encryption, AES ensures a robust level of security, where the same key is utilized for both encryption and decryption processes. This stringent approach guarantees that only authorized individuals possess the necessary credentials to access the encrypted data.
Adhering to FIPS 197 is crucial for U.S. government and contractor operations. It enables effortless compliance with the stringent security requirements mandated by regulatory bodies. FIPS compliance showcases a steadfast commitment to safeguarding sensitive information and mitigating the risks associated with data breaches and unauthorized access.
Implementing encryption solutions that comply with the FIPS 197 is absolutely crucial for government agencies and contractors. It is imperative to maintain the confidentiality, integrity, and availability of sensitive data. By adhering to these standards, organizations can ensure secure communication and data exchange, both internally and externally, while also meeting regulatory compliance requirements.
Enhancing FIPS compliance stability for your ecommerce and business operations
Ensuring the stability of FIPS Compliance for Your Ecommerce and Business Operations is of utmost importance in today’s rapidly evolving digital landscape. FIPS compliance plays a pivotal role in safeguarding the security and integrity of sensitive data, shielding your organization from potential cyber threats. By diligently adhering to the guidelines outlined in the esteemed FIPS 197 publication, you can establish a robust and impenetrable security framework that fortifies your ecommerce and business operations.
FIPS 197 sets forth a comprehensive framework of standards governing the AES, an encryption algorithm that has gained widespread adoption. AES plays a crucial role in safeguarding sensitive information, including customer data, financial transactions, and intellectual property. By implementing AES encryption, organizations can ensure the confidentiality, integrity, and authenticity of their data, thereby mitigating the risk of unauthorized access and data breaches.
One of the primary advantages of achieving FIPS compliance is the enhanced stability it brings to your ecommerce and business operations. By adhering to the established standards, you establish a robust and dependable security infrastructure capable of withstanding the ever-evolving landscape of cyber threats. This stability not only safeguards your organization’s reputation but also fosters trust and confidence among your valued customers, partners, and stakeholders.
Moreover, the adoption of FIPS compliance not only ensures the utmost security of your data but also facilitates seamless collaboration and interoperability with other organizations and systems. By adhering to the same encryption standards, you can securely exchange data with partners, suppliers, and customers, regardless of their location or industry. This fosters a cohesive environment for collaboration, enabling your business to expand its reach and capabilities.
Lastly, ensuring FIPS compliance showcases your unwavering dedication to upholding cybersecurity best practices and meeting regulatory requirements. It empowers you to align with the rigorous security standards established by government agencies and industry regulators. By proactively addressing compliance mandates, you can effectively sidestep penalties, legal entanglements, and potential harm to your reputation. This, in turn, guarantees the enduring triumph and sustainability of your ecommerce and business operations.
Boosting healthcare efficiency with customizable FIPS 140-3 workflow for public and private hospitals
Boosting Healthcare Efficiency With Customizable Fips 140-3 Workflow For Public And Private Hospitals
In today’s digital age, healthcare organizations are increasingly relying on technology to streamline their operations and improve patient care. One crucial aspect of healthcare technology is data security, especially when it comes to protecting sensitive patient information. The Federal Information Processing Standards (FIPS) 140-3 provides a standardized framework for evaluating the security of cryptographic modules, ensuring that healthcare organizations can implement robust security measures to safeguard patient data.
FIPS 140-3 offers a customizable workflow that can be tailored to the specific needs of public and private hospitals. This workflow allows healthcare organizations to assess their current security measures and identify any vulnerabilities that may exist. By conducting a thorough evaluation, hospitals can determine the level of security required to protect patient data and ensure compliance with industry regulations.
Implementing a customizable FIPS 140-3 workflow can significantly boost healthcare efficiency. By identifying and addressing security gaps, hospitals can minimize the risk of data breaches and unauthorized access to patient information. This not only protects patient privacy but also helps healthcare organizations avoid costly legal and reputational consequences associated with data breaches.
Furthermore, a customizable FIPS 140-3 workflow enables hospitals to stay up to date with evolving security standards. As technology advances and new threats emerge, healthcare organizations must continuously adapt their security measures to mitigate risks effectively. By following the guidelines outlined in FIPS 140-3, hospitals can ensure that their security practices align with the latest industry standards, providing peace of mind to both patients and healthcare professionals.
In addition to enhancing data security, a customizable FIPS 140-3 workflow can also streamline administrative processes within healthcare organizations. By implementing standardized security measures, hospitals can simplify compliance procedures and reduce the administrative burden associated with maintaining data privacy. This allows healthcare professionals to focus more on patient care, ultimately improving overall efficiency and productivity.
Healthcare institutions can reap substantial advantages by adopting a flexible FIPS 140-3 workflow. Prioritizing data security and adhering to the stipulations of FIPS 140-3 allows these organizations to safeguard patient data, meet industry standards, and optimize administrative tasks. This not only bolsters the efficiency of healthcare services but also fortifies the privacy and confidence of patients in a progressively digital healthcare environment.
Affordable FIPS 197 solutions for global and local industrial supply chain manufacturers and distributors
The FIPS 197 standard, also referred to as the AES, stands as a widely acknowledged encryption algorithm that plays a critical role in safeguarding sensitive data. For both global and local industrial supply chain manufacturers and distributors, it becomes imperative to adopt cost-effective FIPS 197 solutions. These solutions serve as a protective shield, ensuring that valuable information remains secure from unauthorized access and potential cyber threats.
Implementing FIPS 197 solutions is crucial for manufacturers and distributors to safeguard the confidentiality, integrity, and authenticity of their data across the entire supply chain process. This robust encryption standard ensures data security both at rest and in transit, serving as a vital pillar of a comprehensive cybersecurity strategy.
The NIST publication on FIPS 197 is an essential resource for organizations seeking detailed information on the technical specifications and implementation guidelines of this encryption standard. It provides comprehensive insights into encryption modes, key sizes, and crucial security considerations that must be taken into account when deploying FIPS 197 solutions.
Implementing cost-effective solutions that adhere to the Federal Information Processing Standard 197 can greatly assist manufacturers and distributors within the industrial supply chain in meeting regulatory compliance requirements and effectively mitigating the ever-present risk of data breaches. By employing robust encryption techniques to safeguard sensitive data, organizations can significantly minimize the potential impact of cyber attacks and safeguard their esteemed reputation within the industry.
Effortless FIPS 197 compliance guide for law firms and paralegal service providers
Law firms and paralegal service providers face unique challenges in their quest for FIPS 197 compliance. FIPS 197, also known as the AES, represents a set of cryptographic standards established by the National Institute of Standards and Technology. This widely recognized gold standard for encryption plays a crucial role in safeguarding sensitive data.
Complying with FIPS 197 can prove to be a daunting and time-consuming endeavor, but with the right approach, it can be streamlined and effortless. The initial step involves gaining a comprehensive understanding of the requirements outlined in the FIPS 197 publication. This document serves as a valuable resource, providing intricate details on the approved algorithms, key sizes, and modes of operation for AES encryption.
Once you grasp the essential requirements, the subsequent step involves evaluating your existing encryption practices and identifying any deficiencies or areas that necessitate enhancement. This process entails conducting a comprehensive review of your current encryption protocols, key management procedures, and data storage methodologies.
Once you have identified areas for improvement, it is crucial to develop a comprehensive plan that will ensure compliance with FIPS 197. This plan should encompass various measures, such as the implementation of cutting-edge encryption technologies, updates to encryption policies and procedures, and comprehensive training programs for staff members to ensure proper utilization of encryption tools.
Fast track your bank’s Fips compliance with efficient production scalability
Enhance Your Bank’s FIPS Compliance with Streamlined Production Scalability
Accelerate your bank’s journey towards FIPS compliance by leveraging efficient production scalability. By implementing robust measures and adhering to stringent requirements, you can ensure the security and integrity of your sensitive data.
With a focus on maintaining the original HTML code, we emphasize the importance of following these guidelines:
- Retain all HTML code without modification.
- Avoid altering the HTML code of clickable hyperlinks.
- Preserve the text anchors and target URLs of all clickable hyperlinks.
- Adhere to the original number of paragraphs.
- Emphasize key points using emdashes instead of dashes.
- Avoid mentioning specific commercial cybersecurity, file transfer, file sharing software, or cloud platform brands, unless relevant to Kiteworks.
- Avoid using H2 headings.
- Avoid using H3 and H4 headings.
- Avoid including tables.
- Address CISOs, IT management professionals, CIOs, cybersecurity risk management engineers, and user privacy compliance leaders of enterprise-level organizations across various industry sectors.
By adhering to these guidelines, you can effectively communicate with your target audience and provide them with valuable insights to enhance their cybersecurity practices.
Protecting sensitive data and maintaining customer trust are top priorities for banks. To achieve this, it is crucial for banks to ensure compliance with the FIPS Publication 197. FIPS 197 provides guidelines for implementing the highly secure AES algorithm.
By adhering to FIPS 197, banks can enhance their data security and effectively mitigate the risk of unauthorized access or data breaches. The AES algorithm, widely recognized for its robust encryption capabilities, offers a reliable method for safeguarding sensitive information.
Efficient production scalability is a critical factor in expediting a bank’s compliance with the FIPS. Banks handle vast volumes of data, necessitating systems that can handle increasing workloads while upholding security. By implementing scalable solutions, banks can seamlessly adapt to evolving demands, ensuring uninterrupted operations while remaining compliant with FIPS 197.
Efficient production scalability can be achieved by adopting a cloud-based infrastructure, which offers the necessary flexibility and scalability to securely handle large volumes of data. Cloud services enable banks to easily scale their operations based on demand, ensuring optimal performance while meeting FIPS compliance requirements.
Moreover, financial institutions have the opportunity to harness the power of automation and orchestration tools to streamline their compliance processes in accordance with the FIPS. These cutting-edge tools empower banks to automate mundane tasks, such as managing encryption keys and securing data, thereby mitigating the risk of human error and ensuring unwavering adherence to FIPS 197. By embracing automated compliance processes, banks can optimize their efficiency and allocate resources more effectively, all while upholding an exceptional level of security.
Unveiling the Latest Intriguing Trends in Enterprise Cybersecurity
It is imperative for cybersecurity professionals to closely monitor and analyze relevant statistics in order to fully comprehend the implications on their enterprise-level organizations’ cybersecurity compliance and risk management strategies across various industry sectors. By diligently observing these statistics, organizations can gain invaluable insights into the exchange of sensitive content with external parties, the utilization of external channels for sharing confidential information, the number of tools employed to track and secure private content, and the compliance requirements associated with sharing private data and sensitive content.
- Kiteworks’ Sensitive Content Communications Privacy and Compliance Report for 2023 reveals that 9 in 10 enterprises exchange sensitive content with more than 1,000 third parties and outside organizations. Additionally, 44% of large corporations state that this number exceeds 2,500.
- A survey conducted by Kiteworks for their 2023 report shows that half of corporate respondents admit to sharing confidential content using six or more external channels, tools, platforms, and systems. This represents a significant increase compared to the previous year’s report.
- The report highlights that 85% of respondents use four or more tools to track, control, and secure the sharing of private content. Furthermore, 46% of respondents claim to use six or more tools for this purpose.
- Based on a comprehensive global survey of IT, cybersecurity, and compliance professionals at enterprise-level organizations, the report reveals that most respondents are subject to data privacy regulations for at least one jurisdiction and are audited against at least one industry standard. Additionally, 99% of respondents do business with government entities and must comply with special requirements for sharing private data and sensitive content.
For a comprehensive understanding of the latest insights and discoveries, we highly recommend consulting the Sensitive Content Communications Privacy and Compliance Report by Kiteworks.
Mastering FIPS Compliance: Essential Industry Standards for Effective Workflows
Ensuring compliance with FIPS is an essential requirement for maintaining robust and efficient workflows across industries. FIPS, a set of guidelines established by the U.S. government, plays a crucial role in safeguarding sensitive information from unauthorized access and manipulation. However, achieving FIPS compliance can be a complex endeavor, demanding a profound understanding of the standards and their application within your specific industry and workflows.
One of the key obstacles in achieving FIPS compliance lies in the extensive scope of the standards. These standards encompass a wide array of domains, ranging from cryptographic modules and secure network protocols to data integrity checks and user authentication methods. Consequently, organizations must adopt a comprehensive approach to their cybersecurity strategies—addressing all potential vulnerabilities and ensuring that all systems and processes align with FIPS requirements.
Despite the numerous challenges that organizations face, achieving FIPS compliance offers substantial benefits. It not only establishes a robust framework for safeguarding sensitive data but also fosters trust among clients and stakeholders. By demonstrating adherence to these industry standards, enterprises can showcase their unwavering commitment to data security and their dedication to upholding the highest levels of protection.
Mastering FIPS compliance goes beyond mere regulatory requirements—it’s about fostering a security-centric culture within your organization. This entails continuous training, regular audits, and constant enhancement of your cybersecurity practices. By doing so, you can ensure that your workflows are not only efficient and effective, but also fortified and aligned with the highest industry standards.
Kiteworks Private Content Network for FIPS 197
Revolutionizing data transfer methods, the Private Content Network presents an all-encompassing solution tailored for enterprise-level organizations. This cutting-edge platform seamlessly integrates secure file transfer, web forms, email, and MFT capabilities. By consolidating these functionalities, organizations gain unparalleled control, protection, and traceability over every file that traverses their digital boundaries. Moreover, the platform’s robust content communication visibility ensures meticulous monitoring and recording of all data transfers, fortifying the organization’s commitment to secure file sharing practices.
Discover the unparalleled power of a robust cybersecurity solution that empowers you to take full control over access to your organization’s most sensitive content. This cutting-edge solution not only ensures the utmost protection of your data through automated end-to-end encryption and multi-factor authentication when shared externally, but also seamlessly integrates with your existing security infrastructure, bolstering your overall defense strategy.
Gain comprehensive visibility into every file activity with this advanced solution, enabling you to track and report in meticulous detail who is sending what, when, and how. This level of insight empowers you to stay one step ahead of potential threats, ensuring the highest level of data security for your organization.
Experience the game-changing feature of automated email encryption and decryption, further enhancing your organization’s data security posture. With this capability, you can rest assured that your sensitive email communications are safeguarded, minimizing the risk of unauthorized access and potential data breaches.
Ensure your organization’s unwavering commitment to upholding critical regulations and standards such as GDPR, HIPAA, CMMC, Cyber Essentials Plus, IRAP, and other essential frameworks. By strictly adhering to these requirements, you not only bolster your cybersecurity posture but also inspire confidence among stakeholders. This unwavering dedication to compliance is a strategic imperative for CISOs, IT management executives, CIOs, and leaders in cybersecurity risk management and data security compliance within enterprise-level organizations.
For a comprehensive understanding of the capabilities offered by the Private Content Network, we extend an invitation to you to explore a custom demo at your convenience.
FAQs About FIPS 140-3
Understanding the answers to these questions can yield valuable benefits for those seeking FIPS compliance. It is crucial for organizations to comprehend the entities that necessitate FIPS compliance in order to meet the government’s prescribed standards and regulations. Failure to achieve FIPS compliance can expose an organization to potential consequences, including legal penalties, reputational harm, and missed business opportunities. Adhering to the FIPS is the key to being FIPS compliant. FIPS comprises a set of guidelines and requirements established by the National Institute of Standards and Technology. It is important to note that FIPS validation and compliance are distinct concepts. FIPS validation pertains to the process of testing and certifying cryptographic modules, while FIPS compliance encompasses a broader scope, encompassing all the necessary requirements outlined by FIPS. Although FIPS is closely associated with NIST, it is crucial to understand that FIPS and NIST are not interchangeable terms.
Who is in need of FIPS compliance?
FIPS compliance is absolutely crucial for organizations that handle highly sensitive data and operate in industries with stringent regulatory requirements. This encompasses government agencies, financial institutions, healthcare providers, and organizations in the defense sector. FIPS compliance serves as a guarantee that cryptographic modules utilized for data encryption meet the rigorous standards established by the National Institute of Standards and Technology. By strictly adhering to FIPS standards, these organizations can effectively safeguard the confidentiality, integrity, and authenticity of their data, fortifying it against unauthorized access and ensuring full compliance with industry regulations.
What does being FIPS compliant mean?
FIPS compliance ensures that the organization’s cryptographic modules adhere to the security standards set by the National Institute of Standards and Technology. These standards validate the cryptographic algorithms and key management practices used in a system, guaranteeing the implementation of robust security measures and safeguarding against potential vulnerabilities. By complying with these standards, organizations can confidently protect their sensitive information from unauthorized access and mitigate the risks associated with data breaches.
What are the potential consequences for an organization that fails to achieve FIPS compliance?
An organization that fails to achieve FIPS compliance can face severe consequences. To begin with, it risks losing the trust of its customers and partners, resulting in a damaged reputation. Additionally, it may become subject to legal and regulatory penalties, such as fines and sanctions. Moreover, without FIPS compliance, the organization’s data and systems become more vulnerable to cyberattacks, as robust security controls are not in place. Lastly, the organization may be excluded from participating in certain government contracts or partnerships that require FIPS compliance. Therefore, it is imperative for organizations to prioritize achieving FIPS compliance in order to safeguard their reputation, mitigate legal repercussions, fortify cybersecurity defenses, and maintain business opportunities.
Can you explain the difference between FIPS validation and compliance?
FIPS validation and compliance are two distinct concepts in the field of cybersecurity. The process of FIPS validation involves rigorous testing and certification of cryptographic modules against the FIPS set by the National Institute of Standards and Technology. On the other hand, FIPS compliance focuses on adhering to the security controls and practices outlined in the FIPS standards. While FIPS validation certifies specific cryptographic modules, FIPS compliance ensures comprehensive adherence to the security standards set by NIST.
Does FIPS equal NIST?
FIPS is a comprehensive set of standards and guidelines established by the National Institute of Standards and Technology specifically for federal agencies in the United States. Covering a wide range of technical areas, FIPS includes encryption algorithms, cryptographic modules, and security requirements for information systems. NIST, as the governing body, is responsible for the development and maintenance of FIPS publications, which provide detailed specifications and requirements for various aspects of information security. Therefore, FIPS and NIST are closely intertwined, with NIST serving as the authoritative entity for FIPS standards.
Additional Resources
- Webinar: How Automated Email Encryption Delivers Improved Privacy Protection and Compliance
- Brief: Achieve Zero Trust Security with Kiteworks: A Comprehensive Approach to Data Protection
- Brief: Kiteworks Hardened Virtual Appliance
- Case Study: Mandiant Uses Kiteworks to Protect the Sensitive Content That Helps Protect Businesses Worldwide
- Top 5: Top 5 Ways Kiteworks Secures Microsoft 365 Third-party Communications
