Framework Implementation for NIST CSF 2.0 Compliance
The NIST CSF 2.0 is mandatory for federal agencies in the United States and relevant to a wide range of industries, including healthcare, finance, energy, and telecommunications. These sectors often handle sensitive data and are subject to strict regulations, making compliance with the framework essential. Following are some of the biggest challenges faced by organizations when it comes to NIST CSF 2.0 compliance.
Govern
Compliance with the Govern function requires understanding the organization’s context, defining risk tolerance, establishing clear roles and responsibilities, and enforcing policies consistently. Challenges often stem from the complexity of aligning cybersecurity goals with business objectives, managing supply chain risks, and ensuring oversight across the organization. Effective controls must be implemented to foster accountability, assess performance, and drive continuous improvement in cybersecurity risk management.
Identify
Compliance with the Identify function requires maintaining accurate inventories of hardware, software, services, and data flows, prioritizing assets based on criticality, and managing them throughout their life cycles. Identifying and validating vulnerabilities, gathering threat intelligence, and managing changes and exceptions prove challenging within this function. Controls need to be put in place to understand the organization’s current cybersecurity risks and drive continuous improvement across all CSF functions.
Protect
The Protect function requires managing access to assets, providing cybersecurity awareness and training, and achieving technology infrastructure resilience. Organizations must manage identities, credentials, and access permissions; protect data at rest, in transit, maintain secure software development practices, and ensure adequate resource capacity for availability. Protecting the confidentiality, integrity, and availability of assets and information is vital.
Detect
Continuous monitoring to find anomalies and indicators of compromise, as well as analyzing potential cybersecurity incidents, is needed to comply with the Detect function. Responsibilities include: monitoring networks, physical environments, personnel activity, and technology usage. Challenges include correlating information from multiple sources, understanding the impact and scope of adverse events, and integrating cyber threat intelligence into the analysis.
Respond
Compliance with the Respond function requires managing incident response, conducting investigations to support forensics and recovery, coordinating response activities, and mitigating incidents. Categorizing and prioritizing incidents, executing incident response plans, performing root cause analysis, containing and eradicating incidents, and notifying stakeholders, use valuable resources. Effective controls must be implemented to ensure a swift and coordinated response to cybersecurity incidents.

Recover
The Recover function requires executing incident response plans, verifying the integrity of backups and restored assets, and coordinating restoration activities with internal and external parties. Organizations need to verify backup integrity, restoring systems and services, confirming normal operating status, completing incident-related documentation, and communicating recovery progress and public updates using approved methods and messaging.
Kiteworks Enhances Data Protection and Risk Management in Compliance With NIST CSF 2.0
Support for the Govern Function Across the 5 Core Functions
Kiteworks supports the NIST CSF 2.0 Govern function through granular user settings, external repository integration, and role-based access controls. The platform provides comprehensive capabilities including asset management, authentication, encryption, data loss prevention, SIEM integration, automated notifications, and disaster recovery configurations—helping organizations establish, communicate, and enforce their cybersecurity risk management strategy effectively.
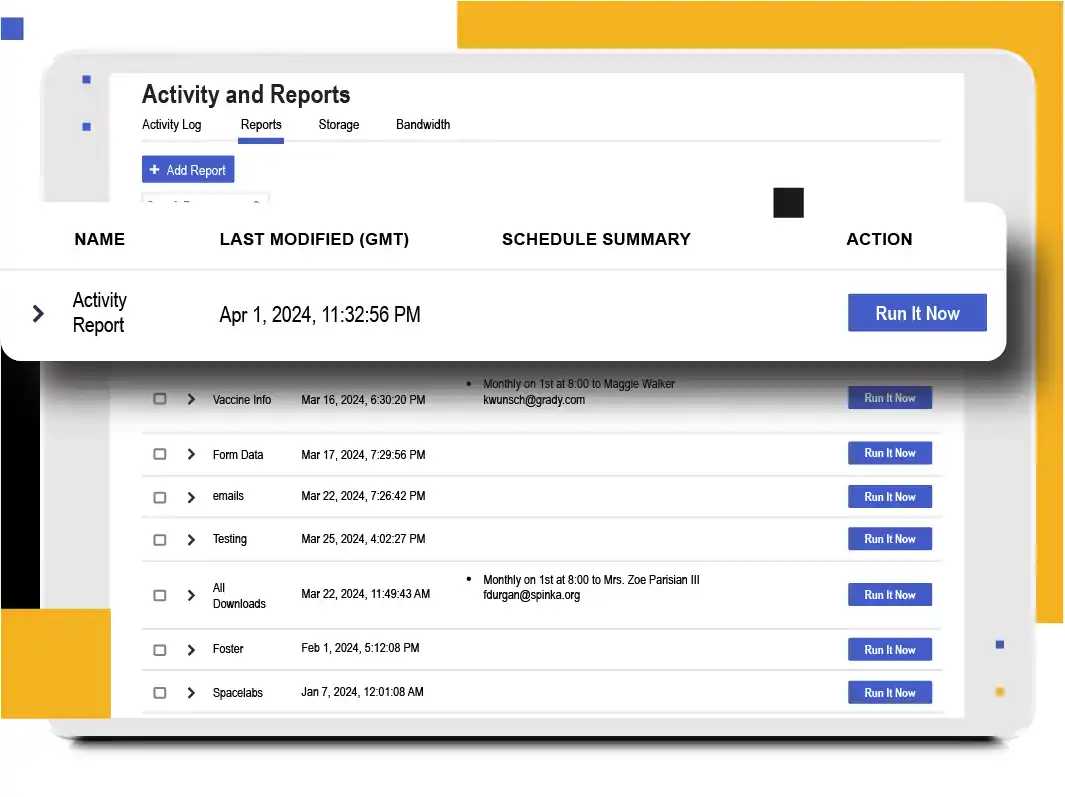
Identify Unstructured Data and Potential Vulnerabilities
Kiteworks maintains accurate inventories of hardware, software, services, and data flows through HSM integrations. It classifies and prioritizes data assets, identifies vulnerabilities through automated and manual penetration testing, and detects suspicious activities using pattern-based detection. The platform’s consolidated activity log and SIEM integration enable continuous risk assessment and improvement.
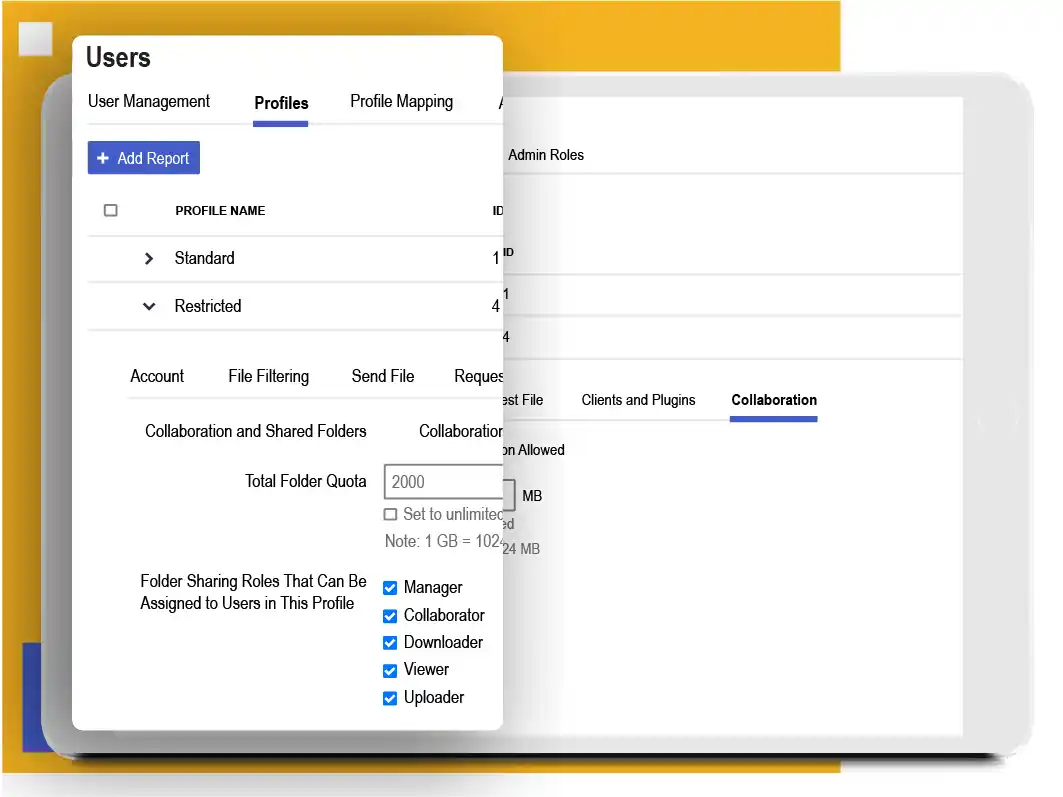
Robust Identity Management Protects Access
Kiteworks provides robust identity management with granular role-based access controls, multi-factor authentication, and identity provider integration. It employs multilayered encryption for data at rest and in transit, offers secure collaboration through SafeEDIT, and prevents unauthorized software execution. The platform’s clustering mechanism and virtual appliance architecture ensure high availability and resilience.
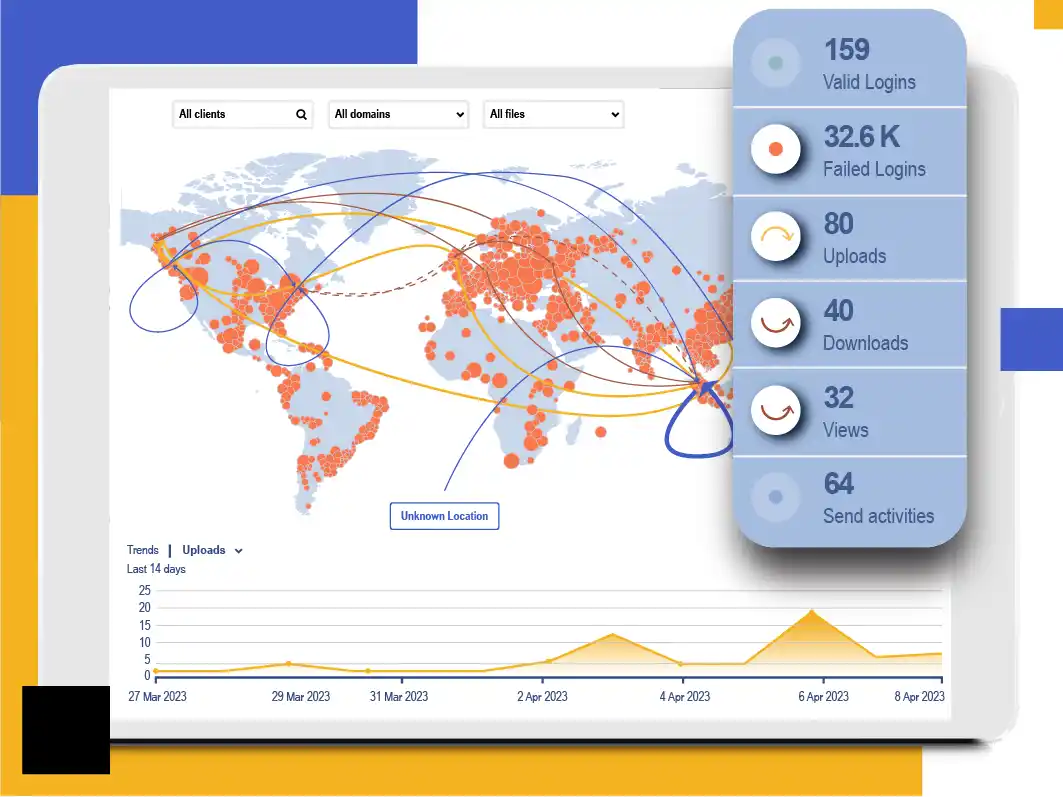
Detect All Activity With Immutable Audit Logs
Kiteworks conducts ongoing penetration testing and employs proprietary patterns to detect suspicious activities. It automatically cleans, normalizes, and aggregates log data into a standardized stream for SIEM integration and real-time analysis. The CISO Dashboard provides authorized staff with audit logs and visual activity representations for incident identification.
Respond to Threats With Incident Management Capabilities
Kiteworks captures all log messages without throttling, providing a consolidated activity log for incident triage, validation, and root cause analysis. It integrates with external monitoring tools for real-time detection and stakeholder notification. Granular access controls enable secure information sharing, while sandboxing contains incidents and continuous testing helps eradicate them.


Quickly Recover and Ensure Business Continuity
Kiteworks provides snapshot and replication capabilities for disaster recovery. The platform enables VM snapshots capturing entire system states for verified restoration. Automatic replication between storage nodes ensures data integrity and seamless failover. Real-time consolidated logging and SIEM integration support established incident management processes and stakeholder communication throughout recovery.
Frequently Asked Questions
Kiteworks supports the NIST CSF governance requirements through granular user profile settings, integration with external repositories, and collaboration roles that respect access controls. The platform also helps organizations establish and enforce cybersecurity risk management strategies by providing asset management, authentication, access controls, data loss prevention (DLP), encryption, audit logs, SIEM integration, automated notifications, and disaster recovery configurations across all framework functions.
Kiteworks maintains accurate inventories of hardware, software, services, and data flows through HSM integrations. It classifies data assets based on various conditions and identifies vulnerabilities through automated and manual penetration testing, threat intelligence sharing, and pattern-based detection of suspicious activities. The platform’s consolidated activity log and SIEM integration facilitate continuous risk assessment and improvement.
Kiteworks provides robust identity management with granular role-based access controls, multi-factor authentication, and identity provider integration. It employs multilayered encryption for data at rest and in transit , offers secure collaboration through SafeEDIT, maintains a secure SDLC process, and prevents unauthorized software execution. The platform’s clustering mechanism and virtual appliance architecture ensure high availability and resilience.
Yes, Kiteworks conducts ongoing penetration testing and employs proprietary patterns to detect suspicious activities. It maintains detailed logs that are automatically cleaned, normalized, and aggregated into a standardized stream for SIEM integration. The CISO Dashboard provides authorized staff with audit logs and visual activity representations, enabling real-time incident identification and analysis.
Kiteworks captures all log messages without throttling, providing a consolidated activity log for incident triage and root cause analysis. It integrates with external monitoring tools for real-time detection and stakeholder notification. For recovery, the platform offers snapshot and replication capabilities, automatic failover, SIEM integration for incident management, and tools for communicating recovery progress to stakeholders.
FEATURED RESOURCES

Discover How Kiteworks Supports NIST 800-171 Compliance

Meeting the FedRAMP Equivalency Requirement of CMMC

Guide: CMMC 2.0 Compliance Mapping for Sensitive Content Communications

Kiteworks Secure Managed File Transfer—When You Absolutely, Positively Need the Most Modern and Secure MFT Solution

