
Eleven Requirements for Secure Managed File Transfer
Today’s modern enterprise requires a secure managed file transfer solution. Managed file transfer (MFT) solutions have surprisingly demonstrated great staying power within the enterprise, despite the emergence and commoditization of many other file transfer mechanisms like email and SFTP. Few businesses however have revisited their MFT investment since they purchased another legacy file transfer solution: the fax machine. The only managed file transfer solution worth having is a secure managed file transfer solution.
Secure Managed File Transfer: An Evolution
As long as efficiency remains a top business priority, managed file transfer solutions will continue to earn their keep, whether the workflow is person to person, person to server, server to person, or server to server. Your managed file transfer solution at a bare minimum should:
- Automate and secure the file transfer process
- Be built on the FTP network protocol
- Support multiple file transfer protocols like FTP, SFTP, OFTP, SCP, HTTP, and HTTPS
- Provide real-time reporting and operational visibility over file transfers in transit
- Detect and resolve failed file transfers
- Offer security and encryption to protect data in transit
- Provide auditing and logging for internal and regulatory compliance
- Integrate with your existing security infrastructure
Most managed file transfer solution providers offer these table stakes and, in normal conditions, compete on price to win business. Normal conditions however ceased in mid-March. The global pandemic created a public health crisis as well as a cybersecurity crisis. Since employees began working from home, the security perimeter has stretched and the attack surface has expanded. Remote work security erodes as hackers exploit unsuspecting employees and unsecure home networks to access product designs, financial budgets, personnel records and other confidential information.

Security and governance have therefore become increasingly important capabilities for an MFT solution. Unfortunately, managed file transfer solutions can’t keep up with the rapid changes in the threat landscape or regulatory compliance environment. In fact, several compliance regulations have emerged since the original managed file transfer solution vendors architected their solutions, including GDPR, PCI DSS, HIPAA, SOC2, NIST 800-53, and many more.
Secure Managed File Transfer: A Checklist
While traditional MFT offers better security than SFTP, it leaves databases and repositories exposed on your servers, and leaves governance up to your workflow developers. Ultimately, your business risks a data breach or compliance violation during every file transfer unless your current managed file transfer solution can govern who accesses confidential information, secure that data in transit, and trace and log the transfer activity.
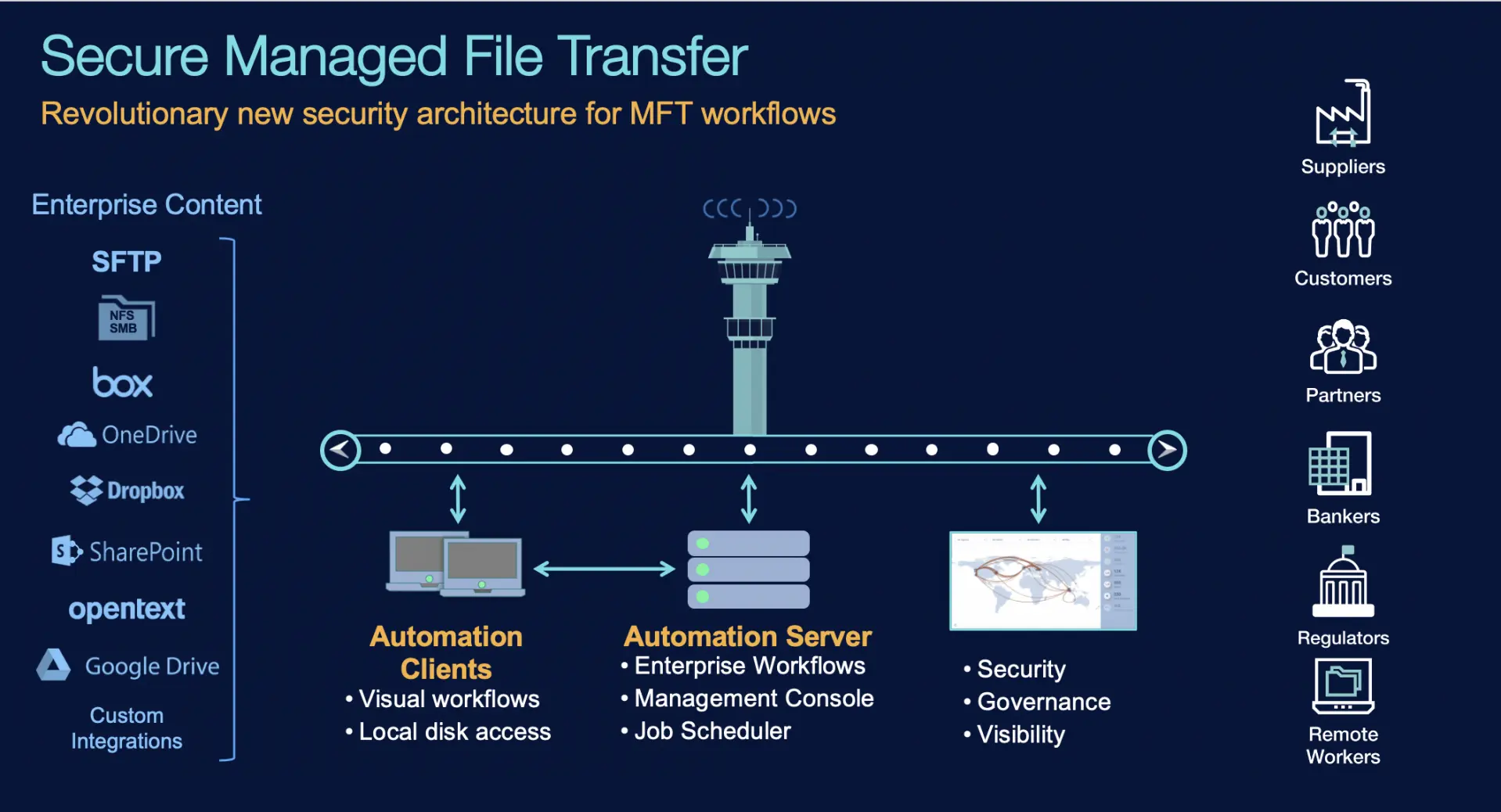 Enterprise content shared externally should funnel through a gauntlet of security and governance checks, driven by your policies. Most important, you must be able to see your critical data assets in transit, their sensitivity class, who is accessing those assets, and in what domains and locations, all to enable security alerts and forensic analysis.
Enterprise content shared externally should funnel through a gauntlet of security and governance checks, driven by your policies. Most important, you must be able to see your critical data assets in transit, their sensitivity class, who is accessing those assets, and in what domains and locations, all to enable security alerts and forensic analysis.
Next-generation MFT requires an architecture that builds security in from the ground up. Consider the following eleven capabilities, split into three distinct categories, a checklist for a modern, secure managed file transfer solution.
Secure Managed File Security
- Hardened virtual appliance – shrink the threat surface with a hardened virtual appliance server that includes the OS, databases, file systems, Web servers, application servers, etc.
- Least privilege – apply a default zero-trust or least privilege principle to all folder access and data transfers. Require specific permission to gain access between services internal to the appliance, access between cluster nodes, as well as external file transfers. All access is subject to expiration policies.
- FedRAMP authorized and FIPS validated – a best practice if not a requirement for working with government agencies; FedRAMP authorization and FIPS compliance demonstrate to the US Department of Defense you consider security a top priority when sharing confidential data.
- Integrated AV and ATP with quarantine – automatically quarantine detected files, provide alerts, and enable the security staff to unlock files in the case of false positives.
- Integrated HSM – ensure that any file decryption requires access to keys stored in a hardened security module, protected with layers of derivations, transformations, and obfuscation.
- Secure enterprise storage access – secure content access to cloud and on-premises content management systems, file shares, and other repositories to prevent accidental leaks and intentional breaches.
Secure Managed File Governance
- Flow authoring access controls – don’t leave governance of MFT workflows like sources, destinations, sensitive data classes, even ciphers to developers. With unified visibility, you can centralize governance of these workflows and exert the same level of control you have over secure email and secure file sharing.
- Granular folder access control roles – go beyond the root directory level in the file-first model by allowing access permissions to be assigned to a nested folder. With a security-first architecture, a granular data access model is independent of the underlying operating system.
- Role-based user policies – go beyond traditional data access controls to control who is allowed to share data, who is allowed to author transfer workflows, who can run them, what domains the data can be sent to, etc.
- Consolidated and standardized logs – aggregate logs from MFT and all other communication channels like secure email, security file sharing, SFTP, and content access connectors. When syntax and semantics are normalized in a single, clean log, SIEM analysts can focus on finding cross-channel patterns that indicate threats or attacks.
Secure Managed File Visibility
- Security visualizations, analytics, notifications – a CISO Dashboard that sees, follows, and records all data movement through all third-party communication channels to detecting anomalies, send alerts, and enable analysis at detailed levels.
If your managed file transfer solution doesn’t have these security, governance, and visibility capabilities, it’s time for an upgrade. Only a secure managed file transfer solution lets you accelerate your business and protect your organization.
To learn more about Kiteworks’ Secure Managed File Transfer solution, schedule a custom demo of Kiteworks today.
Additional Resources
- Blog Post Managed File Transfer Software Vendors
- Blog Post Is SFTP Encrypted?
- Blog Post Most Secure File Sharing Options for Enterprise & Compliance
- Blog Post Enterprise Secure File Sharing
- Blog Post Secure File Transfer Protocol