Security for Data You Share, Send and Use
Deploy a Kiteworks Private Data Network (PDN) to control, monitor, and protect all data exchanged between people, machines, and systems across user collaboration, automated workflows, and enterprise AI—all from one platform. With FedRAMP High Ready authorization and supporting nearly 90% of CMMC 2.0 compliance, Kiteworks meets the most stringent security and regulatory requirements for government and enterprise environments.
Private Data Network

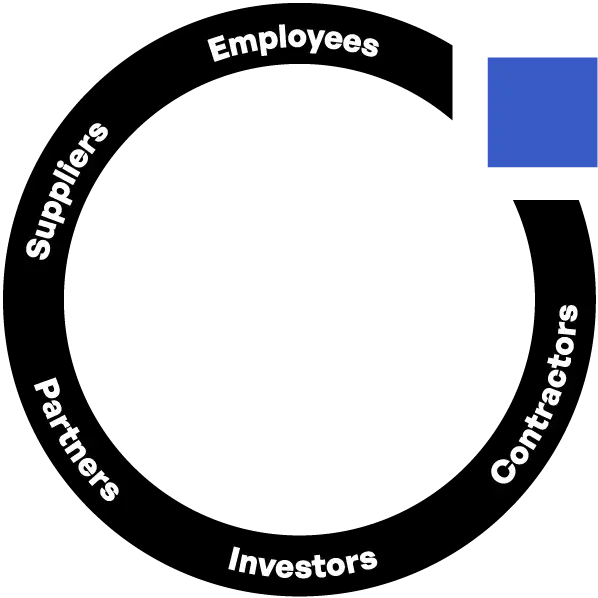
Streamlined Network of Users
Employees, Suppliers, Partners, Investors, and Contractors
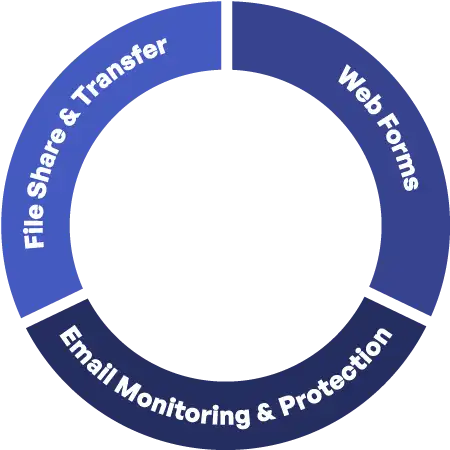
Inbound and Outbound Control Coverage
File Share & Transfer, Email Monitoring & Protection, Web Forms
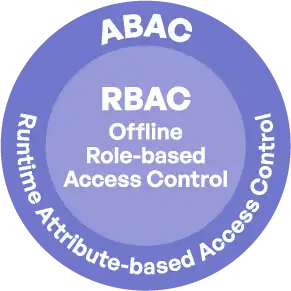
Advanced Policy Engine
Runtime Attribute-based Access Control (ABAC) and Offline Role-based Access Control (RABC)
Add-on Suites
A Kiteworks Private Data Network empowers organizations to effectively manage risk in every send, share, receive, and use of sensitive data.
Thousands of private and public sector organizations use Kiteworks to ensure compliance and manage their risk.



















What Our Customers Say
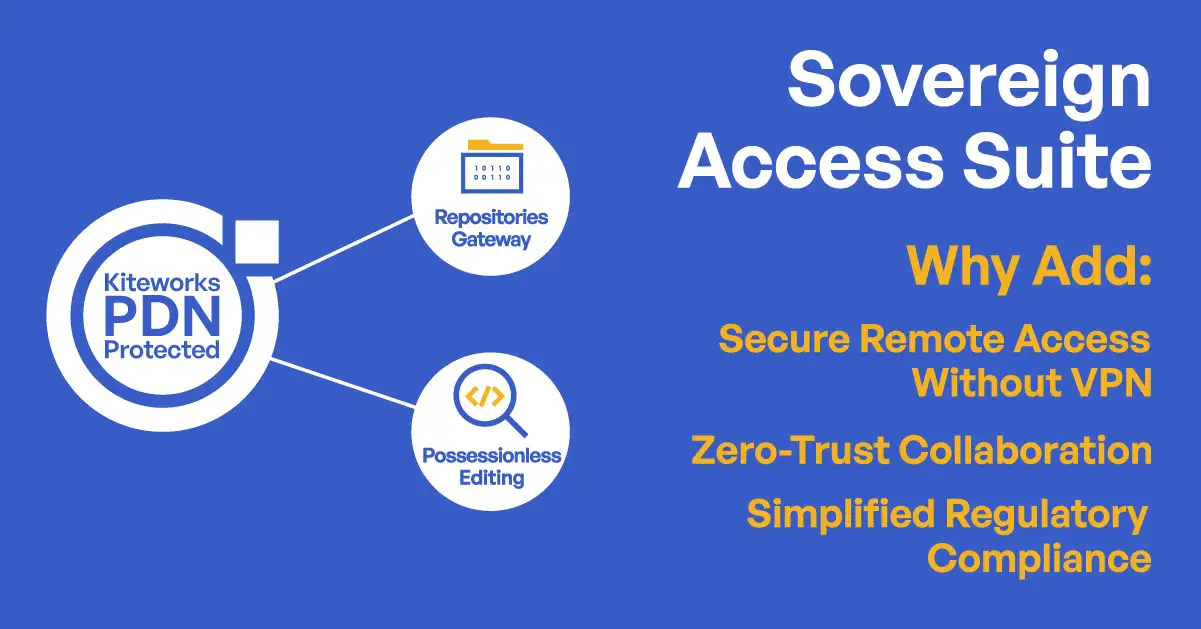
Zero-Trust Data Exchange
The Kiteworks platform unifies, tracks, controls, and secures sensitive data exchanges.
Secure Email
Keep email communications containing PII, PHI, IP, and other sensitive information from falling into the wrong hands. Kiteworks secure email offers you multiple options to fit your business needs, including the Email Protection Gateway that automates email protection and makes end-to-end encryption invisible to email senders and recipients.
Secure Email
Keep email communications containing PII, PHI, IP, and other sensitive information from falling into the wrong hands. Kiteworks secure email offers you multiple options to fit your business needs, including the Email Protection Gateway that automates email protection and makes end-to-end encryption invisible to email senders and recipients.
Secure File Sharing
Set, enforce, monitor, and record who accesses, uploads, views, and downloads files, with whom they are shared, who can edit and who cannot, and to where they are shared. Kiteworks secure file sharing uses least-privilege access, zero-trust policy management, double encryption, and AI-enabled anomaly detection, and integrates with legacy DLP, ATP, CDR, SIEM, and SOAR security investments.
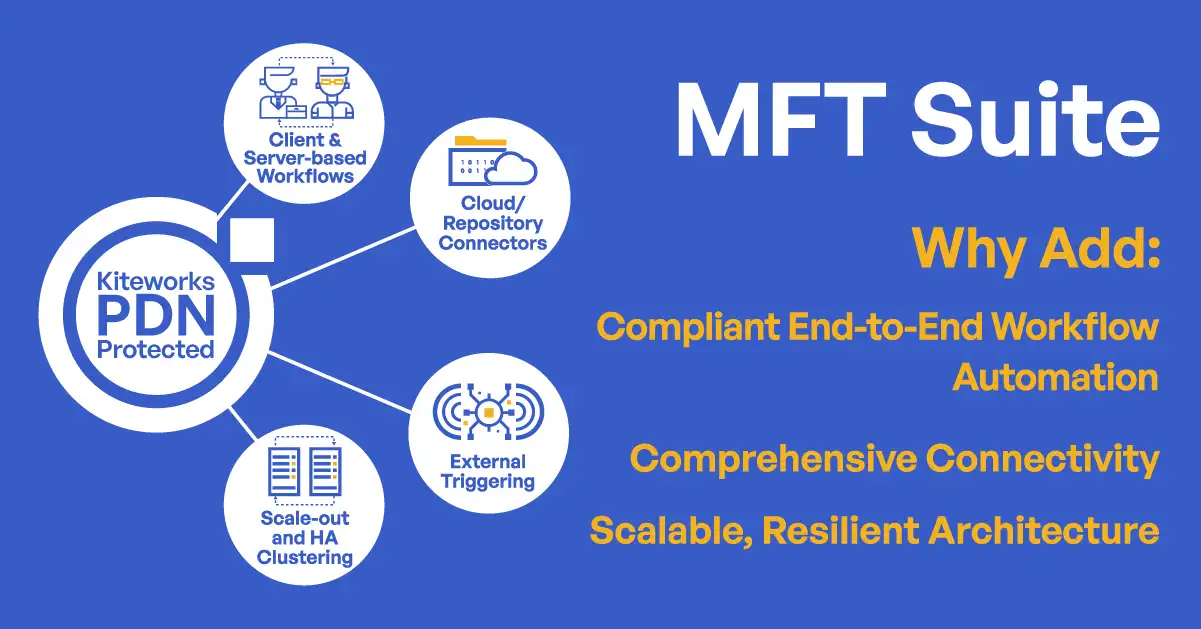
Managed File Transfer
Automate and secure large-scale file transfer operations with a hardened virtual appliance and establish granular policy controls to prevent data breaches and compliance violations. Kiteworks managed file transfer capability uses drag-and-drop authoring, a visual operations console, and unified audit logs.
Secure Web Forms
Streamline data collection, processing, and analysis using easy-to-use, customizable, and feature-rich secure web forms. Kiteworks secure web form capability enables organizations to set policies to protect confidential information while ensuring compliance with data privacy regulations and cybersecurity frameworks.
AI Data Gateway
The Kiteworks AI Data Gateway provides a secure, zero-trust bridge between AI systems and enterprise data, encrypting information at rest and in transit while tracking all access for compliance. It enables AI capabilities like retrieval-augmented generation (RAG) by giving models controlled access to current enterprise data without increasing breach risks.
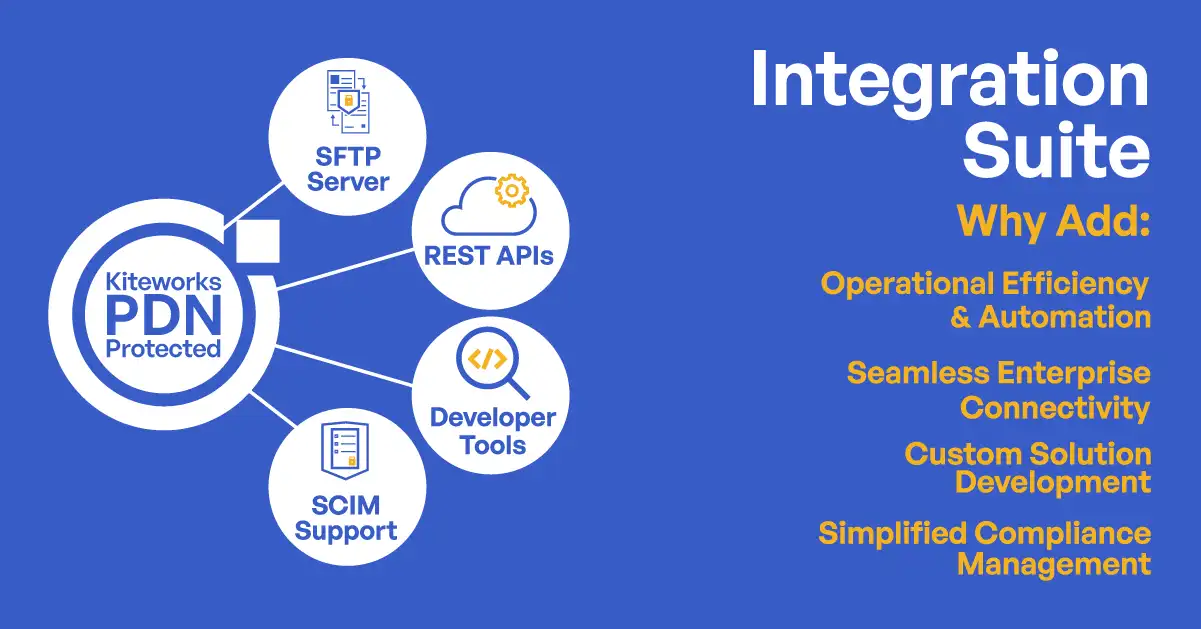
Secure APIs
Build seamless application programming interface (API) integrations to access, transfer, and store sensitive data over email, file sharing, managed file transfer, and web forms. Kiteworks makes it easy to automate management of shared folders, users, roles, policies, and other administrative controls, while employing tracking, controls, and security for regulatory compliance.
Governance, Compliance, and Security Challenges
AI Data Leakage and Compliance Risks
AI systems present significant data leakage and compliance risks due to uncontrolled access, which can lead to severe breaches of sensitive information, especially in environments lacking proper security controls. Navigating complex data regulations is essential for enterprises, as failure to comply can result in substantial fines and reputational harm. Integration challenges with legacy systems can also create vulnerabilities.
Private Data Exchange “Tool Soup”
The more third parties to which an organization sends and shares sensitive data, the greater the risk. When sensitive data is accessed by unauthorized persons and organizations, the security and compliance implications are quite serious. A next-generation digital rights management (DRM) approach with tracking, control, and security as the baseline is required.
Sensitive Data Software Supply Chain Risks
Organizations must protect their sensitive data—not only where it is stored but when it travels through various communication channels to third parties. Cybercriminals unfortunately discovered that vulnerabilities in the software supply chain give them access to hundreds or even thousands of organizations. The security capabilities of email, file sharing, managed file transfer, SFTP, and web forms is extremely important.
Data Security Governance Exposed
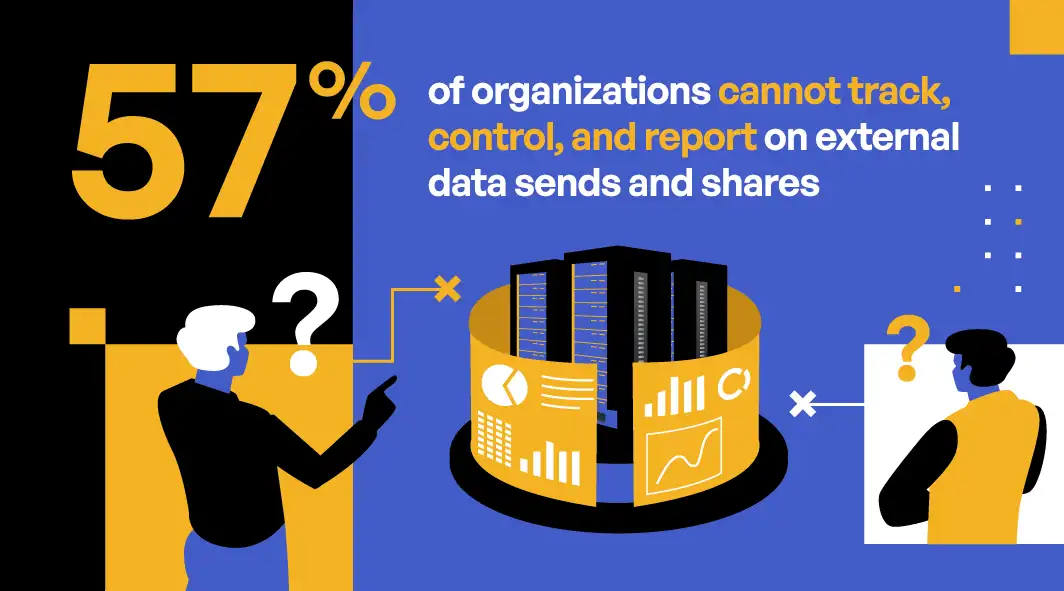
Regardless of industry, organizations struggle to track and control access to sensitive data when it leaves their perimeter. Traditional approaches make it difficult to implement sensitive data governance while 89% of organizations indicated they must generate detailed compliance reports eight or more times annually. Unifying sensitive data exchanges onto one platform can have a dramatic impact.
Data Security Compliance Grows Teeth
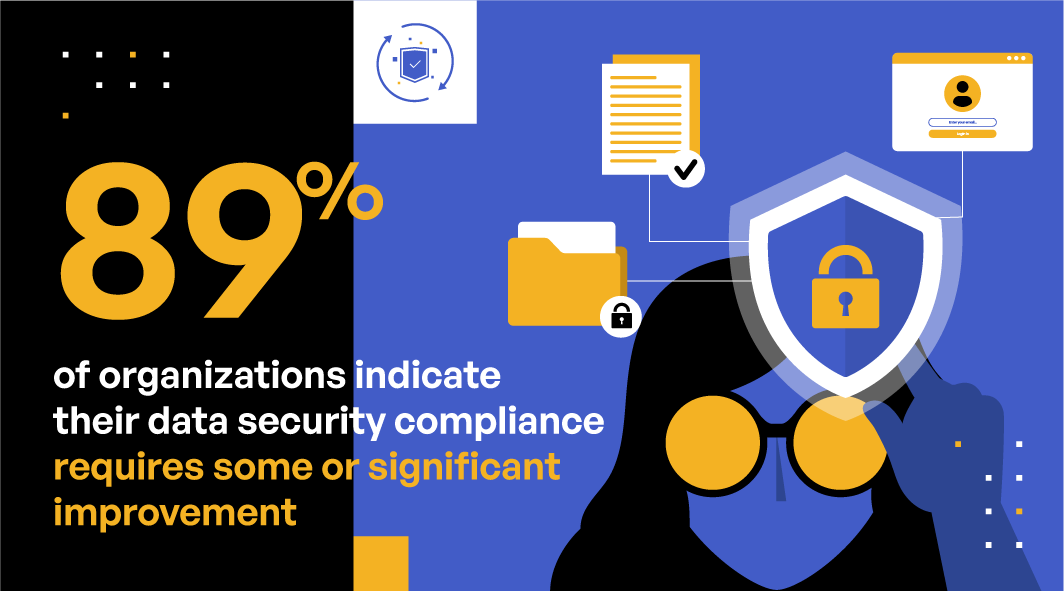
With sensitive data at the center of most data breaches, government agencies and industry bodies have responded with a series of new regulations and standards and tightening of existing ones. 89% of organizations indicate their sensitive data exchange compliance requires some to significant improvement. Centralizing all sensitive data shares and sends in one platform enables organizations to measure and manage compliance risks.
Disparate Logs Drain Productivity
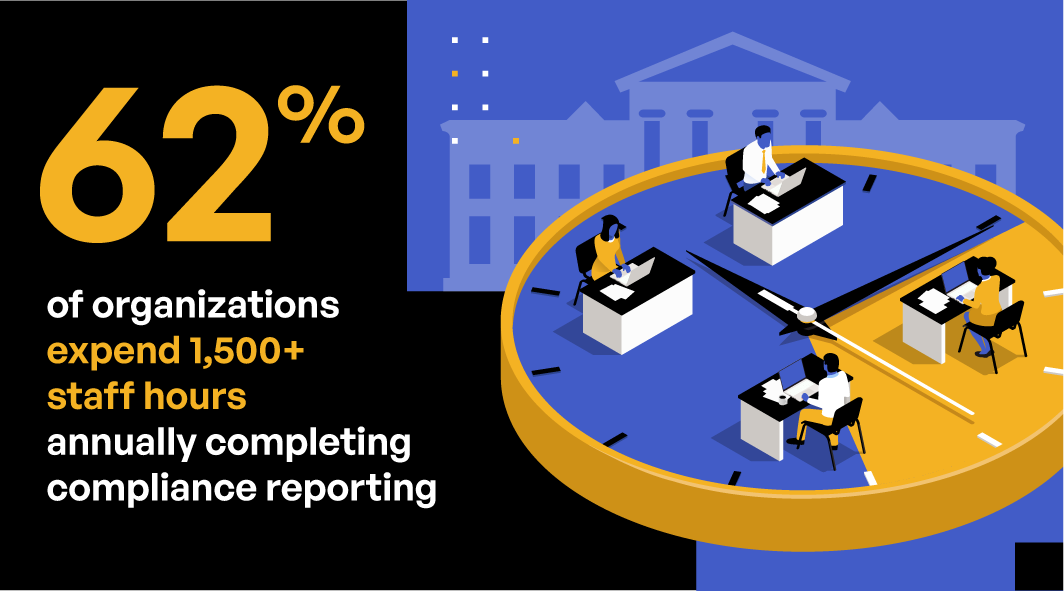
Nearly half of organizations must consolidate over 11 logs associated with sensitive data exchanges. This all adds up, expending valuable time and resources while driving up security and compliance risk. For example, when it comes to compliance reporting, 62% of organizations expend 1,500-plus hours annually. But with a unified compliance approach, all logs are consolidated in one view and integrated with advanced security systems—helping organizations to manage risk while improving efficiencies.
Get started.
It’s easy to start ensuring regulatory compliance and effectively managing risk with Kiteworks. Join the thousands of organizations who feel confident in their private data exchange platform today. Select an option below.