How to Ensure Data Sovereignty Compliance With Your Sensitive Content Communications
Navigate Complex Multi-Layered Security Requirements Across Diverse Business Operations
Public companies face the daunting task of implementing comprehensive information security controls spanning access management, encryption, incident response, continuous monitoring, and regular assessments while ensuring seamless business operations and stakeholder confidence across multiple departments and technology systems.
Implement Comprehensive Access Controls to Prevent Unauthorized Data Access
Public companies must establish robust access control policies that authorize new users, grant appropriate privileges, and prevent unauthorized access across networks, systems, and applications. Organizations need centralized platforms to manage sensitive data changes while implementing strict controls against both intentional malicious insider threats and accidental data leakage. Companies must enforce strong password policies with administrator-controlled requirements and history tracking to maintain security standards.

Secure Sensitive Data Across Multiple Protection Layers and Compliance Requirements
Personally identifiable information must be protected according to local and international data protection laws while implementing comprehensive cryptography for data at rest, in use, and in transit. Organizations need robust incident management systems with proper safeguards to detect and respond to security breaches. Companies must ensure secure data hosting compliance with Omani regulations while establishing technical measures for comprehensive data protection across all storage states.
Establish Comprehensive Monitoring Systems and Threat Detection
Public companies must establish robust log management systems aligned with ISMS frameworks and regulatory requirements while maintaining comprehensive monitoring for cyber threats. Organizations need incident response plans with rapid escalation criteria and must communicate breaches to affected parties within required time frames. Companies must conduct periodic security assessments across all systems, applications, and networks while observing and reporting workflow procedures for complete audit compliance.

Comprehensive Information Security Controls Enablement With Kiteworks
Unified Access Management and Data Loss Prevention
Kiteworks provides comprehensive access control through role-based permissions with least-privilege defaults, ensuring users receive only necessary access rights. The platform supports multiple authentication methods including MFA, SAML SSO, and Active Directory integration. Administrator-controlled password requirements and history tracking enhance security, while DLP integration via ICAP protocol monitors file content and blocks unauthorized sharing attempts, creating layered protection against data leakage.
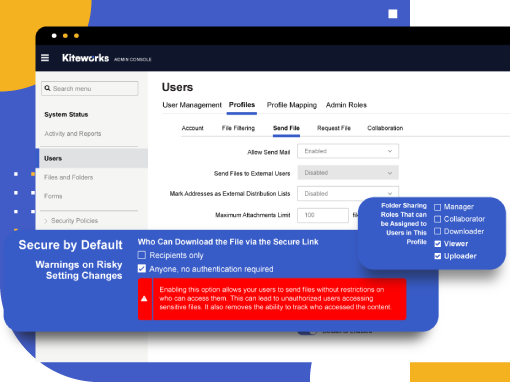
End-to-End Data Protection and Incident Response Capabilities
Kiteworks delivers 256-bit AES encryption for data at rest and TLS 1.3 encryption for data in transit, ensuring comprehensive cryptographic protection. The platform offers on-premises private cloud deployment for regulatory compliance, geographic data storage controls, and consent mechanisms for privacy laws. Built using secure development practices with OWASP standards, Kiteworks includes automated incident detection, comprehensive audit logging, session timeouts, remote wipe capabilities, and geofencing controls for enhanced security.
Kiteworks Delivers Unified Logging and Real-Time Security Monitoring
Kiteworks provides comprehensive logging across all communication channels with exportable logs for SIEM integration and human-readable formats for compliance audits. The platform offers real-time monitoring with configurable security alerts for potential threats, incident notification capabilities, and immutable audit logs that track all user activities. Complete audit logs enable rapid incident response, forensic analysis, and regulatory disclosure requirements while supporting continuous security posture assessments.

Frequently Asked Questions
Circular No. E/1/2022 establishes mandatory information security guidelines issued by Oman’s Capital Market Authority for all public joint stock companies listed on the Muscat Securities Exchange. Companies across banking, telecommunications, manufacturing, and energy sectors must implement comprehensive data protection controls within three months of the circular’s effective date.
Companies must establish access control policies, password management systems, cryptographic protection for data at rest and in transit, incident response plans, business continuity procedures, and continuous monitoring systems. The guidelines also require regular security assessments, employee training programs, and compliance with local data hosting regulations while maintaining detailed audit logs.
Kiteworks provides a unified platform with granular access controls, AES-256 encryption, comprehensive audit logging, and real-time monitoring capabilities. The solution includes multi-factor authentication, DLP integration, geographic data storage controls, and automated incident detection. This defense-in-depth approach enables companies to implement layered security protections while maintaining regulatory compliance.
Noncompliance with Circular E/1/2022 can result in regulatory penalties, loss of investor confidence, and potential suspension from the Muscat Securities Exchange. The Capital Market Authority requires quarterly verification of compliance implementation and annual confirmation in company reports, making adherence essential for maintaining public company status.
Yes, Kiteworks offers flexible deployment options including 100% on-premises private cloud solutions that can be fully isolated from the internet. This addresses Omani data hosting regulations while providing comprehensive security controls. The platform also supports geographic data storage requirements and integrates with existing enterprise systems for seamless compliance implementation.
FEATURED RESOURCES

Kiteworks Solutions for Safeguarding Data and Enforcing Access Control in Saudi Arabia to Enhance Financial Compliance

Understanding Data Sovereignty: Regulations, Security, and Compliance in 2023

Navigate the Digital Trifecta of Data Sovereignty, Cybersecurity, and Compliance With Kiteworks

2025 Cybersecurity Data Privacy and Compliance Prediction Highlights

Survey Findings Reveal Why Data Security and Compliance Leaders Like Kiteworks

CMMC 2.0 Is Here: What Defense Contractors Need to Know About Level 2 Certification
IT, SECURITY, PRIVACY, AND COMPLIANCE LEADERS AT THOUSANDS OF THE WORLD’S LEADING ENTERPRISES AND GOVERNMENT AGENCIES TRUST KITEWORKS














