Navigate Complex Multi-Domain Compliance Requirements Across Government and Critical Infrastructure
Organizations must implement comprehensive controls across three complex domains—governance, defense, and third-party cybersecurity—while ensuring continuous compliance monitoring, detailed audit logs, and secure data handling throughout the entire data life cycle to avoid penalties and reputational damage.
Establish Comprehensive Oversight and Training Across Data Operations
Organizations must conduct annual cybersecurity reviews, implement independent audits, manage human resources cybersecurity requirements, and deliver comprehensive awareness training programs covering data protection throughout its life cycle. Companies face the complex task of ensuring personnel understand secure data handling procedures, restricting unauthorized platform usage, and maintaining detailed documentation of all cybersecurity activities while proving continuous compliance with evolving regulatory requirements and organizational policies.

Manage Multi-Layered Security Across Systems, Devices, and Data Protection
Organizations must implement stringent identity and access management, apply security patches immediately upon announcement, secure mobile devices with MDM systems, protect data confidentiality through watermarking and DLP technologies, ensure advanced cryptographic standards compliance, and establish secure data disposal procedures. Companies struggle to coordinate rapid system updates, manage both organization-owned and BYOD devices, implement comprehensive data protection measures, and maintain detailed records of all security operations while ensuring continuous protection across multiple technological environments.
Secure External Partnerships and Cross-Border Data Transfers
Organizations must screen third-party employees, establish contractual data disposal commitments, document all data sharing operations with detailed justifications, verify hosting capabilities for cross-border transfers , require immediate breach notifications, and reclassify data to minimal levels before sharing. Companies face additional complexities when working with consultancy services on high-sensitivity strategic projects, requiring enhanced security measures, dedicated work environments, non-disclosure agreements, and comprehensive monitoring of all external data sharing activities while maintaining regulatory compliance.
Simplify Saudi Arabia NCA DCC Compliance With Kiteworks’ Unified Security Platform
Streamline Compliance Through Integrated Controls and Comprehensive Monitoring
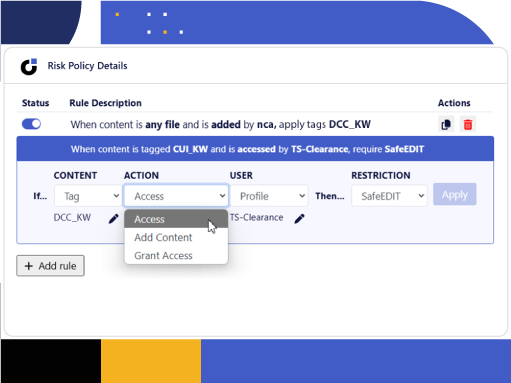
Kiteworks delivers robust authentication methods, role-based access controls , and extensive reporting capabilities that enable organizations to monitor implementation of DCC controls effectively. The platform provides comprehensive tracking features, system-level activity logs, compliance-specific dashboards, and customizable banner messages that facilitate annual audits and independent reviews. Organizations can enforce granular permissions, track all user activities, and generate detailed reports that demonstrate adherence to cybersecurity requirements while maintaining separation of administrative duties.

Comprehensive Security Through Automated Updates and Advanced Data Protection
Kiteworks streamlines security management through one-click updates that apply patches to entire solutions, role-based access controls with least-privilege principles, and mobile device management with remote wipe capabilities. The platform provides dynamic watermarking, DLP integration, double-encryption architecture, and permanent file deletion with comprehensive logging. Organizations benefit from automated security processes, granular administrative controls, advanced cryptographic protection, and detailed audit logs that demonstrate compliance with defense requirements while reducing manual security management overhead.
Secure Third-Party Integration With Complete Visibility and Control
Kiteworks enables secure external collaboration through the Sovereign Access and Data Integration Suites for repository integration, predefined collaboration roles governing access permissions, and comprehensive activity logging for all third-party interactions. The platform supports data sovereignty requirements, provides flexible data classification capabilities, and maintains detailed audit logs of all data sharing operations. Organizations can implement granular access controls, monitor consultancy service activities, enforce geographic restrictions, and ensure complete documentation of external partnerships while maintaining security standards for sensitive strategic projects.

Frequently Asked Questions
The National Cybersecurity Authority’s DCC are mandatory regulations requiring organizations across government, critical infrastructure, and private sectors to implement comprehensive data protection measures. These controls cover three domains: cybersecurity governance, defense, and third-party security, mandating encryption, access controls, regular audits, and secure data handling throughout the entire data life cycle.
All government organizations, private sector entities operating Critical National Infrastructures (CNIs), and companies in banking, energy, healthcare, and other critical industries must comply with DCC. The regulations apply to both physical and digital data handling, making compliance mandatory for organizations processing sensitive information within Saudi Arabia’s jurisdiction.
Noncompliance with DCC can result in significant financial penalties, legal repercussions, and severe reputational damage. Organizations may face increased scrutiny during cybersecurity incidents, potential liability issues, loss of customer trust, and operational restrictions that hinder their ability to conduct business effectively in Saudi Arabia’s digital economy.
Kiteworks provides comprehensive compliance support through granular access controls, double encryption, detailed activity logging, and administrative separation of duties. The platform enables secure data sharing, permanent file deletion, intrusion detection, comprehensive audit logs, and automated security processes that demonstrate adherence to all three DCC domains while protecting sensitive data.
Kiteworks offers a unified platform addressing all DCC domains through integrated controls, one-click security updates, dynamic watermarking, DLP integration, and data sovereignty support. The solution provides comprehensive tracking, role-based access management, advanced cryptographic protection, and detailed audit capabilities that streamline compliance while reducing manual security management overhead for organizations.
FEATURED RESOURCES

Kiteworks SafeEDIT: Next-generation Digital Rights Management (DRM)

Kiteworks’ Guide to the Saudi Arabia National Cybersecurity Authority (NCA) Data Cybersecurity Controls (DCC)

Kiteworks’ Guide to the Saudi Arabia Data & AI Authority Personal Data Protection Law

Understanding Data Sovereignty: Regulations, Security, and Compliance in 2023

Discover How Content-defined Policy Management Supports Data Sovereignty Compliance
IT, SECURITY, PRIVACY, AND COMPLIANCE LEADERS AT THOUSANDS OF THE WORLD’S LEADING ENTERPRISES AND GOVERNMENT AGENCIES TRUST KITEWORKS















