Navigate Complex Multi-Domain Security Requirements Across Healthcare Operations
Healthcare providers face extensive ADHICS compliance demands spanning 11 comprehensive domains while managing complex technical requirements, personnel training, and operational continuity without compromising patient care delivery.
Secure Healthcare Data Against Insider Threats and Human Error
ADHICS requires extensive controls to prevent information leakage, unauthorized access, system compromise, and credential misuse to address human resources as both indispensable assets and the weakest security link. Organizations must implement background verification, role-based access management, comprehensive training programs, disciplinary processes, and secure termination procedures. Administrative and cleaning staff present additional challenges, requiring constant monitoring and surveillance coverage to protect patient healthcare information from accidental or deliberate security breaches.


Manage Complex Asset Life Cycles Across Healthcare Operations
Healthcare entities must maintain comprehensive, up-to-date inventories of all information assets including data, devices, applications, systems, and infrastructure supporting care delivery. ADHICS requires establishing granular relations between asset types, designating clear ownership, implementing acceptable use rules, and addressing bring-your-own-device risks. Organizations must classify assets into four categories based on value and protection needs, create specialized handling procedures, manage removable media and medical devices, and ensure secure disposal through consistent frameworks for categorizing, tracking, handling, and protecting assets across all life-cycle stages.
Domain Security Across Complex Healthcare Systems
Healthcare organizations must simultaneously comply with additional ADHICS domains covering environmental security through access control, third-party security, and continuity planning. These domains require specialized controls for securing facilities, medical devices, paper records, and digital environments. Organizations must implement granular access management, infrastructure defenses, secure external integrations, incident response capabilities, and continuity planning while maintaining ongoing operations, communications oversight, patient privacy preservation, and third-party interactions without compromising care delivery.
ADHICS Made Simple: Secure Healthcare Data With Kiteworks
Embedded Vigilant Access Governance and Accountability Controls
Kiteworks minimizes insider threats through granular access controls that appropriately scope permission assignments and comprehensive activity monitoring that provides compliance oversight. The platform facilitates stringent data access management, security policy awareness reinforcement, and breach investigation support. Custom login banners mandate acceptance of responsibilities while automatically warning administrators about unsafe configurations to reduce errors and negligence. These layered technical safeguards secure the human domain by embedding vigilant access governance, transparency, and accountability tools across access, awareness, and accountability policies.

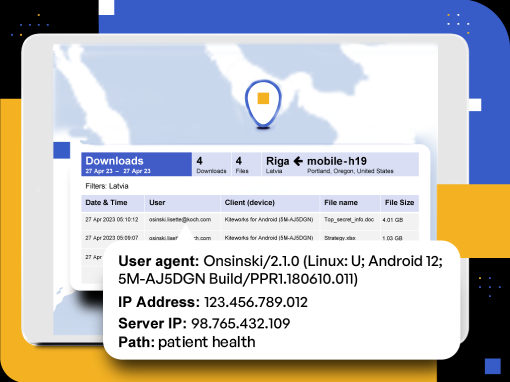
Comprehensive Asset Protection Through Governance and Monitoring
Robust access governance, activity monitoring, and data protection tools fulfill asset management obligations. Granular permissions, tamper-proof logging, remote wipe, and custom forms enable appropriate access control, classification, handling, and disposal across various asset types. The platform maintains file inventories, manages risk exposures, and upholds custodianship duties around digital items. These layered technical safeguards embed security across the entire asset life cycle through standardized frameworks for categorization, communication, retention, and destruction while securing sensitive data from compromise.
Integrated Multi-Domain Protection Through Comprehensive Safeguards
Kiteworks addresses multiple ADHICS requirements through integrated access governance, systemic hardening, resilience provisions, and protective capacities. The platform delivers rigorous protections for facilities, medical devices, and environments storing sensitive data through breach assumptions and resilient threat containment. Granular controls, multi-factor authentication, segmentation, logging, and encryption facilitate access management and secure external integrations. Extensive monitoring covers activity trails, gathers forensic evidence, enables agile quarantines, and supports continuity planning. These integrated safeguards uphold security and availability objectives across maintenance, communications, privacy preservation, and incident response efforts.

Frequently Asked Questions
ADHICS is a comprehensive security framework established in 2019 that mandates strict privacy and security controls for all healthcare entities in Abu Dhabi. The standard covers 11 domains including access controls, communications security, and health information protection. Healthcare providers must comply with basic requirements within six months and advanced requirements within one year to ensure patient data protection and maintain public trust.
All DOH-regulated healthcare entities in Abu Dhabi must comply, including hospitals, medical facilities, diagnostic centers, pharmacies, rehabilitation centers, dialysis centers, mobile healthcare units, and home care providers. The standard applies to healthcare professionals, support staff, and anyone with access to patient health information. Compliance requirements vary based on facility size, with hospitals having 21+ beds requiring advanced-level controls.
Organizations struggle with managing 11 comprehensive domains simultaneously while maintaining patient care delivery. Key challenges include implementing granular access controls, maintaining asset inventories, securing medical devices, managing third-party relationships, training personnel, and ensuring business continuity. The complexity increases with requirements for background verification, incident response planning, and coordinating environmental security across multiple operational areas.
Kiteworks provides integrated solutions including granular access governance, multi-factor authentication, comprehensive activity monitoring, and tamper-proof audit logging. The platform offers encryption for data in transit and at rest, remote wipe capabilities, and automated policy enforcement. These features address multiple ADHICS domains through unified access controls, asset management tools, and incident response capabilities while maintaining operational efficiency.
Kiteworks addresses all 11 ADHICS domains through comprehensive capabilities including human resources security via access governance, asset management through inventory controls, physical security integration, access control with role-based permissions, operations management with monitoring tools, secure communications, health information protection, third-party security, system development security, incident management, and continuity planning through resilient infrastructure and response orchestration features.
FEATURED RESOURCES

Join the (R)evolution: Navigate the Future of Next-gen DRM

Kiteworks Guide to the Abu Dhabi Healthcare Information and Cyber Security Standard
NYC Health + Hospitals: Protecting PHI While Improving Efficiency and Visibility

How To Protect PHI and Comply With HIPAA While Meeting Employee Vaccine Mandates

Secure Your Critical Data With the Kiteworks Private Data Network
IT, SECURITY, PRIVACY, AND COMPLIANCE LEADERS AT THOUSANDS OF THE WORLD’S LEADING ENTERPRISES AND GOVERNMENT AGENCIES TRUST KITEWORKS















